- WHY AVERTIUM?
-
-
Why Avertium?
Context over chaos. Disconnected technologies, siloed data, and reactive processes can only get you so far. Protecting businesses in today’s threat landscape demands more than a set of security tools – it requires context.
That's where Avertium comes in
-
Considering Microsoft?
Avertium Named Microsoft Security Solutions PartnerAvertium’s managed services for Microsoft Security Solutions is delivered through the company’s premium service: Fusion MXDR. Fusion MXDR includes 24x7 monitoring and management of Defender for Endpoint and Sentinel, threat intelligence, attack surface
monitoring, and vulnerability management for Microsoft Security customers. -
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- SOLUTIONS
-
-
Governance, Risk, + Compliance
GRC with context – not complexity. -
Attack Surface Management
No more blind spots, weak links, or fire drills. -
Threat Detection + Response
Detect, adapt, and attack with context. -
Microsoft Security Solutions
End-to-end support from strategy to daily operations to maximize your Microsoft Security.
-
-
- COMPANY
-
-
About Us
Security. It’s in our DNA. It’s elemental, foundational. Something that an always-on, everything’s-IoT-connected world depends on.
Helping mid-to-enterprise organizations protect assets and manage risk is our only business. Our mission is to make our customers’ world a safer place so that they may thrive in an always-on, connected world.
-
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- PARTNERS
-
-
Our Partners
Best-in-class technology from our partners... backed by service excellence from Avertium.
-
Partner Opportunity Registration
Interested in becoming a partner?
With Avertium's deal registration, partners can efficiently and confidently connect with Avertium on opportunities to protect your deals.
-
Latest Avertium Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- NEWS & RESOURCES
-
-
News & Resources
Dive into our resource hub and explore top
cybersecurity topics along with what we do
and what we can do for you. -
Latest Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- CONTACT
What Is Penetration Testing (Not All Pen Tests Are Created Equal)
Penetration Testing Complete Guide: Not All Pen Tests Are Created Equal
Adversaries are constantly looking for exploitable weaknesses. A penetration test, also known as “ethical hacking,” is when a cybersecurity expert employs the tactics, techniques, and procedures (TTPs) that hackers use to test your network’s ability to withstand attacks. By having a friendly expert probe for vulnerabilities, they are more likely to be discovered in the pen test than in an actual attack. To simply put it, better a trusted advisor to find them than a bad actor.
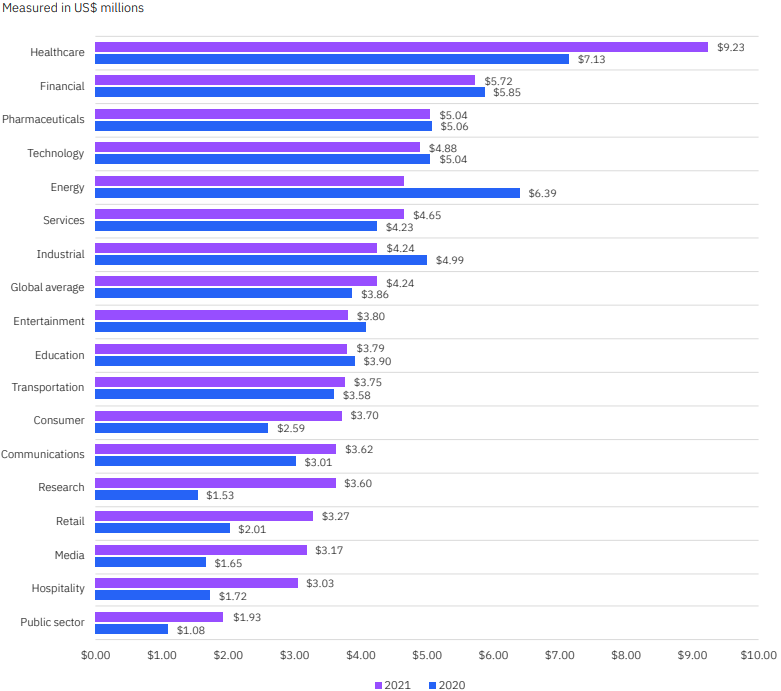
Though there are many reasons to perform penetration tests, the financial cost of a breach may be among the most compelling. Findings from the Ponemon IBM Cost of a Data Breach report discovered the average time to identify a breach in 2021 as 212 days with an additional 75 days to contain. That is an average of 287 total days for the lifecycle of a data breach. The findings also note that data breach lifecycles of more than 200 days had an average cost of $4.87 million, compared to $3.61 million when under 200 days.
