Healthcare Ransomware Threats - MedusaLocker & Maui
Executive Summary
Ransomware gangs continue to wreak havoc on many sectors, including healthcare. With the goal of financial gain, threat actors deploy ransomware on healthcare organizations’ machines through malicious links, malvertising, and phishing emails. With evolving tactics and techniques, it can be difficult for cyber security professionals to keep up. Not to mention, even the most inexperienced cybercriminal with little technical skill can deploy a ransomware attack.
Hospitals and healthcare organizations across the country become victims of ransomware attacks daily. Outdated software, exposed endpoints, and lack of employee security training make healthcare organizations extremely vulnerable to cyber attacks.
Unfortunately, threat actors know just how vulnerable the healthcare sector has become and they’re taking advantage of every opportunity to attack. Recently, the Federal Bureau of Investigation, Cybersecurity and Infrastructure Security Agency (CISA), the Department of Treasury and the Financial Crime Enforcement Network (FinCEN) issued joint warnings for Maui and MedusaLocker ransomware. Both ransomwares are currently responsible for several cyber attacks within the healthcare sector.
North Korean nation-sate threat actors are believed to be behind Maui ransomware, while MedusaLocker has yet to be attributed to a specific threat actor or group. Let’s take a look at Maui and MedusaLocker’s tactics and techniques, as well as how the healthcare sector can protect themselves from ransomware.

medusalocker
Emerging in 2019, MedusaLocker has infected and encrypted systems across multiple sectors, with specific attention to the healthcare sector. MedusaLocker is a ransomware-as-a-service operation (RaaS) and splits payments with affiliates. The affiliates typically receive 55% to 60% of the proceeds.
RaaS has become more popular and powerful as malware campaigns evolve. It becomes even more powerful when ransomware developers provide their ransomware to third parties (affiliates). In return, the affiliates cause further infections or find potential infection vectors. If an affiliate is accepted into the ransomware operation, they receive monetary compensation after they successfully infect an organization.
During 2019, MedusaLocker took advantage of the chaos surrounding the COVID-19 pandemic and launched phishing and spam email campaigns to gain initial access. As of May 2022, the threat actors behind the ransomware are relying on vulnerabilities in Remote Desktop Protocol (RDP) to gain access to their victim’s networks. After encrypting data, MedusaLocker leaves behind a ransom note with clear instructions in the folders containing an encrypted file. The victims are directed to pay a ransom to a specific Bitcoin wallet address.
Tactics & Techniques
To gain access to victim’s networks, MedusaLocker uses phishing and spam email campaigns, attaching the ransomware directly to the email. To avoid security tools, MedusaLocker restarts the targeted machine in safe mode before execution – avoiding encrypting executable files. Avoiding the executable files is more than likely done to avoid rendering the system unusable for paying the ransom.
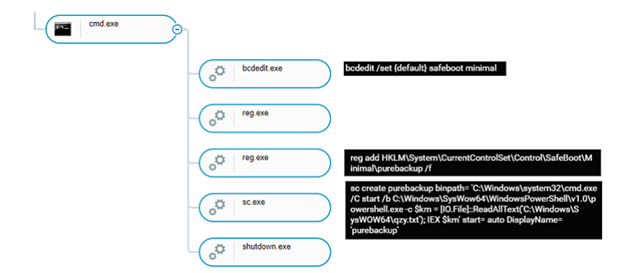
MedusaLocker’s infections start with two files: qzy.bat and qzy.txt. The qzy.bat file is a batch file, while the qzy.txt is a PowerShell script. According to Cybereason, the batch file creates persistence via a Windows Service. The Windows Service does the following:
- Executes a PowerShell script that contains the ransomware payload.
- Allows the service to run in safe mode by changing the registry keys.
- Forces the machine to restart in safe mode.
- Restarts the infected machine
Image 1: MedusaLocker Batch File
Source: Cybereason
Once the machine restarts, the PowerShell script runs and the created service executes. Before deploying, MedusaLocker checks to see if the following mutex exists on their targeted machine: “{8761ABBD-7F85-42EE-B272-A76179687C63}”. If the mutex is present MedusaLocker will stop its execution. MedusaLocker achieves privilege escalation by using a UAC bypass technique. This technique allows the ransomware to run with escalated privileges, enabling it to carry out administrative operations. Persistence is created by “svhost” – a scheduled task that executes every 15 minutes.
