An In-Depth Look at AvosLocker Ransomware
Executive Summary
Ransomware attacks have been a global issue within the cyber security industry and many organizations are left wondering if they’ll be the next victim. According to a report from Kroll, the first quarter of 2022 saw an uptick in ransomware attacks leveraging vulnerabilities. Log4j saw the most activity in the final quarter of 2021 with threat actors exploiting the vulnerability via cryptominers. This year, ransomware gangs are using Log4j to set the stage for network encryption, taking advantage of the vulnerability that knocked the cyber world off its axis in 2021.
With ransomware gangs relentlessly attacking critical infrastructure sectors, organizations are rightfully fearful of looming threats. Ransomware attacks commanded attention in 2021, but also started off strong at the beginning of 2022. Threat actors are rethinking how they attack organizations and have gone beyond with their tactics and techniques – taking their attacks to the next level. According to Palo Alto’s Unit 42, 2021’s ransom demand climbed 133% ($2.2 million) and the average payment rose 78% ($541,010).
Ransomware will continue to be a challenge in 2022 as cyber criminals find new ways to exploit vulnerabilities and remove technical barriers. This year, we have seen several ransomware gangs compromise systems and networks, but one gang in particular has caught the attention of the FBI as well as cyber security researchers. AvosLocker ransomware has targeted organizations in multiple critical infrastructure sectors within the U.S. including the Financial Services, Critical Manufacturing, and Government sectors.
In addition to the U.S., the ransomware gang has targeted Arabia, Germany, Belgium, Spain, Turkey, the United Arab Emirates, the United Kingdom, Canada, Taiwan, and Saudi Arabia. Let’s take a look at AvosLocker ransomware, their tactics and techniques, and how threat actors are using excellent customer service to keep the ransom payments coming.
avoslocker ransomware & christus health
In March 2022, the FBI and the U.S. Treasury Financial Crimes Enforcement Network released a joint advisory addressing AvosLocker and their activity targeting organizations across several critical infrastructure sectors. The RaaS gang deploys ransomware onto their victim’s networks and systems, then threatens to leak their files on the dark web if they don’t pay up. AvosLocker is both the name of the RaaS gang, as well as the name of the ransomware itself.
In May 2022, AvosLocker took responsibility for attacking and stealing data from the Texas-based healthcare organization, CHRISTUS Health. CHRISTUS Health runs hundreds of healthcare facilities across Mexico, the U.S., and South America. The group stole information from a cancer patient registry which included names, social security numbers, diagnoses, dates of birth, and other medical information. The nonprofit Catholic health system has more than 600 healthcare facilities in Texas, Louisiana, New Mexico, and Arkansas. There are also facilities in Columbia, Mexico, and Chile.
Fortunately, the ransomware attack was quickly identified and was limited. While other healthcare organizations have not been as fortunate with ransomware attacks, the AvosLocker attack didn’t impact CHRISTUS Health’s patient care or clinical operations. CHRISTUS Health didn’t reveal whether or not the security incident included ransomware, data exfiltration or extortion, but due to AvosLocker’s reputation, it is more than likely that the incident included at least one of the three.
CHRISTUS Health is not the only healthcare entity impacted by AvosLocker. In April 2022, AvosLocker allegedly attacked McKenzie Health System and leaked data on their leak site. McKenzie Health System reported a hacking incident to the U.S. Department of Health and Human Services and disclosed a security incident regarding a network server. The incident affected over 25,300 people and disrupted some of the health care organization’s IT systems. After an investigation, McKenzie Health disclosed in a statement that a “third party” breached its systems and removed some files. They didn’t name AvosLocker or any other threat actor as the culprit, but researchers found McKenzie Health’s data on AvosLocker’s data leak site in April 2022.
techniques and tactics
AvosLocker was discovered advertising on dark web forums in July 2021 and has been observed targeting Windows machines. The group works with affiliates and splits the profits they receive with a select group of developers. AvosLocker also uses Any Desk ( a remote administration tool) to connect to victims’ machines and manually operate and infect their machines.
According to Trend Micro’s observations, AvosLocker uses Zoho ManageEngine ADSelfService Plus as an entry point into their victim’s systems and networks. They also use spam email campaigns as an initial infection vector to deliver their ransomware payload. Although Trend Micro couldn’t pinpoint a particular CVE ID, they saw some indications that AvosLocker abuses CVE-2021-40539. The group also evades detection by disabling anti-virus solutions.
