- WHY AVERTIUM?
-
-
Why Avertium?
Context over chaos. Disconnected technologies, siloed data, and reactive processes can only get you so far. Protecting businesses in today’s threat landscape demands more than a set of security tools – it requires context.
That's where Avertium comes in
-
Considering Microsoft?
Avertium Named Microsoft Security Solutions PartnerAvertium’s managed services for Microsoft Security Solutions is delivered through the company’s premium service: Fusion MXDR. Fusion MXDR includes 24x7 monitoring and management of Defender for Endpoint and Sentinel, threat intelligence, attack surface
monitoring, and vulnerability management for Microsoft Security customers. -
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- SOLUTIONS
-
-
Governance, Risk, + Compliance
GRC with context – not complexity. -
Attack Surface Management
No more blind spots, weak links, or fire drills. -
Threat Detection + Response
Detect, adapt, and attack with context. -
Microsoft Security Solutions
End-to-end support from strategy to daily operations to maximize your Microsoft Security.
-
-
- COMPANY
-
-
About Us
Security. It’s in our DNA. It’s elemental, foundational. Something that an always-on, everything’s-IoT-connected world depends on.
Helping mid-to-enterprise organizations protect assets and manage risk is our only business. Our mission is to make our customers’ world a safer place so that they may thrive in an always-on, connected world.
-
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- PARTNERS
-
-
Our Partners
Best-in-class technology from our partners... backed by service excellence from Avertium.
-
Partner Opportunity Registration
Interested in becoming a partner?
With Avertium's deal registration, partners can efficiently and confidently connect with Avertium on opportunities to protect your deals.
-
Latest Avertium Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- NEWS & RESOURCES
-
-
News & Resources
Dive into our resource hub and explore top
cybersecurity topics along with what we do
and what we can do for you. -
Latest Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- CONTACT
When Cybercriminal Gangs Go Dark - Avaddon, AstraLocker & Conti
Executive Summary
If you keep up with the latest cyber security news, then you have probably noticed that several cybercriminal gangs have gone dark – especially ransomware-as-a-service (RaaS) gangs. In recent years, RaaS has become the attack vector of choice amongst cyber criminals, and despite other attack vectors gaining popularity it will continue to be their preference.
In May 2021, we witnessed the ransomware gang DarkSide launch a supply chain attack that ended up becoming one of the most impactful ransomware attacks in U.S history. DarkSide gained access to Colonial Pipeline’s virtual private network (VPN) account due to a single compromised password. During the same month, the nation-state threat actor NOBELIUM attacked SolarWinds – an attack that prompted President Biden to put cybersecurity at the top of his list of priorities for the following year.
These attacks were devastating and long-lasting. However, just as quickly as threat actors like DarkSide and NOBELIUM appeared, they disappeared. As the media and infosec community discussed their attacks, the less we heard from the threat actors. In May 2021, one year after disrupting gasoline distribution across the U.S, DarkSide went dark and suspended their operations. Additionally, not much was heard from NOBELIUM after their attack on SolarWinds.
It appeared as if both groups disbanded and were done, but with a little research one can see that is not the case. DarkSide may have gone dark in May 2021, but they re-emerged under the name BlackMatter in June 2021 – causing more destruction. While NOBELIUM has not officially gone dark, they have been very quiet and non-active under their original name. However, recent reports show that NOBELIUM has been active but are identified by other researchers as CozyBear or APT29.
Recently, threat actors like AstraLocker, Conti, and Avaddon have also gone dark – releasing decryption keys and data while saying “goodbye”. Given the prior history of cybercriminals who go dark, are these groups really saying goodbye or are they just rebranding/forming alliances with smaller groups? Let’s take a look at AstraLocker, Conti, and Avaddon’s disappearance and why it is important to keep a close watch on threat actors who shut down their operations.
avaddon ransomware
In May 2021, the FBI and the Australian Cyber Security Center (ACSC) issued an alert regarding the ransomware gang Avaddon and how they were actively leveraging phishing campaigns with double extortion attempts. The Russian threat actors targeted several global private sector entities, including COVID-19 vaccine developers and those in the healthcare sector.
Initially spotted in the wild in February 2019, Avaddon lets affiliates leverage the ransomware if they promise to return a portion of the profits to Avaddon’s developers. Proofpoint observed Avaddon using a victim’s geolocation and system language to determine if they wanted to attack their system. They also observed Avaddon sending more than 1 million messages between June 4 and June 10, 2020.