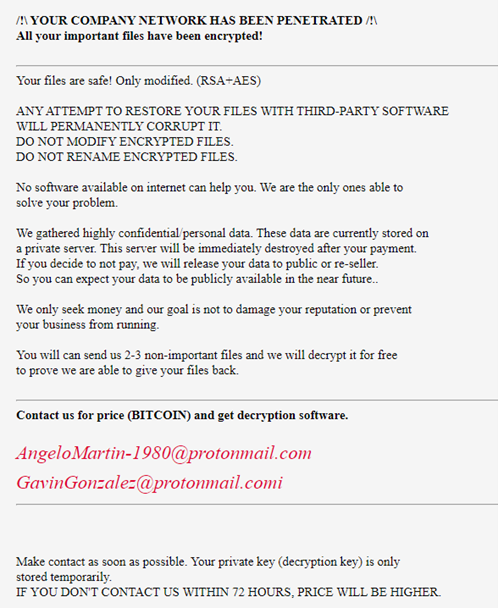
MedusaLocker is known for deleting backups and preventing organizations from recovering any data after infection. By deleting backups, organizations feel as if they are forced to pay the ransom, feeling as if they have no other options. Additionally, a variant of MedusaLocker called AKO, was seen blackmailing victims, threatening to release sensitive data – a method that has gained popularity amongst ransomware gangs. These kinds of threats have also been found in some of MedusaLocker’s ransom notes. MedusaLocker’s ransom demands appear to depend on the victim’s financial status.
Image 2: A MedusaLocker Ransom Note
Source: Cybereason
maui ransomware
As we stated previously, North Korean state-sponsored threat actors are believed to be behind Maui ransomware. According to CISA, the FBI observed and responded to several cyber security incidents within the healthcare sector due to Maui. The incidents included the encryption of servers responsible for providing healthcare services (diagnostic services, imaging services, intranet services, etc.).
Previous Attacks
While CISA recently released a warning about Maui, the ransomware has been infecting servers since May 2021. During that time, Maui infected the servers of a medical center in the District of Kansas. The threat actors ended up receiving $100,000 in Bitcoin to decrypt and recover encrypted files. The medical center notified the FBI and they were able to trace the medical center’s payment to China-based money launderers.
As of 2022, the threat actors behind Maui are still attacking the healthcare sector. In April 2022, one of their seized cryptocurrency accounts received a $120,000 payment. The account was identified by the Kansas medical center and the payment was confirmed to be related to a different medical center located in Colorado. The two cryptocurrency accounts belonging to the Maui ransomware operators were seized by the FBI in May 2022. By working with law enforcement, both health care facilities were able to recover their funds.
Tactics & Techniques
According to CISA, North Korean state-sponsored threat actors have been deploying Maui ransomware within the healthcare sector since May 2021. Some of the incidents disrupted operations and services provided by the targeted healthcare organizations.
The initial points of access for the attacks are unknown, but Stairwell’s Threat Report on the ransomware shows that Maui is an encryption binary (maui.exe) and was designed for manual encryption – allowing the threat actors to pick and choose their targets. Most ransomware variants mass deploy psexec, a group policy object, or an inactive Directory. The operators behind Maui are clearly more targeted in their approach and are more selective about the files they encrypt.
According to Stairwell, Maui doesn’t rely on external infrastructure to receive encryption keys. Instead, the ransomware creates three files in the same directory it was executed from (unless a custom log directory is passed using the -p command line argument) containing the results of its execution. It’s likely that the files are exfiltrated by the ransomware operators and processed via private tooling to generate associated decryption tooling.
As we stated, Maui has a targeted approach and evidence of this can be seen in the decompiled code of the programs. In the below function call taken from IDA Pro, are the usage options for running this program via command prompt. It appears that the path of the file or folder to be encrypted is required, while the other switching options are not. These options allow for changing the log folder destination from the default current directory, also the thread count to be changed (default 1), and an option to “self melt” (default no).
Image 3: Maui Ransomware Function Call
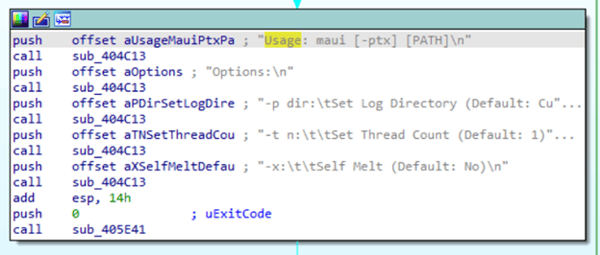
Source: Avertium's Cyber Threat Intelligence Team
Also, there was another option that wasn’t seen during the initial CLI message regarding program usage. The option allows the threat actor to append the public key information in the event of a read error.
