- WHY AVERTIUM?
-
-
Why Avertium?
Context over chaos. Disconnected technologies, siloed data, and reactive processes can only get you so far. Protecting businesses in today’s threat landscape demands more than a set of security tools – it requires context.
That's where Avertium comes in
-
Considering Microsoft?
Avertium Named Microsoft Security Solutions PartnerAvertium’s managed services for Microsoft Security Solutions is delivered through the company’s premium service: Fusion MXDR. Fusion MXDR includes 24x7 monitoring and management of Defender for Endpoint and Sentinel, threat intelligence, attack surface
monitoring, and vulnerability management for Microsoft Security customers. -
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- SOLUTIONS
-
-
Governance, Risk, + Compliance
GRC with context – not complexity. -
Attack Surface Management
No more blind spots, weak links, or fire drills. -
Threat Detection + Response
Detect, adapt, and attack with context. -
Microsoft Security Solutions
End-to-end support from strategy to daily operations to maximize your Microsoft Security.
-
-
- COMPANY
-
-
About Us
Security. It’s in our DNA. It’s elemental, foundational. Something that an always-on, everything’s-IoT-connected world depends on.
Helping mid-to-enterprise organizations protect assets and manage risk is our only business. Our mission is to make our customers’ world a safer place so that they may thrive in an always-on, connected world.
-
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- PARTNERS
-
-
Our Partners
Best-in-class technology from our partners... backed by service excellence from Avertium.
-
Partner Opportunity Registration
Interested in becoming a partner?
With Avertium's deal registration, partners can efficiently and confidently connect with Avertium on opportunities to protect your deals.
-
Latest Avertium Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- NEWS & RESOURCES
-
-
News & Resources
Dive into our resource hub and explore top
cybersecurity topics along with what we do
and what we can do for you. -
Latest Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- CONTACT
An In-Depth Look at Iranian APT "MuddyWater"
Executive Summary
In February 2022, CISA, the Federal Bureau of Investigation (FBI), the U.S. Cyber Command Cyber National Mission Force (CNMF), the United Kingdom’s National Cyber Security Centre (NCSC-UK), and the National Security Agency (NSA) released a joint statement regarding their observation of Iranian government-sponsored APT MuddyWater and their malicious cyber activity. MuddyWater is known for cyber espionage, as well as other cybercriminal operations as part of Iran’s Ministry of Intelligence and Security.
The threat actors have targeted several government and private sector organizations in the defense, oil and natural gas, local government, and telecommunications industries – focusing on Asia, Africa, Europe, and North America.
MuddyWater conducts broad cyber campaigns, exploiting publicly reported vulnerabilities and using open-source tools and strategies to gain access to their target’s systems. Let’s take a look at MuddyWater, their tactics, and their techniques, as well as the current state of cyber espionage.
IRANIAN APT "muddywater"
Also, known as MERCURY, Earth Vetala, Static Kitten, Seedworm, and TEMP.Zagros, MuddyWater is an Iranian APT and a subservient element within the Iranian Ministry of Intelligence and Security (MOIS). The group has been active since 2018 and has provided stolen data and access to the Iranian government by exploiting known vulnerabilities and using open-source tools to deploy their ransomware.
In November 2021, Cisco Talos observed a campaign targeting Turkey government entities, including the Scientific and Technological Research Council of Turkey – Tubitak. MuddyWater has three goals when conducting their attacks: cyber espionage, intellectual property theft, and ransomware attacks.
- Cyber Espionage – this happens when a threat actor attacks an organization for political reasons. In MuddyWater’s case, they support the political dominance of the nation-state in the Middle East, and they are partly motivated by nation-state interests.
- Intellectual Property Theft – this is when threat actors rob companies or certain individuals of their inventions, patents, trade secrets, etc. MuddyWater accomplishes this by carrying out aggressive campaigns against government-affiliated institutions such as research companies and universities.