According to Qualys, process files are appended with the “.avos” extension during the encryption process, while an updated variant appends with the “.avos2” extension. The Linux version also appends with the extension “.avoslinux”. Once their attack is successful, the threat actor publishes the names of their victims on their data leak site which is hosted on the TOR network. This site provides exfiltrated data for sale, which can be found at hxxp://avosxxx…xxx[.] onion. The gang’s latest ransomware variants are located on another leak site. There, you will find AvosLocker’s claims to the “latest Windows variant” – the fastest in the market with scalable threading and selective cyphers.
Now, AvosLocker has added support for encrypting Linux systems. They especially target VMware ESXi virtual machines, which gives them access to a much wider range of organizations. AvosLocker also has the ability to kill ESXi VMs. Additionally, AvosLocker exploits several ProxyShell vulnerabilities including CVE-2021-34473, CVE-2021-31206, CVE-2021-34523, and CVE-2021-31207.
AvosLocker’s ransom note is named “GET_YOUR_FILES_BACK.txt” and is located in each encrypted directory before the file is encrypted. The note gives instructions for the victim which include not shutting down the system (in case encryption is in progress) to avoid corrupting files. The note also asks their victims to visit an onion address with the TOR browser. The site instructs the victim to pay the ransom in order to retrieve the decryption key to decrypt the application or files.
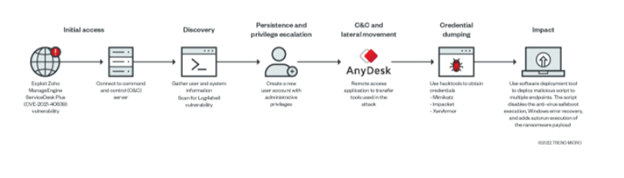
Image 1: AvosLocker Infection Chain
Source: Qualys
The victim submits their payment via a “payment page”. If the payment is not made, then their data goes up for sale. Also, an affiliate program is offered by AvosLocker. The program provides RaaS, as well as services to clients. Those services include:
- Supports Windows, Linux & ESXi.
- Affiliate panel
- Negotiation panel with push & sound notifications
- Assistance in negotiations
- Consultations on operations
- Automatic builds
- Automatic decryption tests
- Encryption of network resources
- Killing of processes and services with open handles to files
- Highly configurable builds
- Removal of shadow copies
- Data storage
- DDoS attacks
- Calling services
- Diverse network of penetration testers, access brokers and other contacts
AvosLocker and Linux
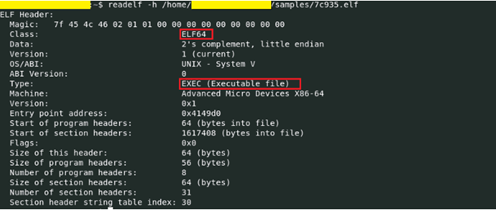
Linux has seen its fair share of vulnerabilities, but AvosLocker’s malware arrives in Linux as an elf file. The file that was analyzed by the research group Qualys, is a x64 based Linux executable file. There is also a command-line application which has some command-line options.
Image 2: Linux File
Source: Qualys
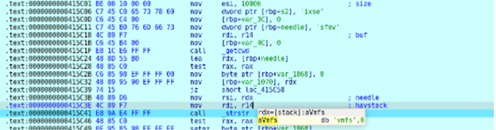
According to Qualys, after execution, AvosLocker collects information regarding the number of threads that need to be created. It then checks for string “vmfs” in the file path provided as a command line argument. Next, it checks for the string ESXi in the file path and once the parameter is found, it calls a routine to kill the running ESXi virtual machine. Finally, AvosLocker drops the ransom note file at the targeted directory and creates a list of files to be encrypted. Please note that only regular files are added to the encryption list. If the file has the extension “avoslinux” then that it’s skipped and isn’t added to the encryption list.
Image 3: vmfs
Source: Qualys
Before AvosLocker starts file encryption, a ransom note named “README_FOR_RESTORE” is created.
Image 4: Ransom Note
Source: Qualys
ransomware 2022
Ransomware continues to remain a threat to organizations everywhere. Ransomware is malware that is often used by cyber criminals who seek financial gain. Just like any other malware, ransomware is delivered to victim’s networks and systems by exploiting known vulnerabilities. Threat actors will take advantage of systems that have not been patched or that have already been compromised and they will use phishing email scams and social engineering tactics to deploy their ransomware.
