- WHY AVERTIUM?
-
-
Why Avertium?
Context over chaos. Disconnected technologies, siloed data, and reactive processes can only get you so far. Protecting businesses in today’s threat landscape demands more than a set of security tools – it requires context.
That's where Avertium comes in
-
Considering Microsoft?
Avertium Named Microsoft Security Solutions PartnerAvertium’s managed services for Microsoft Security Solutions is delivered through the company’s premium service: Fusion MXDR. Fusion MXDR includes 24x7 monitoring and management of Defender for Endpoint and Sentinel, threat intelligence, attack surface
monitoring, and vulnerability management for Microsoft Security customers. -
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- SOLUTIONS
-
-
Governance, Risk, + Compliance
GRC with context – not complexity. -
Attack Surface Management
No more blind spots, weak links, or fire drills. -
Threat Detection + Response
Detect, adapt, and attack with context. -
Microsoft Security Solutions
End-to-end support from strategy to daily operations to maximize your Microsoft Security.
-
-
- COMPANY
-
-
About Us
Security. It’s in our DNA. It’s elemental, foundational. Something that an always-on, everything’s-IoT-connected world depends on.
Helping mid-to-enterprise organizations protect assets and manage risk is our only business. Our mission is to make our customers’ world a safer place so that they may thrive in an always-on, connected world.
-
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- PARTNERS
-
-
Our Partners
Best-in-class technology from our partners... backed by service excellence from Avertium.
-
Partner Opportunity Registration
Interested in becoming a partner?
With Avertium's deal registration, partners can efficiently and confidently connect with Avertium on opportunities to protect your deals.
-
Latest Avertium Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- NEWS & RESOURCES
-
-
News & Resources
Dive into our resource hub and explore top
cybersecurity topics along with what we do
and what we can do for you. -
Latest Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- CONTACT
The Top 5 Cyber Threats Within the Manufacturing Industry
Executive Summary
In previous years, cyber security threats centered around industries such as healthcare, retail, finance, and energy. Manufacturing was rarely included in the conversation, simply because there was a lack of understanding and communication within the industry. The manufacturing industry is different from other industries who have a direct connection with the outside world. Before technology evolved, manufacturing companies were only connected within a network of a single organization with limited internet – making it difficult to connect with organizations or people in general. Organizations within the medical and financial industries don’t have the same barrier due to their public-facing nature. Additionally, the manufacturing companies didn’t believe they were appealing to threat actors – they merely didn’t believe they had much to offer.
However, technology has evolved, and the archaic ways of communicating within the manufacturing industry are obsolete. When communication channels change, so does the cyber threat landscape. Now that the manufacturing industry has no choice but to utilize internet connectivity in a variety of ways, they are faced with the harsh reality that they were unprepared to handle the security challenges that come with having so many vulnerable endpoints.
Also, the idea that the manufacturing industry didn’t have much to offer threat actors is not true. In fact, companies within the industry have a vast amount of information that attackers are just waiting to use as extortion. Companies like Nissan and Norsk Hydro learned the hard way that the industry is not exempt from cyber attacks. Let’s take a look at the top 5 cyber threats within manufacturing and how you can help prevent your organization from becoming another victim.
phishing
Although various industries fall victim to phishing attacks, phishing attacks within the manufacturing industry are very common and it’s one of the industries that receives the most phishing attacks per year. Since 2020, threat actors have exploited several vulnerabilities for financial gain, and they have even exploited vulnerabilities for brand impersonation purposes.
Phishing attacks involve a target opening a malicious email attachment or spoofed website. The attachments and websites compromise the target’s browser settings and use whatever data is available for financial gain. The main way the manufacturing industry falls victim to phishing attacks is through web-based malware downloads that contain trojans or other malicious content. Vulnerabilities are discovered on systems via the malware and the information is transferred to the attacker. The data that’s collected by the threat actor is used to demand ransom or it’s sold on the dark web.
Why is the manufacturing industry especially vulnerable to phishing attacks? There are several reasons.
- Legacy Equipment – The manufacturing industry is known for using devices that are outdated or devices that were designed to maximize security. In order to compromise legacy equipment, attackers would not need to do much work.
