- WHY AVERTIUM?
-
-
Why Avertium?
Context over chaos. Disconnected technologies, siloed data, and reactive processes can only get you so far. Protecting businesses in today’s threat landscape demands more than a set of security tools – it requires context.
That's where Avertium comes in
-
Considering Microsoft?
Avertium Named Microsoft Security Solutions PartnerAvertium’s managed services for Microsoft Security Solutions is delivered through the company’s premium service: Fusion MXDR. Fusion MXDR includes 24x7 monitoring and management of Defender for Endpoint and Sentinel, threat intelligence, attack surface
monitoring, and vulnerability management for Microsoft Security customers. -
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- SOLUTIONS
-
-
Governance, Risk, + Compliance
GRC with context – not complexity. -
Attack Surface Management
No more blind spots, weak links, or fire drills. -
Threat Detection + Response
Detect, adapt, and attack with context. -
Microsoft Security Solutions
End-to-end support from strategy to daily operations to maximize your Microsoft Security.
-
-
- COMPANY
-
-
About Us
Security. It’s in our DNA. It’s elemental, foundational. Something that an always-on, everything’s-IoT-connected world depends on.
Helping mid-to-enterprise organizations protect assets and manage risk is our only business. Our mission is to make our customers’ world a safer place so that they may thrive in an always-on, connected world.
-
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- PARTNERS
-
-
Our Partners
Best-in-class technology from our partners... backed by service excellence from Avertium.
-
Partner Opportunity Registration
Interested in becoming a partner?
With Avertium's deal registration, partners can efficiently and confidently connect with Avertium on opportunities to protect your deals.
-
Latest Avertium Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- NEWS & RESOURCES
-
-
News & Resources
Dive into our resource hub and explore top
cybersecurity topics along with what we do
and what we can do for you. -
Latest Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- CONTACT
The Top 5 Cyber Threats in the Healthcare Industry
Executive Summary of cyber threats in the healthcare industry
The healthcare sector should be the last industry cyber criminals attack, but no exceptions are made when threat actors are looking to make money. Lately, the healthcare industry has seen an uptick in attacks and there are five attack vectors that are of major concern. From medical clinics to hospitals, there appears to be no sign of attacks slowing down within healthcare. Let’s look at the top 5 most common types of cyber threats in the healthcare industry.
ransomware
When it comes to healthcare, ransomware is the most common attack vector for cyber criminals. It’s become such an issue, that the National Health Information and Analysis Center, the Financial Services Information Sharing and Analysis Center, and the Center of Internet Security teamed up to host country-wide trainings on how to defend against ransomware.
Between July 1 and September 30, 2021, researchers found 68 healthcare ransomware attacks globally. The United States was home to 60 percent of those attacks, with France, Brazil, Thailand, Australia, and Italy following. Medical clinics are the most frequently attacked sub-industry for ransomware attacks, with ten ransomware gangs taking center stage.
Top 10 Global Ransomware Gangs for Q3
|
Pysa |
|
AstroLocker |
|
DoppelPaymer |
|
LockBit |
|
Hive |
|
Ragnarok |
|
CLoP |
|
Ryuk |
|
Groove |
|
Vice Society |
While some ransomware gangs try not to focus on attacking healthcare facilities, the Hive ransomware gang intentionally attacks the industry. In September 2021, the gang was responsible for attacking four healthcare facilities in the United States. One of the facilities, a medical center in Missouri, was a victim of Hive and had patient information stolen from its servers. After stealing the information, the ransomware gang posted it online – including names, medical information, and Social Security numbers. Hive was also responsible for a ransomware attack against Memorial Health which resulted in emergency room diversions and appointment cancellations.
Hive uses phishing emails to gain access to networks and RDP to navigate the network. Fortunately, the attack didn’t cause care disruptions; however, other healthcare facilities, like Springhill Medical Center are not as fortunate.
