The Pitfalls of Online Chat Features
Executive Summary
Online chat features on websites are so common today that most people expect to use them as an effective way of communicating with customer service. Having a live chat option on a website can reduce phone calls to customer service, is efficient, and is convenient for businesses and for customers. However, like all innovative technology, chatbots and live chat features come with their own set of security risks.
While chat software does an excellent job of connecting website visitors to customer service agents in real time, it also can do an excellent job of connecting malicious threat actors to unknowing customer service agents. Also, threat actors can gain access to an organization’s systems and networks through poorly monitored chatbots. Customers that share personal and sensitive information across chats could have that information fall into the wrong hands.
There are ways for organizations to stay safe but continue to provide the convenience of an online chat feature on their site. Let’s look at the pitfalls of online chatbots and live chats, and how organizations can securely chat with customers online.
chat features and Comm100
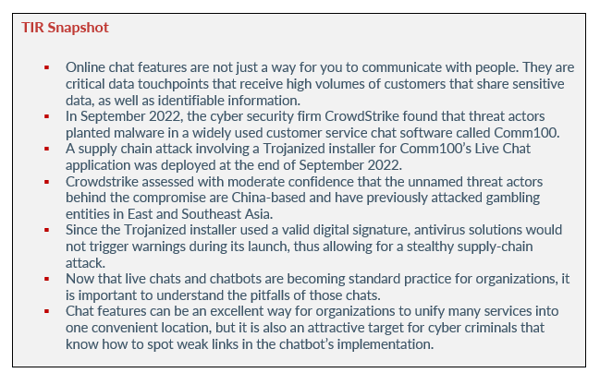
Online chat features are not just a way for you to communicate with people. They are critical data touchpoints that receive high volumes of customers that share sensitive data, as well as identifiable information. Although the efficiency of live chats and chatbots are something both organizations and customers crave, the chats can be and have been breached.
In September 2022, the cyber security firm CrowdStrike found that threat actors planted malware in a widely used customer service chat software called Comm100. The company is based in Vancouver, British Columbia and over 15k customers across 51 countries use the software. According to CrowdStrike, a supply chain attack involving a Trojanized installer for Comm100’s Live Chat application was deployed at the end of September 2022.
CrowdStrike identified the Trojanized file at organizations within the technology, manufacturing, healthcare, industrial, insurance, and telecommunications sectors of North America and Europe. Researchers suspect that the malware was likely present in Comm100’s Live Chat application installer for a few days.
After the attack, Crowdstrike assessed with moderate confidence that the unnamed threat actors behind the compromise are China-based and have previously attacked gambling entities in East and Southeast Asia. According to CrowdStrike, the attribution was made based on the presence of Chinese-language comments within the malware, as well as the following tactics and techniques in connection with the targeting of online gambling entities:
- The use of chat software to deliver malware
- The use of the Microsoft Metadata Merge Utility binary to load a malicious DLL named MidlrtMd.dll
- C2 domain-naming convention using Microsoft and Amazon-themed domains along with api. subdomains
- C2 domains hosted on Alibaba infrastructure
CrowdStrike stated that the attack used a signed Comm100 desktop agent app for Windows which can be downloaded from the company’s website. Also, there was a JavaScript-based implant embedded within the weaponized executable. The implant executed second-stage JavaScript code hosted on a remote server – designed to give the malicious actor stealthy remote shell functionality by spawning new instance cmd.exe.
Post exploitation includes installing additional malicious files on the affected host, including a malicious loader DLL named MidIrMd.dll. This loader decrypts a payload file named license using a customized variant of RC4 encryption with a hardcoded key.
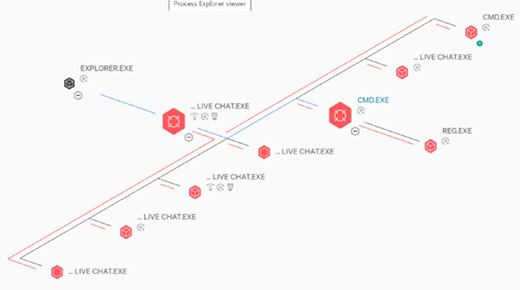
Image 1: Supply Chain Attack via Chat Feature
Source: The Hacker News
Since the Trojanized installer used a valid digital signature, antivirus solutions would not trigger warnings during its launch, thus allowing for a stealthy supply-chain attack. After being compromised, Comm100 released an updated installer and stated they were performing a root cause analysis for additional information. Comm100 did not state how many of their customers were affected.
