- WHY AVERTIUM?
-
-
Why Avertium?
Context over chaos. Disconnected technologies, siloed data, and reactive processes can only get you so far. Protecting businesses in today’s threat landscape demands more than a set of security tools – it requires context.
That's where Avertium comes in
-
Considering Microsoft?
Avertium Named Microsoft Security Solutions PartnerAvertium’s managed services for Microsoft Security Solutions is delivered through the company’s premium service: Fusion MXDR. Fusion MXDR includes 24x7 monitoring and management of Defender for Endpoint and Sentinel, threat intelligence, attack surface
monitoring, and vulnerability management for Microsoft Security customers. -
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- SOLUTIONS
-
-
Governance, Risk, + Compliance
GRC with context – not complexity. -
Attack Surface Management
No more blind spots, weak links, or fire drills. -
Threat Detection + Response
Detect, adapt, and attack with context. -
Microsoft Security Solutions
End-to-end support from strategy to daily operations to maximize your Microsoft Security.
-
-
- COMPANY
-
-
About Us
Security. It’s in our DNA. It’s elemental, foundational. Something that an always-on, everything’s-IoT-connected world depends on.
Helping mid-to-enterprise organizations protect assets and manage risk is our only business. Our mission is to make our customers’ world a safer place so that they may thrive in an always-on, connected world.
-
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- PARTNERS
-
-
Our Partners
Best-in-class technology from our partners... backed by service excellence from Avertium.
-
Partner Opportunity Registration
Interested in becoming a partner?
With Avertium's deal registration, partners can efficiently and confidently connect with Avertium on opportunities to protect your deals.
-
Latest Avertium Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- NEWS & RESOURCES
-
-
News & Resources
Dive into our resource hub and explore top
cybersecurity topics along with what we do
and what we can do for you. -
Latest Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- CONTACT
TIR-20221219: Stay Vigilant with Cybersecurity During the Holidays
Executive Summary
During the holiday season, people tend to become so wrapped up with spending time with loved ones and spreading good cheer, that they get lax with making sure their cyber environments are safe. Researchers have reported an observed increase in ransomware attacks during the holidays and on weekends. The attacks on Kaseya and SolarWinds happened during holidays, and experts warn that there will be no shortage of attacking during the 2022/2023 holiday season.
Last year, Avertium reported that cyber attacks tend to take place during the holiday season when threat actors know organizations have less staff. Although this is a different year, the same best practices that applied last year, apply this year as well. Let’s look at why organizations and individuals should be consistent with using cyber security best practices during the holiday season.
holiday cyber attacks & the damage they cause
At the end of August 2021, the weekend just before Labor Day, CISA issued a warning regarding ransomware awareness during the holiday weekend. They observed an increase in ransomware attacks occurring during a time when most people are off from work. Threat actors know that holidays mean limited staff and resources, making it a prime time for an attack.
Researchers at Infosecurity Magazine recently reported that over 57% of attacks targeting retail websites in 2021 were carried out by sophisticated bots. The bots tried to hijack customers’ accounts and steal personal and financial information. The bots are actually capable of mimicking human mouse movements and clicks to confuse any retailers’ cyber security defenses. Bot driven cyber attacks have the potential to worsen existing supply-chain issues, threatening stock availability. It’s expected that these kinds of attacks will continue into the holiday season.
kaseya
During the Fourth of July weekend, the IT management software company, Kaseya, experienced a massive supply-chain cyber attack. The attack, orchestrated by ransomware gang REvil, impacted 1,000 businesses in 17 countries. After realizing the breach, Kaseya instructed customers by way of a security advisory on their website, to shut down their VSA servers to stop the spread of the attack while it was being investigated. Researchers reported that REvil intentionally waited until the Fourth of July weekend to strike.
REvil successfully orchestrated the largest ransomware attack in history by exploiting multiple zero-day vulnerabilities in Kaseya’s on-premises VSA product. Because of these vulnerabilities, REvil was able to deploy a ransomware encryptor to connected endpoints. The gang demanded a ransom of $70 million for a universal decryptor key (later dropping to $50 million).
colonial pipeline
During May 2021, leading into Mother’s Day weekend, DarkSide deployed ransomware against the Colonial Pipeline. This attack took down the largest fuel pipeline in the United States and resulted in a week-long suspension of operations across the East Coast. There were gas outages in Georgia, Alabama, Tennessee, Florida, Virginia, Maryland, North Carolina, and South Carolina.
