- WHY AVERTIUM?
-
-
Why Avertium?
Context over chaos. Disconnected technologies, siloed data, and reactive processes can only get you so far. Protecting businesses in today’s threat landscape demands more than a set of security tools – it requires context.
That's where Avertium comes in
-
Considering Microsoft?
Avertium Named Microsoft Security Solutions PartnerAvertium’s managed services for Microsoft Security Solutions is delivered through the company’s premium service: Fusion MXDR. Fusion MXDR includes 24x7 monitoring and management of Defender for Endpoint and Sentinel, threat intelligence, attack surface
monitoring, and vulnerability management for Microsoft Security customers. -
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- SOLUTIONS
-
-
Governance, Risk, + Compliance
GRC with context – not complexity. -
Attack Surface Management
No more blind spots, weak links, or fire drills. -
Threat Detection + Response
Detect, adapt, and attack with context. -
Microsoft Security Solutions
End-to-end support from strategy to daily operations to maximize your Microsoft Security.
-
-
- COMPANY
-
-
About Us
Security. It’s in our DNA. It’s elemental, foundational. Something that an always-on, everything’s-IoT-connected world depends on.
Helping mid-to-enterprise organizations protect assets and manage risk is our only business. Our mission is to make our customers’ world a safer place so that they may thrive in an always-on, connected world.
-
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- PARTNERS
-
-
Our Partners
Best-in-class technology from our partners... backed by service excellence from Avertium.
-
Partner Opportunity Registration
Interested in becoming a partner?
With Avertium's deal registration, partners can efficiently and confidently connect with Avertium on opportunities to protect your deals.
-
Latest Avertium Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- NEWS & RESOURCES
-
-
News & Resources
Dive into our resource hub and explore top
cybersecurity topics along with what we do
and what we can do for you. -
Latest Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- CONTACT
Iranian Cyber Threats - APT42 & HomeLand Justice
Executive Summary
Recently, there has been an uptick in activity from Iranian APTs and threat groups. In February 2022, CISA, the Federal Bureau of Investigation (FBI), the U.S. Cyber Command Cyber National Mission Force’ (CNMF), the United Kingdom’s National Cyber Security Centre (NCSC-UK), and the National Security Agency (NSA) released a joint statement regarding their observation of Iranian government-sponsored APT MuddyWater – an Iranian APT observed targeting the defense, oil and natural gas, local government, and telecommunications industries.
By August 2022, another Iranian APT named APT35 was seen using a data extraction tool called Hyperscrape to steal data from well-known email providers (Yahoo!, Google, etc.). The APT was seen attacking a wide range of targets, using a new strain of malware. Now, researchers have observed more Iranian threat actors and APTs scanning for and exploiting well known vulnerabilities.
CISA and the FBI recently warned that Iranian threat actors have been consistently improving their offensive cyber capabilities and their attacks are intended to cause physical consequences. Let’s take a look at Iranian APT activity, recent attacks, as well as tactics and techniques.

iranian apts - apt42 & homeland justice
Since 2015, APT42 has been responsible for over 30 cyberespionage attacks via credential harvesting. The threat actor has specifically targeted Australia, Europe, the Middle East, and the U.S. APT42 is known for deploying highly targeted spear phishing and surveillance operations in at least 14 countries.
According to the threat intelligence firm, Mandiant, APT42 could be operating on the behalf of the Islamic Revolutionary Guard Corps Intelligence Organization (IRGC-I0). IRGC tends to rely on contractors to execute different cyber operation missions.
Also, the threat actor has targeted corporate and personal email accounts to harvest credentials and infect Android devices with spyware. Parties within the U.S., Europe, Australia, and the Middle East have been targeted by APT42. Mandiant stated that APT42’s operations appear to be focused on organizations and people of interest to the Iranian government for foreign policy, domestic politics, and regime stability purposes.
Additionally, APT42 shares partial overlaps with APT35. Mandiant’s report on APT42 stated that that they can conclude with moderate confidence that the group operates on the behalf of the IRGC but originates from different missions based on their different targeting patterns, tactics, techniques, and procedures. The differences being the following:
- APT 42 – Operations put more focus on organizations and people related to the Iranian government.