During 2021, Avaddon was able to exploit several organizations by sending email attachment downloads via PowerShell. After the attachments were opened, Avaddon ran and displayed a ransom message, later demanding $800 payments in bitcoin via TOR. Avaddon’s operators also offered 24/7 customer support and resources regarding the purchase of bitcoin and testing files for decryption. They wanted to make sure they lessened the challenges that could interfere with their victims paying the demanded ransom.
In addition to healthcare, Avaddon affiliates target North America in the manufacturing, education, and financial sectors on a global scale. Avaddon’s affiliates used Windows Scheduled Task for persistence, as well as ProtonMail service to send and receive data at the early stages of intrusion. If victims refuse to pay, they threaten them with DDoS attacks in addition to encryption.
As stated previously, Avaddon conducted their attacks via phishing campaigns. The malware allowed the attackers to capture operating system operations, network configurations, hostnames, disk information, and network interferences. They were also able to capture Volume Shadow Copy files and delete services.
By June 2021, Avaddon appeared to call it quits and shutdown their RaaS operation, releasing decryption keys for their victims to BleepingComputer.com. The gang gave the technology site a password and a link to a password-protected ZIP file. The file contained the decryption keys for Avaddon ransomware’s victims.
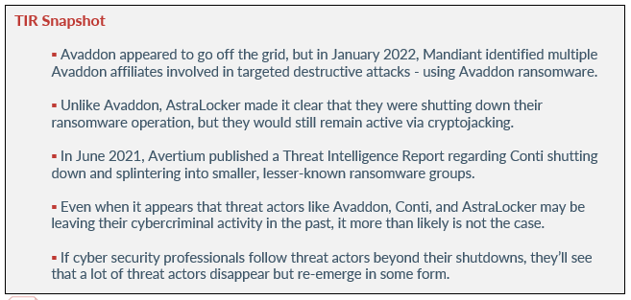
Avaddon appeared to go off the grid but even after they went dark, Mandiant tracked Avaddon and found that there were other ransomware families that shared code similarities. They also observed previous RaaS services operating since 2019 to 2021 connected to Avaddon’s source code. Mandiant stated that the timeline of the services and the similarities in the code could be a part of the rebuilding process. Mandiant also speculated that Avaddon could be collaborating with other threat actors, or the source code is likely being shared by multiple threat actors.
astralocker
In June 2022, AstraLocker was a lesser-known ransomware strain that dropped its payload directly from email attachments. The ransomware gang focused less on reconnaissance and lateral network movement, and more on performing “smash-n-grab” attacks. Their goal was to lure victims through a Microsoft Word document and receive a quick payout once the victim opened the document.
Instead of choosing VBA macros to distribute their malware, AstraLocker chose OLE objects. They also chose to use an outdated packer called Safe Engine Shielder v2.4.0.0, to pack the executable. This packer is so old that reverse engineering is nearly impossible.
In July 2022, AstraLocker shut down and released decryptors – stating that they were switching to cryptojacking. Like Avaddon, the developers released a ZIP archive with AstraLocker’s decryptors. Cryptojacking happens when an attacker maliciously hacks into a computer (mobile device or laptop) and installs malicious software. The software is used to steal cryptocurrency and a code runs in the background (even after attackers have left), hijacking their victims’ resources.
AstraLocker has already been linked to Chaos ransomware based off of a Monero wallet address. Additionally, analysis revealed that AstraLocker is based on the leaked source code of Babuk Locker – a dangerous ransomware strain that left cyber space in September 2021. Unlike Avaddon, AstraLocker made it clear that they were shutting down their ransomware operation, but they would still remain active via cryptojacking. Cryptojacking is a quieter way for AstraLocker to make money.
conti
Conti is one of the most talked about ransomware gangs in the history of cyber security. Conti is a Russian-speaking RaaS organization, that uses RaaS to deploy disruptive ransomware attacks that target critical infrastructure (hospitals and government organizations). Conti generally focuses on attacking companies with more than $100 million in annual revenue. They specialize in double extortion, simultaneous data encryption, and data exfiltration for financial gain. If the ransom is not paid, Conti will blackmail their victims by threatening to publish stolen files.
It is believed that Conti is controlled by a Russian-based cybercrime group, Wizard Spider. Wizard Spider is known for creating and operating TrickBot banking malware. Conti also helped popularize the removal of an organization’s backups after encryption.
Unlike other ransomware gangs, Conti has historically targeted critical infrastructure. To date, Conti has successfully infiltrated the networks of the Defense Industrial Base (DIB), Leon Medical Centers, Nocona General Hospital, and Rehoboth McKinley Christian Health Care Services (RMCHCS).