Once the threat actor is in a system and has the opportunity to deploy their ransomware, the malware overtakes the victim’s files and systems – encrypting key information. The information is often rendered unusable to the organization and the threat actor will then demand a ransom payment in exchange for decryption. If the ransom is not paid, then data is either held hostage or leaked for all to see.
Ransomware attacks pressure victims to pay up and in full or else.
According to Palo Alto’s research on ransomware attacks for 2022, the most targeted regions for ransomware attacks include the Americas, Europe, the Middle East, Africa, and Asia Pacific – with construction and professional and legal services being the most targeted sectors. Because the long-term effects of a ransomware attack can be devastating and go beyond the actual cost of the ransom, it’s important for organizations to remain vigilant with protecting their cyber environments.
- Americas – 60% of victims listed attributed to this region
- Africa, Europe, Middle East, and Asia Pacific – 31% and 9% were attributed to these regions respectively
At the tail end of 2021, ransomware gangs exploited Log4Shell (CVE-2021-44228) quickly. Log4Shell is a zero-day critical vulnerability was found in the Apache Log4j2 Java-based logging library. It is an unauthenticated remote code execution (RCE) flaw that allows for complete system takeover with Log4j2.0-beta9 up to 2.16.1. This means that the flaw could allow attackers to install cryptominers and steal data, as well as credentials.
Because organizations failed to patch the vulnerability when it was disclosed, threat actors had a field day. After the news broke about how easy it was to exploit Log4j2, threat actors made swift moves. Log4Shell resulted in massive world-wide scanning with the payloads running from miners, Unix DDoS malware, and framework stagers pushed to compromised hosts.
This kind of mass scanning was expected because as with any exploit, attackers with motives will exploit anything they can in order to receive what they want (money, credentials, sensitive data, etc.). However, since December 2021, the issues surrounding Log4Shell still persist and there is no sign of them disappearing. Now, in 2022, Log4j is still being exploited, this time, by AvosLocker. The ransomware gang has been observed scanning multiple endpoints for the Log4j vulnerability using NmapNSE script.
ransomware trends on the rise
Ransomware trends are on the rise and there are three in particular that everyone needs to keep an eye on:
- Victim Shaming - While victim shaming isn’t new, it certainly has increased with the use of multi-extortion techniques in an effort to force organizations to pay the demanded ransom. Currently, threat actors will not only encrypt files, but they will also use their leak sites as leverage and threaten follow-on attacks (i.e., DDoS attacks) to get a swift payout. They’ll release samples of stolen data on the dark web to prove they have the information and are serious about releasing all of it. This also stops offline backups from keeping the negative effects of a ransomware attack to a minimum.
- RaaS Lowers Technical Bar – Because ransomware has been proven to be so successful and produce large payouts, cyber criminals carry out easy attacks – lowering the barrier to entry and expanding the reach of ransomware. RaaS is now being offered by “entrepreneurial” threat actors who are simply trying to capitalize on a growing number of cyber criminals who want a piece of the action. The “entrepreneurs” offer RaaS to cyber criminals and have agreements with set terms for providing ransomware affiliates – often in exchange for monthly fees of a percentage of a ransom. This is a trend that is expected to increase in 2022.
- Increasing the Use of Zero-Day Vulnerabilities – Ransomware attacks generally leverage a variety of vulnerabilities, but in 2021, there were at least 42 vulnerabilities, observed by Palo Alto, being used by ransomware operators. Threat actors are starting to track high profile vulnerabilities to gain an initial foothold in an organization’s system. Palo Alto has observed the timeframe from vulnerability to exploit getting shorter. This happened with Microsoft Exchange Server Vulnerabilities (CVE-2021-26855 and CVE-2021-27065).
ransomware gang customer service & paying the ransom
Ransomware and big business may have more in common than one might think. Ransomware operations are starting to behave more like businesses than criminals. In 2022, ransomware gangs are renting out office space, hiring graphic designers to beautify their web presence, and they are even providing prompt customer service to their victims and/or clients. From the outside looking in, these ransomware gangs look a lot like tech companies and operate as if they are Fortune 500 companies. They have investments in development, and they market their products and services just like any other company would.
Ransomware gangs like Conti can sometimes appear to be more disciplined than a lot of legitimate tech companies. They have an agile development framework that is often seen in Silicon Valley – go offline to develop, come back online to test, then retreat to work out the kinks and flaws. Some might say that ransomware is experiencing its own tech bubble with groups setting themselves apart from competitors by pulling bigger hauls, being hyper organized, and sometimes corporatizing their operations.