Proactively searching for these weaknesses can reduce the risk of a breach and potentially eliminate the need for costly recovery measures. Because as we all know, the shorter the lifecycle, the smaller the cost to your organization.
The scope of pen tests varies, depending on the organizational need. Depending on an organization’s needs, any of these elements (and more) could be part of a thorough one-time penetration test:
- Network
- Systems
- Endpoints
- Cloud Architecture
- Internally Developed APIs
- Web and/or Mobile Apps
- Third-Parties
The goal of a penetration test is to answer the question: Are we secured? Can we withstand social engineering or other attacks?
However, as the demand for penetration testing grows, so does the commoditization and dilution of the service offering. Deciding on a pen test provider can be a challenge when companies are using the same terminology to describe vastly different services, both in terms of quality and scope.
In other words, not all pen tests are not created equal.
Related Resource: Why Pen Tests are key to a Robust Incident Response Plan
*Ponemon IBM Cost of a Data Breach report
Stages of Pen Testing
The stages of a pen test can break down into four parts.-
Planning and Reconnaissance: This phase determines the scope and timing of the test. It determines the testing parameters and when the test will begin.
-
Pre-Attack: Before carrying out an attack, the testers will gather intelligence and consider tactics, techniques, and procedures (TTPs) that may be useful for exploiting your vulnerabilities. This phase focuses on data collection as the hackers determine the most likely avenues for attack.
-
Attack: After determining potential vulnerabilities, the ethical hackers will begin the test. Depending on the scope of the test, there may be multiple approaches taken by the pen testers.
-
Post-Attack: Once the testing is complete, the testers will restore the system configurations and deliver a report of the test’s findings including vulnerabilities, remediation suggestions, and an analysis of the test’s conclusions.
WHAT ARE PENETRATION TESTING METHODOLOGIES and why are they important?
A penetration testing methodology is how penetration tests are organized and performed. The goal is to help you customize your pen test based on your need and help pen testers follow the most effective steps to help you avoid security vulnerabilities.
The Most Popular Pen Testing Methodologies
OSSTMM: Open Source Security Testing Methodology Manual is a pen testing methodology developed by the Institute for Security and Open Methodologies. OSSTMM provides a customized approach to penetration testing. You can use it to assess your specific business needs from a penetration test and it can also help you maintain compliance with regulations and laws within your industry.
There are 7 rules that help the Institute for Security and Open Methodologies identify potential security threats. These rules are:
- Project scope
- Confidentiality and non-disclosure assurance
- Emergency contact information
- Statement of work change process
- Test plan
- Test process
- Reporting standards
OWASP: Open Web Application Security Project is a set of guidelines that serve as a resource to many IT professionals. They can use OWASP to develop a thorough list of vulnerabilities facing your organization as well as helping to avoid future vulnerabilities or mend any existing vulnerabilities.
The steps of the OWASP Top Ten aim to guide pen testers to more effective pen tests. The steps include:
- Broken access control
- Cryptographic failures
- Injection
- Insecure design
- Security misconfiguration
- Vulnerable and outdated components
- Identification and authentication failures
- Software and data integrity failures
- Security logging and monitoring failures
- Server-side request forgery
NIST: The National Institute of Standards and Technology is a technology structure that can provide you with a set of configuration technology standards. These standards can be used during penetration testing to fully assess your networks for vulnerabilities.
The NIST penetration testing methodology consists of five functions as part of its cybersecurity framework. The functions are:
- Identify
- Protect
- Detect
- Respond
- Recover
PTES: Penetration Testing Execution Standard is a comprehensive list containing seven steps to help IT professionals conduct an effective pen test. The seven steps in this process are:
- Pre-engagement interactions
- Intelligence gathering
- Threat modeling
- Vulnerability analysis
- Exploitation
- Post Exploitation
- Reporting
One thing to keep in mind is that there are different variations of penetration tests that can be used. The scope of a pen test also varies based on what your organization needs or wants to shield itself from. Penetration testing methodologies are an effective way to tailor your pen test to your organization.
Where Pen Tests Can Fall Short
With pen testing, you often get what you pay for. There are plenty of discount-shop security companies that ostensibly offer penetration testing services at bargain rates. The problem is that these companies frequently use a checklist approach to their testing and apply a limited scope to your security needs.
And unfortunately, a one-size-fits-all approach to pen testing will almost certainly lead to lackluster results, including the failure to adequately address your business’s specific threat environment.
Check-the-Box Pen Testing: The Race to the Bottom
When pen testing is approached as just another item to cross out from cyber hygiene or project management checklists, the results will likely be insufficiently thorough. If the need to have completed a pen test replaces the actual purpose of conducting one, the test’s goal of catching and addressing security issues is compromised.