In June 2021, Avertium published a Threat Intelligence Report regarding Conti shutting down and splintering into smaller, lesser-known ransomware groups. According to our partners, AdvIntel, Conti is currently rebranding as multiple ransomware groups and the brand (not the organization) is shutting down. On May 19, 2022, Conti’s official website went offline, as well as their negotiations service site. Conti’s infrastructure (chat rooms, servers, proxy hosts, etc.) went through a massive reset.
The publicity function of Conti’s blog is still active, but the operational function of “Conti News” (used to upload new data to force victims to pay) is defunct – including infrastructure related to data uploads, negotiations, and the hosting of stolen data. AdvIntel believes that Conti can no longer support their operation and that the shutdown was not spontaneous but calculated. Conti spread out into smaller groups that are mostly unknown so they could avoid law enforcement but still stay mobile in cyber space.
KEEPING A CLOSE WATCH ON DISAPPEARING THREAT ACTORS
When threat actors break out into smaller groups or form alliances with groups, it means that they are trying to reorganize and avoid the pressures that come with being a large and visible group.
Since disbanding in June 2021, Conti’s members have formed alliances with and splintered off into BlackCat, AvosLocker, Hive, and FiveHands. These are four threat groups who are not as well-known – something that Conti was likely seeking. Most cybercriminal gangs, who shut down and join other gangs, will have some of the same tactics, techniques, or TTPs as they did previously.
If members from a disbanded gang join another one, they will eventually tell on themselves. Some gangs have been known to accidentally leave old email addresses attached to ransom notes, use the same source code of their previous brand to deploy ransomware, or even have the same exact ransom note language from a previous one.
For example, one of the ways BlackMatter was discovered to be a rebrand of DarkSide, is due to the similarities between the groups’ goals. Both groups had a set of rules that prohibited them from attacking critical infrastructure and both groups made it clear that their priority was to make money and “take care of their families”. The two groups were also using the same encryption algorithm – a custom Salso20 matrix.
If cyber security professionals follow threat actors beyond their shutdowns, they’ll see that a lot of threat actors disappear but re-emerge in some form. By keeping a close watch, cyber security professionals will be able to get a head of the threat.
RaaS gangs go dark, re-emerge, or join other ransomware gangs for a few reasons:
- Members may join other gangs or threaten to hurt operations
- Law enforcement has started to intervene and there is fear of arrest (AstraLocker can quietly cryptomine instead of encrypting and demanding a ransom)
- The Group made a mistake that cost them money or freedom (Conti’s leaked chat logs)
How Avertium is Protecting Our CUSTOMERS
Threat actors like Avaddon, AstraLocker, and Conti are persistent and have one bottom line – financial gain. Staying current with the latest cyber threats and paying close attention to how threat actors move is necessary if you want to keep a safe cyber environment. Additionally, Avertium has services that can help organizations stay ahead of threats, as well as recover from attacks. Avertium’s Cyber Threat Intelligence team is on watch for when these rebranded groups will resurface:
- Avertium offers VMaaS to provide a deeper understanding and control over organizational information security risks. If your enterprise is facing challenges with the scope, resources, or skills required to implement a vulnerability management program with your team, outsourced solutions can help you bridge the gap.
- Minimizing the impact of a successful ransomware attack requires detecting it as early in the attack as possible. A Security Information and Event Management (SIEM) system can help an organization to accomplish this. Avertium offers a comprehensive SIEM-based approach that increases the potential for detecting a ransomware infection before it deploys. SIEM provides a holistic overview of a company’s IT environment from a single point of view in terms of its specific security events, empowering teams to detect and analyze unusual behavior.
- Fusion MXDR is the first MDR offering that fuses together all aspects of security operations into a living, breathing, threat-resistant XDR solution. By fusing insights from threat intelligence, security assessments, and vulnerability management into our MDR approach, Fusion MXDR offers a more informed, robust, and cost-effective approach to cybersecurity – one that is great than the sum of its parts.
- Avertium offers Zero Trust Architecture, like AppGate, to stop malware lateral movement.
- Avertium offers user awareness training through KnowBe4. The service also Incident Response Table-Top exercises (IR TTX) and Core Security Document development, as well as a comprehensive new-school approach that integrates baseline testing using mock attacks.