- APT35 – Operations put more focus on long-term intensive operations targeting the Middle Eastern and U.S. military, government, media, energy, defense industrial bases, engineering, telecommunications, and business services.
Both APT42 and APT35 have used MAGICDROP (used to decrypt files from its .data section and writes them to the system’s Temp directory) and BROKEYOLK malware (a .NET downloader, which downloads and executes malicious software or malware from the hardcoded address of an adversaries’ C2 server), but the groups don’t share similarities regarding C2 infrastructure or how the groups use the malware.
It is also important to note that both APT42 and APT35 have links to a threat cluster tracked as UNC2448 by Mandiant. Additionally, Microsoft and Secureworks disclosed APT42 as a Phosphorus subgroup deploying ransomware attacks for financial gain via BitLocker.
HomeLand Justice
Between May and June 2022, the Albanian government was attacked by threat actors from Iran. The attack was in response to an upcoming conference in Albania being hosted by the Iranian opposition group Mojahedin-e Khalqs. After the attacks, Albania had to shut down online access to several government services. The threat actors deployed ransomware onto the networks of the Albanian government – leaving an anti-Mujahideen message on all desktops.
Also, it was suspected that the attacks included an unknown backdoor called ChimneySweep and a ransomware tool called RoadSweep. Researchers at Mandiant discovered that on the day after the Albanian attacks, ZeroClear malware was uploaded to a public malware registry. This malware has previously been linked to Iranian hackers. At the time, researchers did not link these attacks to a particular threat group.
However, in June 2022, HomeLand Justice created a website and several social media profiles with anti-MEK messages. By July 2022, HomeLand Justice took responsibility for the cyber attacks on the Albanian government infrastructure. The attack destroyed sensitive government data and disrupted government services to the public. HomeLand Justice even posted videos of the attack on their website. Also, via social media, HomeLand Justice advertised Albanian government information for release in a .zip file or in a video of a screen recording of confidential documents. The advertisements continued into August 2022.
In September 2022, the Albanian government became the victim of, yet another cyber attack launched by Iranian threat actors – using similar tactics, techniques, and malware. These attacks were likely in response to severed diplomatic ties between Albania and Iran, and Albania asking all Iranian diplomats and embassy staff to leave the country after July’s cyber attack. This is the first time a country has severed diplomatic relations because of a cyber conflict.
As a result of the attacks, the U.S. imposed sanctions on Iran’s Ministry of Intelligence and its minister for allegedly engaging in other cyber activities against the U.S. and its allies (Albania).
“Iran’s cyber attack against Albania disregards norms of responsible peacetime State behavior in cyberspace, which includes a norm on refraining from damaging critical infrastructure that provides services to the public,” said Under Secretary of the Treasury for Terrorism and Financial Intelligence Brian E. Nelson. “We will not tolerate Iran’s increasingly aggressive cyber activities targeting the United States or our allies and partners.” - Brian E. Nelson – Under Secretary of the Treasury for Terrorism and Financial Intelligence (Treasury.gov)
apt42 tactics & techniques
Their main goal is to harvest credentials from email accounts, track Iranian government dissidents, and steal documents and research related to Iran. APT42’s activity primarily focuses on the Middle East; however, they have targeted journalists, government officials that oppose the IRGC, and Western think tanks.
Targeting high-priority victims inside and outside of Iran, APT42 is a threat to foreign policy officials. The group’s surveillance activity includes the surveillance of Iranian dual-nationals, dissidents inside Iran and those who fled Iran for their safety, as well as prior government officials. APT42’s credential harvesting campaigns include detailed social engineering, with one case lasting 37 days. The threat actor masqueraded as a well-known journalist from a large U.S. media company and requested an interview from their target. The APT engaged the target for 37 days before directing them to a phishing landing page.