In 2019, Springhill Medical Center was attacked by a ransomware gang and that attack led to a baby’s death. The baby was born with its umbilical cord wrapped around his neck, depriving him of oxygen during delivery. A heartrate monitor usually detects and informs hospital staff of life-threatening situations, but the monitor never alerted staff due to its system being compromised by a ransomware attack. The doctor delivering the baby stated that she would have delivered her via cesarean section had she been able to see the heart monitor’s readout. She stated that the situation was preventable. As a result, the baby was born with severe brain damage and died nine months later. The hospital had to defend themselves in a trial related to the attack in September 2021.
The ransomware gang, Ryuk, was suspected of being the culprit due to their track record with attacking medical facilities between 2019 and 2020. The recent healthcare cyber attack they were responsible for was locking up Universal Health Services’ systems for days in September 2020, which resulted in delayed lab results and patients being diverted to other hospitals. However, it is still not confirmed who is to blame for the ransomware attack and whether or not the attackers will be charged with ransomware-related homicide.
business email compromise
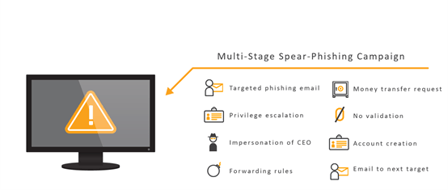
The FBI calls business email compromise (BEC) the “Billion Dollar Scam”. The tactic involves attackers using spoofed emails (spear-phishing emails) or compromised accounts to persuade employees to transfer large sums of money to fraudulent accounts. Typically, the attacker pretends to be someone of authority or power within the medical facility, like the CEO or Vice President. Before sending the spoofed email pretending to be someone from the organization, attackers do thorough research on how the CEO might sound so that victims are more likely to believe their scam. In addition to spear-phishing emails, attackers will also spoof a website or use malware to infiltrate hospital networks to gain access to email chains about billing and invoices.
Image 1: Stages of Spear-Phishing Campaigns
Source: Avertium
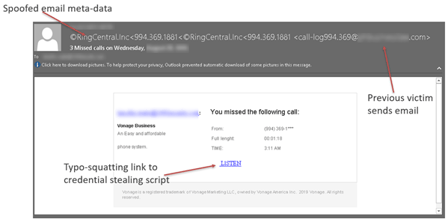
One of the most recent instances we have of a BEC attack is a California hospital that was attacked between December 2020 and April 2021. The attack happened when an employee clicked on a malicious link in their work email, thus opening the door for other email accounts to be compromised. The organization noticed suspicious activity in March 2021 and terminated authorized access to compromised email accounts.
Image 1: Stealing Credentials
Source: Avertium
The attackers allegedly accessed and exfiltrated claims information, dates of birth, lab results, addresses, and other private patient information. The hospital notified patients of the breach in September 2021, but one patient decided to sue the healthcare system for breach of contract, negligence, and violating California consumer privacy and medical confidentiality laws. The patient’s lawyer stated that the breach could have been preventable had the organization trained their employees on how to avoid becoming a victim of phishing attacks.
insider threats
Sometimes, organizations are so enthralled with keeping track of outside threats, that they forget to be conscious of threats within their very own organization. Insiders often have access to systems and networks which puts them in the perfect position to compromise them. They may also have knowledge of vulnerabilities or of the network set up.
Some insiders are just careless, accidentally losing work devices with sensitive information, but others are malicious and intentionally cause devastation to an organization. According to HealthItSecurity.com, the healthcare industry isn’t proactive when it comes to stopping insider data breaches. In a report published by Verizon, researchers found that the healthcare industry was the only industry that had more inside threats(56%) than external threats (43%).
In 2011, a night security guard employed at a Texas hospital built a botnet using the hospital’s network. He recorded himself moving around the hospital, going from desk to desk using a Ophcrack CD and the botnet, which was on a USB flash drive. He used his credentials to gain access to different areas and showed the viewers of his YouTube channel how he removed the hospital’s antivirus software from the system to install the botnet.