- Different IT Infrastructure - Different sets of technologies are used for manufacturing units that are in separate locations. Each kind of technology may have different hardware and software – causing security frameworks to become fragmented. This means that a single security framework will not work for all the systems.
- Industrial Espionage – If a manufacturer has government contracts, they are a prime target for threat actors who are motivated by cyber espionage. They know that there are certain sectors that will be greatly compromised if they can attack the suppliers and clients related to a particular industry.
- Sizeable Financial Gain – As we mentioned earlier, the manufacturing industry used to believe that they didn’t have much to offer attackers. However, that is not true. The manufacturing industry is vast and has a copious amount of sensitive data that can be used for financial gain (credit card information, bank details, data related to financial institutions, and social security numbers). Such data can be sold or used to compromise other networks for ransom.
- Lack of Centralized Visibility - Not having one single platform to view data flow is a great entry point for a threat actor. There are many hidden loopholes and complexities within the fragmented framework that attackers can exploit.
- Less Secure Encryption Techniques – Because the manufacturing industry primarily focuses on production and distribution, they are sometimes oblivious to cyber security issues. Threat actors know that the industry’s focus isn’t on them, so they take advantage of the sector’s lack of complex encryption techniques and ignorance regarding phishing.
In 2018, Kaspersky Lab reported that more than 400 manufacturing companies became phishing targets. At the time, there was a phishing campaign geared toward stealing money from corporate accounts. The attackers used a variety of tools and standard phishing techniques to distribute harmful software via emails disguised as commercial offers. The threat actors also used legitimate software (TeamViewer or Remote Manipulator System) to orchestrate their attacks. The programs helped the threat actors gain access to devices, scan for information on current purchases and financial software. Additional tools were used to get higher-level permissions and steal data.
Kaspersky Lab observed that in some cases, the threat actors sent out malicious email attachments, but in others they sent their victim’s links to sites. In both instances, the emails persuaded the target to download the tools used by the threat actors on his or her own initiative. The report acknowledged that using modern technology and educating staff about phishing exploits have kept organizations safe.
ransomware
In 2021, the manufacturing industry endured the brunt of cyber attacks in general. IBM published a report (X-Force Threat Intelligence Index) in 2021 and unveiled how ransomware and other vulnerabilities affected supply chains, with manufacturing being the most targeted industry. In the past, the financial services and insurance industry experienced the most ransomware attacks, but in 2021 manufacturing dethroned those industries and has become the most attacked industry via ransomware.
“For the first time in five years, manufacturing outpaced finance and insurance in the number of cyberattacks levied against these industries, extending global supply chain woes. Manufacturers have a low tolerance for downtime, and ransomware actors are capitalizing on operational stressors exacerbated by the pandemic. “ IBM
Attackers relied on the ripple effect that takes place when manufacturing organizations have their production flow disrupted. The threat actors knew the attacks would cause their downstream supply chains to force them into paying a ransom. The report further stated that 47% of the attacks within the manufacturing industry were due to vulnerabilities that companies didn’t patch – this highlights the need for all manufacturing companies to include vulnerability management in their security plans.
Avertium published a Threat Intelligence Report in April 2022 featuring Bridgestone Corp. In March 2022, Bridgestone Corp. notified the public that they were hit by a ransomware attack. Bridgestone is a tire supplier for Toyota vehicles. Initially, it was suspected that Pandora ransomware was behind the attack because it happened shortly after the gang attacked Denso Corp., (another car parts supplier) however, it turned out to be the work of LockBit ransomware.
Bridgestone’s breach impacted several cities and plants were inoperable for days. LockBit gave Bridgestone a timeframe to pay their demanded ransom before they released the company’s data. Like other ransomware groups, LockBit removed information from Bridgestone’s systems and threatened to disclose the information to the public. Bridgestone was the second auto parts supplier attacked by a ransomware gang in a very short span of time.
intellectual property theft
Intellectual property (IP) theft is a type of information theft that can severely damage a company, yet it’s often overlooked. Now that attackers have figured out new ways to infiltrate a network and move laterally within a system discreetly, the potential for IP theft has grown. Over time, threat actors can enter a system without being detected, move laterally, mine information, and leave a system before anyone even realizes they were there.