In addition to sophisticated social engineering tactics, APT42 collects multi-factor authentication (MFA) codes to bypass authentication. In May 2017, the group targeted an Iranian opposition group that operated out of Europe and North America. They sent the group’s senior leadership spear-phishing emails that mimicked legitimate Google correspondence. The correspondence contained links to fake Google Books pages, which directed the victims to sign-in pages. The sign-in pages attempted to steal the victim’s credentials and MFA authentication codes.
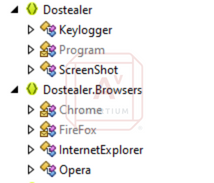
Another way APT42 exploits their targets is by information theft, such as keylogging and cookie stealing. Avertium’s Cyber Threat Intelligence Team (CTI) was able to analyze two malware samples, Dostealer (aka winrarcontainer) and SilentUploader (a DLL). Dostealer is primarily used for credential theft in information stealing. Reverse engineering of the executable reveals several of the built-in functions of the malware, including:
- Keylogger
- Screen Shots
- Cookie stealing (for several popular browsers)
Image 1: DoStealer
According to the CTI team, the cooker stealer functions rely on a splite DLL, which is dropped by the executable to ensure functionality. Below, you will find the malware checking to see if the sqlite3.dll file exists and writing if it does not.
Image 2: Checking for splite3.dll
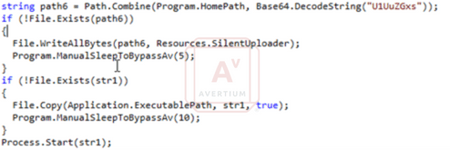
Below, you’ll find another code block that checks for and writes silentuploader, then sleeps to bypass antivirus detection before executing.
Image 3: Bypassing Antivirus Detection
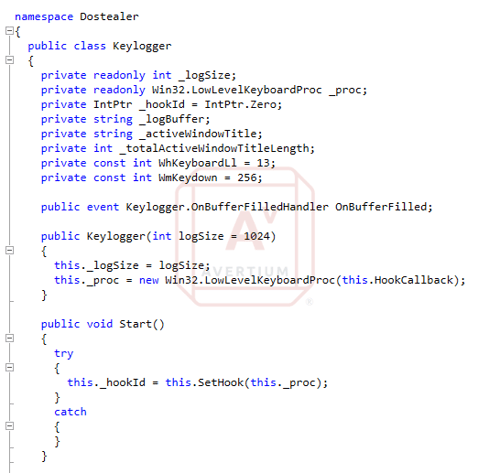
APT42 also has custom backdoors and tools which include publicly available code copied directly from GitHub project. This likely means that the group may have limited in-house resources for developing malware. Some of the malware families utilized include the custom reconnaissance tool PowerPost and the PowerShell backdoor TameCat, as well as the VBA-based dropper TabbyCat. APT42 delivers the malware through malicious documents attached to spear-phishing emails. The Android malware used by APT42 is designed to monitor communications of victims and track their locations.
Image 4: Code for Keylogger Function
what this means for the u.s.
In the past, holding threat actors responsible and accountable for cyber attacks was difficult due to varying laws in different countries. In previous years, threat actors freely wreaked havoc on critical infrastructure in various countries, including the U.S. In December 2020, we saw the attack on SolarWinds – a widely used IT management software application leveraged by the U.S. government and by the security industry. Next, we witnessed DarkSide’s cyber attack on Colonial Pipeline, followed by REvil’s attack on Kaseya.
As a result of these devastating attacks, President Biden stated that one of his goals for 2021 was to strengthen the nation’s cyber security and bring other countries together to combat cybercrime and improve law enforcement cooperation. An Executive Order was administered to tackle cybersecurity challenges facing the U.S. Therefore, it is not shocking that the U.S. has decided to sanction Iran for attacking an ally (Albania).
The sanctions that the U.S. has imposed upon Iran include freezing the assets of the targeted individuals and entities in the U.S., thus making it illegal for American citizens to do business with Iran. Nevertheless, Iran has rejected the sanctions and believes that they are politically motivated.
