Monti Ransomware
executive summary
Monti ransomware, known for its versions on both Windows and Linux systems, grabbed the attention of cybersecurity experts in June 2022. The ransomware became noticed not only for its similar name to the notorious Conti ransomware but also for its use of similar tactics.
Monti intentionally copied the tactics, techniques, and procedures (TTPs) of the Conti team. They even incorporated many of Conti's tools and took advantage of Conti's leaked source code. Since its discovery, the Monti ransomware group has been consistently targeting companies and exposing their data on their leak site. Let’s look at Monti, their tactics and techniques and their motive for attacks.
tir snapshot
- Monti ransomware was discovered by researchers in June 2022. The group drew attention due to operating like the now defunct, Conti ransomware group.
- In September 2022, Blackberry's Incident Response team investigated a security incident linked to Monti.
- The threat actor had exploited the well-known Log4Shell vulnerability on a client's internet-facing VMware Horizon virtualization system.
- Once Monti gained entry to the victim's VMware Horizon Connection Broker server through the Log4Shell exploit, they proceeded to install Google Chrome and used it for downloading attack tools onto the server.
- After taking a hiatus, Monti came back in August 2023 with a new Linux-based Monti variant (Ransom.Linux.MONTI.THGOCBC).
- The researchers at Trend Micro reported that there are notable differences from previous Linux-based versions.
- One difference being the use of the "--type=soft" parameter to shut down virtual machines on the system instead of the previous "--type=hard" option. This may have been done to evade detection.
- Monti's code enhancements indicate their desire to improve evasion of detection and their desire to make it difficult for security professionals to detect and mitigate their actions.
monti ransomware
2022
As previously stated, Monti ransomware was discovered by researchers in June 2022. The group drew attention due to operating like the now defunct, Conti ransomware group. Not only is the group’s name similar to Conti’s but Monti’s TTPs are similar as well. Monti has been observed targeting companies in the legal and government sectors, posting their breaches to a data leak site built by the operators.
In September 2022, BlackBerry's Incident Response team investigated a security incident linked to Monti. The threat actor had exploited the well-known Log4Shell vulnerability on a client's internet-facing VMware Horizon virtualization system. During the investigation, it was found that Monti had encrypted 18 user desktops and compromised a three-server ESXi cluster, affecting a total of 21 virtualized servers.
Once Monti gained entry to the victim's VMware Horizon Connection Broker server through the Log4Shell exploit, they proceeded to install Google Chrome and used it for downloading attack tools onto the server. They also downloaded and installed AnyDesk and Action1, which are remote monitoring and maintenance agents.
The attackers, armed with their own tools, extracted login credentials from computer memory and scanned the network. They used Microsoft Windows' built-in Remote Desktop Protocol (RDP) to link to other servers, link to shared network files, and, in the end, introduce the Monti ransomware strain. Their goal was to encrypt several hosts in the network, including those containing Veeam-based backups. Here is a list of various tools leveraged by Monti:
- Action1 RMM
- AnyDesk RMM
- Avast Anti-rootkit driver
- GMER
- MEGASync
- Mimikatz
- netscan (and netscan64)
- PSEXEC
- PuTTY
- Veeam-Get-Creds
- Veeamp
- WinRAR
- WinSCP
Another key takeaway is that this was the time researchers from the Malware Hunter Team discovered that Monti’s encrypted files seemed similar to encrypted files by a Conti version, which suggested codebase reuse. They also noticed that Monti’s ransomware note was very similar to Conti’s, with only two minor changes.
- Monti’s TOR-based URL for contacting the threat actors was unique.
- The beginning sentence of the note states “Monti” instead of “Conti” (but the rest of the verbiage is straight out of Conti’s playbook).
Image 1: Monti's Ransomware Note
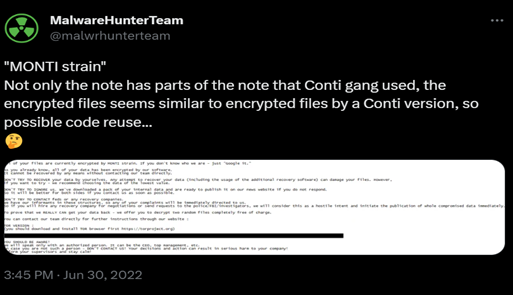
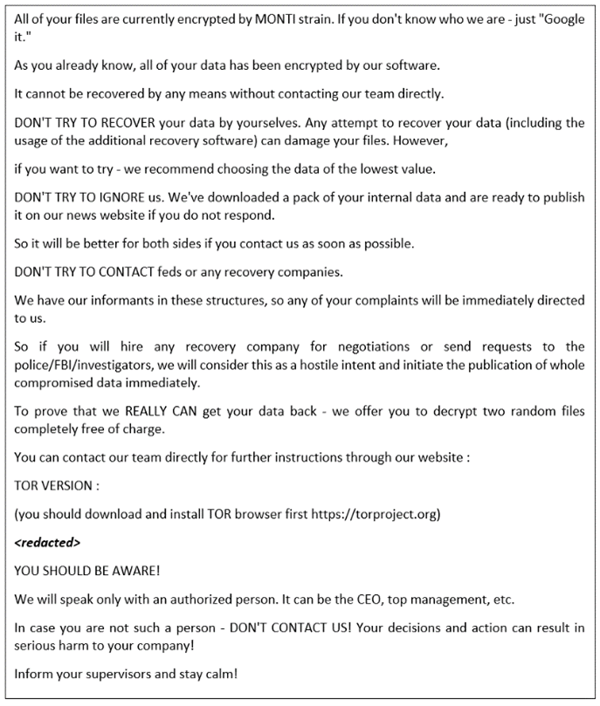
Source: BlackBerry
After initial analysis, Black Berry’s Incident Response team found that the file they examined closely matched the characteristics of the locker.exe executable found in the Conti v3 code leaks, such as file name, size, compile time, and import table hash. Most section hashes also matched, except for the .data section, strengthening the evidence that the file is a Conti v3 payload.