The data that is accessed by the attackers can be stolen or altered. You may not even realize anything happened until you see your company’s trade secrets used elsewhere. This is particularly dangerous for the manufacturing industry because it can be difficult to protect company information that is needed to create products. Now that threat actors can transfer information in seconds, it would be easy for trade secrets, copyrighted information, and contracts to be stolen. Some manufacturing companies have contracts with government agencies and are at risk of APT (nation-state) attacks. The motivation for these attacks can be anything from pure cyber espionage or a desire to gain military secrets.
The Chinese government-linked hacking group named Winnti is an example of how APTs focus on stealing IP to further their goal of cyber espionage. The group runs a massive Chinese government-linked hacking operation that’s worth billions of dollars. They specialize in stealing intellectual property and other data from the U.S. and foreign companies. The group has existed since 2010 and researchers believe they operate on behalf of Chinese state interests. In 2019, Winnti was able to infiltrate corporate computer networks within the technology and manufacturing industry – targeting companies in North America, East Asia, and Western Europe. So far, the group has stolen sensitive documents, blueprints, diagrams, formulas, and manufacturing-related data. They have also stolen source code and research and development documents.
Unfortunately, Winnti had years to conduct reconnaissance and identify valuable data due to the group not being discovered in company systems until 2021. As a result, the group was able to collect hundreds of gigabytes of information that could be used in future cyber attacks. The information stolen includes credentials, employee emails, network architecture, and customer data. The value of the stolen data was not mentioned, however Chinese cyber espionage in general costs the U.S. between $180 billion and $540 billion annually.
The motivation for an intellectual property theft attack has less to do with financial gain and more to do with stealing data. Also, IP theft is difficult for cyber security specialists to detect because the threat actors are simply stealing data as discreetly as possible with no plans for monetary gain. Ransomware attacks are much easier to detect because the threat actors are seeking to gain something financially – often leaving ransomware notes and other evidence that they were in their target’s systems.
supply chain attacks
Supply chain attacks are a serious issue for security regardless of the industry, but in recent years, supply chain attacks within the manufacturing industry have become more prominent. A supply chain attack happens when threat actors access an organization’s network via a third-party vendor or supplier. Access can be gained through viruses or malicious software, giving the attacker keys to sensitive information, customer records, and payment information.
Because a supply chain can be large in scope, the attack itself can be difficult to trace. Naturally, manufacturing organizations and businesses work with dozens of suppliers. Any disruption to the manufacturing process causes a ripple effect and severe delays. It’s important for manufacturing organizations to protect their supply chain and make sure the companies they do business with are equally committed to security. There are three types of supply-chain attacks:
- Software Supply Chain Attacks – this attack requires just one compromised application or piece of software in order to disrupt an entire supply chain. These attacks target an application’s source code and delivers malicious code to a trusted app or software system.
- Firmware Supply Chain Attacks – this attack inserts malware into a computer’s boot record and takes one second to unfold. After the targeted computer boots up, the malware is executed, and an entire system is at risk. These attacks are quick, damaging, and sometimes undetectable.
- Hardware Supply Chain Attacks – this kind of attack depends on physical devices. Threat actors target devices they know will make its way through an entire supply chain to maximize its reach and the damage it will cause.
A great example of a successful supply attack against a manufacturer is February 2022’s attack on Nvidia, the largest microchip manufacturer within the U.S. Avertium published a Threat Intelligence Report featuring Lapsus$’ attack on the microchip giant. Lapsus$ attacked Nvidia and caused outages within their internal network, taking 1TB of schematics, driver and firmware code, documentation, and SDKs. Lapsus$ also leaked a 19GB archive of those files online. Lapsus$ also stole Nvidia’s driver signing certificate, which can be used to sign malware.