“Like previous illegal US sanctions against the Ministry of Intelligence, this new label will never be able to create the slightest hinder in the determination of the Iranian people’s security servicemen in this proud institution,” – Nasser Kanaani (Iran’s Foreign Ministry spokesperson)
After Albania was attacked in July 2022, the U.S. government spent time working alongside private sector partners to help Albania mitigate and recover from the attack. Lately, the U.S. government has become quicker in responding to cyber attacks and attributing state-backed attacks.
In May 2022, the U.S. government was able to attribute a cyber attack on the satellite communications provider, Viasat, to the Russian government. In the summer of 2021, they were able to attribute Microsoft Exchange server attacks to Beijing in just three months. In 2017, it took the U.S. government a lengthy eight months to pin the malware to a specific threat actor.
“Iran’s conduct disregards norms of responsible peacetime State behavior in cyberspace, which includes a norm on refraining from damaging critical infrastructure that provides services to the public. Albania views impacted government networks as critical infrastructure. Malicious cyber activity by a State that intentionally damages critical infrastructure or otherwise impairs its use and operation to provide services to the public can have cascading domestic, regional, and global effects; pose an elevated risk of harm to the population; and may lead to escalation and conflict.” – The White House
The U.S. government plans to continue to hold malicious threat actors accountable and invites their partners and allies to join them in building a secure and resilient digital future. For every action, there is a reaction and cyber security professionals can only hope that Iranian state-backed actors won’t retaliate due to the new sanctions.
How Avertium is Protecting Our CUSTOMERS
Threat actors like APT42 and HomeLand Justice can gain unlimited access to networks and systems, furthering reconnaissance. Avertium is here to keep your organization safe and to mitigate any attacks caused by bad actors:
- To identify the source of your breach and the scope that it reached; you’ll want to include Avertium’s DFIR (Digital Forensics and Incident Response) services in your protection plan. We offer DFIR to mitigate damage from a successful breach. This service is provided as an on-demand crisis response service, as well as a retainer-based program.
- Implement XDR as a prevention method. Our XDR is a combination of monitoring software like LogRhythm, Microsoft Azure Sentinel, or AlienVault, combined with endpoint protection such as SentinelOne. XDR platforms enable cybersecurity through a technology focus by collecting, correlating, and analyzing event data from any source on the network. This includes endpoints, applications, network devices, and user interactions.
- MDR provides an in-depth investigation into potential threats to an organization’s network. Avertium’s risk-based approach to managed security delivers the right combination of technology, field-validated threat intelligence, and resource empowerment to reduce complexity, streamline operations, and enhance cybersecurity resilience. If you need a more advanced security solution, MDR is the next step. MDR is an outsourced security control solution that includes the elements of EDR, enhanced with a range of fundamental security processes.
- Avertium offers VMaaS to provide a deeper understanding and control over organizational information security risks. If your enterprise is facing challenges with the scope, resources, or skills required to implement a vulnerability management program with your team, outsourced solutions can help you bridge the gap.
- Avertium offers user awareness training through KnowBe4. The service also Incident Response Table-Top exercises (IR TTX) and Core Security Document development, as well as a comprehensive new-school approach that integrates baseline testing using mock attacks.
avertium's recommendations
General Recommendations
- Tabletop Exercises: Have a good cyber incident response plan in place that has been tested with tabletop exercises.
- Security Review: Be sure to review the plan and improve it every time it’s tested on real cyber threats.
- Risk Analysis: Prevent an attack by ensuring your organization has a detailed defense strategy based on a risk analysis approach.
- Cybersecurity Education: Educate your employees on cyber security preparedness and the dangers of opening potentially malicious documents. Annual or quarterly training modules can help prevent threat actors from tricking employees into opening malicious email attachments.
Avertium & CISA Recommend the following when dealing with threat actors like HomeLand Justice:
- Ensure anti-virus and anti-malware software is enabled and signature definitions are updated regularly and in a timely manner. Well-maintained anti-virus software may prevent use of commonly deployed cyber attacker tools that are delivered via spear-phishing.
- Adopt threat reputation services at the network device, operating system, application, and email service levels. Reputation services can be used to detect or prevent low-reputation email addresses, files, URLs, and IP addresses used in spear-phishing attacks.