Avertium’s Recommendations
For threat actors like Avaddon, Conti, and AstraLocker, Avertium recommends the following:
- Maintain offline, encrypted backups of data and regularly test backups
- Create, and exercise a basic cyber incident response plan and a communications plan
- Mitigate internet-facing vulnerabilities and misconfigurations
- Reduce the risk of phishing emails by enabling strong span filters and implementing a cybersecurity user awareness training program
- Practice good cyber hygiene
- Ensure antivirus and antimalware software signatures are up to date
- Implement application allow listing
- Ensure user privileged accounts are limited
- Employ MFA
- Implement cybersecurity best practices
- Organizations can detect and block malware by scanning emails and email attachments.
MITRE Map
Avaddon
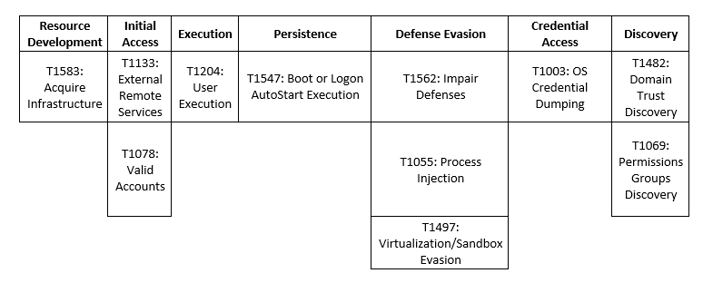
AstraLocker
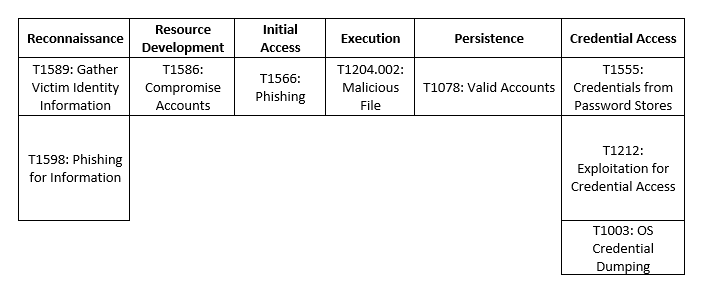
Conti
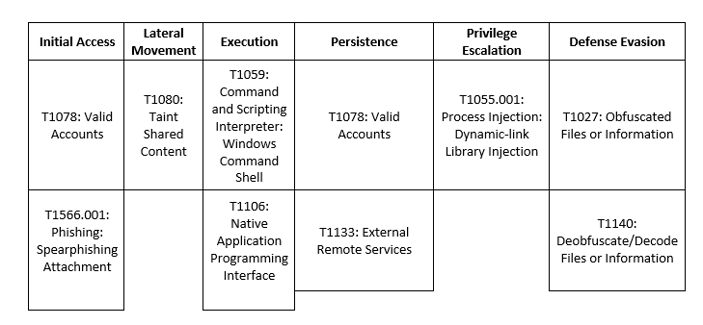
Indicators of Compromise (IoCs)
AstraLocker
- cf3bdf0f8ea4c8ece5f5a76524ab4c81fea6c3a1715b5a86b3ad4d397fca76f3
- b0a010e5a9b353a11fb664501de91fc47878d89bf97cb57bc03428c7a45981b9
- 17ea24ce8866da7ef4a842cba16961eafba89d526d3efe5d783bb7a30c5d1565
- 08565f345878369fdbbcf4a064d9f4762f4549f67d1e2aa3907a112a5e5322b6
- 5c061e188979d3b744a102d5d855e845a3b51453488530ea5dca6b098add2821
- 60167b6a14b7da2257cb6cbdc7f1ebcb4bdfa16c76cc9a7539c9b8d36478d127
- 71ba916a7f35fe661cb6affc183f1ce83ee068dbc9a123663f93acf7b5a4263e
Avaddon
- http://myphotoload[.com]/photo.php?id=816832
- http://myphotoload[.com]/photo.php?id=793048
- http://myphotoload[.com]/photo.php?id=561172
- http://myphotoload[.com]/photo.php?id=466485
- http://myphotoload[.com]/photo.php?id=212624
- http://myphotoload[.com]/photo.php?id=177139
- 0056713a80d21bc490b5e605633d4408c002d35bdcbaa277e881ec242f2ec3db
- 0da756b7957dd8b94cf151a913a37050bb23b44369853933a27a0ce178c006e5
- 1c399e7900028b36c42a5a4c96ca6b39485ea86fdf447dde5f29c9996090df74
- 26a65f16c238969fc3ab8250653ae5d2c4c1f0b1b16b6cc555a58d5c304b9c1b
- 2ab0685cc91f991edd96f5712b44bd42e9e1ee5b01c4cf830ca6279bd727005e
- 38a383d2b43042e94328f9f6327e0312c9e13de1ca74cee5c38cd34607823b5d
- 42b379a1bfc5b8d772ecf75af27e86cc163052edc6be323c6a8561593b9b24a5
- 45f97ecc46812f2018088f5da572f34b1ac55eaa09bf92f0fff562c2fa57bb26
- 6389e3c49b6f4009ca0f1631436d481065a3b3cfab7a15a073edbb61dd971c73
- 75adf0d7e708b54f8debec4767e2ba3cc52cdf0264a8d6545865d4c7ae7352d0
- 80c09156923349232ebb9c4dbf384929f481f2cb62a0ffab9f07293e6967a8cc
- 8b7a1996a891ae757309cdc7440dc7c0930a19e20ac4f57a656ce0a9e0b05ea3
- 9a73f2354fca80dc0f330e65c94b7758b67666852ed87759e915054511bca08c
