- WHY AVERTIUM?
-
-
Why Avertium?
Context over chaos. Disconnected technologies, siloed data, and reactive processes can only get you so far. Protecting businesses in today’s threat landscape demands more than a set of security tools – it requires context.
That's where Avertium comes in
-
Considering Microsoft?
Avertium Named Microsoft Security Solutions PartnerAvertium’s managed services for Microsoft Security Solutions is delivered through the company’s premium service: Fusion MXDR. Fusion MXDR includes 24x7 monitoring and management of Defender for Endpoint and Sentinel, threat intelligence, attack surface
monitoring, and vulnerability management for Microsoft Security customers. -
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- SOLUTIONS
-
-
Governance, Risk, + Compliance
GRC with context – not complexity. -
Attack Surface Management
No more blind spots, weak links, or fire drills. -
Threat Detection + Response
Detect, adapt, and attack with context. -
Microsoft Security Solutions
End-to-end support from strategy to daily operations to maximize your Microsoft Security.
-
-
- COMPANY
-
-
About Us
Security. It’s in our DNA. It’s elemental, foundational. Something that an always-on, everything’s-IoT-connected world depends on.
Helping mid-to-enterprise organizations protect assets and manage risk is our only business. Our mission is to make our customers’ world a safer place so that they may thrive in an always-on, connected world.
-
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- PARTNERS
-
-
Our Partners
Best-in-class technology from our partners... backed by service excellence from Avertium.
-
Partner Opportunity Registration
Interested in becoming a partner?
With Avertium's deal registration, partners can efficiently and confidently connect with Avertium on opportunities to protect your deals.
-
Latest Avertium Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- NEWS & RESOURCES
-
-
News & Resources
Dive into our resource hub and explore top
cybersecurity topics along with what we do
and what we can do for you. -
Latest Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- CONTACT
TIR-20211004 An In-Depth Look at Ransomware Gang, Conti
Executive Summary
As the ransomware epidemic continues to expand, RaaS gangs like Conti are making it difficult for enterprises to keep up. In September 2021, the FBI, NSA, and CISA warned that Conti ransomware attacks were on the rise and impacting victim networks through malicious email links, attachments or stolen Remote Desktop Protocol (RDP) credentials. Recently, CISA and the FBI have discovered over 400 Conti attacks within the United States, as well as international organizations. The ransomware gang has successfully encrypted servers and has demanded ransom from its victims in exchange for stolen data. With ransom demands as high as $25 million, the question begs, who is Conti and how can they be stopped?
Who is conti?
A Russian-speaking RaaS organization, Conti uses RaaS to deploy disruptive ransomware attacks that target critical infrastructure, like hospitals and government organizations. They specialize in double extortion operations of simultaneous data encryption and data exfiltration for financial gain. If the ransom is not paid, Conti will blackmail their victims by threatening to publish stolen files.
In May 2021, the FBI notified the public stating that Conti tried to breach over a dozen healthcare and first responder organizations. By September 2021, the gang successfully stole the data of several healthcare organizations. According to our partner, Advanced Intelligence, Conti builds their negotiation strategies based on the premise that the majority of targets who pay the ransom, do so because they need to restore their data – making prevention of data leaks a secondary goal.
It is believed that Conti is controlled by a Russian-based cybercrime group, Wizard Spider. Wizard Spider is known for creating and operating TrickBot banking malware. The group began using TrickBot in 2016 for financial fraud and now has three ransomware families – Ryuk, Conti, and BazarLoader. However, Conti only uses TrickBot if they need additional resources. Once they deploy it, they may wait and stay in the network, beaconing out by using Cobalt Strike.
Image 1: Tweet from CISA
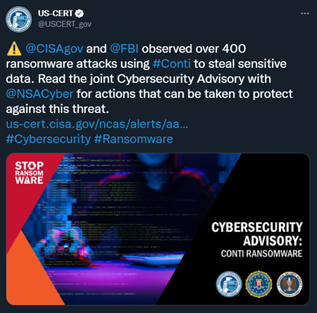
Source: Twitter.com/2USCERT_gov
Conti's clever tactics
It’s no secret that Conti uses several tactics to exploit their victim’s networks and systems. They have been known to utilize tools easily found within their victim’s networks as an aid in their attacks, adding tools as needed (Mimikatz and Sysinternals) to escalate privileges and move laterally through a network. This gives Conti the leverage to gain unauthorized access to networks by stealing RDP credentials and weaponizing malicious email links or attachments.
