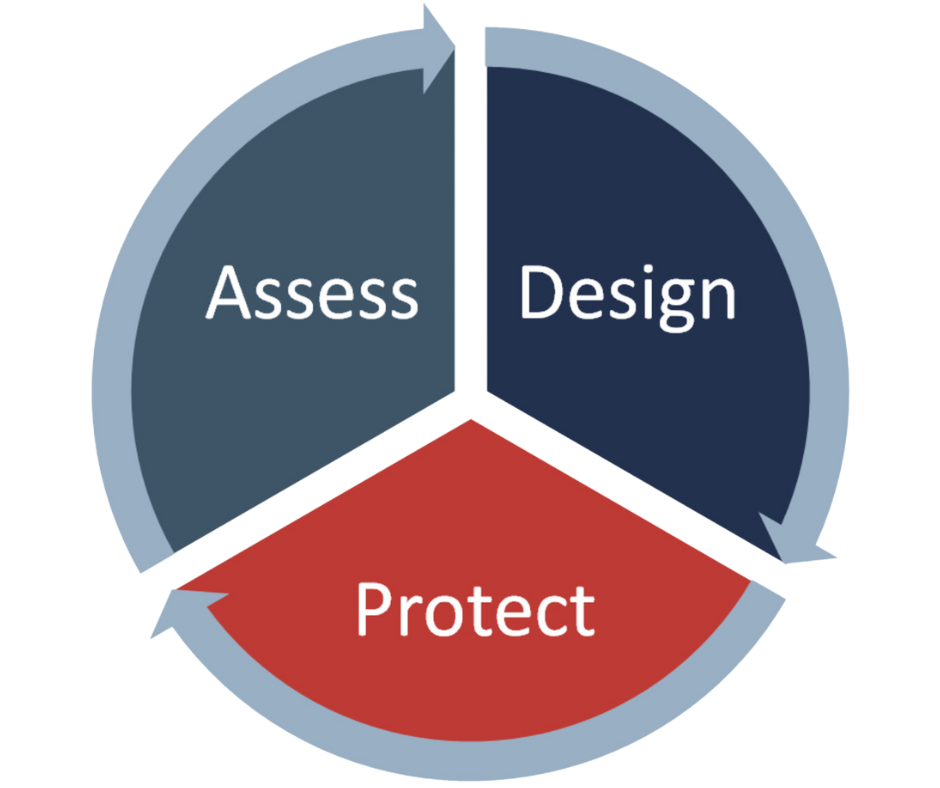
Design
Build a foundation suited for resilience and scale.
Put the plan in action. Design frameworks and implement programs that adapt, scale, and align to your business needs.
Protect
Reinforce security operations with managed services.
Extend programs and investments with co-managed threat detection, automated response, and 24/7 coverage.
Where are you in your security journey?
solutions
Compliance certifications
From healthcare compliance to data privacy and payment security, Avertium provides expert solutions across all major compliance frameworks and standards.
Auditing and compliance frameworks
- SOC 2
- NIST
International standards
- ISO
Security best practices
- CIS
Healthcare compliance
- HIPAA
- HITRUST
Payment security
- PCI DSS
Differentiators
Our managed services offer more than standard out-of-the-box solutions. Combine human expertise with integrated technologies, automations, and streamlined workflows.
Cyber Fusion Centers
Fusion Engine 2.0
Automations & Telemetry
Integrated platforms
An instrumental resource...
"Having a resource to help us stay updated on what's really happening in the industry has been very helpful. It has allowed us to prioritize critical areas effectively, alleviating time constraints faced by our staff."
CAMERON MILLER, IT MANAGER AT SOUTHWEST SERVICE ADMINISTRATORS, INC. | AVERTIUM CUSTOMER
Avertium has the kind of expertise you can rely on...
"We're a unique company, so it's reassuring to have a dependable resource I can turn to when a client request falls outside my expertise. Having an expert to rely on gives me the confidence that I'm providing accurate information and making the right decisions."
JACK BRYANT, IT SERVICES & SUPPORT MANAGER AT NOTARYCAM | AVERTIUM CUSTOMER
We’ve never failed a security audit…
“They have a capable and competent team. They have an acute attention to detail, and they’re never afraid to call it like it is. They usually have their core recs, and then a broader scope of recs that really add a lot of value to things beyond PCI. We’ve never failed a security audit from a customer because of what we’ve established – Avertium has been a huge part of that success.”
MAX GOLDFARB, CISO AT INTERNOVA TRAVEL GROUP | AVERTIUM CUSTOMER
You really can’t put a price on the impact…
“You really can’t put a price on the impact – the value of the working relationship has been phenomenal. And it’s evolving every day.”
JOHN JEFFRIES, CISO AT THE UNIVERSITY OF TENNESSEE MEDICAL CENTER (UTMC) | AVERTIUM CUSTOMER
Take your next step toward adaptive and scalable security and compliance |



























.png?width=500&height=200&name=qcm%20technologies%20logo%20(1).png)