- If your organization is employing certain types of software and appliances vulnerable to known Common Vulnerabilities and Exposures (CVEs), ensure those vulnerabilities are patched. Prioritize patching known exploited vulnerabilities.
- Monitor for unusually large amounts of data (i.e. several GB) being transferred from a Microsoft Exchange server.
- Check the host-based indications, including webshells, for positive hits within your environment.
- Maintain and test an incident response plan.
- Ensure your organization has a vulnerability management program in place and that it prioritizes patch management and vulnerability scanning of known exploited vulnerabilities. Note: CISA’s Cyber Hygiene Services (CyHy) are free to all state, local, tribal, and territorial (SLTT) organizations, as well as public and private sector critical infrastructure organizations.
- Properly configure and secure internet-facing network devices.
- Do not expose management interfaces to the internet.
- Disable unused or unnecessary network ports and protocols.
- Disable/remove unused network services and devices.
- Adopt zero-trust principles and architecture, including:
- Micro-segmenting networks and functions to limit or block lateral movements.
- Enforcing phishing-resistant multifactor authentication (MFA) for all users and VPN connections.
- Restricting access to trusted devices and users on the networks.
MITRE Map
APT42
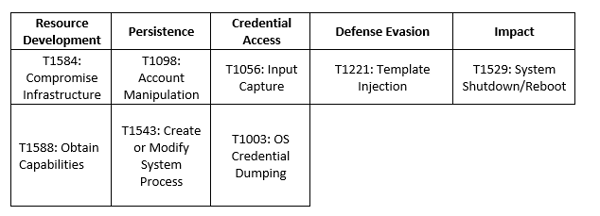
HomeLand Justice
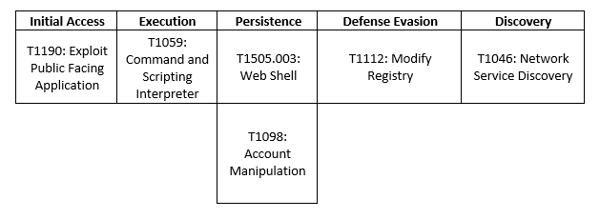
Indicators of Compromise (IoCs)
HomeLand Justice
File Hashes
- f116acc6508843f59e59fb5a8d643370dce82f492a217764521f46a856cc4cb5
- e1204ebbd8f15dbf5f2e41dddc5337e3182fc4daf75b05acc948b8b965480ca0
- bad65769c0b416bb16a82b5be11f1d4788239f8b2ba77ae57948b53a69e230a6
- bb45d8ffe245c361c04cca44d0df6e6bd7596cabd70070ffe0d9f519e3b620ea
- e67c7dbd51ba94ac4549cc9bcaabb97276e55aa20be9fae909f947b5b7691e6b
- ac4809764857a44b269b549f82d8d04c1294c420baa6b53e2f6b6cb4a3f7e9bd
- d1bec48c2a6a014d3708d210d48b68c545ac086f103016a20e862ac4a189279e
- d145058398705d8e20468332162964dce5d9e2ad419f03b61adf64c7e6d26de5
- 1c926d4bf1a99b59391649f56abf9cd59548f5fcf6a0d923188e7e3cab1c95d0
- fb49dce92f9a028a1da3045f705a574f3c1997fe947e2c69699b17f07e5a552b
- 45bf0057b3121c6e444b316afafdd802d16083282d1cbfde3cdbf2a9d0915ace
- dfd631e4d1f94f7573861cf438f5a33fe8633238d8d51759d88658e4fbac160a
- 734b4c06a283982c6c3d2952df53e0b21e55f3805e55a6ace8379119d7ec1b1d
- f8db380cc495e98c38a9fb505acba6574cbb18cfe5d7a2bb6807ad1633bf2df8
- 0b647d07bba697644e8a00cdcc8668bb83da656f3dee10c852eb11effe414a7e