Image 4: Threat Actor Appending Public Key
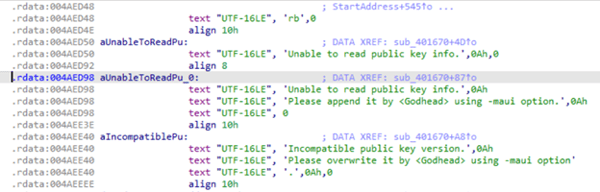
Source: Avertium's Cyber Threat Intelligence Team
Every file encrypted by Maui contains a customer header, which allows the ransomware to programmatically identify already encrypted files. The files original path and an encrypted copy of the AES key can be found in the header. While encrypting files, Maui outputs status information back to the ransomware operators.
ransomware & the healthcare sector
In October 2021, Avertium published a Threat Intelligence Report regarding the top 5 cyber threats in the healthcare sector. Ransomware ranked as the most common attack vector for the sector. Between July 1 and September 30, 2021, researchers found 68 healthcare ransomware attacks globally. The United States was home to 60 percent of those attacks, with France, Brazil, Thailand, Australia, and Italy following. Medical clinics are the most frequently attacked sub-industry for ransomware attacks, with several ransomware gangs taking center stage (DoppelPaymer, Pysa, CLoP, Groove, etc.).
We can now add MedusaLocker and Maui ransomware to the long list of ransomware threatening to disrupt the healthcare sector. Some ransomware gangs choose not to focus on attacking critical infrastructure like healthcare. However, a lot of ransomware gangs are pushing what little moral compass they have to the side and are happy to attack the sector if it means a big pay day.
In 2019, Springhill Medical Center was attacked by a ransomware gang and that attack led to a baby’s death. The baby was born with its umbilical cord wrapped around his neck, depriving him of oxygen during delivery. A heartrate monitor usually detects and informs hospital staff of life-threatening situations, but the monitor never alerted staff due to its system being compromised by a ransomware attack.
The doctor delivering the baby stated that she would have delivered her via cesarean section had she been able to see the heart monitor’s readout. She stated that the situation was preventable. As a result, the baby was born with severe brain damage and died nine months later. The hospital had to defend themselves in a trial related to the attack in September 2021. Ryuk was suspected to be behind the attack, but that has yet to be confirmed.
From the instances in this report, it’s evident that ransomware is a major threat to the healthcare sector, yet the sector still is not implementing security best practices. Ransomware attacks within the healthcare sector will not only cost organizations funds, but they can and have cost people their lives. Following basic cyber security best practices could save a life and keep finances safe:
- Secure connected medical devices – if a medical device is connected to the internet in any way, then it is an end point for an attacker. Require clinicians to insert a username and password prior to utilizing a connected medical device.
- Apply strong passwords – passwords prevent cyber criminals from gaining unauthorized access to your healthcare organization’s network. Implementing multifactor authentication (MFA) in addition to a strong password of eight characters or more will make it extremely difficult for a threat actor to break in.
- Fortify your network – phishing and malware are used by cyber criminals to obtain patient healthcare information. Safeguard your network from untrusted users by securing applications and web portals.
- Train your staff – employees should be trained regularly on cyber security best practices to help protect healthcare organizations. Most healthcare breaches are due to employee negligence.
How Avertium is Protecting Our CUSTOMERS
It’s important to get ahead of the curve by being proactive with protecting your organization, instead of waiting to put out a massive fire. Avertium offers the following services to keep your organization safe:
- Avertium offers user awareness training through KnowBe4. The service also Incident Response Table-Top exercises (IR TTX) and Core Security Document development, as well as a comprehensive new-school approach that integrates baseline testing using mock attacks.
- Avertium offers VMaaS to provide a deeper understanding and control over organizational information security risks. If your enterprise is facing challenges with the scope, resources, or skills required to implement a vulnerability management program with your team, outsourced solutions can help you bridge the gap
- Fusion MXDR is the first MDR offering that fuses together all aspects of security operations into a living, breathing, threat-resistant XDR solution. By fusing insights from threat intelligence, security assessments, and vulnerability management into our MDR approach, Fusion MXDR offers a more informed, robust, and cost-effective approach to cybersecurity – one that is great than the sum of its parts.
- Avertium offers Zero Trust Architecture, like AppGate, to stop malware lateral movement.
- Minimizing the impact of a successful ransomware attack requires detecting it as early in the attack as possible. A Security Information and Event Management (SIEM) system can help an organization to accomplish this. Avertium offers a comprehensive SIEM-based approach that increases the potential for detecting a ransomware infection before it deploys. SIEM provides a holistic overview of a company’s IT environment from a single point of view in terms of its specific security events, empowering teams to detect and analyze unusual behavior.
