A comprehensive guide to
RANSOMWARE
Everything you need to know about ransomware
Ransomware attacks, targets, strategies + more
What is ransomware?
Ransomware is any software used to infiltrate a network with the intent of either disrupting or destroying its data, devices, or infrastructure. This software is used during a ransomware attack, where a malicious attacker holds a network hostage for a requested sum of money.
Related resource → [eBook] Ransomware Trends in 2021
How do ransomware attacks work?
During a ransomware attack, a device is targeted and infected by an attacker. The ransomware locks or encrypts files and programs on the device to prevent their use and demands a ransom from the victim in return for their release. The most common form of ransomware is a malicious link within an email that leads to a website where an attack package is downloaded. Examples of previous, notable ransomware attacks include Colonial Pipeline, JBS, and Acer.
What does a typical ransomware attack lifecycle look like?
The cyber kill chain, or ransomware lifecycle, tracks the sequential phases of a cyberattack; understanding this process can help you identify and prevent an attack. Typical attacks tend to contain a pattern of...
- Reconnaissance
- Malware delivery
- And finally, exploitation.
The ransomware attack lifecycle begins before you even realize your data has been captured. In the reconnaissance phase of an attack, hackers infiltrate your network to begin extracting and editing files. Once they’ve gained access to your systems, they install malware and begin the exploitation phase in which they manipulate your network and initiate the attack.
Why are ransomware attacks dangerous?
Ransomware attacks have many dangerous short- and long-term effects on your employees, clients, third-party vendors, and company reputation. An attack could result in the theft of company data or personal identity information, loss of financial funds through ransom payments, disruption of critical infrastructure, and much more. These ramifications are not only dangerous to the bottom line of an organization but could result in the downfall of a company entirely.
Related resource → [Blog] Why Ransomware Is So Dangerous and Hard to Stop
Where did ransomware originate?
The first-ever noted ransomware attack was the 1989 AIDS Trojan virus. Attackers released floppy disks containing viruses and forced the victims to pay a sum of money to fix their devices. Since ransomware can leave a long-lasting and negative impact on a company’s reputation, numerous cases throughout history have gone unreported, making it hard to create a definitive timeline for ransomware.
What we do know is that with every milestone in technological advancements, ransomware is not far behind. Today, ransomware is a larger threat than ever as it has recently taken on a business-like model and is an almost equal counterpart to cybersecurity firms.
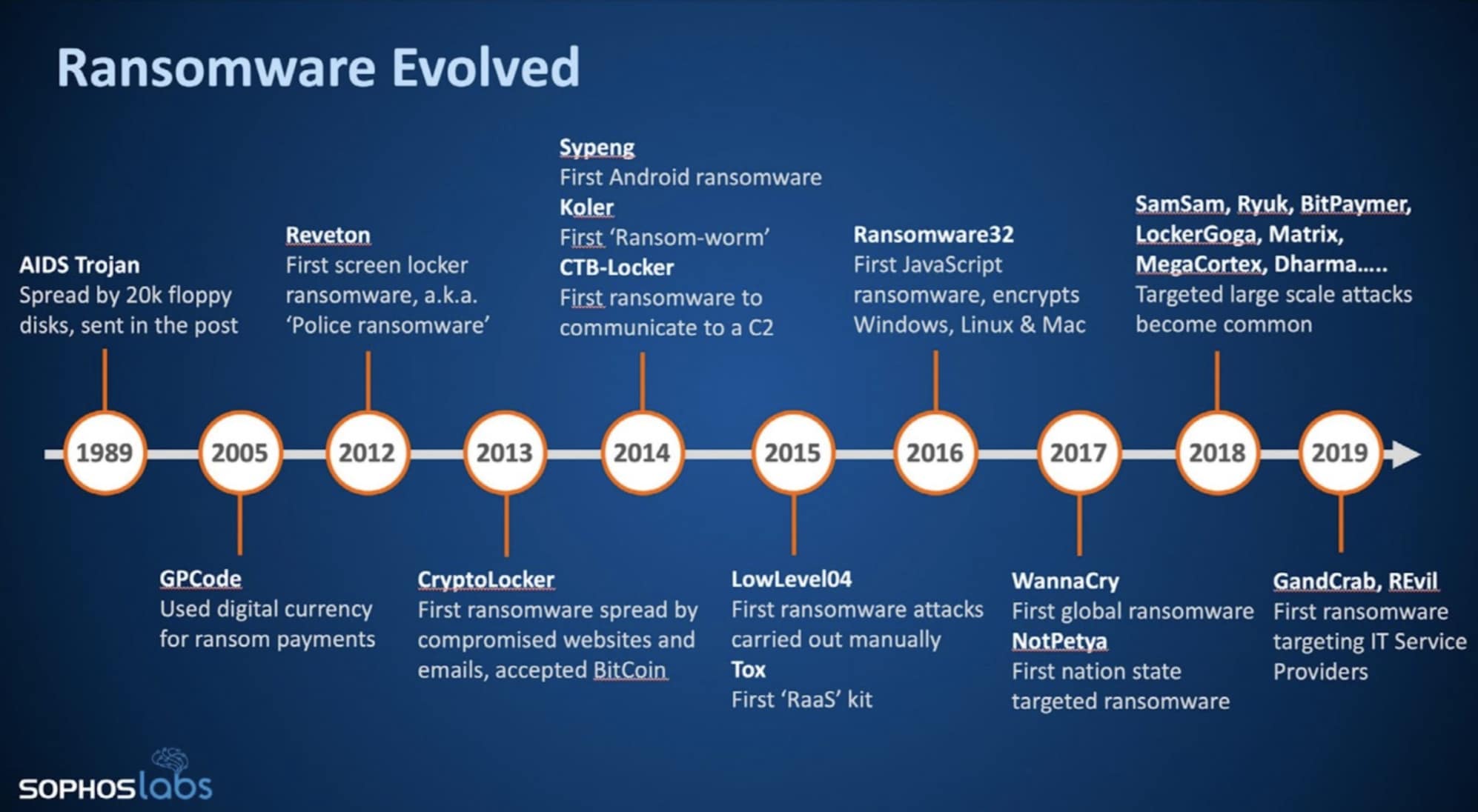
Source: Sophos an Avertium Technology Partner
Where are ransomware attacks most common geographically?
No country is safe from ransomware, but some areas suffer from attacks more frequently than others. The most common countries to harbor attackers are the United States, China, Russia, and North Korea.
Related resource → [Blog] Most Ransomware Attacks Still Come from Russia, China, and North Korea