After installing the botnet, he showed viewers how he accessed the infected machines remotely. The security guard was part of a hacking group that was using botnet machines to attack other hacking groups, including Anonymous. It wasn’t until an analyst from McGrew Security noticed screenshots of the hospital’s HVAC system online, that the FBI was notified, and the security guard was arrested.
Each year, insider threats are consistently named as the biggest risk to healthcare data. With remote work and telehealth becoming more available, it’s important for healthcare organizations to be proactive with training employees on best cyber security practices, as well as keeping a watchful eye on who they hire.
data breaches
Unfortunately, data breaches are familiar territory for the healthcare industry and the sector experiences more data breaches than any other sector. There are several ways the breaches happen, with the most common being credential-stealing malware, employee negligence, and insider’s disclosing patient data.
Patient data is the most valuable data for attackers to steal. It’s more valuable than credit card information and social security numbers. Credit card information sells for about $1 to $2 on the dark web, while patient data can sell for as much as $363. Because the data is more valuable, cyber criminals have more incentive to attack medical databases. Another factor for cyber criminals looking to reap the rewards of stolen medical data is the weak and outdated systems of healthcare organizations. The industry has been slow to update their cybersecurity technology and they often times have substantial financial resources. Cyber criminals know this and assume money will be easy to collect.
Attackers infiltrate systems through IoT based medical equipment and devices connected to centralized networks. In October 2021, Macquarie Health Corporation, based in New South-Wales, had to take its servers offline to recover from a data breach. The group runs 12 hospitals across Australia and had over 6,700 legal documents containing patient information posted on the dark web.
ddos attacks
In our previous threat report, we discussed DDoS and how the Meris botnet is infecting systems on a global scale, primarily focusing on the technology industry. Did you know that DDoS attacks are popular within the healthcare industry as well? This technique is used by cyber criminals to overwhelm networks, causing a major problem for healthcare systems that need to access their network for proper patient care.
In 2018, Boston Children’s Hospital was attacked by hacktivist group, Anonymous. The group launched a massive DDoS attack against the hospital as retaliation for the hospital’s involvement in a child custody case. The attack disrupted the hospital’s network for two weeks, causing the hospital to lose over $300,000 trying to mitigate the attack. Not only did Anonymous disrupt the hospital’s network, but the attack also caused Harvard University and all of its hospitals to lose internet access as well. DDoS attacks can occur in a variety of ways, but this particular attack is the most common way a healthcare entity could be victimized.
why the healthcare industry is consistently at risk
The healthcare industry is two to three times more likely to be a target for cybercrime than any other industry. Cyber security firm, Herjavec Group, reported that healthcare accounts for 18% of the nation’s gross domestic product (about $3.5 trillion) and they expect it to soar over the next decade. They also predict that global healthcare spending will increase dramatically from $8 trillion in 2013 to more than $18 trillion in 2040.
Most attackers won’t consider patients or vulnerable people when they see an opportunity. As previously stated, healthcare information is the most profitable information to sell on the black market, but there are other reasons why the industry is a constant target for cyber criminals.
Medical devices that are on a network are an easy way for attackers to gain entry. Because the machines are constantly changing and newer version are created every year, those in charge of online security and patient data have a hard time keeping up. The devices are designed for medical reasons, but they aren’t made with security in mind. The devices don’t store data, but they can be used to launch attacks on servers that do store data due to their lack of security.
Remote work and inconvenience are additional reasons why the healthcare industry is at risk for attacks. Medical professionals are often overworked and on time constraints. They may not consider online security to be a priority when their primary role is to save lives. Lack of proper authentication measures for devices and lack of time to devote to ensuring security are issues in this sector that must be addressed. Not wanting to disrupt convenient working practices to implement new technology may end up costing the industry more than time.
avertium's recommendations
Insider threat remediation is expensive and could end up costing the healthcare industry around $10.81 million. DDoS, ransomware, BEC, and data breach attacks put the healthcare industry in devastating situations daily. That’s why it’s important to get ahead of the curve by being proactive with protecting your organization, instead of waiting to put out a massive fire. If you are a member of the healthcare sector and need to implement best practices, take a look at Avertium’s recommendations.