Industrial Iot attacks
As we previously stated, for decades the manufacturing industry didn’t believe threat actors were interested in targeting them. They assumed that the Industrial IoT (Internet of Things) devices that they use for daily operations and processes served no purpose for an attacker, therefore developers spent little time ensuring that their IoT devices had basic firewalls or other security controls. When you have little to no concern for security, exploits will happen.
In February 2020, three of the largest manufacturers had their Industrial IoT devices infected with malware. TrapX Security discovered a cryptocurrency miner on several IoT devices including a printer, a smart TV, as well as an automatic guided vehicle manufacturer (AGV). The attacks were a part of a campaign in which attackers embedded systems running Windows 7 with malware. At the time, Windows 7 had reached end-of-life, but millions of PCs worldwide still ran the operating system.
According to Security Week, the malware was a self-spreading downloader that ran on malicious scripts associated with a cryptocurrency miner named Lemon_Duck. The malware spread so quickly on the AGV manufacturing site that it disrupted vehicle communications. AGVs are used to deliver materials or execute certain tasks in a manufacturing plant. If the communications are disrupted or if the commands are generated by malware, it can cause the vehicle to go off track and cause physical damage to things or people.
The vulnerability also affected a smart TV that had a built-in PC running Windows 7. The smart TV was connected to a manufacturing network and the TV provided data to employees in charge of the production line. Because of the Windows 7 vulnerability, an attacker was able to install malware on the TV and deployed a crypto-miner several months prior. This kind of threat could have compromised the entire network, as well as other companies that had assets within the enterprise and manufacturing networks.
In the past, cybersecurity was primarily a critical focus for large enterprises, but things have changed. The engineers who design the devices for manufacturers need to implement strong cyber security features into the devices they design. Vulnerabilities on Industrial IoT devices are often related to issues that are introduced by the user during the operation or installation phase of the device.
Not changing default passwords, not enabling security features, and a lack of firewalls provide entry points for threat actors. Simply eliminating passwords and user controls that welcome weak security options can help keep manufacturing companies safe and help prevent the deployment of vulnerabilities.
How Avertium is Protecting Our CUSTOMERS
The manufacturing industry has a lot of catching up to do when it comes to security. However, it’s not too late for organizations within the industry to take action and start securing their cyber environments. Avertium has advanced services that can help keep your organization safe:
- Avertium recommends utilizing our service for DFIR (Digital Forensics and Incident Response) to help you rapidly assess, contain, eradicate, and recover from a security incident like a malware attack.
- MDR provides an in-depth investigation into potential threats on an organization’s network. Avertium’s risk-based approach to managed security delivers the right combination of technology, field-validated threat intelligence, and resource empowerment to reduce complexity, streamline operations, and enhance cybersecurity resilience. If you need a more advanced security solution, MDR is the next step. MDR is an outsourced security control solution that includes the elements of EDR, enhanced with a range of fundamental security processes.
- Implement XDR as a prevention method. Our XDR is a combination of monitoring software like LogRhythm, Microsoft Azure Sentinel, or AlienVault, combined with endpoint protection such as SentinelOne. XDR platforms enable cybersecurity through a technology focus by collecting, correlating, and analyzing event data from any source on the network. This includes endpoints, applications, network devices, and user interactions.
- Avertium offers Zero Trust Architecture, like AppGate, to stop malware lateral movement.
- Avertium offers Vulnerability Management to provide a deeper understanding and control over organizational information security risks. If your enterprise is facing challenges with the scope, resources, or skills required to implement a vulnerability
- Avertium offers third-party risk monitoring and attack surface management.
- Avertium offers user awareness training through KnowBe4. The service also includes Incident Response Table-Top exercises (IR TTX) and Core Security Document development, as well as a comprehensive new-school approach that integrates baseline testing using mock attacks.
Avertium’s Recommendations
- Intellectual Property Theft
- Identify the most valuable data and know what intellectual property you have and where it may be located.
- Periodically review the user access to your IP and sensitive data.
- Locate your cyber security gaps and weak spots by reviewing user access rights.
- Establish a data security policy.
- Monitor your employees continuously to make sure they are working securely within the corporate network.