What types of ransomware attacks exist?
There are three different types of ransomware attacks.
-
Consumer Ransomware Attack: Cybercriminals take a “spray and pray” approach to ransomware infections. They attempt to infect as many computers as possible and ask for a low ransom per infection. These attacks are often automated, and encryption begins shortly after the computer is infected.
-
Server-Focused Ransomware Attack: By encrypting vital files on critical systems (such as asp.net files in a web application), these attacks are designed to make an organization incapable of doing business.
-
Critical Mass Attack: This targets user workstations instead of company servers. These attacks achieve the same objective as a server-focused attack by rendering a high percentage of a company’s computers unusable. This also means it exploits more vulnerable client machines.
How does ransomware infiltrate networks?
Ransomware comes in an abundance of forms and attack vectors. Three of the most common methods used by hackers include:
-
Virus Encrypted Content: This can include photos and videos that you may be asked to click on or download.
-
Phishing Campaigns: Emails from unknown senders or with abnormal content from what you typically receive are likely a phishing attempt. It is best to avoid any links within these emails and to report them immediately.
-
Hacked IDs and Passwords: Accounts with passwords that are simple and less frequently changed are subject to attacks. Sharing passwords through unsecured networks such as email, text or open storage environments also provides easy access for any cyber threat who is able to find it.
Other forms of infiltration include:
Who can participate in ransomware attacks?
The short answer is anyone. The proliferation of Ransomware as a Service (RaaS) has made it easy for less sophisticated cybercriminals to deploy complex software. This easy access to the necessary tools and code from RaaS groups makes pulling off bigger ransomware attacks much more attainable.
What is Ransomware as a Service (RaaS)?
Ransomware as a service refers to ransomware users offering their own tools to other hackers and building out their network with a business-like model. This is a growing trend throughout the dark web and is what allows many smaller hackers to pull off larger and more in-depth breaches.
Related resource → [Blog] Ransomware as a Service (RaaS) Threats
What are RaaS gangs?
RaaS gangs are specific groups that are well-known for creating businesses that develop and sell ransomware code. These groups are also known for participating in their own sizable ransomware attacks. They work operationally to sell their tools and initiate new members into their networks with the intent of expanding and growing their business.
RaaS gangs often work alongside botnet operations as well. Botnets are large, connected networks of breached devices that can be utilized by RaaS gangs when they need. A botnet herder deploys viruses and malware code onto devices by getting users to unknowingly download them. From here, they can choose to either disrupt the infected device or use the device to further spread their reach. Some examples of major RaaS gangs include Hive, Darkside, Lockbit 2.0, REvil, Conti and BlackMatter.
Related resource → [Blog] The Rise of RaaS Gangs + What You Need to Know
What devices can ransomware attackers use to reach victims?