- Ransomware Attacks – typically, ransomware attacks happen when a threat actor is seeking a ransom in exchange for a decryption key or stolen data. In MuddyWater’s case, they have attempted to deploy ransomware such as Thanos on networks to do two things: Destroy evidence they were in a network or system, and 2. Disrupt operations of private organizations.
muddywater'S Tactics & Techniques – Turkish government
MuddyWater uses several malware variants such as PowGoop, Canopy, Small Sieve, POWERSTATS, and Mori. MuddyWater also uses malicious documents to deploy Remote Access Trojans (RATs) on vulnerable systems. According to Cisco Talos, MuddyWater plants a malicious macro in their documents that, once triggered, drops two WSF files on the endpoint. Additionally, MuddyWater uses DNS to contact the command and control (C2), while original contact with hosting servers is done via HTTP. PowerShell and Visual Basic scripting are used for their initial payload, in addition to LoLBins to assist in the initial stages of infection.
As we previously stated, MuddyWater was seen targeting Turkish government entities in November 2021. Cisco Talos observed that the campaign included malicious Excel documents (also known as XLS maldocs) and executables stored on a file hosting domain named “snapfile[.]org” that’s delivered to victims via PDF documents with embedded links.
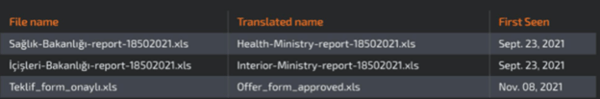
MuddyWater hosts the maldocs on attacker-controlled or public media-sharing websites which are downloaded by malicious PDFs. The PDFs are distributed via email and are designed to trick targets into downloading and opening them. Research shows that MuddyWater uses malicious PDFs as their entry point for their attacks. Additionally, a set of malicious Excel spreadsheet files were seen distributed with Turkish names, some masquerading as legitimate documents from the Turkish Health and Interior Ministries.
Image 1: Files with Turkish Names
Source: Cisco Talos
MuddyWater’s maldocs include malicious VBA macros that are instrumental in the infection chain. This infection chain has three key artifacts on the infected endpoint. According to Cisco Talos, they include:
- Registry is key for persistence.
- Malicious PowerShell-based downloader script – this is meant to download and execute the next payload on the infected endpoint.
- Malicious VB script (an intermediate component that is set up for persistence by creating a malicious Registry Run for the infected user).
muddywater's infection chain
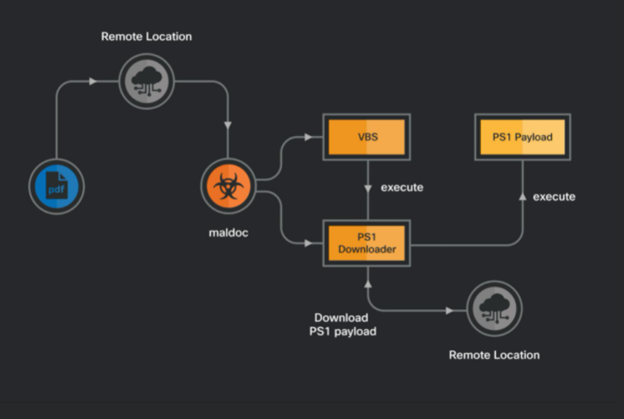
As stated above, the delivery method for MuddyWater’s malware is done by distributing malicious PDFs with embedded links. The first stage includes the target trying to open the PDF file, which then displays an error message that asks the target to click on a link to resolve the issue. After clicking the download button, the endpoint receives a second stage which is a Windows executable or a malicious XLS file.
Image 2: Infection Chain
Source: Cisco Talos
Sometimes, MuddyWater uses decoy documents in the executable-based threat vector with content that’s similar to the original PDF files disseminating the maldocs and executables. Malicious PowerShell scripts are downloaded and executed once the victim opens the document. In this infection chain, intermediate VBS scripts are replaced with a PowerShell implementation, which creates a directory in the victim’s home folder. There are two PowerShell scripts stored in the directory:
- Instrumentor script - activates next the next stage from a disk called .CloudCache.conf.
- Downloader script – downloads the next stage from a remote location on an endpoint called .CloudDrive.conf.