- Phishing Attacks
- Have a layered approach to email security by consistently sending phishing simulations designed to evaluate an employee’s familiarity with email phishing attacks.
- Use role-based training to familiarize employees with digital threats.
- Supply Chain Attacks
- Investing in SOC analysts will ensure that your organization’s cyber security infrastructure in examined and that problems are identified.
- Utilize your organization’s red and blue teams and create a fake supply chain attack that mimics a real threat. This will help you identify whether or not your current security practices are enough to stop a threat.
- Password management platforms will help prevent supply chain attacks and will give IT admins insight into employee password practices. This will also enforce password security best practices across the whole organization.
- Vendors should have limited access to your systems and should only have access to what they need to do their job.
- IoT Theft
- Each device should have a strong unique ID.
- Disable unnecessary ports or services.
- Monitor network activity to determine unauthorized use.
- Update your software consistently.
- Ransomware
- Keep your data backed up and check to see that your backups are working properly on a consistent basis.
- Using multi-factor authentication will keep attackers out of your systems and networks.
- Update your software by patching. Not doing so will leave your systems and networks vulnerable to attackers looking to exploit weaknesses.
- Having multiple security systems is ideal. Firewalls, anti-virus software, and spam filters will enable you to detect intrusions quickly.
- Awareness training for your employees is important. They should know how to spot phishing emails to avoid compromising the organization.
MITRE Map(s)
Winnti

Lapsus$
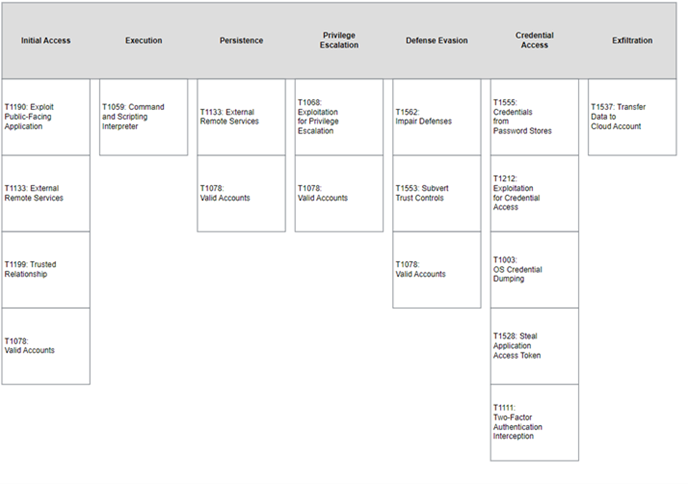
LockBit
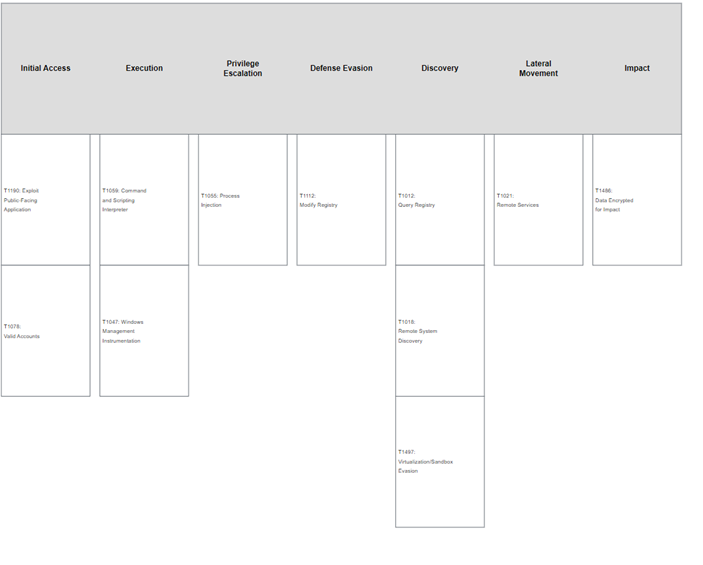
Indicators of Compromise (IoCs)
Winnti
- 0c605276ff21b5150365b7d1991f5904
- 152d5284b9ed6503b01a61ad6df78204
- 6a5bb8dd8e1f6bb18602fca0e309f0e2
- 7cae7510f67d0725d844cc528805780b
- 9dbf67fd22957a6066d08cb366e7c0c9
- 082dbca2c3ca5c5410de9951a5c681f0c42235c8
- 1275894d8231fe25db56598ddcf869f88df5ad8d
- 1316f715d228ae6cc1fba913c6cc309861f82e14
- 2d336978af261e07b1ecfaf65dc903b239e287a4
- 4d1b8791d0715fe316b43fc95bdc335cb31a82ca
- 9139c89b2b625e2ceee2cbf72aef6c5104707a26
- 9267fe0bb6d367fc9186e89ea65b13baa7418d87
- a009a0f5a385683aea74299cbe6d5429c609f2d2
- bb93ae0fee817fe56c31bdc997f3f7d57a48c187
- f2d04fe529e2d8dab96242305255cfb84ce81e9c
- f8d46895e738254238473d650d99bdc92c34ee44
- 714cef77c92b1d909972580ec7602b0914f30e32c09a5e8cb9cb4d32aa2a2196