Further investigation showed that while the code within the leaked Conti executable was identical to the team’s sample, running the Conti payload didn't actually encrypt any files.
Examining the .data section of the leaked locker.exe revealed its purpose. The presence of certain strings like DECRYPT_NOTE, .EXTEN, and publickey suggested that the file served as a template for creating functional ransomware payloads.
2023
After taking a hiatus, Monti came back in August 2023 with a new Linux-based Monti variant (Ransom.Linux.MONTI.THGOCBC). The researchers at Trend Micro reported that there are notable differences from pervious Linux-based versions. Unlike the previous variant, which relied heavily on Conti’s leaked source code, this new version uses a different encryption method and exhibits unique behaviors. When comparing the new variant to the old one, the researchers found that Monti’s new code base is only 29% similar to Conti’s leaked code, as opposed to the previous 99% similarity rate.
The new Linux version is meant to target VMware ESXi servers, legal, and government organizations. There are some notable modifications in the new version which include:
- The new Linux version now supports specific command line arguments, removing some from the older version and introducing the --whitelist
- The latest version now uses the "--type=soft" parameter to shut down virtual machines on the system instead of the previous "--type=hard" option. This change to "--type=soft" indicates that Monti might have opted for this method to reduce the chances of immediate detection while carrying out activities.
- Also, the developers manipulated the /etc/motd and html files, substituting their content with a ransom message declaring the successful infiltration of the server.
- The new variant adds the characters "MONTI" along with an additional 256 bytes that are related to the encryption key.
- The new version of the malware adds the ".MONTI" extension to files it encrypts and creates a ransom note called 'readme.txt' in each directory it processes.
Trend Micro’s analysis also found that the new variant uses AES-256-CTR encryption via the OpenSSL library’s evp_enc – a departure from the old variant’s use of Salsa2020. The researchers also discovered that their analyzed sample employs different encryption methods for files. However, the previous method utilized a --size argument to determine how much of a file to encrypt. The new variant solely relies on the file size for its encryption process.
Similar to earlier versions, the latest version adds the .monti file extension to files that it encrypts and places its ransom note, named readme.txt, in each affected directory. The ransom note does not read differently than the one from 2022.
defense
Monti used some elements of the Conti source code as a foundation for their new variant, which is apparent due to similar functions. However, they made substantial modifications to the code, particularly to the encryption algorithm. These code enhancements not only indicate Monti’s intent to improve evasion of detection but the group also wants to make it even harder for security professionals to detect and mitigate their actions.
To safeguard your organization, consider these recommendations based on Monti's TTPs:
- Patch Log4Shell Vulnerability: Ensure that your systems are promptly patched and updated to address the Log4Shell vulnerability. Monti has been known to exploit this vulnerability to gain access to systems.
- Application Whitelisting: Employ application whitelisting to allow only trusted applications to run on your systems. This can help prevent unauthorized or malicious software, like Monti, from executing.
- Network Segmentation: Isolate critical systems from less critical ones through network segmentation. This limits lateral movement if an attacker gains initial access.
- Regular Backups: Continue to maintain regular backups of your data, ensuring that they are isolated and secure. Test your backups periodically to confirm their effectiveness in case of ransomware attacks.
- User Training: Continuously educate your employees about cybersecurity best practices, including how to spot phishing attempts and suspicious behavior.
- Monitoring and Logging: Maintain robust monitoring and logging capabilities to detect and investigate suspicious activities promptly.
- Incident Response Plan: Develop and regularly update an incident response plan that includes specific procedures for dealing with Monti or similar ransomware attacks.
