- WHY AVERTIUM?
-
-
Why Avertium?
Context over chaos. Disconnected technologies, siloed data, and reactive processes can only get you so far. Protecting businesses in today’s threat landscape demands more than a set of security tools – it requires context.
That's where Avertium comes in
-
Considering Microsoft?
Avertium Named Microsoft Security Solutions PartnerAvertium’s managed services for Microsoft Security Solutions is delivered through the company’s premium service: Fusion MXDR. Fusion MXDR includes 24x7 monitoring and management of Defender for Endpoint and Sentinel, threat intelligence, attack surface
monitoring, and vulnerability management for Microsoft Security customers. -
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- SOLUTIONS
-
-
Governance, Risk, + Compliance
GRC with context – not complexity. -
Attack Surface Management
No more blind spots, weak links, or fire drills. -
Threat Detection + Response
Detect, adapt, and attack with context. -
Microsoft Security Solutions
End-to-end support from strategy to daily operations to maximize your Microsoft Security.
-
-
- COMPANY
-
-
About Us
Security. It’s in our DNA. It’s elemental, foundational. Something that an always-on, everything’s-IoT-connected world depends on.
Helping mid-to-enterprise organizations protect assets and manage risk is our only business. Our mission is to make our customers’ world a safer place so that they may thrive in an always-on, connected world.
-
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- PARTNERS
-
-
Our Partners
Best-in-class technology from our partners... backed by service excellence from Avertium.
-
Partner Opportunity Registration
Interested in becoming a partner?
With Avertium's deal registration, partners can efficiently and confidently connect with Avertium on opportunities to protect your deals.
-
Latest Avertium Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- NEWS & RESOURCES
-
-
News & Resources
Dive into our resource hub and explore top
cybersecurity topics along with what we do
and what we can do for you. -
Latest Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- CONTACT
Attack Surface Management vs. Vulnerability Management
Welcome to Attack Surface Management
Over the years, vulnerability management (VM) was performed in conjunction with penetration testing, vulnerability scanning, and web app assessments. These were some of the key players in helping us understand which of our technology assets are susceptible to ransomware threats and identify where the vulnerabilities lie within our organization to quickly seal up. However, with the widespread cloud migration and online presence, the average business’s digital footprint has expanded exponentially.
Today’s attack surface extends beyond your physical IT assets, now encompassing your entire digital footprint. This expansion has fundamentally changed the surface area that security teams must protect. Gone are the days of vulnerability management serving as an adequate defense for your attack surface… today’s cybersecurity professionals have to think bigger: they have to think about attack surface management (ASM).
What is Attack Surface Management? How does it differ from Vulnerability Management?
Vulnerability management is essentially a subset of attack surface management. Vulnerability management simulates the tactics, techniques, and procedures (TTPs) of real-world attackers, which not only gives visibility into the health of a cybersecurity program but also offers clear, actionable solutions to prevent hackers from infiltrating a business’s systems.
By implementing a regular cadence of vulnerability assessments and management testing tools, you are taking a critical step in helping your organization bulk up its cybersecurity posture. But keep in mind, this step is merely a subset of the robust attack surface management program.
With attack surface management (ASM), you’re pursuing the continual identification, inventory, classification, priority, and security monitoring of internal & external digital assets that store, transmit, or process sensitive data.
Your attack surface includes all of your assets that store your data – from hardware to software – that are accessible from the internet. Think of susceptible areas on your “surface” as attack vectors. Any unknown, unprotected, and unmonitored assets can be seen as an opportunity for bad actors. In other words, everything that bad actors can and will learn about vulnerable businesses as they investigate the threat landscape will be included in your ASM planning.
Related Reading: How Multi-Cloud Environments Expand Your Attack Surface and How to Manage and Reduce the Risk
Vulnerability Management vs. Attack Surface Management --
How are they alike/different?
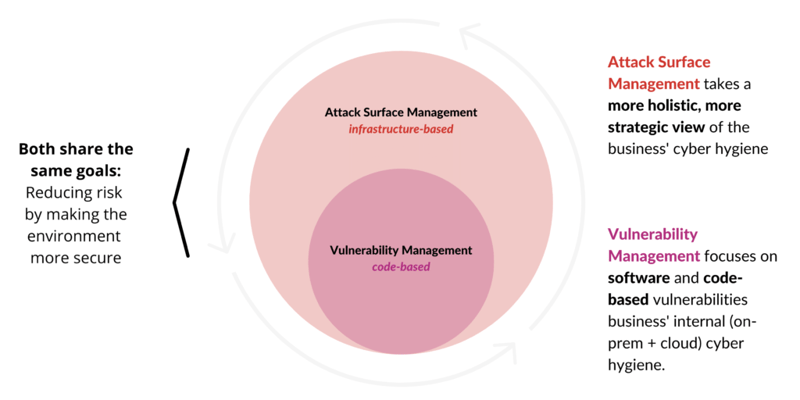
Related Resource: Ransomware Trends in 2021
Challenges in Managing Your Attack Surface
The best way to manage your attack surface is to shrink your attack surface… but that is easier said than done. There are a few challenges that arise when attempting to shrink an attack surface.
Shadow IT → Your organization’s central IT team cannot protect what they cannot see… and that’s the definition of shadow IT. When remote workers are putting up workstations or servers to meet their immediate needs, meeting corporate security protocols often isn’t a priority. These endpoints go unpatched, unprotected, creating an easy opportunity for an attack.