Unfortunately, as pen testing becomes more widely practiced cybersecurity hygiene, the market will continue to flood with check-the-box pen testing approaches. The market for cheap pen tests becomes a race to the bottom – companies offer increasingly diluted services, nominally called pen tests, that allow companies to feel as though they have done due diligence.
Even if the test looks official with the firm’s logo and letterhead (or presented in a customized package), make sure that you are receiving more than just a vulnerability scan wearing a pen test’s label. These tests cannot offer what a thorough, human-run pen test ought to provide.
Related Resource: Recovering from a Negative Pen Test
Common Mistakes Made by Pen Testers
Penetration tests can be complex meaning there are common mistakes that can occur if the pen test is inexperienced or not meticulous enough.
Some inexperienced pen testers solely rely on tools when conducting a pen test. This is not always effective because attention to detail and advanced problem-solving skills are also needed to ensure a penetration test is performed properly. This is why it’s imperative to hire an experienced and professional pen tester.
There are pen testers who can effectively perform a penetration on an organization’s network. However, some of these pen testers lack the ability to write an effective report about the results of a business's pen test. Not only do these pen testers fail to write an effective report they also forget to elaborate on what security threats are facing an organization.
Elements of a Quality Pen Test
When choosing a penetration test service, how can you know that you are getting a thorough test?
In a quality pen test, there will be a combination of automated vulnerability scans and human testing that accurately simulates a real-world attack. Professional standards like PTES, PCI DSS, and NIST 800-115 define essential elements of a pen test, but most specialized firms will enhance these with proprietary methods to better emulate a bad actor and deliver better results.
Pen Testing vs. Vulnerability Scanning
Vulnerability scanning on its own is not a pen test, but it is all you may receive from some smaller firms. The two services are often confused for one another, and understandably so. Both are intended to identify the flaws in IT infrastructure by testing systems for often-exploited weaknesses. However, vulnerability scans use automated processes to check systems for known flaws while flagging possible risks.
Penetration tests, on the other hand, are designed to find flaws in an IT network's architecture and also estimate the likelihood of a hostile attacker gaining unauthorized access to a company’s assets. How different firms may go about conducting each of these services can vary widely depending on their levels of experience, operating budgets, or other factors.
Open source tools are available for vulnerability scans and can present some helpful findings, but these are by no means the same as a detailed penetration test.
Smaller businesses with limited resources may be compelled by the lower cost of an automated vulnerability scan – which is certainly better than doing nothing at all. However, it is worth the extra time and expense to have a penetration test performed by a human. Not only is it a best practice, but it is also necessary to remain in compliance with various security standards and requirements.
Related Resource: Building an XDR Solution: Factors You Ought to Consider for ZTNA, EDR, Vulnerability Scanning, and SIEM
Human-Run Pen Tests
While vulnerability scans are useful for finding superficial vulnerabilities in your systems, they do not provide insight on what may be hidden inside your network or how multiple, lesser vulnerabilities could be combined to produce a more critical one. The hands-on approach of human-run pen testing means that expert analysts will explore the ways that vulnerabilities can be pieced together to exploit your systems.
In a human-run pen test, the tester and the user talk through the project and set up rules of engagement before performing the actual penetration test. While a vulnerability scan typically focuses only on web applications, a pen tester can take any approach and test whichever combination of resources that a client might want to have tested.
Human interaction also provides access to the knowledge and expertise of the penetration tester. While vulnerability scanners can provide plenty of insight, they are limited to how the information is conveyed in the report. With a human pen tester, you can ask specific questions about your environment and its vulnerabilities and receive highly contextualized answers and advice.
Social Engineering
Social engineering covers a wide variety of attack strategies focused on the vulnerabilities revealed through human interaction. The purpose is to identify how an attacker could manipulate a person or a group to divulge personal information or sensitive data. It can show flaws in user behavior, such as failure to follow security processes, and helps to evaluate user knowledge of security.
Social engineering may be done in a variety of ways, including analog methods with in-person or over-the-phone interactions or digital approaches through social media, email, and other digital communication. Open Source Intelligence (OSINT) leverages information that is available to the general public to anticipate common patterns of attack. There are several social engineering techniques that attackers commonly use:
-
Phishing, Vishing, and Smishing: This refers to the practice of sending emails, phone calls, and text messages respectively to coax the recipient into revealing sensitive information like login credentials. When these practices are highly targeted, they are referred to as spear phishing, vishing, or smishing.
