- WHY AVERTIUM?
-
-
Why Avertium?
Context over chaos. Disconnected technologies, siloed data, and reactive processes can only get you so far. Protecting businesses in today’s threat landscape demands more than a set of security tools – it requires context.
That's where Avertium comes in
-
Considering Microsoft?
Avertium Named Microsoft Security Solutions PartnerAvertium’s managed services for Microsoft Security Solutions is delivered through the company’s premium service: Fusion MXDR. Fusion MXDR includes 24x7 monitoring and management of Defender for Endpoint and Sentinel, threat intelligence, attack surface
monitoring, and vulnerability management for Microsoft Security customers. -
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- SOLUTIONS
-
-
Governance, Risk, + Compliance
GRC with context – not complexity. -
Attack Surface Management
No more blind spots, weak links, or fire drills. -
Threat Detection + Response
Detect, adapt, and attack with context. -
Microsoft Security Solutions
End-to-end support from strategy to daily operations to maximize your Microsoft Security.
-
-
- COMPANY
-
-
About Us
Security. It’s in our DNA. It’s elemental, foundational. Something that an always-on, everything’s-IoT-connected world depends on.
Helping mid-to-enterprise organizations protect assets and manage risk is our only business. Our mission is to make our customers’ world a safer place so that they may thrive in an always-on, connected world.
-
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- PARTNERS
-
-
Our Partners
Best-in-class technology from our partners... backed by service excellence from Avertium.
-
Partner Opportunity Registration
Interested in becoming a partner?
With Avertium's deal registration, partners can efficiently and confidently connect with Avertium on opportunities to protect your deals.
-
Latest Avertium Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- NEWS & RESOURCES
-
-
News & Resources
Dive into our resource hub and explore top
cybersecurity topics along with what we do
and what we can do for you. -
Latest Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- CONTACT
Email Phishing Campaigns (Beware Of These Scams)
TIR-20210816 Executive Summary
Phishing attacks / email scams are a tried-and-true method for retrieving data, but certain campaigns can be difficult to filter. Two campaigns that come to mind are Photo Copyright and SharePoint phishing campaigns. Not only do these campaigns wreak havoc on their victim’s devices and networks, but they are becoming exceptionally clever as time progresses. Let’s look at the similarities between Photo Copyright phishing campaigns and SharePoint phishing campaigns:
- Both campaigns ask you to click a link that leads you to download a file that does not exist.
- Both campaigns pretend to be hosted on sharing platforms.
- Both campaigns can steal your information for malicious use at later times, and both can infect your computer with malware.
- Both campaigns target a specific audience using social engineering.
- Photo Copyright phishing campaigns typically target website owners.
- Microsoft SharePoint phishing campaigns typically target people who work remotely.
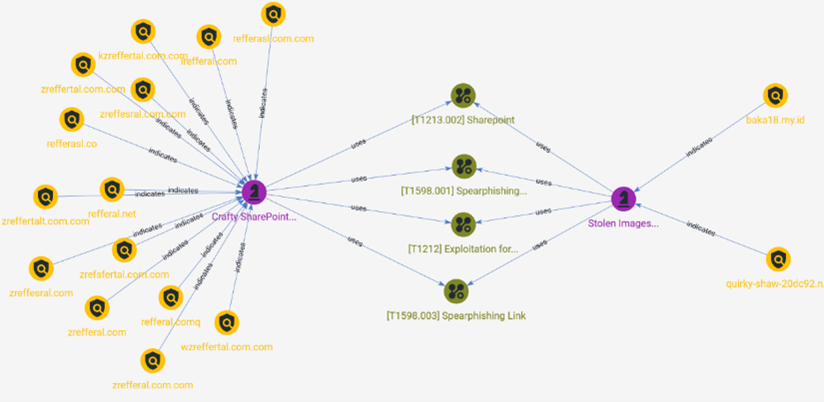
Photo Copyright Phishing Campaigns
While phishing email attacks are common, the variations of these attacks are constantly evolving. One of the latest attacks involves a phishing email campaign that threatens to take legal action against you for using copyrighted images without consent. Attackers make these threats by sending a suspicious email to your email account, masquerading as a professional or licensed photographer with the “links” to the stolen images and a note to download a document with further proof that their images were stolen. It all seems quite convincing until you click on the link(s) and download a malicious JavaScript file.