Darkside gained entry into the Colonial Pipeline Company’s network through a virtual private network account. The virtual private network allowed employees to remotely access the company’s computer network. While the account was no longer being used when the attack happened, DarkSide was still able to access it. It was later discovered that the password for the account was discovered on the dark web, which means a Colonial Pipeline employee more than likely used the same password on another account that was previously hacked. Additionally, the VPN account didn’t use multifactor authentication, which allowed DarkSide to breach the Colonial Pipeline network by using a stolen username and password.
jbs
United States based food processing company, JBS, is another organization that was compromised during a holiday weekend. On May 30, 2021, right before Memorial Day weekend, JBS announced that they were the target of an organized cyber attack by REvil, affecting servers supporting North American and Australian IT systems. REvil infected the company’s systems with malware and demanded a ransom for decryption.
As a result, JBS had to take portions of their systems offline and paid REvil $11 million in bitcoin to avoid further disruption of their business. The company was able to continue operations through their backups, but they lost $11 million by paying the demanded ransom. Even though JBS paid the ransom to prevent the malware from spreading or returning, there is no guarantee that REvil won’t target them again. Threat actors seek one thing, money, and paying large ransoms can lead to double extortion.
retailers and fedex
Supply-chain cyber attacks are the most prominent during the Christmas shopping season and retailers often struggle with prevention. In 2017, an exploit called NotPetya attacked large electric utilities and stalled the operation of many retailers. NotPetya infected computers, as well as data and wired machines globally – extracting data and demanding massive amounts of money in the form of Bitcoins. The attack occurred during the Christmas season and although it was intended to cripple the Ukraine, the attack was felt around the world.
Not only did the NotPetya attack disrupt utility operations, but it also affected shipping companies like FedEx and Maersk who deliver orders for retailers. Things became so bad that FedEx had to resort to manual processes for pick-up, sorting, and delivery. Some of Maersk’s corporate network systems for its container business were paralyzed, which prevented retail customers from booking ships and from receiving quotes. The NotPetya attack caused more than $10 billion total loss in damages, making it the most devastating cyber attack in history.
A supply-chain disruption like NotPetya can cause catastrophic harm to a brand’s reputation and financial performance. Couple the disruption with the holiday season and you are looking at devastation beyond what most retailers can fathom.
why threat actors attack during the holiday season
Unfortunately, threat actors know that most organizations operate on a skeleton crew during the holidays. It’s no coincidence that Target’s massive breach in 2013 happened a day before Thanksgiving, and SolarWinds was breached just before Christmas in 2020. Attackers look forward to employees being out of town during U.S. holidays and they plan accordingly.
Major U.S. holidays mean that there’s less staff keeping an eye out for threats, which means more opportunities for attackers to make their move. If employees are out of town or enjoying time off with family, it’s more difficult to react and to react quickly to an attack making its way through a company’s network. This extra time gives threat actors leverage and the chance to try various passwords and usernames, as well as extend their reach to more devices.
During these vulnerable moments, companies have been known to call a third party to deal with an attack or pay a large ransom before the holiday weekend or season ends. According to a report by security firm, BlackFog, Ransomware attacks grew by 150% in 2020 and the damages of cybercrime may reach $6 Trillion this year (up from $3 Trillion in 2015). Protecting your company and employing monitoring tools while employees are away or during an influx in customers is imperative.
social engineering
Social Engineering is also an enormous threat and serves as one of the primary techniques for initiating a cyber attack. The holiday season presents a particular vulnerability, as traveling employees usually set automatic out-of-office (OOO) replies directing people to another employee who can assist them.
An attacker can use these OOO messages to target the working employee with phishing-emails, pretending to be the OOO employee. Generally, the attacker will request special access to proprietary systems while masquerading. If your company has people working (even while out of the office) during the holidays, this vulnerability is likely to be exploited.
How Avertium is Protecting Our CUSTOMERS
- Minimizing the impact of a successful ransomware attack requires detecting it as early in the attack as possible. A Security Information and Event Management (SIEM) system can help an organization to accomplish this. Avertium offers a comprehensive SIEM-based approach that increases the potential for detecting a ransomware infection before it deploys. SIEM provides a holistic overview of a company’s IT environment from a single point of view in terms of its specific security events, empowering teams to detect and analyze unusual behavior.
- Today’s attack surface extends beyond your physical IT assets, now encompassing your entire digital footprint. This expansion has fundamentally changed the surface area that security teams must protect. Gone are the days of vulnerability management serving as an adequate defense for your attack surface… today’s cybersecurity professionals have to think bigger: they have to think about attack surface management (ASM). Avertium offers Attack Surface Management and 3rd Party Vendor Risk services to keep your organization ahead of the curve.