After embedding Word documents with PowerShell scripts, Conti stages Cobalt Strike by way of the Word documents before dropping Emotet onto the network. This gives threat actors access to deploy their ransomware. However, unlike other RaaS gangs, Conti has been seen inside a victim’s network for several days to a few weeks before they actually deploy their ransomware, using dynamic-link libraries (DLLs) for delivery.
Backup Removal
You may have read this far and are wondering, what’s so clever about Conti’s tactics? In the cyber intelligence world, if an organization is attacked by any cybercriminal group, they more than likely will be able to restore their data via backups. If that happens, the chances of a ransomware gang receiving their ransom is slim. That’s why Conti became strategic and developed a methodology to remove backups, thus forcing their victims to pay. Clever, right?
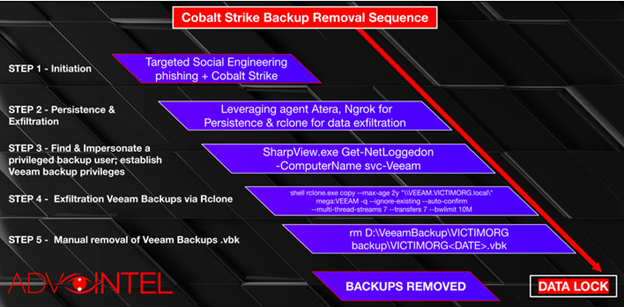
According to Advanced Intelligence, the way Conti removes backups is by selecting a team of people with experience related to backup identification, localization, and deactivation. The backup removal team then uses Veeam backup software to aid in this feat. Veeam is a backup, recovery, and data management solutions platform for cloud, virtual, and physical environments. After finding Veeam privileged users and services, Conti exfiltrates, removes, and encrypts backups to ensure that you have no chance of recovering your files.
Cobalt Strike
Conti’s attacks are initiated through spam messages with direct Cobal Strike beacon backdoor delivery. Through social engineering, the spam campaigns ensure that executives and employees open those emails, and the Cobalt Strike beacons are executed. Next, the Atera module and Ngrok application are leveraged to establish persistence. Atera is a legitimate remote management agent that Conti uses to avoid Cobalt Strike detections, while Ngrok is used to establish a tunnel to the local host. The local host serves as a path for data exfiltration.
Through Rclone weaponization, Conti exfiltrates the data and an external location for data synchronization is established. Once the data is in the attacker’s hands, they glean all data related to finance, legal, accounting, insurance, and Information Technology. Finally, Conti ensures their victim can’t recover from their attack by locking their victim’s system and removing their backups.
Image 2: Backup Removal Sequence
Source: Advanced Intelligence
VOIP and ProtonMail
If victims decide not to adhere to ransom demands within two to eight days, Conti has another trick up their sleeve – calling the victim. The calls are made by using single-use Voice Over Internet Protocol (VOIP) phone numbers. The attackers may also use ProtonMail, a webmail service that offers end-to-end encryption for message delivery.
PrintNightmare
Another way Conti is deploying its ransomware is through a Microsoft Vulnerability named PrintNightmare. In August 2021, PrintNightmare (CVE-2021-34481) was a Microsoft vulnerability that affected the PrintSpooler service – a service that runs on every computer participating in the Print Services system for Windows-based print clients. If organizations have not patched this vulnerability, they are leaving their networks wide open to be attacked by Conti. The group has already stated that the vulnerability is “fresh, but sensational” and they’ll “use it until we shut it down.”
ProxyShell
PrintNightmare isn’t the only Microsoft vulnerability Conti is exploiting. The ransomware gang is also targeting unpatched Exchange servers with ProxyShell (an evolution of ProxyLogon). Conti has been using this vulnerability to gain access to a targeted network and set up a remote web shell. The attacks happen rapidly, and within 30 minutes, Conti generates a complete list of the network’s computers, domain controllers, and domain admins. Four hours after that, the attackers have the credentials of domain admin accounts at their disposal and start executing demands.
TrickBot
We previously mentioned TrickBot and how Conti is more than likely using it in the same way Wizard Spider was using it. TrickBot was a primary tool for Wizard Spider and played an integral part in their Big Game Hunting (BGH) operations. In September 2020, CrowdStrike Intelligence found that a non-standard configuration file was being sent to victims infected with TrickBot. The files gave instructions to victims asking them to communicate with the C2 server address 0.0.0.1 on port 1. As a result, an unknown number of bots were isolated from the TrickBot network and were unreachable through the standard C2 channel. Wizard Spider was able to infect over one million systems worldwide by using TrickBot malware.