What makes this scheme even more convincing is that the downloaded malicious files appear as if they’re hosted on Google Drive or Share Point. Once the files are downloaded, attackers can take control of your computer and hold it ransom, spy on your activity, and they could have access to important information security (bank accounts, email, contacts, etc.).
These photo copyright phishing emails tend to look extremely threatening and usually have awkward grammar. The attacker will even quote U.S Copyright statutes to make the letter sound more professional, like this letter that was posted on Sangfroidwebdesign.com.
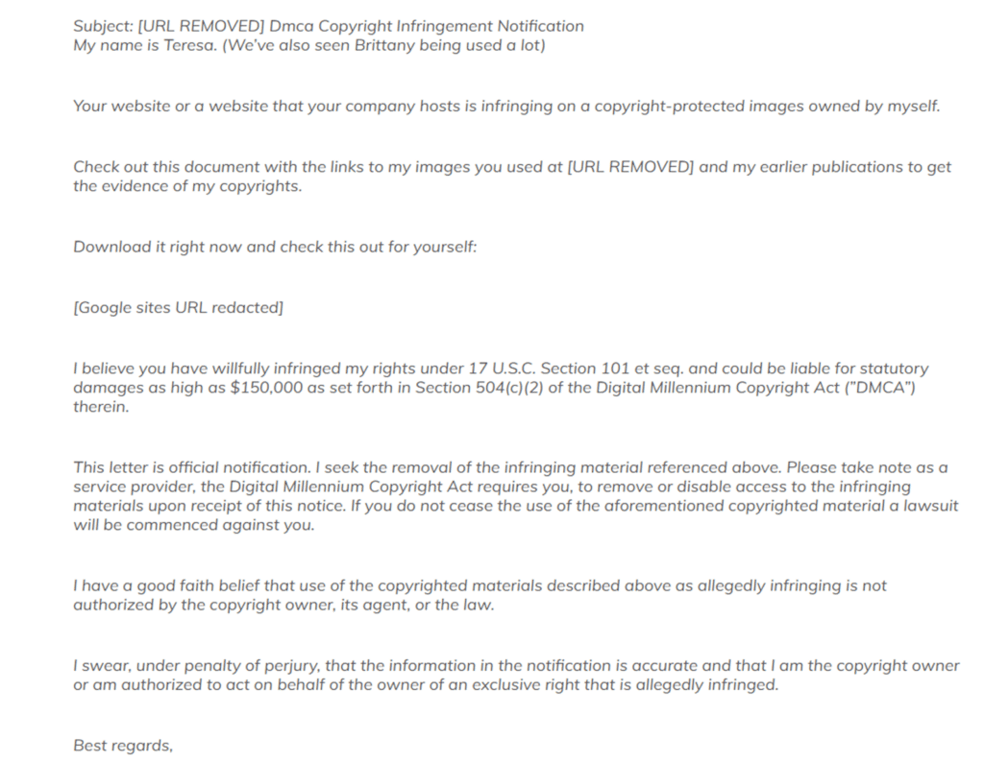
Don’t be fooled by the convincing language. Clicking on any link in an email with these characteristics could lead to compromising important information stored on your computer.
Indicators of Compromise (IoC’s) for Photo Copyright Phishing:
- quirky-shaw-20dc92[.]netlify[.]app
- baka18[dot]my[dot]id
Spoofed Microsoft SharePoint Phishing Campaign
In July 2021, another email phishing campaign was reported Microsoft. This campaign uses spoofed original sender email addresses and display sender addresses containing top-level domains to target organizations who use Office 365. The phishing attack also uses “Microsoft SharePoint” in spoofed display names to lure victims to click on “file share” requests titled “bonuses, price books, and staff reports – all valid requests, if they came from a legitimate source.
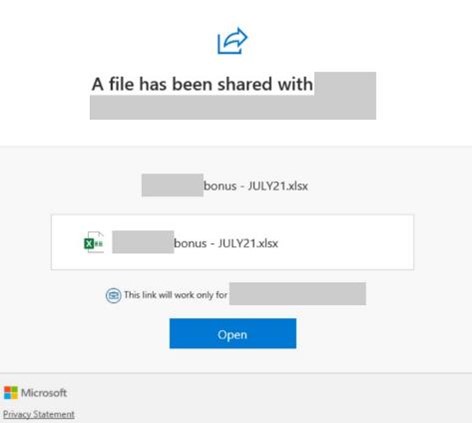
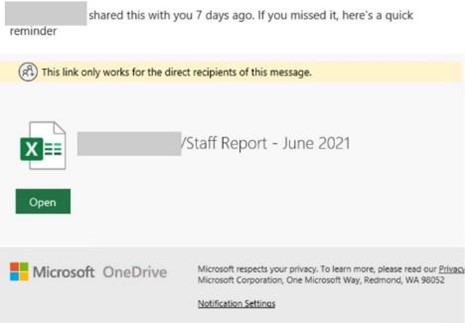
The goal is to get unsuspecting users of these platforms to click on phishing URLs that require them to sign-in to what they think is their file sharing platform, but it’s a phishing page with bogus Microsoft branding.
