- ABOUT
-
-
About Us
Security. It’s in our DNA. It’s elemental, foundational. Something that an always-on, everything’s-IoT-connected world depends on.
Helping mid-to-enterprise organizations protect assets and manage risk is our only business. Our mission is to make our customers’ world a safer place so that they may thrive in an always-on, connected world.
-
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- SOLUTIONS
-
-
Governance, Risk & Compliance
GRC with context – not complexity. -
Attack Surface Management
No more blind spots, weak links, or fire drills. -
Managed XDR & SecOps
Detect, adapt, and attack with context. -
Microsoft Security Solutions
End-to-end support from strategy to daily operations to maximize your Microsoft Security.
-
-
- PARTNERS
-
-
Our Partners
Best-in-class technology from our partners... backed by service excellence from Avertium.
-
Partner Opportunity Registration
Interested in becoming a partner?
With Avertium's deal registration, partners can efficiently and confidently connect with Avertium on opportunities to protect your deals.
-
Latest Avertium Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- NEWS & RESOURCES
-
-
News & Resources
Dive into our resource hub and explore top
cybersecurity topics along with what we do
and what we can do for you. -
Latest Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- CONTACT
Ransomware Vs. Phishing Vs. Malware (What's The Difference)
Avertium is kicking off October, Cybersecurity Awareness Month, by providing clarity on an often-confused topic: What is the difference between malware, ransomware, and phishing attacks? It's a great question, so let's dive in.
Malware, ransomware, and phishing attacks are nothing new to enterprise and small business cybersecurity teams. With total annual losses in the trillions of dollars, there's no hiding from their impact: Organizations are continually being challenged to protect themselves against threats that are multiplying and evolving faster than ever.
Here are the basics you need to know about these persistent and increasingly sophisticated forms of a cyberattack:
What is Ransomware?
Ransomware is a specific variety of malware that infects target devices, locks or encrypts files and programs to prevent their use, and demands a ransom from you in return for their release. Fees are typically in the hundreds or low thousands of dollars, to make the ransom more palatable than alternative mitigation and are often demanded in bitcoin.
A malicious link within an email is the most common vector for ransomware. A message may appear to be from a trusted source; however, clicking the link leads you to a site that downloads the attack package.
Ransomware is so lucrative that it has become commoditized. Criminal websites that offer ransomware-as-a-service allow anyone to launch these attacks, with little or no technical knowledge required.
Cybersecurity insurer Coalition reports that ransomware accounts for 41% of reported losses, far ahead of runners-up funds transfer loss (27%) and business email compromise incidents (19%).
Related Reading: How to Leverage Your SIEM to Detect and Respond to Ransomware
How to detect ransomware:
Detecting when you’ve been hit with a ransomware attack is usually pretty straightforward. When you open your computer, you might see a message that looks something like this:
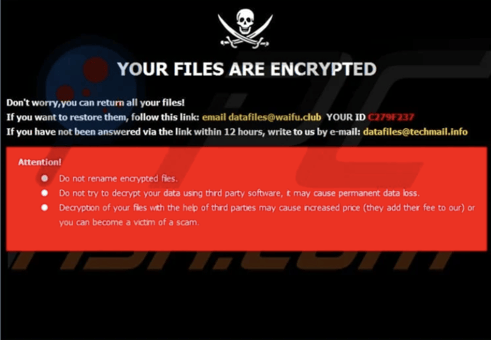
At this point, you’ve already been hit and there’s nothing you can do to go back and stop the attack. But if you know what to look out for, preventing ransomware is entirely realistic and possible for any organization. Here are a few indicators that your systems might be compromised by ransomware:
-
A sudden increase in disk activity accompanied by poor system or application performance: This can signal that there’s a hacker in your system searching for and encrypting files ahead of the attack.
-
New accounts are created with privileged access: Once attackers break into your system, the first thing they’ll want to do is establish persistence and escalate privileges so they can have maximum impact.
-
Suspicious traffic that’s communicating with the command and control servers: Command and control servers connect the internal network with public access, serving as the hackers’ main line of communication.
-
Unauthorized access or changes within security controls and systems: If you see any installations that you don’t recognize, consider it a flashing warning sign that someone else has access to your
-
Scanning of ports inside your network: Hackers use this method to move laterally throughout your network so they can track your most sensitive data.
HOW TO prevent ransomware:
When contending with ransomware, the best offense is a good defense. Antivirus, endpoint detection and response (EDR) tools, and security information and events management (SIEM) tools are designed to work in tandem to detect suspicious activity, alert the appropriate parties, and hopefully, stop a ransomware attack before it’s too late.
One of the easiest ways to shield your organization from a ransomware attack is to train and equip your employees to spot the warning signs. It’s imperative that you develop a clear and effective plan for how you and your employees discover, manage, and recover from a ransomware infection.
Regularly backing up your data is essential in reducing the risk associated with a ransomware attack. If your computers are regularly backed up, it’s more likely you’ll be able to restore your information in the event that a ransomware attack wipes it out.
You should also consider conducting a ransomware readiness assessment – an evaluation tool that allows you to clearly gauge your organization’s preparedness against ransomware infections. By finding and assessing your gaps ahead of time, you can fill them before a hacker finds them too.
What is a Phishing Attack?