Ransomware dates back to the 1980s and became even more common in the 2000s. SamSam ransomware was one of the first to offer first class customer service for their victims and now, other threat actors are following suit. Conti has developed a reputation for prompt response times – replying in minutes or hours instead of leaving their victims waiting. This creates a sense of trust with their victims and has ushered in a new era of brand conscious ransomware gangs.
While a ransomware gang with phenomenal customer service may convince you to pay their demanded ransom and cooperate, the FBI discourages you from doing just that. Paying the ransom only encourages other threat actors to target additional organizations and gives the green light for other cyber criminals to continue to distribute ransomware. Paying the ransom also helps fund the adversary’s illicit activities.
While it’s understood that your business operations may be disrupted or even be completely non-functioning, it’s always best to report ransomware incidents to the FBI immediately. The FBI has investigators and analysts, and they need critical information to help track the ransomware attackers, hold them accountable, and prevent future attacks. Field office contacts can be located at http://www.fbi.gov/contact-us/field-offices
How Avertium is Protecting Our CUSTOMERS
Even with anti-malware solutions installed, AvosLocker is a great risk to organizations. AvosLocker can disable anti-virus software and deploy their ransomware before you even realize they’re in your system. However, Avertium has advanced services that can help keep your organization safe:
- Avertium recommends utilizing our service for DFIR (Digital Forensics and Incident Response) to help you rapidly assess, contain, eradicate, and recover from a security incident like a malware attack.
- Implement XDR as a prevention method. Our XDR is a combination of monitoring software like LogRhythm, Microsoft Azure Sentinel, or AlienVault, combined with endpoint protection such as SentinelOne. XDR platforms enable cybersecurity through a technology focus by collecting, correlating, and analyzing event data from any source on the network. This includes endpoints, applications, network devices, and user interactions.
- MDR provides an in-depth investigation into potential threats on an organization’s network. Avertium’s risk-based approach to managed security delivers the right combination of technology, field-validated threat intelligence, and resource empowerment to reduce complexity, streamline operations, and enhance cybersecurity resilience. If you need a more advanced security solution, MDR is the next step. MDR is an outsourced security control solution that includes the elements of EDR, enhanced with a range of fundamental security processes.
- Avertium offers Zero Trust Architecture, like AppGate, to stop malware lateral movement.
Avertium’s Recommendations
Avertium and the FBI recommend the following guidelines for general ransomware attacks:
- Regularly back up data, air gap, and password-protect backup copies offline. Ensure copies of critical data are not accessible for modification or deletion from the system where the data resides.
- Implement a recovery plan that includes maintaining and retaining multiple copies of sensitive or proprietary data and servers in a physically separate, segmented, secure location (i.e., hard drive, storage device, the cloud).
- Identify critical functions and develop an operations plan in the event that systems go offline. Think about ways to operate manually if it becomes necessary.
- Implement network segmentation.
- Install updates/patch operating systems, software, and firmware as soon as they are released.
- Use multi-factor authentication where possible.
- Use strong passwords and regularly change passwords to network systems and accounts, implementing the shortest acceptable timeframe for password changes. Avoid reusing passwords for multiple accounts and use strong passphrases where possible.
- Disable unused remote access/RDP ports and monitor remote access/RDP logs.
- Require administrator credentials to install software.
- Audit user accounts with administrative or elevated privileges and configures access controls with the least privilege in mind.
- Install and regularly update anti-virus and anti-malware software on all hosts.
- Only use secure networks and avoid using public Wi-Fi networks. Consider installing and using a virtual private network (VPN).
- Consider adding an email banner to messages coming from outside your organization.
- Focus on cyber security awareness and training. Regularly provide users with training on information security principles and techniques as well as overall emerging cybersecurity risks and vulnerabilities (i.e., ransomware and phishing scams).
- Back-up critical data offline.
- Ensure copies of critical data are in the cloud or on an external hard drive or storage device. This information should not be accessible from the compromised network.
- Secure your back-ups and ensure data is not accessible for modification or deletion from the system where the data resides.
- Use multi-factor authentication with strong passwords, including for remote access services.
- Keep computers, devices, and applications patched and up to date.