- Avertium also offers continuous monitoring of the threat landscape with automatic synchronization of IoCs into our MDR/XDR platforms
- Avertium offers 24x7 MDR/XDR alert monitoring over the holidays
- KnowBe4 also offers a Holiday Cybersecurity Resource Kit to help equip end users with information and educate them on social engineering attacks.
avertium's recommendations
- Remote work environments seem to be the new normal for a lot of organizations these days. It’s important to recognize that this new working environment opens the door for attackers to infiltrate systems and networks. The attack on the Colonial Pipeline is a good example of becoming lax with safety requirements for remote employees. If an organization has remote employees, Avertium recommends the following:
- Give instructions to employees for accessing company systems from the outside. If an organization uses a secure VPN connection, employees should be required to use it and no other. Don’t allow employees to find their own solutions.
- Have employees address the security of their home networks. Personal computers are an easy way for attackers to gain access to networks. Ensuring employees have passwords to home routers and the proper firewalls lowers the chances of an attack.
- Have employees change passwords frequently and maintain a list of applications that are approved. The fewer the applications that need to be patched, the better.
- If an employee suspects an attack on their home system, it should be reported immediately.
- Train employees on popular attack methods like phishing. Avertium offers training through KnowBe4to help keep your employees informed and safe.
- Out-of-Office Replies
- Avertium recommends encouraging employees to avoid all work-related activities while away from work.
- Ensure that access to systems and resources is shared throughout the company so there is never a legitimate need to contact an employee who’s on vacation. Any such requests should be an immediate red flag to leadership as it could be an attacker attempting to breach your environment.
- Recommendations for Retailers
- Monitor third-party vendor risk with Avertium’s Attack Surface Management Service (ASM). Supply chain ecosystems can be overwhelmingly large, but history has taught that security issues impacting an organization can disrupt the broader system.
- Identify and manage network accounts held by your third-party vendors and service providers. Don’t give organizations full reign and ensure that each vendor has an email account managed by the retailer, not the supplier and not themselves.
- Be diligent with monitoring for changes. Have solutions and strategies in place that provide a real-time and quantifiable idea of supplier security to ensure there are no threats that could impact your business or your customers.
- Holiday change freezes must be approved by special committees. To avoid disruptions in service, Avertium recommends to halt changes during the holiday season.
- Ensure the organization has an off-line backup of data.
- General Tips for Protecting Yourself from Cyber Threat During the Holidays
- Keep a clean machine. Before picking out that perfect gift, be sure that all internet-connected devices ‒ including PCs, smartphones, and tablets ‒ are free from malware and infections by running only the most current versions of software, web browsers and other apps.
- Use secure Wi-Fi. Using free public Wi-Fi to shop online while at your favorite coffee shop is tremendously convenient, but it is not cyber safe. Don’t make purchases while connected to public Wi-Fi; instead use a virtual private network (VPN) or your phone as a hotspot.
- Lock down your login. Create long and unique passphrases for all accounts and use multi-factor authentication wherever possible. Multi-factor authentication will fortify your online accounts by enabling the strongest authentication tools available, such as biometrics or a unique one-timecode sent to your phone or mobile device.
- Resist the urge. Be wary of offers too good to be true – no matter how tempting they might be. Buy only from trusted and established online retailers and avoid websites of retailers you’ve never heard of.
- Think before you click. Pay attention to emails you receive. Don’t open emails from unknown senders or click on links in suspicious messages.
- Shop securely. Not only should you make sure your internet connection is secure. Check to make sure you’re shopping on a site that uses SSL protection. The easiest way to tell is to check your browser’s address bar. Look for https is the URL. Sites without the s are not safe to submit payment information or other personal details.
- Pay wisely. Use a credit card or pre-paid debit card instead of a debit card linked to your bank account. Or use a reliable, established third-party payment service, such as Google Pay, Apple Pay or PayPal.
- Monitor your accounts. Check your online financial accounts regularly for suspicious spending. Also, take advantage of text and email alerting services that many banks and credit card companies now offer.