Phishing attacks are often a vessel to deliver malware that masquerades as a communication from a trusted or reputable source. This type of cybercrime can come in the form of an email, a phone call (fishing), or a text message (smishing). The most common conduit is through email, with 96% of phishing attacks in 2019 leveraging the tool.
A phishing attack may look or sound like it’s from a company, friend, or family member, even someone within your own organization and contain a request for privileged information, or a link or attachment that results in a malicious download. Common phishing scams seem to come from a bank, credit card company, social media site, or online payment site.
More sophisticated phishing attacks can be a fraudulent invoice, an alert about supposed suspicious activity from your account, a coupon or reward offer, or a fake confirmation notice. Phishing kits allow cybercriminals with limited expertise to spam attacks with authentic-appearing emails or text messages.
The 2019 Verizon Data Breach Investigation Report noted that nearly one-third of all breaches for the reporting period involved phishing.
Related Reading: How to Protect Workers from Increased Phishing Attacks During COVID-19
How to detect a Phishing attack:
Phishing can be both one of the most subtle yet most dangerous attacks on your network. Here are some signs that you’ve been phished:
-
A common indicator of phishing is a request for personal information such as login details, authentication codes, and data such as social security numbers or birthdays. Phishers can pose as brands, friends, family, coworkers, and even complete strangers – whatever it takes to get your personal data and access your accounts.
-
A phishing message can sound like, “You’ve won a prize! Click here.” or “Hey honey, it’s mom – can you send me a quick password?” Neither sound all too sinister, but you should never exchange any personal information or click any suspicious links when you don’t completely trust the source.
How to PREVENT a Phishing attack:
-
You can prevent phishing by turning on a spam filter within your organization’s email network. Spam filters are a valuable tool for separating legitimate emails from trusted sources and those that are delivered with malicious intent.
-
If you receive a link in an email, make sure you hover over the link before clicking on it and check to see if the web address has an “HTTPS” in the URL. HTTPS links are securely encrypted to help you stay safe while browsing the internet. The alternative would be HTTP links which lack the added layer of security you get with an HTTPS link.
As mentioned, prevention is better than any reaction you could have. Install an anti-phishing extension on your computer’s browser so it can scan websites before you visit them, showing you a warning instead of immediately redirecting to the fishy link.
What is Malware?
Malware is an umbrella term, and it's a sizable umbrella: The amalgamation of “malicious” and “software” is used to refer to any intrusive, unwanted software that is designed to compromise, damage, or destroy your computer, device, network, or the data contained within. The most common examples of malware include:
- Viruses
- Worms
- Trojans
- Ransomware
- Fileless malware
- Adware
- Malvertising
- Spyware
Because malware is so broad in its definition and diverse in applications, getting hit by one malware attack can look different from another. A virus might overwrite system files and use your email address book to send copies of itself to new victims. A trojan might hijack your device to assemble an army of bots that conducts DDoS attacks on other targets. Adware might take over the settings on your browser and spam you with full-screen ads, popups, and videos.
CSO Online has an analysis of emerging trends that reveals the global impact of malware, including that 94% of malware is delivered via email.
Related Reading: Using Application Whitelisting to Stop Malware
How to detect MALWARE:
Malware can be evasive and well-disguised, designed to infiltrate and compromise your personal data and networks. However, there are ways you can catch an infection ahead of time.
A general rule of thumb is if your device is suddenly behaving differently, malware might be the reason why. For example, if your battery life dramatically decreases, your device is processing more slowly, or you notice emails you never sent in your inbox, you might have a malware infection. Initially, it may not be obvious that your computer issues are associated with malware, but it’s smart to conduct further investigation to make sure that’s not the case.
Malware detection software is designed to scan your organization’s network both before and after an attack has occurred, helping you stay on the defense while covering your bases if something slips by.
How to PREVENT MALWARE:
-
Only install software from direct links to prevent a malware infection; getting your software right from the source – a trusted source, at that – is the best way to avoid suspicious links and files.
-
You might sometimes see pop-ups on your screen about updates to your device or other network complications – these are usually a sign that a hacker is trying to enter your systems. Avoid clicking any pop-ups and instead, look into the issue yourself to see if there’s any true legitimacy.
-
Regularly scanning your network is a great way to check in and ensure your systems are all clear, helping you both catch and prevent a malware infection.
What do ransomware, phishing, and malware have in common?
There is one thing ransomware, phishing, and malware all have in common: You can avoid the damages of a potential attack. Reduce your risk of attack by taking action to prepare your organization for any malicious intruders. Following the important steps above to detect and prevent ransomware, phishing, and malware ensures the valuable information stored in your networks remains safe.
Learn More About Protecting Your Organization from Common Threats
Damaging malware, ransomware, and phishing attacks are very common, and also avoidable. Your enterprise or small business can limit vulnerability and reduce risk by ensuring systems are updated and patched, implementing regular staff training and making cybersecurity awareness an organizational priority.
Avertium assists organizations with developing and managing resources designed to eliminate risks from malware, ransomware, and phishing attacks. Contact us to learn more about strategies and solutions that improve your security and compliance stance.

Rising Ransomware Attacks, the Advent of XDR, & What it Means for the Future of Threat Detection and Response
Access this webinar-on-demand for a fast-paced virtual panel discussion to learn about these key topics:
- New threat vectors arising from the remote work model
- Technology countermeasures and their limitations
- Traditional MSSP vs MDR vs a whole new approach