Mitigating AvosLocker
- Maintain multiple copies of sensitive or proprietary data and servers in physically separate, segmented and secure locations (hard drive, storage device, the cloud).
- Implement network segmentation and maintain offline, password-protected data backups. This ensures limited disruption in case of an attack.
- Keep copies of critical data separate from the system where the data resides
- Install and update antivirus software on all hosts and enable real-time detection
- Install updates and patches to operating systems, software and firmware in a timely manner and stay up to date about new updates and patches.
- Review domain controllers, servers, workstations, and active directories for new or unknown user accounts.
- Audit and configure user accounts with least privilege in mind. Limit admin privilege only to those who need it and only for as long as they need it.
- Disable unused ports.
- Consider adding an email banner to emails received from outside your group
- Disable all hyperlinks in received emails.
- Use multi-factor authentication where possible.
- Use strong passwords, change passwords often and do not reuse passwords to network systems and accounts.
- Require admin credentials to install software.
- Only use secure networks and avoid using public Wi-Fi networks. Consider installing and using a virtual private network.
- Focus on awareness and training about ransomware and phishing scams.
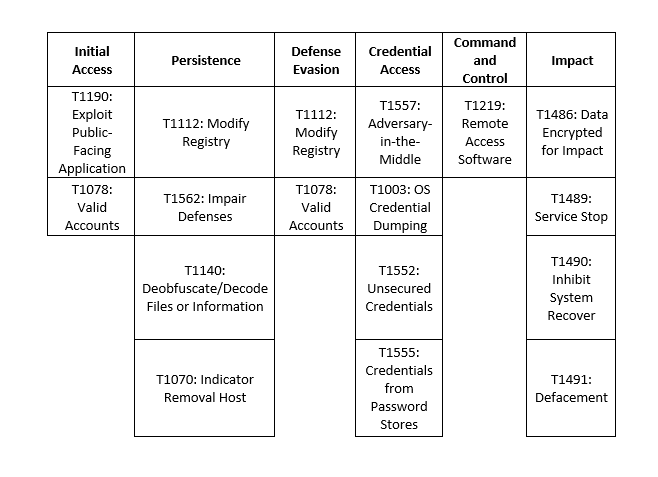
MITRE Map
Indicators of Compromise (IoCs)
- a5ad3355f55e1a15baefea83ce81d038531af516f47716018b1dedf04f081f15
- 05ba2df0033e3cd5b987d66b6de545df439d338a20165c0ba96cde8a74e463e5
- 912018ab3c6b16b39ee84f17745ff0c80a33cee241013ec35d0281e40c0658d9
- e81a8f8ad804c4d83869d7806a303ff04f31cce376c5df8aada2e9db2c1eeb98
- ddcb0e99f27e79d3536a15e0d51f7f33c38b2ae48677570f36f5e92863db5a96
- 14f0c4ce32821a7d25ea5e016ea26067d6615e3336c3baa854ea37a290a462a8
- According to the FBI:
- Persistence mechanisms on victim systems include the modification of Windows Registry
- 'Run' keys and the use of scheduled tasks.
- Tools associated with AvosLocker
- Cobalt Strike
- Encoded PowerShell scripts (publicly available tool)
- PuTTY Secure Copy client tool “pscp.exe”
- Rclone
- AnyDesk
- Scanner
- Advanced IP Scanner
- WinLister
SUPPORTING DOCUMENTATION
Top 5 cyber threats of Q1 2022 | Security Magazine
Remain Vigilant: Log4Shell Still Being Exploited (avertium.com)
AvosLocker Claims Data Theft From Another Healthcare Entity (govinfosecurity.com)
Microsoft Word - AvosLocker_CSA_TLP_White (ic3.gov)
Ragnar Locker Ransomware: Everything You Need To Know (Attacks & Analysis) (avertium.com)
FBI Releases AvosLocker Ransomware Advisory (securityintelligence.com)
Why good customer service is key to ransomware scams. (slate.com)
Ransomware group strikes second U.S. health care system in the last two months (cyberscoop.com)
AvosLocker ransomware - what you need to know | The State of Security (tripwire.com)
2022-unit42-ransomware-threat-report-final.pdf (paloaltonetworks.com)
Ransomware payments spiked 70 percent last year - The Washington Post
AvosLocker Ransomware Behavior Examined on Windows & Linux | Qualys Security Blog
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.
Related Resource: Ragnar Locker Ransomware: Everything You Need to Know (Attacks & Analysis)