-
Baiting: Similar to phishing, baiting is when a promise of something valuable is used to motivate an unsuspecting user to reveal information.
-
Impersonation: An impersonation attack is when an attacker impersonates a trusted individual in order to steal sensitive data from a business. These attacks often target high-ranking executives.
-
Pretexting: Overlapping with impersonation, pretexting refers to when an attacker invents a scenario that creates a convincing reason for the recipient to reveal their information. This often takes the form of an impersonator asking the recipient to “confirm” their identity for a fabricated reason.
Related Resource: Social Engineering Q&A: How to Strengthen Your Weakest Link
The Importance of Human-Run Pen Tests in the Real-World: The 2017 Equifax Data Breach
In 2017, Equifax was the victim of a security breach that exposed the financial data of 148 million customers. A vulnerability in Apache Struts – a widely-used open-source web server – enabled a cybercriminal to install a web shell on Equifax’s computers. Using the access provided by this web shell, the attacker expanded their reach to internal systems and was ultimately able to access the sensitive financial data.
While a number of factors made the entire Equifax hack possible, the crux of the issue was that the Apache Struts vulnerability was unpatched on their systems. The Equifax breach occurred three months after a patch was released to address that vulnerability, and the Department of Homeland Security had even issued a warning that it was being actively exploited and should be patched as soon as possible.
So why didn’t Equifax apply the patch?
According to Graeme Payne, the former CIO of Equifax blamed for the breach, his security team thought that they had applied the patch. The team had scanned the affected servers and assumed that the vulnerability had been successfully addressed when they received a false-negative result from a misconfigured scanner.
Equifax’s team was relying on a tool-based test when they ran their vulnerability scan, and the tool found no vulnerabilities in their attack surface. However, a human attacker was able to look deeper and find a string of vulnerabilities that enabled them to perform an “entirely preventable” attack that cost Equifax nearly two billion dollars.
Related Resource: Why Pen Tests are Key to a Robust Incident Response Plan
Which Type of Penetration Testing is Right for Your Business?
As technology continues to become more complex, the service of penetration testing is becoming more saturated. It’s imperative that you weed out any penetration tests that would not effectively protect your organization from security vulnerabilities. When determining which pen test is right for you it’s important to consider how your business will continue to grow, and change and what potential threats are facing your organization.
Different organizations need different levels of pen tests. Some organizations choose to have penetration tests performed more than once within a given window of time, while others opt for a one-time pen test. Not only consider the desired outcome, but also the size of your organization to determine the length of time you should take for a pen test to be performed. You should think of what compliance mandates must be followed for your organization to meet industry standards. Any potential threats facing your organization should also be taken into consideration when determining what level of pen test you need.
Tips for Spotting Good and Bad Pen Tests
In the world of cybersecurity, reputation and credibility are key. If a penetration testing organization lacks the skill sets, qualifications, and resources necessary to carry out your security testing, it is most certainly not a good fit.
Finding a Reputable Pen Tester
Consider the approach of the pen tester – Any reputable penetration testing firm should take a systematic and thorough approach to pen testing. After meeting with the company’s testers to discuss the scope and methodology of your test, you should feel comfortable trusting the company's procedure.
Consider what other, complementary services the company offers – Security detection, defense, and incident response companies are also in a better position to help your long-term security goals. Working with a range of client verticals and organizational sizes, these specialists participate in frequent "Blue Team" and "Red Team" exercises.
Consider the background of the individuals performing the pen tests – Look for companies where the testers have varied experiences, extensive backgrounds, and certifications including:
Some questions you can ask a perspective pen test firm (not an extensive list):
-
What are the differences between penetration testing and vulnerability scanning?
-
Why should I hire a third party to perform penetration testing?
-
Which level of penetration testing is best for us? What are your options?
-
Should penetration testing include a human element or can it be done using tools alone?
-
Should I retest after remediation, do I have to hire a different firm?
-
How do you balance applying automated tools to the target vs manual processes and tools?
-
How often should I have penetration testing done when preparing for a HIPAA or PCI assessment?
-
What standards do you follow in your pen testing program, and does your firm have a framework?
Take a look at one of our latest eBooks:
"2022 Cybersecurity Predictions"
How Avertium Can Help
Avertium’s penetration testers do not hurry through projects or clients, and they are accessible to help you plan your project and educate your staff. When you collaborate with Avertium's penetration testers, you are working with a committed, highly knowledgeable staff based in the United States with an extensive list of certifications and experiences.
To learn more about Avertium’s penetration testing services, reach out to start the conversation about addressing your company’s vulnerabilities.