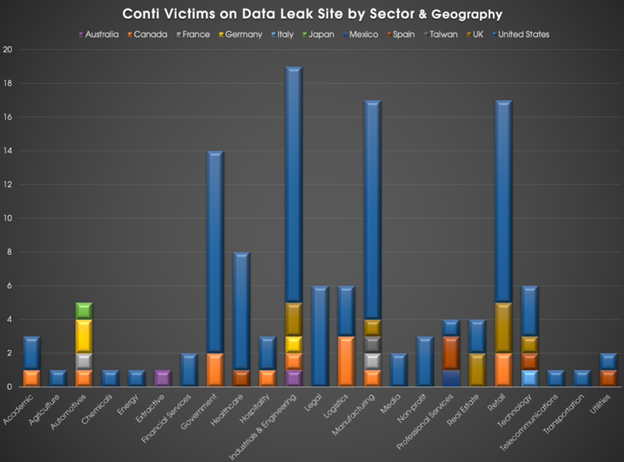
After Wizard Spider’s initial attacks utilizing TrickBot, things tapered off for the ransomware gang. However, researchers at CrowdStrike have seen a resurgence of Wizard Spider as they introduced Conti. In August 2020, Wizard Spider began using a data leak site for Conti. Additionally, Conti has already been used to compromise over 120 networks, with stolen data listed on their data leak site. If you take a look at the graph below, you can see that their targeting is opportunistic, which is an indicator of Wizard Spider and other ransomware operations.
Graph 1: Data Leak Site by Sector and Geography
Source: Crowdstrike.com
the differences between conti & other ransomware gangs
Unlike other ransomware gangs like DarkSide and REvil, Conti has historically targeted critical infrastructure. To date, Conti has successfully infiltrated the networks of the Defense Industrial Base (DIB), Leon Medical Centers, Nocona General Hospital, and Rehoboth McKinley Christian Health Care Services (RMCHCS).
According to HealthHitSecurity.com, Conti also leaked the data of these healthcare organizations when they refused to pay the ransom for file decryption. Some of the information stolen included social security numbers, contact information, insurance details, diagnoses, treatments, and photographs. In February 2021, it was discovered that Conti’s website included at least 20 files of patient data from Leon Medical Centers.
Another way Conti differentiates itself from other RaaS models is that they more than likely pay a wage to the people who deploy the ransomware, instead of a percentage of the ransom from a successful attack.
Conti Threatens Journalists
In October 2021, Conti published a threatening letter to the media and to journalists reporting on their activity. In the letter, Conti stated that they have seen screenshots of their chats surrounding ransom negotiation with a Japanese electronics company. As a result of seeing their conversation leaked to the public, Conti decided to terminate their negotiations with the company and publish their data.
Conti also stated that if organizations continue to leak their negation conversations, they will terminate all negotiations with that particular organization and dump their data onto their blog. They further stated that they respect journalism when it’s done properly, but not when reporting is done behind their backs.
The letter was Conti’s first public comment, but they made it clear that there is more to come. In the best interest of our clients and the public, Avertium will not publish anything that appears to be an in-progress negotiation between Conti and their victims. This report includes Conti’s public statement and information about their internal tactics that were previously published.
Image 3: Conti's Public Statement

Source: Twitter.com/@vxunderground
don't pay the ransom
CISA, the FBI, and Microsoft discourage organizations from paying ransom in exchange for decryption. Our partner, Sophos, found that paying ransom demands increases the likelihood that attackers will try to double the ransom and still keep your data – making it a difficult path to data recovery.
In 2020, Sophos released a report where they surveyed 5,000 global IT decision-makers within a range of sectors. After surveying, they found that 51% of those organizations faced a ransomware attack during that year. Within the U.S., 59% of those surveyed were a victim of an attack, but only 25% were able to stop an attack before their data was encrypted. The cost to recover from the attacks without paying the ransom was quite expensive at $732,520, however; when an organization did pay the ransom, that number skyrocketed to $1.4 million.
Additionally, 56% of the organizations that did not pay the ransom were able to recover encrypted data from backups. Chester Wisnewski, Sophos’ principal research scientist, stated that organizations who are hit by a ransomware attack will feel pressure to pay the ransom in order to avoid damage. However, paying makes little difference in recovering data when it comes to cost and time, and it is not recommended to pay attackers the ransom. Instead, organizations should utilize the mitigation techniques and services offered by cyber intelligence professionals before paying a ransom that could financially cripple their business.
Avertium's Case Study
Avertium has services that will help any organization prevent or mitigate a ransomware attack like Conti. We once had a customer who ran a legacy SIEM appliance and subscribed to our managed security services to monitor a portion of its environment. However, over time, the company outgrew the SIEM’s capabilities, and the expansion of endpoints created a “Wild West” of unmonitored vulnerability. The customer was put at risk, so Avertium recommended that the customer upgrade to LogRhythm for more advanced alerting and to expand the breadth of protection across all networks, including endpoints.