- 7AD64B64E0A4E510BE42BA631868BBDA8779139DC0DAAD9395AB048306CC83C5
- CAD2BC224108142B5AA19D787C19DF236B0D12C779273D05F9B0298A63DC1FE5
- f116acc6508843f59e59fb5a8d643370dce82f492a217764521f46a856cc4cb5
- 63dd02c371e84323c4fd9a161a75e0f525423219e8a6ec1b95dd9eda182af2c9
- 7ad64b64e0a4e510be42ba631868bbda8779139dc0daad9395ab048306cc83c5
- 3c9dc8ada56adf9cebfc501a2d3946680dcb0534a137e2e27a7fcb5994cd9de6
- 45bf0057b3121c6e444b316afafdd802d16083282d1cbfde3cdbf2a9d0915ace
IP Addresses
- 144[.]76[.]6[.]34
- 148[.]251[.]232[.]252
- 148[.]251[.]233[.]231
- 176[.]9[.]18[.]143
- 185[.]82[.]72[.]111
- 216[.]24[.]219[.]65
- 216[.]24[.]219[.]64
- 46[.]30[.]189[.]66
APT42
File Hashes
- 00b5d45433391146ce98cd70a91bef08
- 04a6997f0a8021b773ebb49977bc625f
- 0a3f454f94ef0f723ac6a4ad3f5bdf01
- 335849d8fb13a4a189ba92af9bdf5d1d
- 34d37f64613f3fe00086ac8d5972db89
- 3c6302fb6bdb953e2073a54b928fad9c
- 3d67ce57aab4f7f917cf87c724ed7dab
- 60e6523d29e8a9b83f4503f2e7fd7e1d
- 63cd07e805bcd4135a8e3a29fa3ceebd
- 651d72776c0394693c25b1e3c9ec55d0
- 88df70a0e21fb48e0f881fb91a2eaade
- 8a847b0f466b3174741aac734989aa73
- 8e0eb3ceb1bbe736beaf64353dda1908
- 96444ed552ea5588dffca6a5a05298e9
- 9a1e09b7ce904eefb83dc8d7571826f9
- 9bd1caf6b79f6a69981a15d649a04c19
- 9d0e761f3803889dc83c180901dc7b22
- 9dd30569aaf57d6115e1d181b78df6b5
- a04c2c3388da643ef67504ef8c6907fb
- ae797446710e375f0fc9a33432d64256
- afb5760c05db35a34c5dc41108ba72c2
- b7bc6a853f160df2cc64371467ed866d
- bdf188b3d0939ec837987b4936b19570
- d30abec551b0fb512dc2c327eeca3c43
- da7d37bfb899a0094995944d4c5e2f21
- df02a8a7cb2afb80cc2b789d96f02715
- f3d25b1cedf39beee751eb9b2d8d2376
- 03d7ffd758e98c9a2c8c4716c93f09687000e22e
- 03eadb4ab93a1a0232cb40b7d2ef179a1cd0174d
- 08270b049ae33f0bcd1d207ed77f999d51a09d94
- 08d2aea84d6c148ff2ad4653856fb080eb99abf2
- 1504da49f6fe8638c7e39d4bcb547fbb15376462
- 186f07279ac0f15cc7be5caf68addabb2091bc84
- 2374f5a9278b209563e8193847a76c25c12eec8f
- 280b64c0156f101eaad3f31dbe91f0c1137627dc
- 29175a0015909186f69f827630ef3fe2c1c5302c
- 3b9a2e34f5d603b55cf7fd223d4e5c784b805242
- 448e6d519a340845a55b4b1809488427c0d79cdd
- 470b850363677d3d54629a92ac8b5143f4584a09
- 6303907ec7d1d591efffe876720a0ab051bfd429
- 66d36d0b170cf1a0001cca16357961a2f28cba60
- 75b7db0597f234838e7c8431b57870411842775d
- 7649c554e87f6ea21ba86bb26ea39521d5d18151
- 8f2bc0d6adfb4cad43fdda9f3d732c859eb79e35
- 9624d9613fe8cdc6833888b9e68892565e3a5d11
- aba938bf8dc5445df3d5b77a42db4d6643db4383
- b66ae149bbdfc7ec6875f59ec9f4a5ae1756f8ba
- c760adecea4dbb4dd262cb3f3848f993d5007b2e
- d08982960d71a101b87b1896fd841433b66c7262
- dbb64b0202bb4da6796279b5fa88262a6e31787e
- e3712e3d818e63060e30aec2a6db3598cbf0db92