- 720610b9067c8afe857819a098a44cab24e9da5cf6a086351d01b73714afd397
- 869165044402a5f82f4cb8ddd51663ebb05f86345f346f765dcc54b20706cf7c
- b9d4ec771a79f53a330b29ed17f719dac81a4bfe11caf0eac0efacd19d14d090
- e1e0b887b68307ed192d393e886d8b982e4a2fd232ee13c2f20cd05f91358596
Lapsus$
- zip
- 2no[.co]
- https://cdn.discordapp.com/attachments/879433223103459409/879433370159968306/Setup2[.exe]
- https://cdn.discordapp.com/attachments/879422002287493133/879685414934417479/R24[.bmp]
- https://cdn.discordapp.com/attachments/879422002287493133/879653243217670164/app24[.bmp]
- https://cdn.discordapp.com/attachments/879422002287493133/879653242093600808/sfx_123_201[.bmp]
- https://cdn.discordapp.com/attachments/879422002287493133/879653239560228884/help24[.bmp]
- https://cdn.discordapp.com/attachments/879422002287493133/879653236993318933/Falioca24[.bmp]
- https://cdn.discordapp.com/attachments/879422002287493133/879423887002206228/Passat[.bmp]
- https://cdn.discordapp.com/attachments/879422002287493133/879423620030550088/Real231[.bmp]
- https://cdn.discordapp.com/attachments/879422002287493133/879423245999276102/VerminateMechanize_2021-08-18_15-57[.bmp]
- https://cdn.discordapp.com/attachments/873056123240972371/875681686568992788/E_PL_Client[.bmp]
- https://cdn.discordapp.com/attachments/870454586861846551/870548989903274054/jooyu[.exe]
- https://cdn.discordapp.com/attachments/928009932928856097/936319550855716884/Windows11InstallationAssistant[.zip]
- https://t.me/[minsaudebr]
- ip[.sb]
- lapsusgroup@protonmail[.com]
- 0a7921d68d31d9d6cb23d0060daf018ead026c31069f8147c2127bd7a062578d
- 0c409e9c2ba44bc27e9d26e07deba2ba7372fa7ce4ca67da0696d4322c7e19d0
- 28d71a579fb75cb672af489ce602392b4504f895c3881691a12c51cea7719f4d
- 2c5d8cf9d86b78fdf3eb085e48b5e13989331ae2be1b9793204717f2da76f253
- 39772550650d897f50e3353a601d611e38bc65670e8883a60e0f9ac0a40b774c
- 41dba5cf17e66001306398b1117761d3bfdbf823807282edfa898d21ee08065a
- 42a888e2cf677ed57ea3e072c5ccdbe15492745c4cb14bb3f2d72f4db81a4756
- 57d417306e6d1d2f4943736a43e33818f87666b962107939395d56a500f26968
- 62d9bab3db42901422cbf4ffa5c2f6bd01f3e04f988ae54401216d294b1d5798
- 661913595df0ab71310fb9c3ab56af07c47a4fe9b5f25fb1da7ee0c83b199bca
- 666d848a4ecb284b4b6f70f0e6c8126fff9facb5427dabd0fe7b45502d70f0b2
- 67923efca1ac97b09b579dfd774399eb0327ffe25bf60ecb42a6d3d833639455
- 7b76caa7c924e3271e67f576f4f73b9338b93c579298d76375af493749d6cdbc
- 91922830b0dadc450c785a55789ecdbc801801eb76e029e1c35673ac0ba60f86
- 927965d51c202140e974ea473ed143e701e1ed3b6b34583200d5a8935457a36f
- 9a305e8a3616def77c4c7f18c0c91a7b67544fd4473c209d95b8b614c31a5790