- aacf0bd167217a2805b665fc62151fb9191849ed172ed0ca80cb31b7401f39d7
- b14fb581b4d9aa2b032d2eddaea81ecd437c12cb11fa5dbaeb5a3861f12c1f90
- b5596e898af25ee3925b6e14b710a405705e2d27f2c2ba652e35c70fe9f7c200
- cc2634e2e75c0336eee1f2a94b855ac2355d10f2e0f085cca834e59b651bf1f7
- ccb343bcf26b45cd3ed2e68526f78ecbd31efec43a965b6fd863e17364c9da61
- e51835060510f38d7a127576ae34ad6780801d15d7ea29fc6e00296c10792b6b
- f3886e63cff5240fbc30acbf4b8bcc00c4c2f036391d4a4fd7182540f4b028bd
- For the complete list of IoCs, please click here.
Conti
- 0737ebb6ede108d90216bc06ccfce57defa2179bfda93a34edd868a6f9172a78 (associated with newer leaked sourced code)
- fb49dce92f9a028a1da3045f705a574f3c1997fe947e2c69699b17f07e5a552b
- 3d3308249c9678add3a18400dee765e1
- 6237d6565ebde559310120a80567e016
- ed475bccfcbe008930aa837a8effd7a9
- 0aebd55ec0cb8ff6e7f5a853c68f9948f4ed824e
- ac2785ef856f0a6a93a68d4c6f45fc87ff7bb530
- bf8a4f936ea526547304941b071a893c26c4fc8b
- 5f3ae6e0d2e118ed31e7c38b652f4e59f5d5745398596c8b31248eda059778af
- e1b147aa2efa6849743f570a3aca8390faf4b90aed490a5682816dd9ef10e473
- fb737da1b74e8c84e6d8bd7f2d879603c27790e290c04a21e00fbde5ed86eee3
- 160[.]77
- 215[.]61
- 19[.]173
- Gojihu[.com]
- Sazoya[.com]
- Yawero[.com]
- Suhuwow[.com]
- Mihojip[.com]
- Hewecas[.com]
- Balacif[.com]
- Wuvehus[.com]
- Codasal[com]
- Xekezix[.com]
- Conti uses remote access tools that beacon to domestic and international VPS infrastructure over ports 80, 443, 8080, and 8443.
Supporting Documentation
Threat Alert: Russian-Backed Threat Actors, Avaddon Ransomware (healthitsecurity.com)
End of Year Recap for 2021 (avertium.com)
Threat Actor Profile – “BlackMatter” Ransomware (avertium.com)An In-Depth Look at Black Basta Ransomware (avertium.com)
An In-depth Look at Conti's Leaked Log Chats (avertium.com)
Smash-and-grab: AstraLocker 2.0 pushes ransomware direct from Office docs (reversinglabs.com)
AstraLocker Ransomware - Decryption, removal, and lost files recovery (updated) (pcrisk.com)
Avaddon_Ransomware.pdf (subexsecure.com)
Avaddon RaaS | Breaks Public Decryptor, Continues On Rampage - SentinelLabs (sentinelone.com)
AstraLocker ransomware shuts down and releases decryptors (bleepingcomputer.com)
Avaddon ransomware shuts down and releases decryption keys (bleepingcomputer.com)
One Source to Rule Them All: Chasing AVADDON Ransomware | Mandiant
AstraLocker 2.0 infects users directly from Word attachments (bleepingcomputer.com)
TIR-20211004 An In-Depth Look at Ransomware Gang, Conti (avertium.com)
Evidence suggests that DarkSide and BlackMatter are the same groupSecurity Affairs
Threat Hunting for Avaddon Ransomware (force.com)
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.