- Avertium's Services
- User awareness training and phishing simulation campaigns using KnowBe4.
- Zero-trust networking as-a-service (ZTNaaS).
- Network and endpoint monitoring and response (XDR).
- Contact your sales representative for more information about DDoS services from our partners.
- Employee Based Security - Train Employees to Develop Better Security Habits
- Create a strong password.
- Consider using a password manager.
- Use multi-factor authentication, if available.
- Use security questions properly.
- Create unique accounts for each user per device.
- Be suspicious of unexpected emails.
- Keep all of your personal electronic device software current.
- Network Based Security Practices
- Use and maintain anti-virus software and a firewall.
- Regularly scan for spyware.
- Keep software up to date.
- Evaluate your software settings.
- Avoid unused software programs.
- Establish guidelines for computer use.
- Encrypt sensitive files.
- Dispose of sensitive information properly.
- Physical Security Practices
- Password-protect all computers.
- Consider using physical locks on devices with sensitive information.
- Consider an alarm or lock.
- Back up your files.
- Implement physical access control plans.
- Conduct background checks as part of the hiring process when hiring someone who will have access to sensitive information.
- Zero Trust Approach
- Verify access of users on each device and include MFA technologies. The extra layer of security could help prevent breaches.
- Verify access of users on each device and include MFA technologies. The extra layer of security could help prevent breaches.
MITRE TTPs:
Ransomware
- [T1598] Phishing for Information
- [T1190] Exploit Public-Facing Application
- [T1562] Impair Defense
- [T1567] Exfiltration Over Web Service
- [T1566] Phishing
- [T1133] External Remote Services
Insider Threats
Data Breaches
- [T1213] Data from Information Repositories
- [T1602] Data from Configuration Repository
- [T1531] Account Access Removal
- [T1486] Data Encrypted for Impact
- [T1485] Data Destruction
Business Email Compromise
- [T1397] Spear-phishing for Information
- [T1598] Phishing for Information
- [T1591] Gather Victim Org Information
- [T1548] Abuse Elevation Control Mechanism
DDoS
- [T1583] Acquire Infrastructure
- [T1595] Active Scanning
- [T1589] Gather Victim Identity Information
- [T1584] Compromise Infrastructure
- [T1583] Resource Development
- [T1498] Network Denial of Service
Indicators of Compromise (IoCs):
Hive Ransomware
- hivecust6vhekztbqgdnkks64ucehqacge3dij3gyrrpdp57zoq3ooqd[.onion]
- http://hivecust6vhekztbqgdnkks64ucehqacge3dij3gyrrpdp57zoq3ooqd[.onion/]
- e1a7ddbf735d5c1cb9097d7614840c00e5c4d5107fa687c0ab2a2ec8948ef84e
- 7202c948aa5af1134efdfe978ec6ef60
- 7a731229659ec9175cfaf1358d0367f2
- f49a50f9867fa2be206aef078d2240f3
- 1cc80ad88a022c429f8285d871f48529c6484734
- 2877b32518445c09418849eb8fb913ed73d7b8fb
- http://hivecust6vhekztbqgdnkks64ucehqacge3dij3gyrrpdp57zoq3ooqd[.onion/]
Pysa
- 14abd57e8eb06191f12c0d84f9c1470b