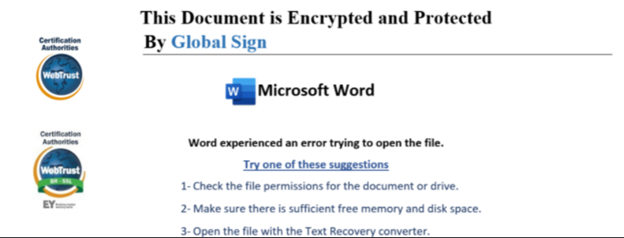
In August 2021, MuddyWater deployed another version of the executable and targeted Pakistani entities. This version also included a decoy document followed by the use of a PowerShell-based downloader script. The Registry run key is used for persistence. It’s unclear if the Turkish attacks in November 2021 were a continuation of Pakistani-related activity.
Image 3: Malicious Document Sent to Pakistan Victims
Source: Cisco Talos
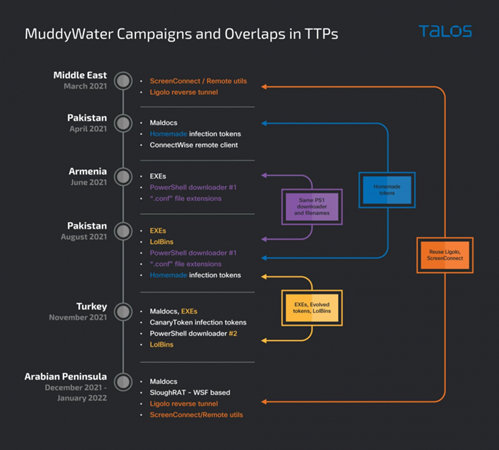
In April 2021, MuddyWater was observed deploying a RAT and the EXE-based infection vector from the Pakistan attack. They were also seen targeting Armenia in June 2021 using the same types of Windows executable files. All of the above campaigns used an implementation of signaling tokens.
Image 4: MuddyWater Campaigns Observed by Talos
Source: Cisco Talos
is the Iranian APT "muddywater" a single actor?
Because MuddyWater has used a variety of lures and has targeted different geographic regions, cyber analysts are saying that MuddyWater is more than likely a conglomerate of subgroups and not a single threat actor. The sub-groups that Cisco Talos observed appear to operate independently and are motivated by espionage, intellectual theft, and destructive or disruptive operations based on their victims.
The Turkish, Pakistan, and other campaigns researchers observed, involve the same TTPs - which is evidenced by the gradual adoption of various techniques over time within the campaigns. Cisco Talos believes there are links between the various campaigns, including MuddyWater’s migration of “techniques from region to region, along with their evolution into more advanced versions.”
the state of cyber espionage & nation-state threat actors
Most nation-state threat actors’ goal is cyber espionage, which makes them a serious threat to the U.S. and other countries. We previously mentioned that cyber espionage is primarily politically motivated and today’s threat landscape is seeing this kind of cyber attack more frequently.
Although it can be difficult for law enforcement to crack down on nation-state threat actors, there has been some success in finding and arresting some groups. In March 2022, Avertium published a report featuring the nation-state threat actor APT40 and their espionage attacks on the maritime, robotics, and biomedical industries. The threat actor has focused their attacks on the U.S., Canada, Europe, the Middle East, and the South China Sea.
In July 2019, four members of the group were charged with attacking governments, universities, and various companies across the globe on behalf of the Chinese government. The four suspects were a part of a much larger operation that set up a company (Hainan Xiandun) as a front for their attack campaigns. According to the Intrusion Truth blog, Hainan Xiandun was under the direction of the Chinese Ministry of State Security (MSS), and an employee, Wu Shurong, worked as a hired hacker for the company. Shurong created malware and used it to compromise computer systems belonging to universities, governments, and companies.
The other three suspects were MSS officers who worked for the Hainan provincial department, their names are Ding Xiaoyang, Cheng Qingmin, and Zhu Yunmin. The U.S. alleged that the MSS has directed Bronze Mohawk’s attack campaigns since 2011 – directing them to steal confidential business information for dissemination in China. Bronze Mohawk’s attacks were conducted for the sole purpose of leaking sensitive information.