Although CrowdStrike did not name the threat actor behind Comm100’s attack, the tactics, techniques, and procedures point to a threat actor named Earth Berberoka or GamblingPuppet. The threat actor was seen using a fake chat app called MiMi in their attacks against the gambling industry.
live chat - sendwithus
The communications platform Sendwithus, was almost breached by a threat actor attempting to social engineer a live chat agent. The threat actor tried to gain access to a Fortune 1000 customer’s account but was unsuccessful due to the company’s attitude regarding customer service. Because the company tries to go above and beyond for customers, the unknowing agent was not able provide the access the threat actor was hoping to receive.
Take a look at the conversation below:
“Attacker: Hi, we have employees in COMPANY who needs access in your portal. Do you manage providing access to our employees?
Sendwithus: Ah, you’ll need to get access from an administrator on the account.
This initial question seemed odd, but it didn’t trigger immediate alarm bells with our staff. But the repeated attempts to gain information made us suspicious.
Attacker: hmmm.. and any idea who or how will I know who supposedly this person be?
Attacker: By any chance, you know if COMPANY is tied up or something like that with your company?
Attacker: well maybe for a start, I want to understand the service your company is providing because our employees are requesting access from your portal.” – chat log provided by Matt Harris – CEO and cofounder of Sendwithus
As you can see above, the conversation between the threat actor and the company looks off. If the company didn’t make a concerted effort to understand who account administrators need to be and which users need access to those accounts, the attacker would have likely been successful. In the above case, the customer service agent noticed that the individual on the other end of the chat was not one of the mangers they were familiar with. They also noticed that the customer’s email address was listed as noemail[@]noemail[.]com and not a “@company.com” email address.
Another red flag was the individual’s IP address. The company’s chat service reported that the IP address resulted in an IP block within a reasonable proximity to the “customer’s” headquarters. Additionally, the customer service agent knew that if a chat user was logged into a Sendwithus account, their account information should have been alongside the chat window. In this case, the threat actor was not logged in at all. Due to this evidence, the customer service agent declined to provide information and told the threat actor to contact their internal administrator. The customer service agent successfully thwarted a social engineering attempt that could have resulted in a devastating breach.
seesaw
Despite the difference in apps, the threat actors behind the Seesaw app compromise had the same idea as the threat actors behind Comm100’s breach. In September 2022, parents and teachers from school districts in Illinois, New York, Oklahoma, and Texas were sent an inappropriate photo via Seesaw, an app that is used by 10 million teachers, students, and parents to communicate.
Seesaw stated that the hackers didn’t gain administrative access to Seesaw but they were able to breach user accounts via credential stuffing. Credential stuffing means that an attacker looks through prior data breaches to determine combinations of usernames and passwords. Credential stuffing is why cyber security experts advise against reusing the same username and password for more than one account.
The photo was sent as a link to bitly, a link-shortening service that obscures web addresses. The photo was also sent from some parents’ accounts to other users – appearing as if there was a message sent by a school family.
revolut
In September 2022, the Fintech startup Revolut was breached in a highly targeted attack. The threat actors gained access to the personal information of tens of thousands of customers. According to a Revolut spokesperson, Michael Bodansky, an unauthorized third party gained access to customers for a short period of time.
Although Revolut stated that only 0.16% of their customers were breached, the company has 20 million customers. Revolut mentioned in their breach disclosure that 50,150 customers were impacted. The company declined to say what types of data were accessed but customers noticed something was off on September 11, 2022 when some received inappropriate language via Revolut’s support chat.
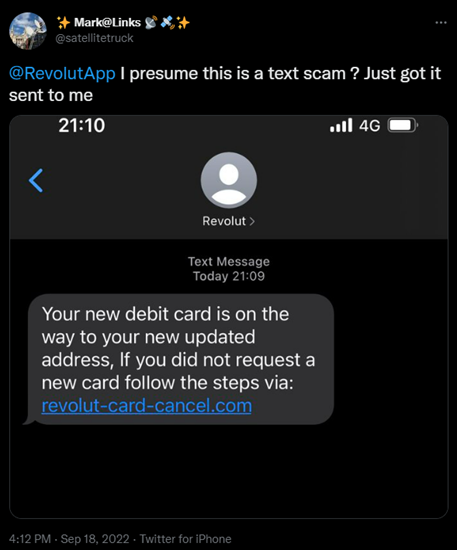
A few days later, customers reported receiving an email saying their account was affected by a cyber attack. After the initial breach, customers began receiving smishing messages stating that their new debit card was on the way, and they simply needed to click a link if they didn’t request a new card.