Ransomware is not confined to solely business networks. It can breach any device or network that has access to the internet. As the IoT (internet of things) continues to expand, more unprotected devices are channels for ransomware attacks and spreading these breaches. This means anyone who operates any smart device (at home or at work) is susceptible to ransomware.
Related resource → [Article] The IoT Ransomware Threat Is More Serious Than You Think
How do I know if I am a victim of ransomware?
It is apparent when a victim's network encounters ransomware. It is common during these attacks for hackers to completely shut down an organization's online systems and to display a ransom note through the contaminated devices. The note will typically include an exact sum and instructions on how to pay the ransom. For organizations that face ransomware threats, it is common that they end up paying the fee or risk losing all of their company data and devices.
Does ransomware only go after large businesses?
No. Ransomware most often hunts vulnerabilities, not specific targets. This means that any business– regardless of its industry or size– is susceptible to ransomware attacks if its attack surface is weak. Because of this, breaches are growing among smaller organizations that believe they are less likely to be attacked, and therefore, do not invest in cybersecurity.
Related resource → Why are SMEs More Susceptible to Data Breaches?
What are the impacts of a company that is breached by ransomware?
Ransomware is most commonly known for its potential financial ramifications. However, there are many other consequences an organization may face with a ransomware attack, such as:
-
Data Loss: Attackers may permanently erase data stored on a network or leak it out to the public.
-
Public Relations: Once a company's clients, its partners, and the public find out that the organization was hacked, it is challenging to regain trust from those third parties. Without the correct public relations specialists and incident response plan in place, the business may seem like a liability.
-
Legal Matters & Regulations: If an organization is responsible for any personally identifiable information and it is breached or leaked by hackers, the blame falls onto that company. These legal battles and repercussions lead to even greater impacts on its finances and reputation.
- Operations: In the time that an organization’s network is infected and held hostage, both production and sales are consequently brought to a halt. For some companies, it is detrimental to miss several days of production and benchmarks.
What is the average cost of a ransomware attack?
The financial impacts of ransomware attacks vary from situation to situation. However, one thing is clear– the average cost of incurring a ransom attack is growing. In 2019, the average remediation cost for an attacked company was $761,000. That figure more than doubled in 2020 with the average remediation cost totaling over $1.85 million.
Colonial Pipeline Ransomware Attack
What Happened
In May 2021, the Colonial Pipeline experienced a ransomware attack, resulting in a shutdown for all of the organization’s digital systems. The Colonial Pipeline moves oil from the Gulf of Mexico to the eastern United States and is one of the most important pipelines in the United States. The attack caused issues for oil consumers and airlines along the East Coast. President Joe Biden declared this attack a state of emergency for the nation.
How the Company Detected the Attack
On May 7th, 2021, a Colonial Pipeline employee found a ransom note on one of the internal IT systems. The ransomware organization DarkSide gained access to the Colonial Pipeline’s IT network through an exposed password that was not protected by multi-factor authentication.
How They Protected Themselves
Colonial Pipeline turned to the security firm Mandiant to help investigate details of the attack. In addition to Mandiant, the organization also called the FBI and Department of Homeland Security to help protect themselves during the attack. The Colonial Pipeline CEO made the decision to pay the almost $5 million ransom demanded by DarkSide. The attack did not spread to pipeline operations however the organization wanted to avoid all risks of this happening. The pipeline was shut down for multiple days, which affected the price of gas for many consumers across the east coast.
The Aftermath of the Attack
The United States law enforcement was able to recover $2.3 million of the ransom money. The U.S. government used this attack to develop methods to prevent another attack of this nature. Congress also held a hearing to discuss the aftermath of DarkSide’s attack.
What are proactive steps an organization can take against ransomware attacks?
One of the easiest steps to protecting your organization against a ransomware attack is providing security awareness training for your employees. Training is often conducted through social engineering means like phishing and watering hole attacks, and it greatly reduces the probability of a ransomware infection affecting your organization.
Another important step is maintaining a recent, comprehensive and segregated backup of your data. If a breach is successful, the backup allows you to wipe the infected machine and restore it with minimal impact on your operations. It is imperative to perform these backups regularly and store them on media that isn’t directly connected to a machine, such as cloud-based solutions.
If a company is unable to maintain or access a recent backup, a golden image is a solid secondary option. These secure, clean images allow you to wipe an infected machine and quickly install all the important programs, security patches and configurations a user needs. This allows them to get back up and running without wasting time reconfiguring a machine after an incident.