How Avertium is Protecting Our Customers
It’s important to get ahead of the curve by being proactive with protecting your organization, instead of waiting to put out a massive fire. Avertium can provide the following services to help keep your organization safe from Monti ransomware attacks:
- Fusion MXDR is the first MDR offering that fuse together all aspects of security operations into a living, breathing, threat-resistant XDR solution. By fusing insights from threat intelligence, security assessments, and vulnerability management into our MDR approach, Fusion MXDR offers a more informed, robust, and cost-effective approach to cybersecurity – one that is greater than the sum of its parts.
- Expanding endpoints, cloud computing environments, and accelerated digital transformation have decimated the perimeter in an ever-expanding attack surface. Avertium offers Attack Surface Management, so you’ll have no more blind spots, weak links, or fire drills. See every threat in your attack surface, every device, every entry point, and every vulnerability. Our Attack Surface Management services include:
- Risk Assessments
- Pen Testing and Social Engineering
- Infrastructure Architecture and Integration
- Zero Trust Network Architecture
- Vulnerability Management
- Minimizing the impact of a successful ransomware attack requires detecting it as early in the attack as possible. A Security Information and Event Management (SIEM) system can help an organization to accomplish this. Avertium offers a comprehensive SIEM-based approach that increases the potential for detecting a ransomware infection before it deploys. SIEM provides a holistic overview of a company’s IT environment from a single point of view in terms of its specific security events, empowering teams to detect and analyze unusual behavior.
MITRE MAP
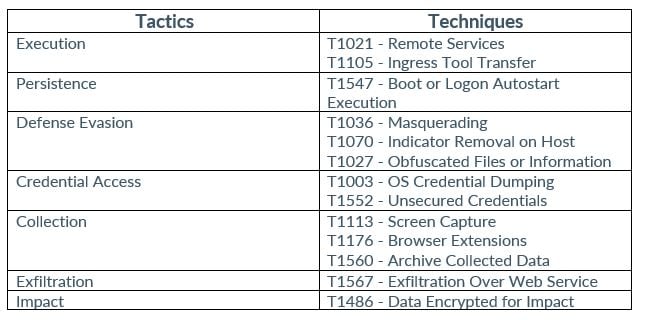
INDICATORS OF COMPROMISE (IOCs)
URLs
- hxxp://monti5o7lvyrpyk26lqofnfvajtyqruwatlfaazgm3zskt3xiktudwid[.]onion
- hxxp://mblogci3rudehaagbryjznltdp33ojwzkq6hn2pckvjq33rycmzczpid[.]onion
SHA1
- f1c0054bc76e8753d4331a881cdf9156dd8b812a
- a0c9dd3f3e3d0e2cd5d1da06b3aac019cdbc74ef
- 13ab5762ff5023163b1ca7c7749112b3673cd3db
- 2bde2bb7b02950999daba6df694a587d80ad9207
- 65f71c07e76c2452022158537107490677629d51
MD5
- 4f70ac14f40c1a580203c7883ed07671
- 573a63e2cdedbbae968942f8ea361ad8
- b774d0ad0ae7a9d3ec00281bc8682cd2
- 1d134f4db4319c99568293b2c2601b3db7c5b91a
- 6c8d2b7035721dd184597cfd2864b0afd28d7bd2
- 9e015d3a92977db7deb1027ed1bd5ff85f7ca247
- 158dcb26239a5db7a0eb67826178f1eaa0852d9d86e59afb86f04e88096a19bc
- 702099b63cb2384e11f088d6bc33afbd43a4c91848f393581242a6a17f1b30a0
- b45fe91d2e2340939781d39daf606622e6d0b9ddacd8425cb8e49c56124c1d56
- 6345ac3f61b9f4ce64e82d3896baf1fa
- 9325f2301ad9e5fb4cf5673fa64446ae
- c924c22fadbe9fa6ae67df401aa03d13
SHA256
- 78517fb07ee5292da627c234b26b555413a459f8d7a9641e4a9fcc1099f06a3d
- 9aa1f37517458d635eae4f9b43cb4770880ea0ee171e7e4ad155bbdee0cbe732
- df492b4cc7f644ad3e795155926d1fc8ece7327c0c5c8ea45561f24f5110ce54
Domain
- dropmefiles.com[.]ua
Supporting Documentation
The Curious Case of “Monti” Ransomware: A Real-World Doppelganger (blackberry.com)
Ransomware Roundup – Monti, BlackHunt, and Putin | FortiGuard Labs (fortinet.com)
Monti Ransomware Unleashes a New Encryptor for Linux (trendmicro.com)
Monti, the New Conti: Ransomware Gang Uses Recycled Code (darkreading.com)
Monti ransomware targets VMware ESXi servers with new Linux locker (bleepingcomputer.com)
Monti Ransomware Unleashes a New Encryptor for Linux (trendmicro.com)
Monti Ransomware New Linux Variant Attacking Industries (gbhackers.com)
Cyber Swachhta Kendra: Monti Ransomware (csk.gov.in)
Monti ransomware targets legal and gov’t entities with new Linux-based variant (therecord.media)
Monti Returns From 2-Month Break with Revamped Ransomware Variant - Security Boulevard
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.