- ae9e7613eb86358cf0c50eb2753c82c605f170fcae1ada510506d037d2987e66
- c33defdd2c60f2d74ebaabbe82805a7a36fa2428cda8c42fd202396b4eda28f6
- d2e03bb72a530d14de71be2c7d4aa2275887113aa2ff6d57f53c57f4a8516365
- f088dac66ed4630d674073125c7562aa3eb283a30bc4bcc162abf0d47458ce8f
- http://81.4.105.174/Dlmfs[.jpg]
- http://81.4.105.174/FileOne[.png]
- http://81.4.105.174/InjectPersistenceF2[.log]
- http://81.4.105.174/Ipqtn[.jpg]
- http://81.4.105.174/Koqomwipj[.jpg]
- http://81.4.105.174/Lavgimu[.jpg]
- http://81.4.105.174/Liafandgotica[.png]
- http://81.4.105.174/Mstst[.log]
- http://81.4.105.174/Prwcwm[.jpg]
- http://81.4.105.174/Qraqpk[.png]
- http://81.4.105.174/Ribtcqqqb[.log]
- http://81.4.105.174/SentinelInstaller[.png]
- http://81.4.105.174/SentinelWiskonsinDam[.jpg]
- http://81.4.105.174/Sifican[.log]
- http://81.4.105.174/Vcdrpuc[.log]
- http://81.4.105.174/VideoPublicAllocation[.log]
- http://81.4.105.174/VirtualAlloc2[.log]
LockBit
- 215.113[.39]
- 60.160.[200]
- 190.143[.101]
- 100.11[.72]
- 138.62[.35]
- 182.193[.120]
- 162.143[.218]
- 38.235[.234]
- 227.255[.190]
- 80.147[.102]
Supporting Documentation
Top 7 Cyber Threats for Manufacturing Companies (bitlyft.com)
IBM Security X-Force Threat Intelligence Index | IBM
Inside the Ring: Report details massive Chinese IP theft - Washington Times
How manufacturers can protect IoT products from cyberattacks (designworldonline.com)
IoT Devices at Major Manufacturers Infected With Malware via Supply Chain Attack | SecurityWeek.Com
Five ransomware attacks in 2022 so far you should know about | Cyber Security Hub (cshub.com)
An In-Depth Look at Pandora Ransomware (avertium.com)
Manufacturing is the ‘Most Targeted’ Industry for Cyber Attacks | Datamation
400 manufacturing companies attacked using TeamViewer and RMS | Kaspersky official blog
What is a Supply Chain Attack? Solutions & Examples | Keeper (keepersecurity.com)
IT, healthcare and manufacturing facing most phishing attacks: report | ZDNet
2021 Manufacturing and Supply Chain Security Roundup (securityintelligence.com)
Manufacturers are bombarded with phishing attacks - Graphus
Why Manufacturing IP is So Susceptible to Cyber Theft - Security Boulevard
An In-Depth Look at Data Extortion Group, Lapsus$ (avertium.com)
An In-Depth Look at Pandora Ransomware (avertium.com)
Inside the Ring: Report details massive Chinese IP theft - Washington Times
What is Intellectual Property Theft and How to Prevent It | Ekran System
The Importance of Securing the Manufacturing Supply Chain (finextra.com)
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.
Related Resource: [Threat Report] The Top 5 Cyber Threats in the Healthcare Industry