Image 2: Tweet to Revolut
Source: Twitter
After following the link, users were asked to complete a security challenge to confirm they were not a robot before being asked to solve a visual CAPTCHA. Once that step was completed, users were taken through a set of well-crafted pages that asked them to log into Revolut. Login details included the users phone number, password, full name, email address, debit card information, and date of birth.
how can organizations remain safe?
Now that live chats and chatbots are becoming standard practice for organizations, it is important to understand the pitfalls of those chats. Yes, chat features can be an excellent way for organizations to unify many services into one convenient location, but it also is an attractive target for cyber criminals that know how to spot weak links in the chatbot’s implementation.
They know that if they can find the weak link, they will be able to access many systems.
In addition to the previously mentioned attacks, threat actors can also gain unrestricted access to information via man-in-the-middle attacks. This kind of attack allows them to access a chat conversation and passively monitor the chatlog or alter the messages sent. This is done to carry out a potential phishing attack or trick the end user into giving up personal information.
In 2017, Delta Airline suffered a data breach via their chatbot systems. Threat actors were able to modify the chatbot’s source code, allowing them access to information entered on Delta’s website. Over 825k customers had their sensitive information stolen as a result of the breach.
The outcomes of chatbot attacks include critical threats to organizations, as well as wasted resources. There are some organizations that have started to develop their own chatbots to limit external exposure and risks. However, this option is often too expensive for smaller businesses. Therefore, choosing a trustworthy chatbot operator with strong cyber security practices is likely to be the best option. Chatbot operators with strong cyber security best practices will also monitor their chatbots closely as a part of a larger culture of vigilance.
In addition to choosing the right chatbot operator, organizations should also make sure that all information sent via chat is encrypted and that only those with the right credentials can read the messages if data is intercepted by a threat actor in some way. Additionally, using redundant security practices can boost the security of messages exchanged via chat. One way to boost security is by using payment profiles. This would force users to communicate with chat agents via an account on file rather than entering sensitive information directly.
It is also important to note that any good chatbot provider will test their systems in varying ways to see where they are weak. By doing this, the provider can see how their security systems function. Finally, authenticating users is crucial for security. If possible, authenticate users by having them use a username and password before they can access a chatbot.
When it comes to live chat compromises where an agent could be tricked, there are some best practices that should be followed, including but not limited to:
- Verify – You don’t want to be suspicious and defensive regarding every chat that comes through, but you should always verify who you are speaking to. Your chats should start by checking to see if the user is logged in, if you have talked with them previously, and what account they are associated with.
- Use Official Channels – Only offer support for customers via an organization’s official chat. A ticketing system with a dedicated email or a dedicated phone line for priority support is also helpful.
- Whitelist Acceptable Use – You should have a very limited list of acceptable support items that get handled via chat. All other requests should be escalated to email, ensuring chat times are quick and secure.
- Ask Questions – if something feels off and you are uncertain about a customers’ request, ask your team for help. Sometimes, it takes a team to come to a conclusion regarding a questionable situation.
- Links – When a customer sends a link, be wary of clicking on it. This same idea applies to files that are sent via chat or email.
When trying to secure any environment, redundancy is a best practice organizations should implement. This is the most holistic approach to keeping your organization safe from threat actors. Doing the above over and over again will help keep attackers out of an environment.
How Avertium is Protecting Our CUSTOMERS
The end goal of most threat actors compromising chat features is likely a financial one. Deploying malware/ransomware on a system or network is the easiest way for them to achieve that goal. In conjunction with the recommendations above, Avertium offers the following services to help keep your organization safe:
- Fusion MXDR is the first MDR offering that fuses together all aspects of security operations into a living, breathing, threat-resistant XDR solution. By fusing insights from threat intelligence, security assessments, and vulnerability management into our MDR approach, Fusion MXDR offers a more informed, robust, and cost-effective approach to cybersecurity – one that is great than the sum of its parts.
- Avertium offers VMaaS to provide a deeper understanding and control over organizational information security risks. If your enterprise is facing challenges with the scope, resources, or skills required to implement a vulnerability management program with your team, outsourced solutions can help you bridge the gap.
- Avertium offers Zero Trust Architecture, like AppGate, to stop malware lateral movement.
- Avertium offers user awareness training through KnowBe4. The service also includes Incident Response Table-Top exercises (IR TTX) and Core Security Document development, as well as a comprehensive new-school approach that integrates baseline testing using mock attacks.