- 8a2677c671504aa9e7b400778819a92fc9317979
- 190e0ce36c1a63ec976f7e80618c620f75f853a370ea3e602253a98781f4e5c6
- accounting-consult[.xyz]
- englishdialoge[.xyz]
- englishdict[.xyz]
- firefox-search[.xyz]
- wiki-text[.xyz]
- firefox-search[.xyz]
- sbvjhs[.club]
- sbvjhs[.xyz]
AstroLocker
- 14a52f10653ab52dbfa4f84c93d12af3
- 1473cd276e116f53bd88e51405e4afaf
- 0a671d9d7ca62274e5e210813d02d860846baf59188e2a07522cd3a1cc3f9cc0
- 2c44444d207a78da7477ae1af195d4265134e895bebb476f7b2c003f1467a033
- albanallahacrab[.club]
- dclogictrust[.com]
- masskwearing[.cyou]
- felpojdhf8980[.cyou]
- supercombinating[.com]
- 06dd860ae6d69e0b579e22715c8663f2
- 30ff38e859a849b6776dd7b0f299ba83605858f661297f39585bcf928769feef
DoppelPaymer
- 0c6889688b060544205620fe1fdbfa4d
- 3eed5f9a1d57b6ae71a5d434ea38814d
- 41b279fa879354ce8a47970758efe40a
- 72ba727d7441954ecaefd9732d12a36c
- 65cf7f65f443e4bb0e743ccb19105813a12e6eb1
- 8631dc198c7641300b08d17fa8686095f045821a
- ab291a932bcc1c74231a7a7fda74017956927f37
- eeecdd240ae03ffb38445d887418d63bf31bc2bc
- 0864575d4f487e52a1479c61c2c4ad16742d92e16d0c10f5ed2b40506bbc6ca0
- 91e310cf795dabd8c51d1061ac78662c5bf4cfd277c732385a82f181e8c29556
- b21ad8622623ce4bcdbf8c5794ef93e2fb6c46cd202d70dbeb088ea6ca4ff9c8
- b5c188e82a1dad02f71fcb40783cd8b910ba886acee12f7f74c73ed310709cd2
- dda4598f29a033d2ec4f89f4ae687e12b927272462d25ca1b8dec4dc0acb1bec
LockBit
- 15a6d62854e3e7221589b9b6e8e395af
- 1e43127237176bf49f1647140602f190
- 4d25a9242eac26b2240336fb94d62b1e
- 53ec94e3325c7ea427857b0a1e911c66
- 12ac32d012e818c78d6db790f6e11838ca75db88
- 162b08b0b11827cc024e6b2eed5887ec86339baa
- 199d193f31fd7d117070a66e89c4839dddd513b2
- bd14872dd9fdead89fc074fdc5832caea4ceac02983ec41f814278130b3f943e
- bea7aed0dfbf7ce7491d7c8cfed35a2e626fbd345bb7425a34dae6f5894629b1
- http://lockbitsup4yezcd5enk5unncx3zcy7kw6wllyqmiyhvanjj352jayid[.onion]
- lockbitapt6vx57t3eeqjofwgcglmutr3a35nygvokja5uuccip4ykyd[.onion]
- lockbitsap2oaqhcun3syvbqt6n5nzt7fqosc6jdlmsfleu3ka4k2did[.onion]
- lockbitsup4yezcd5enk5unncx3zcy7kw6wllyqmiyhvanjj352jayid[.onion]
Ragnarok
- a30bea3ba2c697013bbda0140e5d42dc1d51304055d81eee26d2be7a2d05483d
- 390eda84632720eb71c5f1d1c0b05ac280a4f67364745a9491476a6d0d9c113b
- e03bb74167a5349f96ff88e5f0ed94f3
- 61a9b3b5320cb4d06155542a25868194
- 83f117bb1cceff7837933a070c5b917f42539b11
- 7a99c3d4e361c97dc2c27e077c4c55e5c47cbe36
- 588c10739ef20be93cb8f0b2de90d23027fbf281
CLoP
- gl-box[.com]
- http://gl-box[.com]
- https://gl-box[.com]
- Jobsafelive[.com]
- co[.nz]
- pcoptimumrewards[.com]
- r0gersverifyaccount[.ca]
- sanpotechservice[.online]
- santat7kpllt6iyvqbr7q4amdv6dzrh6paatvyrzl7ry3zm72zigf4ad[.onion]
- managersmaers@tutanota[.com]
- unlock@gl-box[.com]
- unlock@rsv-box[.com]
- unlock@support-box[.com]
Ryuk
- a5e03a5150537126dffcf2391dfab934
- 9a2155e3b5471ca8321e8c74edb277c9a8e756e0
- 09a0e87008e34a7a434c5d853600f693ab9de181e1f863ef6a90edf8c3fccd54
- 2a380d0c2aa2234c0a37bdaaaa9489ef
- 2cc630e080bb8de5faf9f5ae87f43f8b
- 1efc175983a17bd6c562fe7b054045d6dcb341e5