Avertium’s Recommendations
Avertium and CISA recommend the following for MedusaLocker ransomware:
- Implement a recovery plan that maintains and retains multiple copies of sensitive or proprietary data and servers in a physically separate, segmented, and secure location (i.e., hard drive, storage device, or the cloud).
- Implement network segmentation and maintain offline backups of data to ensure limited interruption to the organization.
- Regularly back up data and password protect backup copies stored offline. Ensure copies of critical data are not accessible for modification or deletion from the system where the data resides.
- Install, regularly update, and enable real time detection for antivirus software on all hosts.
- Install updates for operating systems, software, and firmware as soon as possible.
- Review domain controllers, servers, workstations, and active directories for new and/or unrecognized accounts.
- Audit user accounts with administrative privileges and configure access controls according to the principle of least privilege.
- Disable unused ports.
- Consider adding an email banner to emails received from outside your organization.
- Disable hyperlinks in received emails.
- Enforce multifactor authentication (MFA).
- Only use secure networks; avoid using public Wi-Fi networks.
- Consider installing and using a virtual private network (VPN) to establish secure remote connections.
- Focus on cybersecurity awareness and training. Regularly provide users with training on information security principles and techniques as well as overall emerging cybersecurity risks and vulnerabilities, such as ransomware and phishing scams.
Avertium and CISA recommend the following for Maui ransomware:
- Limit access to data by deploying public key infrastructure and digital certificates to authenticate connections with the network, Internet of Things (IoT) medical devices, and the electronic health record system, as well as to ensure data packages are not manipulated while in transit from man-in-the-middle attacks.
- Use standard user accounts on internal systems instead of administrative accounts, which allow for overarching administrative system privileges and do not ensure least privilege.
- Turn off network device management interfaces such as Telnet, SSH, Winbox, and HTTP for wide area networks (WANs) and secure with strong passwords and encryption when enabled.
- Secure personal identifiable information (PII)/patient health information (PHI) at collection points and encrypt the data at rest and in transit by using technologies such as Transport Layer Security (TPS). Only store personal patient data on internal systems that are protected by firewalls, and ensure extensive backups are available if data is ever compromised.
- Protect stored data by masking the permanent account number (PAN) when it is displayed and rendering it unreadable when it is stored—through cryptography, for example.
- Secure the collection, storage, and processing practices for PII and PHI, per regulations such as the Health Insurance Portability and Accountability Act of 1996 (HIPAA). Implementing HIPAA security measures can prevent the introduction of malware on the system.
- Implement and enforce multi-layer network segmentation with the most critical communications and data resting on the most secure and reliable layer.
- Use monitoring tools to observe whether IoT devices are behaving erratically due to a compromise.
- Create and regularly review internal policies that regulate the collection, storage, access, and monitoring of PII/PHI.
MITRE Map
MedusaLocker
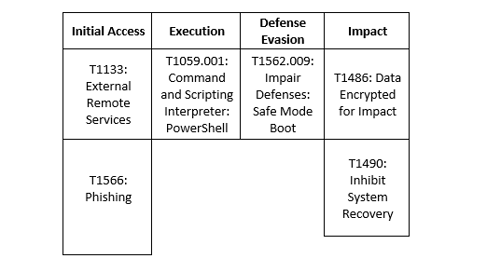
Maui
Indicators of Compromise (IoCs)
MedusaLocker
Hashes

IP Addresses

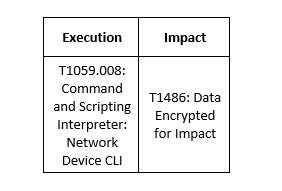
Maui
Hashes
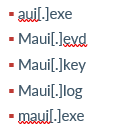
File Names
Supporting Documentation
North Korea Attacks Health Sector With Maui Ransomware (govtech.com)
Cybereason vs. MedusaLocker Ransomware
FBI seized $500K worth of bitcoin obtained from Maui ransomware attacksSecurity Affairs
MedusaLocker Ransomware - AlienVault - Open Threat Exchange
Ransomware: In the Healthcare Sector (cisecurity.org)
Report: Maui ransomware (stairwell.com)
Cybersecurity Best Practices [Checklist] (welchallyn.com)
The Top 5 Cyber Threats in the Healthcare Industry (avertium.com)
How Affiliates Use Ransomware as a Service (safeguardcyber.com)
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.
Related Resource: The Top 5 Threats in the Healthcare Industry