In 2021, President Biden stated that one of his goals was to strengthen the nation’s cyber security and bring other countries together to combat cybercrime and improve law enforcement cooperation. President Biden also acknowledged that securing supply chains and maintaining strong cyber security best practices should be continued work. This statement came after the attack on Kaseya – a supply chain ransomware attack conducted by REvil. Although the Kaseya attack was a ransomware supply-chain attack, supply chain attacks and nation-state threat actors are often linked.
In March 2022, the FBI stopped the Russian-state Cyclops Blink botnet from attacking the U.S. Cyclops Blink is a modular malware that infects internet-connected devices via firmware updates – targeting WatchGuard and ASUS devices. Cyclops Blink is controlled by the Russian Federation’s Main Intelligence Directorate and has compromised thousands of devices worldwide to date.
At the end of 2021, Security Week published an article stating that cyber espionage will remain a primary motive for nation-state adversaries in 2022.
“Hostile state activity will continue to focus primarily on espionage rather than on disruption and destruction. Several states, notably China, Russia, and Iran, will continue to conduct operations aimed at harvesting bulk data to support subsequent cyber operations and traditional espionage activities.” – Security Week
How Avertium is Protecting Our CUSTOMERS
Threat actors like MuddyWater can gain unlimited access to networks and systems, furthering reconnaissance. Avertium is here to keep your organization safe and to mitigate any attacks caused by APTs like MuddyWater:
-
To identify the source of your breach and the scope that it reached; you’ll want to include Avertium’s DFIR (Digital Forensics and Incident Response) services in your protection plan. We offer DFIR to mitigate damage from a successful breach. This service is provided as an on-demand crisis response service, as well as a retainer-based program.
-
Implement XDR as a prevention method. Our XDR is a combination of monitoring software like LogRhythm, Microsoft Azure Sentinel, or AlienVault, combined with endpoint protection such as SentinelOne. XDR platforms enable cybersecurity through a technology focus by collecting, correlating, and analyzing event data from any source on the network. This includes endpoints, applications, network devices, and user interactions.
-
MDR provides an in-depth investigation into potential threats to an organization’s network. Avertium’s risk-based approach to managed security delivers the right combination of technology, field-validated threat intelligence, and resource empowerment to reduce complexity, streamline operations, and enhance cybersecurity resilience. If you need a more advanced security solution, MDR is the next step. MDR is an outsourced security control solution that includes the elements of EDR, enhanced with a range of fundamental security processes.
-
Avertium offers Vulnerability Management to provide a deeper understanding and control over organizational information security risks. If your enterprise is facing challenges with the scope, resources, or skills required to implement a vulnerability management program with your team, outsourced solutions can help you bridge the gap.
-
Avertium offers user awareness training through KnowBe4. The service also Incident Response Table-Top exercises (IR TTX) and Core Security Document development, as well as a comprehensive new-school approach that integrates baseline testing using mock attacks.
Avertium’s Recommendations to PROTECT AGAINST Iranian apt "muddywater"
-
Tabletop Exercises: Have a good cyber incident response plan in place that has been tested with tabletop exercises.
-
Security Review: Be sure to review the plan and improve it every time it’s tested on real cyber threats.
-
Risk Analysis: Prevent an attack by ensuring your organization has a detailed defense strategy based on a risk analysis approach.
-
Cybersecurity Education: Educate your employees on cyber security preparedness and the dangers of opening potentially malicious documents. Annual or quarterly training modules can help prevent threat actors from tricking employees into opening malicious email attachments.
MITRE ATT&CK Threat Mapping
[T1548.002] Abuse Elevation Control Mechanism: Bypass User Account Control
- MuddyWater bypasses UAC (User Account Control) by using various techniques. They do this to elevate process privileges on a system. The UAC allows a program to elevate privileges, giving MuddyWater the ability to perform a task under administrator-level permissions.
[T1560.001] Archive Collected Data: Archive via Utility
- MuddyWater uses the native Windows cabinet creation tool, makecab.exe, to compress stolen data. The threat actor compresses the data before exfiltration via third-party utilities.
[T1509.001] Command and Scripting Interpreter: PowerShell
- MuddyWater uses PowerShell commands and scripts for execution. PowerShell is an interactive command-line interface scripting environment found in Windows operating systems.