- Minimizing the impact of a successful ransomware attack requires detecting it as early in the attack as possible. A Security Information and Event Management (SIEM) system can help an organization to accomplish this. Avertium offers a comprehensive SIEM-based approach that increases the potential for detecting a ransomware infection before it deploys. SIEM provides a holistic overview of a company’s IT environment from a single point of view in terms of its specific security events, empowering teams to detect and analyze unusual behavior
avertium's recommendations
- Customer Service Agents:
- Verify – You don’t want to be suspicious and defensive regarding every chat that comes through, but you should always verify who you are speaking to. Your chats should start by checking to see if the user is logged in, if you have talked with them previously, and what account they are associated with.
- Use Official Channels – Only offer support for customers via an organization’s official chat. A ticketing system with a dedicated email or a dedicated phone line for priority support is also helpful.
- Whitelist Acceptable Use – You should have a very limited list of acceptable support items that get handled via chat. All other requests should be escalated to email, ensuring chat times are quick and secure.
- Ask Questions – if something feels off and you are uncertain about a customers’ request, ask your team for help. Sometimes, it takes a team to come to a conclusion regarding a questionable situation.
- Links – When a customer sends a link, be wary of clicking on it. This same idea applies to files that are sent via chat or email.
- Organizations:
- If possible, develop your own chatbots to limit external exposure and risks.
- Choose a trustworthy chatbot operator with strong cyber security practices is likely to be the best option.
- Chatbot operators with strong cyber security best practices will also monitor their chatbots closely as a part of a larger culture of vigilance.
- Use redundant security practices to boost the security of messages exchanged via chat.
- One way to boost security is by using payment profiles. This would force users to communicate with chat agents via an account on file rather than entering sensitive information directly.
- Any good chatbot provider will test their systems in varying ways to see where they are weak. By doing this, the provider can see how their security systems function.
- If possible, authenticate users by having them use a username and password before they can access a chatbot.
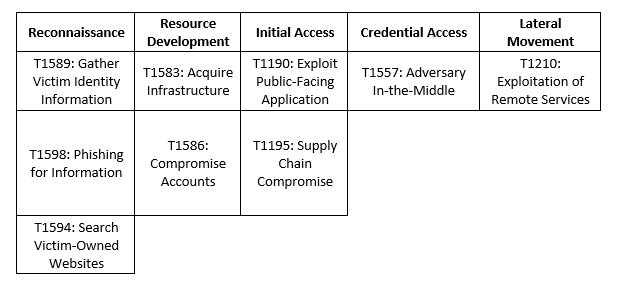
MITRE Map
Indicators of Compromise (IoCs)
Hashes
- 6f0fae95f5637710d1464b42ba49f9533443181262f78805d3ff13bea3b8fd45
- ac5c0823d623a7999f0db345611084e0a494770c3d6dd5feeba4199deee82b86
- ac9f2ae9de5126691b9391c990f9d4f1c25afa
- 912fbfda2d4abfe9f9057bdd8c
- c930a28878a5dd49f7c8856473ff452ddbdab
- 8099acd6900047d9b3c6e88edca
Network Indicators
- http[:]//api.amazonawsreplay[.]com/collect_log
- http[:]//api.amazonawsreplay[.]com
- http[:]//api.amazonawsreplay[.]com/livehelp/init
- http[:]//api.microsoftfileapis[.]com
- https[:]//selfhelp[.]windowstearns[.]com
- http[:]//api.amazonawsreplay[.]com/livehelp/collect
Supporting Documentation
Live Chat Security | Secure Chat Solution | Provide Support
Hackers Compromise Corporate Chat Software | Silicon UK Tech
Live Chat Security: Everything You Need to Know for Secure Live Chat - Comm100
Live chat and customer data security | WhosOn
Comm100 Chat Provider Hijacked to Spread Malware in Supply Chain Attack (thehackernews.com)
Comm100 Usage Statistics (builtwith.com)
Delta Sues Chatbot Provider Over 2017 Breach - WSJ
Comm100 Chat Provider Hijacked to Spread Malware in Supply Chain Attack (thehackernews.com)
Popular school messaging app hacked to send explicit image to parents (nbcnews.com)
Revolut confirms cyberattack exposed personal data of tens of thousands of users | TechCrunch
Revolut data breach: 50,000+ users affected - Help Net Security
Live support service hacked to spread malware in supply chain attack (bleepingcomputer.com)
If your web site offers live chat, be prepared for hackers (venturebeat.com)
New APT Group Earth Berberoka Targets Gambling Websites With Old and New Malware (trendmicro.com)
Chatbots Gone Rogue: How Weak Chatbot Security Enables Bad Actors (alacriti.com)
Threat Actor Delivered Malware Via Trojanized Live Chat Installer | Decipher (duo.com)
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.