Lastly, performing a ransomware readiness assessment (or a ransomware risk assessment) is another crucial step in mitigating and managing threats. A ransomware readiness assessment is designed to evaluate an organization’s processes, tools, and overall preparedness in the face of an attack. By conducting a ransomware assessment, you can proactively identify risks within your cybersecurity policies and develop a ransomware readiness plan before you’re even hacked.
How do you respond to a ransomware attack if you're not prepared?
If you’re unprepared when a ransomware attack strikes, there are five ways to minimize the damage and get systems back up and running with minimal downtime:
- Isolate the ransomware infection to assure it doesn’t spread any further. There are two methods by which ransomware spreads– exploiting loopholes in program security and taking advantage of human behavior.
-
Remediate the ransomware damage. How you take action on the infected machine will depend on if a data backup exists or not.
-
Try recovering the lost data. While data encrypted by ransomware is not recoverable, some variants include logical or programming errors. This can allow an expert to develop solutions that may enable the decryption of some or all of the encrypted files. The No More Ransom Project is an excellent resource for this.
-
Eradicate the malware. This is the simplest method for guaranteeing a device is no longer infected with ransomware. If this is not possible for some reason, then more research is required.
-
Rebuild and resume operations following a ransomware attack. After the breach is identified and eradicated, ensure all systems are hardened, patched, replaced, and tested before you re-introduce the previously compromised systems to your production environment. Once normal operating procedures and incident prevention measures are in place, communicate with stakeholders to verify all systems are stable and functional.
What can I implement to optimize my security?
No one knows your organization like you do. That’s why a cybersecurity self-assessment tool (or ransomware self-assessment tool) can give you greater insight into data that’s right in front of you.
A typical cybersecurity self-assessment tool helps you identify threats to then determine their associated level of risk. Using a ransomware risk assessment template will show you how to prioritize your cybersecurity processes so that you can stop wasting time and resources and make the most of your cybersecurity partnership.
Also, working with an MSSP (managed security services provider) is one of the most efficient ways to optimize your security. MSSPs use an assortment of security tools in addition to a SIEM device to help detect, thwart, and gather information on security attacks. They are also responsible for providing timely notification of events through the monitoring of network and security log events, identification, and remediation of today’s modern threats are the primary functions of a virtual SOC.
An MSSP can also help you combat ransomware by utilizing a Zero Trust Network Architecture. They eliminate the element of trust that is found in today’s typical environments. Doing this reduces your attack surface by limiting which users and devices can access sensitive corporate resources.
Being susceptible to ransomware threats is something that organizations can’t stop, but with the proper controls in place, you can minimize and manage the attack surface to stop most attacks before they start. There are no guarantees that every attack will be stopped, so it’s important to have a remediation plan in place for that worst-case scenario.
However, if you become a ransomware victim, focus on mitigation prevention and containment:
-
Extended Detection & Response: We believe that XDR in all of its forms - tools, platforms, services - is fundamentally an approach, not a toolset. Rather than point solutions that claim to be “XDR,” Avertium employs XDR as a philosophy, delivering on the promise that XDR makes: the right combination of innovative technology, field-validated threat intelligence, and resource empowerment to reduce complexity, streamline your operations and expertly manage your attack surface.
-
Zero Trust Network Architecture: As a key component of Avertium’s rigorous approach to providing extended detection and response (XDR), ZTNA gives our customers more visibility into data across networks, the cloud, endpoints, and applications.
-
Digital Forensics and Incident Response: Provided as an on-demand crisis response service as well as a retainer-based program, Avertium’s Digital Forensics and Incident Response (DFIR) helps you to rapidly assess, contain, eradicate, and recover from a security incident to minimize impact and return you to normal operations.
Ransomware gangs understand the current challenges faced by organizations in a work-from-anywhere environment and a collapsed perimeter - they view this as a segue into extorting data. The time it takes to detect, contain, and respond is very challenging in an unprepared company.
Having a higher level of visibility shines a spotlight on unauthorized users faster, allowing for enhanced containment and stronger, more timely incident response. Avertium’s team of industry experts can help you implement cutting-edge monitoring and detection technology (EDR) to meet the challenges of today, and prevent the threats of tomorrow.
ABOUT AVERTIUM
Avertium is the security partner that companies turn to for end-to-end cybersecurity solutions that attack the chaos of the cybersecurity landscape with context. By fusing together human expertise and a business-first mindset with the right combination of technology and threat intelligence, Avertium delivers a more comprehensive, more programmatic approach to cybersecurity – one that drives action on the ground and influence in the boardroom. That’s why over 1,200 mid-market and enterprise-level organizations across 15 industries turn to Avertium when they want to be more efficient, more effective, and more resilient when waging today’s cyber war. Show No Weakness®