[T1509.003] Command and Scripting Interpreter: Windows Command Shell
- MuddyWater abuses the Windows Command Shell for execution and is the primary command prompt on Windows systems. This can be used to control a system and can be invoked remotely via Remote Services. The threat actor also has a custom tool for creating reverse shells.
[T1555] Credentials from Password Stores
- MuddyWater uses LaZagne (an open-source tool uses to cover passwords on a system) and other tools for credential dumping. The threat actor dumps passwords that were saved in their victim’s email.
[T1041] Exfiltration Over C2 Channel
- MuddyWater receives exfiltrated data through C2 infrastructure. This means that data is stolen by exfiltrating it over an existing command and control channel.
[T1589.002] Gather Victim Identity Information: Email Addresses
- MuddyWater gathers their victim’s identity information with spear-phishing emails. They have successfully targeted government employees with this method. MuddyWater uses the malicious PDFs as their entry point to their attacks. The PDFs are emailed to their victims.
Indicators of Compromise (IoCs)
Canary Tokens
- oy80la8r9iyub22nbhb7wvxrk
- kbu1xo0s8ktfxrzsn9iuei3e9
- azp6ai8pg5aq0c619ur0qzi6h
- o1txrtd8gn7i9rt159k5baoys
- smnszrsk7gqjplt0j1idwjrcr
- agsbmym5re3whgnd5a8kzntai
- 60ld4guht70xby71u3io4w43n
- lmbvetj0iif8dwjgutckpppq3
- kc7snpabrp9z0wp1p1klqgkr9
- 04p62zz698bdzv2fdbgupdm4j
- mpei7e608jb22i90z9x8g0gdu
- qut1gl1r6ywzgs1ts922sxtqv
- 09xzzwe761avzxxmyzi85r7hv
- nx4fiakqe1gc02hrnlv8fyis4
- b90963gx06jykhz61kv534zcm
- bruhtg2dtbzk7j1fsttxga85e
- d3g23n4gdcrep20q3wzm153xn
- xxe2sm2rddhxfto9gjx25fo9c
- gikx04xwvf3uu4af8ekrvfeoj
File Hashes
- 8d6ed63f2ffa053a683810f5f96c76813cdca2e188f16d549e002b2f63cee001
- 42aa5a474abc9efd3289833eab9e72a560fee48765b94b605fac469739a515c1
- d3ecc4137fc9a6d7418b4780864baf64cf7417d7badf463dff6ea48cd455915b
- 9991b185c9e9732501e0c2bd841e32a4022f0735a0527150bc8e64ac363d409d
- d9de66497ad189d785d7535ab263e92ffad81df20b903c5e1d36859b4ed38b6d
- 5cdc7dd6162a8c791d50f5b2c5136d7ba3bf417104e6096bd4a2b76ea499a2f4
- 26ed7e89b3c5058836252e0a8ed9ec6b58f5f82a2e543bc6a97b3fd17ae3e4ec
- a8701fd6a5eb45e044f8bf150793f4189473dde46e0af8314652f6bf670c0a34
- b726f4dd745891070f2e516d5d4e4f2f1ce0bf3ff685dc3800455383f342e54d
- c9931382f844b61a002f83db1ae475953bbab449529be737df1eee8b3065f6eb
- fcdd38ff378605c66333429d9df2242fbce25a5f69f4d6d4c11d9613bcb409b0
- c13cb1c9277324534075f807a3fcd24d0d3c024197c7437bf65db78f6a987f7a
- 450302fb71d8e0e30c80f19cfe7fb7801b223754698cac0997eb3a3c8e440a48
- b1e30cce6df16d83b82b751edca57aa17795d8d0cdd960ecee7d90832b0ee76c
- 921b4520b75fcd0071944a483d738223b222ba101e70f2950fbfbc22afbdb5d0
- d7de68febbbdb72ff820f6554afb464b5c204c434faa6ffe9b4daf6b691d535f
- 8b9be9e4d18c5fc71cd12dbfd60ea41eb88a07497e96faa2ba20fdc929b32c0b