- eafe0287e6ae983c6f1ff68f6c7780cc3a037783
- f937b1b7b3593a38702f870077658a891974edda
- d6b7b27e13700aaa7f108bf9e76473717a7a1665198e9aafcc2d2227ca11bba9
- d8a0d25776c28e17e724da2b1c8fdae28d7c6b32cfa9d3d2a20f3f57ff370488
Vice Society
- 6f191f598589b7708b1890d56b374b45c6eb41610d34f976f0b4cfde8d5731af
- CVE-2021-34527
- CVE-2021-1675
Terms
DDoS – (Distributed Denial of Service) – takes advantage of capacity limits that apply to any network resources. A DDoS attack sends multiple requests to the compromised web resource, trying to exceed the site’s capacity. This prevents the site from functioning properly.
IoT (Internet of Things) – computer hardware, such as appliances, machines, and sensors. They transmit data over the internet or other networks.
Ransomware – malicious software that infects a device and stops users from accessing data and files until a ransom is paid.
BotNet – – a network of computers infected by malware that are remotely controlled by an attacker.
Spearphishing – attackers use carefully crafted emails to get victims to respond. Research is done prior to sending to better tailor the email for that person.
Ophcrack CD – a windows password cracker.
Supporting Documentation
HC3 Identifies Top 10 Ransomware Threat Actors in Q3 2021 for Healthcare (healthitsecurity.com)
Cl0p Ransomware Contact Domain IP Exposed - Pastebin.com - AlienVault - Open Threat Exchange
Hive Ransomware Continues to Attack Healthcare Providers (healthitsecurity.com)
Ragnarok ransomware IOCs - 16 October 2020 - AlienVault - Open Threat Exchange
Baby's Death Alleged to Be Linked to Ransomware | Threatpost
Ryuk Ransomware Now Targeting Webservers - AlienVault - Open Threat Exchange
IOCs DoppelPaymer - AlienVault - Open Threat Exchange
Ransomware: In the Healthcare Sector (cisecurity.org)
Cyberattacks have become vastly more sophisticated (biopharma-reporter.com)
Business Email Compromise — FBI
Insider Threats: In the Healthcare Sector (cisecurity.org)
Healthcare Industry Worst in Stopping Insider Data Breaches (healthitsecurity.com)
3 Ways Healthcare Orgs Can Work to Prevent Insider Security Threats (hitconsultant.net)
Security Guard installs Botnet on Hospital Network – CYBER ARMS – Computer Security (wordpress.com)
Data Breaches: In the Healthcare Sector (cisecurity.org)
Roundup: Health Care Data Breaches and Defenses in the News (securityintelligence.com)
California Hospital Sued Over Data Breach - Infosecurity Magazine (infosecurity-magazine.com)
DDoS Attacks: In the Healthcare Sector (cisecurity.org)
Healthcare Data Breaches & DDoS Attacks: A Rising Threat? | Verizon
9 Reasons Healthcare is the Biggest Target for Cyberattacks (swivelsecure.com)
PYSA Ransomware Gang adds Linux Support - AlienVault - Open Threat Exchange
Vice Society ransomware joins ongoing PrintNightmare attacks - AlienVault - Open Threat Exchange
APPENDIX II: Disclaimer
This document and its contents do not constitute and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of the Client's compliance with any law, regulation, or standard.