- e45aeccb798f5cf6cb5d877821d1f4aa7f55cf6f
- e8f50ecea1a986b4f8b00836f7f00968a6ecba4f
- ecf9b7283fda023fa37ad7fdb15be4eadded4e06
- 003676e6240421426e5c0919eb40bdde52b383eb1c54596deb77218c3885cdc5
- 110c77f66a8d4d8ccc9dc468744302cf368efd071e3e4af39338b699f6bc7808
- 21c5661eb5e54d537c6c9394d7bd4accf53e06851978a36c94b649c4f404a42e
- 28de2ccff30a4f198670b66b6f9a0ce5f5f9b7f889c2f5e6a4e365dea1c89d53
- 2c33b1dd793ad5e59180719d078301ee7ebb6cf7465286c19b042accca6ac749
- 2c92da2721466bfbdaff7fedd9f3e8334b688a88ee54d7cab491e1a9df41258f
- 3cad59c65ee1e261658c2489dc45a7c6875d8ccb917d291d282e48bca1b74752
- 4bcc2ad5b577954a6bd23aff16566ce0784a71f9526a5ae849347ae766f4033f
- 5d3ff202f20af915863eee45916412a271bae1ea3a0e20988309c16723ce4da5
- 5ee98a677f58b897df3287448e63a1a781d312d2a951f438e1d7e4ab658fa4a0
- 6618051ea0c45d667c9d9594d676bc1f4adadd8cb30e0138489fee05ce91a9cb
- 734d9639fcfffef1a3c360269ccc1cda4f1d0e9dc857fa438f945e807b022c21
- 7a650d3b1e511a05d0441484c7c7df59a63003ce77cd4eb7081323fd79d2b9a3
- 7eb564f0afc23cc8186e67f8c0d7e6c80215b75c9f0c4b35f558a9e35743ca41
- 90e5fa3f382c5b15a85484c17c15338a6c8dbc2b0ca4fb73c521892bd853f226
- 9410963ede9702e7b74b4057fee952250ded09f85a4bb477d45a64f2352ec811
- 971c5b5396ee37827635badea90d26d395b08d17cbe9e8027dc87b120f8bc0a2
- 9f2bc9aebb3ee87cfbdef1716b5f67834db305cf400b41b278d5458800c5eeeb
- a37a290863fe29b9812e819e4c5b047c44e7a7d7c40e33da6f5662e1957862ab
Supporting Documentation
PowerPoint Presentation (hivepro.com)
U.S. imposes sanctions on Iran over cyber activities, cyberattack on Albania | Reuters
Microsoft investigates Iranian attacks against the Albanian government - Microsoft Security Blog
Iranian APT Targets Email Credentials in Espionage Attacks | Decipher (duo.com)
APT42 supported by Iranian terrorist group, report finds | SC Media (scmagazine.com)
Hackers deploy new ransomware tool in attacks on Albanian government websites - CyberScoop
CISA Alert AA22-264A - Iranian HomeLand Justice APT Group's TTPs (picussecurity.com)
Iran Cyber Threat Overview and Advisories | CISA
Albania says Iranian hackers hit the country with another cyberattack - CyberScoop
Emerging Cyber Threats of September 2022 (picussecurity.com)
APT42 IOCs - AlienVault - Open Threat Exchange
Iranian APT Targets Email Credentials in Espionage Attacks | Decipher (duo.com)
Iranian State Actors Conduct Cyber Operations Against the Government of Albania | CISA
USA imposes sanctions on Iran over Albania cyber attack | E&T Magazine (theiet.org)
Why Albania’s cyberattacks matter to the U.S. (axios.com)
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.