Unfortunately, the customer didn’t take our advice due to cost and lack of internal resources to focus on the project. As a result, the customer became a victim of a ransomware attack via a compromised email that gained access through the company’s endpoints and was rapidly spreading through an unmonitored area of the network.
Avertium sprang into action and immediately upgraded the customer’s Sophos antivirus software to InterceptX+EDR endpoint protection. Our services combined with our human expertise allowed us to stop and clean up the ransomware. We were also able to evict the threat actor from the victim’s network. The customer recognized their error in judgment and hired a professional to build on the security program foundation Avertium began. If you ever find yourself in a similar situation, we can do the same for you. Hopefully, you choose prevention and take advantage of our XDR Services now, so you don’t need DFIR services later.
avertium's recommendations
- Avertium offers vulnerability management as a service (VMaaS) to remove any unnecessary applications and implementing XDR tools to prevent ransomware and phishing attacks.
- It’s also recommended by Avertium and the FBI that your business require multi-factor authentication to remotely access networks. Implementing network segmentation and filtering network traffic to stop phishing emails from reaching victims is also helpful.
- Recommendations from Avertium and our partner, Advanced Intelligence:
- Conti uses developed social engineering techniques to lure victims. Avertium offers user awareness training with KnowBe4.
- Due to Conti using corporate VPN compromise and TrickBot delivery as an alternative for attack initiation, it’s wise to track externally exposed endpoints.
- Prevent lateral movement by implementing network hierarchy protocols with network segregation and decentralization.
- Use whitelisting tools to audit or block command-line interpreters (AppLocker).
- Rclone and other data exfiltration command-line interface activities can be captured through correct logging of process execution with command-line arguments.
- Have security protocol in place for Veeam to avoid account takeover. Enabled backups decrease Conti’s ransom demands and can lead to data recovery without you having to pay them.
Indicators of Compromise (IoCs):
- fb49dce92f9a028a1da3045f705a574f3c1997fe947e2c69699b17f07e5a552b
- 23.106.160[.]77
- 23.106.215[.]61
- 23.82.19[.]173
- Gojihu[.com]
- Sazoya[.com]
- Yawero[.com]
- Conti uses remote access tools that beacon to domestic and international VPS infrastructure over ports 80, 443, 8080, and 8443.
- Conti may use port 53 for persistence.
- New accounts and tools (especially Sysinternals) that were not installed by your organization.
- Disabled endpoint detection and constant HTTP and DNS beacons.
MITRE TTPs:
- [T1566] Spearphishing Campaigns
- Cobalt Strike
- TrickBot
- Emotet
- [T1212] Exploitation for Credential Access
- ProxyShell
- [T1133] External Remote Services
- Altera
- [T1210] Exploitation of Remote Services
- Altera
- PrintNightmare
- [T1589] Gather Victim Identity Information
- Mimikatz
- [T1041] Exfiltration Over C2 Channel
- Cobalt Strike
Terms
RaaS (Ransomware as a Service) – A malicious organization or vendor offers other threat agents, including hackers and state-sponsored attackers, a proven ransomware tool that can be used to launch attacks against chosen victims. Successful attacks result in the seizure or encryption of target files, information, or systems, which are held for ransom: The victim is told to pay up or lose access forever.
TrickBot – An advanced Trojan spread by way of spearphishing campaigns – campaigns contain malicious links attachments, etc. that execute malware. TrickBot can also be used to drop other malware, like Conti ransomware.
Dynamic-link libraries (DLL) – A module containing functions and data that can be used by another module (application or DLL).
Mimikatz – open-source application that allows users to view and save credentials.
Supporting Documentation
Paying the Ransom Can Double Ransomware Attack Recovery Costs (healthitsecurity.com)
Dynamic-Link Libraries (Dynamic-Link Libraries) - Win32 apps | Microsoft Docs
Backup “Removal” Solutions - From Conti Ransomware With Love (advintel.io)
Wizard Spider Modifies and Expands Toolset [Adversary Update] (crowdstrike.com)
Conti ransomware gang is targeting unpatched Microsoft Exchange servers - SiliconANGLE
Conti Ransomware - AlienVault - Open Threat Exchange
Operation Exchange Marauder: Mass exploitation of Microsoft Exchange (avertium.com)
Microsoft Exchange Server Breach is Formally Attributed to China by the U.S (avertium.com)
APPENDIX II: Disclaimer
This document and its contents do not constitute and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of the Client's compliance with any law, regulation, or standard.