Mergers and Acquisitions (M&A) → In many mergers and acquisitions, the company being acquired doesn’t have up-to-date records of all its assets. As a result, this creates a similar situation where there could be assets that are not patched or tested, leading to out-of-date and vulnerable operating systems, frameworks, and third-party applications.
While shadow IT and M&As are the primary challenge to effective ASM, there are a few additional contributors to an expanded attack surface:
- Technology mistakes arising from...
- Internet of Things (IoT)
- Vulnerable and outdated software
- Unknown open-source software (OSS)
- Intellectual property infringement
- And human mistakes arising from...
- Phishing
- Data leaks
- Third-party vendor managed assets
Bad Actors may have a better understanding of your attack surface than you do. And that’s due to the fact that most organizations don't exactly have a complete picture of their assets. Until a detailed audit is conducted, these assets remain undiscovered, leaving vulnerable spots on your attack surface. In short, all it takes for an attacker to set in motion a cyber attack is simply one vulnerable point in your organization.
Related Reading: 3 Reasons Why You Need a Human-Run Penetration Test
Components of A Comprehensive Approach to ASM
Sun Tzu’s “Art of War” aptly outlines what it takes to have a comprehensive approach to attack surface management:
“If you know the enemy and know yourself, you need not fear the result of a hundred battles. If you know yourself but not the enemy, for every victory gained you will also suffer a defeat.”
In other words, when managing your attack surface, the key to victory is to have both strategy and tactics based on a deep understanding of your company, your team, and your processes, in addition to a solid understanding of the threats you’re up against. With this knowledge, you’ll be able to see the full picture of how to protect your business.
Applying the Art of War to ASM
The Avertium team takes this approach to help you stay ahead of any attackers or threats. In this case, a comprehensive approach to ASM – knowing thy self and knowing thy enemy – starts by taking the following steps into consideration:
- Asset discovery and identification
- Classification and prioritization
- Security ratings and risk scoring
- Continuous security monitoring
- Security threat intelligence
1. Asset discovery and identification →
Some organizations will utilize Open Source Intelligence (OSINT) and Dark Web enumeration to identify their attack surface – similar to the information that an attacker can see while they plan attacks against your organization. By doing this, businesses will have an idea of how an attack might be conceived and start brainstorming the measures they need to take to mitigate it.
It’s good to note that this can also assess your physical and software assets, identifying what functions and parts of the system you will need to review/test for security vulnerabilities.
When going through this step, some good questions to ask are:
- Which devices are connected to my environment?
- Which devices are unmanaged and unprotected?
- Does this device have a port(s) open?
- Are there any unauthorized applications running?
2. Classification and prioritization →
Once your assets have been thoroughly discovered, you can categorize and prioritize them according to each one’s level of risk – from assets that need to be remediated immediately to assets that can wait according to your specific risk appetite. It’s important to identify the high-risk areas first and work backward.
It’s important to take into account any and all remote entry points – interfaces with outside systems and to the Internet – and especially, areas where the system allows anonymous, public access. Oftentimes, these are where you are most exposed to an attack.
3. Security ratings and risk scoring →
Effective attack surface management is only possible once relevant assets and potential vulnerabilities are identified and categorized by rating and scoring. Discovery must include a comprehensive network scan and system audit. Sophisticated software tools and applications can effectively automate a large part of this process.
The catalog of assets should be classified according to potential vulnerabilities, as well as configuration, patch, and compliance states, which generates an initial risk assessment.
Risk is then reduced by applying controls reducing the threat posed by the vulnerability. In a cybersecurity context, this can include operations like segregating vulnerable portions of the network or devices or deploying enhanced authentication or authorization solutions. Generally, this is accomplished accordingly by the rating and scoring of the identified asset.
Resource: 6 Steps to Implementing a Zero Trust Network
4. Continuous security monitoring →
Continuous network monitoring is required to stay abreast of today's sophisticated attacks. This means the catalog of assets must also be continually refreshed to stay up-to-date, but this also means leveraging the right tools and technologies to continuously monitor your attack surface.
Fusion MXDR is the first MDR offering that fuses together all aspects of security operations into a living, breathing, threat-informed XDR solution.
By fusing insights from threat intelligence, security assessments, and vulnerability management into our MDR approach, Fusion MXDR offers a more informed, robust, and cost-effective approach to cybersecurity - one that is greater than the sum of its parts.
5. Security threat intelligence →
Knowing thy enemy starts with gathering intelligence on potential adversaries' tactics, techniques, and procedures (TTPs). You can also work with a trusted partner such as Avertium to leverage our Cyber Threat Intelligence (CTI) Resources to further strengthen your security processes.
Note: Michael Howard at Microsoft and other researchers have developed a method for measuring the attack surface of an application, and to track changes to the attack surface over time, called the Relative Attack Surface Quotient (RSQ). Using this method you calculate an overall attack surface score for the system and measure this score as changes are made to the system and to how it is deployed. Researchers at Carnegie Mellon built on this work to develop a formal way to calculate an Attack Surface Metric for large systems like SAP. They calculate the attack surface as the sum of all entry and exit points, channels (the different ways that clients or external systems connect to the system, including TCP/UDP ports, RPC endpoints, named pipes...), and untrusted data elements. Then they apply a damage potential/effort ratio to these attack surface elements to identify high-risk areas.
Related Reading: 8 Essential Steps to Take After a Data Breach
How Avertium Can Help You with Attack Surface Management
Expanding endpoints, cloud computing environments, accelerated digital transformation, and the move to work from home have decimated the perimeter. Avertium's approach to attack surface management empowers companies with the strategic insight needed to drive board-level decisions, blending tactical action with a big-picture approach that protects business-critical assets.