According to the Microsoft Security Intelligence team, the phishing emails contain two URLs with malformed HTTP headers, with the first one being a Google storage resource directing victims to an AppSpot domain. After requiring the user to sign-in, they are taken to another Google User Content domain with an Office 365 phishing page. The second URL is in the notification settings and links back to a compromised SharePoint.
Unfortunately, July 2021 was not the first time there was malicious activity concerning SharePoint. Avanan, a software company that catches advanced email attacks, detected a phishing email scam in August 2018. The email included an embedded link which led to a SharePoint file posing as an access request to a OneDrive file. After clicking on the link, victims were directed to a landing page designed to steal their Office 365 credentials. Over a year later, Naked Security, Cofense, and PhisLabs detected similar phishing email campaigns designed to steal Office 365 credentials.
The reason why the attackers can go undetected for so long and slip past endpoint security software, is because they change the encoding mechanisms using different methods for each segment, switching between plaintext HTML code, escaping, Base64, ASCII, chars, and yes, even Morse code. The phishing email campaign is also known to use Google and Digital Ocean to host their phishing pages.
Indicators of Compromise (IoC’s) for SharePoint Phishing:
- ‘zreffertalt.com.com’
- ‘zreffesral.com.com’
- ‘kzreffertal.com.com’
- ‘wzreffertal.com.com’
- ‘refferal.comq’
- ‘refferal.net’
- ‘zreffertal.com.com’
- ‘zrefferal.com.com’
- ‘refferasl.com.com’
- ‘zreffesral.com’
- ‘zrefsfertal.com.com’
- ‘irefferal.com’
- ‘refferasl.co’
- ‘zrefferal.com’
- xls.HTML
- xslx.HTML
- Xls.html
- .XLS.html
- xls.htML
- xls.HtMl
- xls.htM
- xsl_x.h_T_M_L
- .xls.html
- ._xslx.hTML
- ._xsl_x.hTML
Avertium’s Recommendations
- Photo Copyright Phishing
- Have a layered approach to email security by consistently sending phishing simulations designed to evaluate an employee’s familiarity with email phishing attacks.
- Use role-based training to familiarize employees with digital threats.
- Keep employees aware of where photos and their origin in relation to the company. For example, are they the property of the company or have they been issued to the company by a licensed photographer?
- SharePoint Phishing
- Keep track of typo-squatted domains and contain disabled attachments that originate from outside of your organization.
- Inventory all authorized hardware and software.
- Photo Copyright Phishing & SharePoint Phishing
- Install phishing filters in your email application
- Make it easy for employees to report potential phishing emails
- Do not click on links or open attachments in suspicious emails
- Institute mandatory phishing awareness training for all employees.
Sources
MITRE TTPs
[T1598.001] Spear phishing Service
[T1598.003] Spear phishing Link
[T1213.002] SharePoint
[T1212] Exploitation for Credential Access
Supporting Documentation
https://twitter.com/MsftSecIntel/status/1421232634357714947
https://www.zdnet.com/article/microsoft-watch-out-for-this-sneakier-than-usual-phishing-attack/
https://securityintelligence.com/news/sharepoint-phishing-attacks/
https://www.avertium.com/flash-notice-avertium-detects-increase-in-stolen-images-phishing-campaign/
https://thehackernews.com/2021/08/hackers-spotted-using-morse-code-in.html
https://attack.mitre.org/techniques/T1598/003/
https://attack.mitre.org/techniques/T1598/001/
https://attack.mitre.org/techniques/T1213/002/
https://attack.mitre.org/techniques/T1212/
Note: The Avertium Threat Report analyzes one current threat that has been shared by threat intelligence networks across the globe. Used internally by the Avertium CyberOps Team, this report will outline a “top-of-mind” threat and how it ought to be addressed accordingly.
This informed analysis is based on the latest data available.