- 7dc49601fa6485c3a2cb1d519794bee004fb7fc0f3b37394a1aef6fceefec0c8
- a69fee382cf86f9e457e0688932cbd00671d0d5218f8043f1ee385278ee19c8c
- 63e404011aeabb964ce63f467be29d678d0576bddb72124d491ab5565e1044cf
- 6910ddb58aee9a77e7bb9cadef9e6280a9b5b495edf0b6538cf8bdc1db8b1f4c
- d851badfcf3b3a8b4210bdb33948d0d1d918ec6bf0f1f85cbae6bb8feec7cd74
- aa72f1543d4a4e6ecbfc2da0167f5601c5c692bed73243cf01f616bc4af68afe
- 8f255a1f2e17828a5b9205d6991e2c85c3320311da28048785262396cbc568c7
- cddd5514b7ed3d33ff8eaa16b7b71621ced857755246683e0d28c4650ea744bf
- b4d0161ecab5a7847d325c88ce1a4fc2ca2e11fad0b77638b63ae1781c8b5793
- f6569039513e261ba9c70640e6eb8f59a0c72471889d3c0eaba51bdebb91d285
- 28f2198f811bbd09be31ad51bac49ba0be5e46ebf5c617c49305bb7e274b198c
- 04d6ed9c6d4a37401ad3c586374f169b0aa8d609710bdcf5434d39e0fd4ed9bd
- 69e3a454c191ee38663112cf5358a54cca1229188087ed18e92bc9c59b014912
- dc28b5e878152b5305b8d251019895caa56a7a95a68eccb89a6ecc41da8aadb9
IPs
- 74.131[.]16
- 118.167[.]120
- 118.164[.]165
- 118.164[.]195
- 118.164[.]213
- 202.242[.]84
- 199.133[.]149
- 119.170[.]124
- 118.164[.]165
- 236.212[.]22
- 245.81[.]135
- 141.27[.]211
- hxxp://185.118.167[.]120/
- hxxp://137.74.131[.]16:443/
- hxxp://185.141.27[.]211:443/
- hxxp://149.202.242[.]84:443/
- hxxp://172.245.81[.]135:10196/Geq5P3aFpaSrK3PZtErNgUsVCfqQ9kZ9/ef4f0d9af47d737076923cfccfe01ba7/layer.jpg
- hxxp://172.245.81[.]135:10196/Geq5P3aFpaSrK3PZtErNgUsVCfqQ9kZ9/Pan-op/gallery.jpg
- hxxps://snapfile[.]org/d/c7817a35554e88572b7b
- hxxps://snapfile[.]org/d/0c88a47c3160338bbb68
- hxxp://snapfile[.]org/756a12c43a0fb8d56fbf
- hxxps://snapfile[.]org/5bc3985cf17565a97dbd
- hxxps://snapfile[.]org/55e1c83e920bb7dc949c
- hxxp://canarytokens[.]com/about/d3g23n4gdcrep20q3wzm153xn/index.html
- hxxp://canarytokens[.]com/tags/traffic/images/azp6ai8pg5aq0c619ur0qzi6h/
- hxxp://canarytokens[.]com/tags/traffic/images/azp6ai8pg5aq0c619ur0qzi6h/post.jsp
Supporting Documentation
Cyber Insights 2022: Nation-States | SecurityWeek.Com
Statement by President Joe Biden on Cybersecurity Awareness Month | The White House
Iranian APT: New Methods to Target Turkey, Arabian Peninsula (bankinfosecurity.com)
FBI Disrupts Cyclops Blink Botnet Used by Russian Intelligence Directorate (hackread.com)
Intellectual Property (IP) Theft Definition & Examples | Awake Security
LaZagne, Software S0349 | MITRE ATT&CK®
MuddyWater targets Middle Eastern and Asian countries in phishing attacks | TechRepublic
U.S. says Iranian 'MuddyWater' cyber actors targeting various sectors worldwide | Reuters
Biden Directs ‘Full Resources’ to Respond to Kaseya Ransomware Attack – MeriTalk
"Bronze Mohawk" & Cyber Espionage (avertium.com)
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.
Related Resource: [Threat Report] An In-Depth Look at Pandora Ransomware