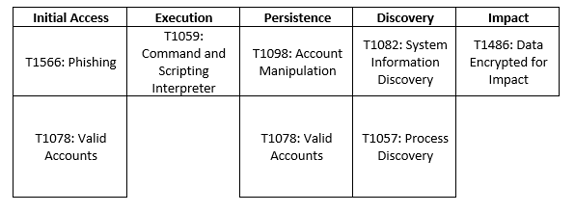
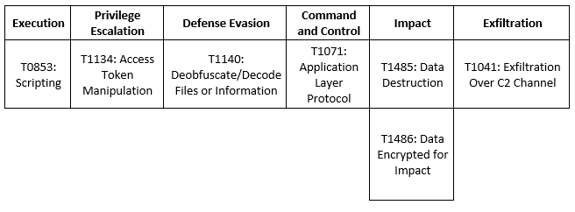
MITRE Map
DarkSide
REvil
Indicators of Compromise (IoCs)
REvil
- 4a91cb0705539e1d09108c60f991ffcf
- 4b4c98ac8f04680f7c529956cfe8519b
- 4d674a7b4159f4e319a2ce3f80d9770c
- 561cffbaba71a6e8cc1cdceda990ead4
- 57191a04cf06228c0643cc99b252ad1e
- 610c9c5f0686dfc0fcd6d68778ce5025
- 612b61376219736601d49d2001645b30
- 64f7ac45f930fe0ae05f6a6102ddb511
- 6522e8c9e387b09b42fce2c1e3ab702a
- 67e49cfcd12103b5ef2f9f331f092dbe
- 699f256b79697ee9ed64085b9147e9b8
- 6bb2471eadf06c5569d59b7c59032119
- 6eb69acd2ac82be838c8b3d8910b0d70
- 72252bba9d1670c42d19f16d17e0e269
- 72a589da586844d7f0818ce684948eea
- 79f2341510d9fb5291aefc3e69d18253
- 7d113ca1ae3f5d652e95a7235bb5f500
- 7d1807850275485397ce2bb218eff159
- 7ea501911850a077cf0f9fe6a7518859
- 7ee222438c0df7ce6f440572c4b79ca4
- 832c01c4a1149a793773a2acb39bb10b
- 849fb558745e4089a8232312594b21d2
- 85a62b3356f96a883d6e112a982a96aa
- 8b868c29f9683f77cd20ef17d2f8973b
- 8d84df31c8b92febddeca8c6f04c5d54
- 927a21de29cca731a1530884b5ecd182
- 9478050023c7f8668df4fc39b0ddd79c
DarkSide
- Owa[.]speedjudgmentacceleration[.com]
- hxxp://royalbank.accesslogs-2-2[.com/]
- hxxps://emailhost.]network/National-Conference-2021
- hxxps://factsreporter[.com]/2016/11/16/news-review-equity-residential-nyseeqr-tesla-motors-inc-nasdaqtsla/
- hxxps://factsreporter[.com]/2018/01/19/trending-stocks-in-review-builders-firstsource-inc-bldr-summit-hotel-properties-inc-inn/
- hxxp://www.pinkoak[.org]/
- hxxps://www.pinkoak[.org]/
- demo[.]speedjudgmentacceleration[.com]
- demo[.]store.speedjudgmentacceleration[.com]
- ]scrgabvdubdhjpq.speedjudgmentacceleration[.com]
- shop[.]store.speedjudgmentacceleration[.com]
- test[.]old.speedjudgmentacceleration[.com]
- wordpress[.]speedjudgmentacceleration[com]
- speedjudgmentacceleration[.com]
- speedjudgmentacceleration[.com]
- [hxxp://]speedjudgmentacceleration.com:443/
- hxxp://website.speedjudgmentacceleration[.com]/
- hxxps://website.speedjudgmentacceleration[.com]/
- [hxxp://]klant-herstel.club/IngMaps
- [hxxp://]klant-herstel.club/ax
Supporting Documentation
Ransomware Awareness for Holidays and Weekends | CISA
Why company hacks like the REvil ransomware attack tend to happen over holiday weekends | Fortune
FBI, CISA warn of potential cyberattacks over holiday weekends | ZDNet
Why company hacks like the REvil ransomware attack tend to happen over holiday weekends | Fortune
Colonial Pipeline Cyber Attack: Hackers Used Compromised Password - Bloomberg
Colonial Pipeline attack: Everything you need to know | ZDNet
JBS USA cyber attack affecting North American and Australian systems | ZDNet
The State of Ransomware in 2021 | BlackFog
EDR vs. MDR: Which Threat Detection is Right for You? (avertium.com)
How the Cyber Grinch Stole Christmas: Managing Retailer Supply Chain Cyber Risk - Security Boulevard
JBS paid hackers $11M ransom to avoid further disruption | Cybersecurity Dive
Holiday Cybersecurity Tips | NCDIT
Ransomware Awareness for Holidays and Weekends | CISA
Attack Surface Management vs. Vulnerability Management (avertium.com)
Stay Vigilant With Cybersecurity During the Holidays (avertium.com)
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.