- WHY AVERTIUM?
-
-
Why Avertium?
Context over chaos. Disconnected technologies, siloed data, and reactive processes can only get you so far. Protecting businesses in today’s threat landscape demands more than a set of security tools – it requires context.
That's where Avertium comes in
-
Considering Microsoft?
Avertium Named Microsoft Security Solutions PartnerAvertium’s managed services for Microsoft Security Solutions is delivered through the company’s premium service: Fusion MXDR. Fusion MXDR includes 24x7 monitoring and management of Defender for Endpoint and Sentinel, threat intelligence, attack surface
monitoring, and vulnerability management for Microsoft Security customers. -
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- SOLUTIONS
-
-
Governance, Risk, + Compliance
GRC with context – not complexity. -
Attack Surface Management
No more blind spots, weak links, or fire drills. -
Threat Detection + Response
Detect, adapt, and attack with context. -
Microsoft Security Solutions
End-to-end support from strategy to daily operations to maximize your Microsoft Security.
-
-
- COMPANY
-
-
About Us
Security. It’s in our DNA. It’s elemental, foundational. Something that an always-on, everything’s-IoT-connected world depends on.
Helping mid-to-enterprise organizations protect assets and manage risk is our only business. Our mission is to make our customers’ world a safer place so that they may thrive in an always-on, connected world.
-
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- PARTNERS
-
-
Our Partners
Best-in-class technology from our partners... backed by service excellence from Avertium.
-
Partner Opportunity Registration
Interested in becoming a partner?
With Avertium's deal registration, partners can efficiently and confidently connect with Avertium on opportunities to protect your deals.
-
Latest Avertium Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- NEWS & RESOURCES
-
-
News & Resources
Dive into our resource hub and explore top
cybersecurity topics along with what we do
and what we can do for you. -
Latest Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- CONTACT
Everything You Need to Know About Night Sky Ransomware
When: In December 2021, cybersecurity professionals panicked as Log4Shell challenged the safety of open-source security.
What: The vulnerability is an unauthenticated remote code execution (RCE) vulnerability and Log4j2 is a popular logging library that is used by millions of applications for logging. The Log4Shell exploit allowed for attackers to install cryptominers, as well as steal data and credentials.
Outcome: After the news broke about how easy it was to exploit Log4j2, threat actors made swift moves. Log4Shell resulted in massive worldwide scanning with the payloads running from miners, Unix DDoS malware, and framework stagers pushed to compromised hosts. Conti became the first sophisticated ransomware group to actively exploit the vulnerability, but now there is a new group of threat actors trying to get in on the action.
Who: A group of unknown threat actors have been using Night Sky ransomware to exploit vulnerabilities in Log4j2. There are a total of three Log4Shell vulnerabilities, and while patches are available, Night Sky is still an issue for unpatched versions of the Log4j2 software. Let’s look at Night Sky ransomware and why patching Log4j2 has become a challenge.
Log4Shell Re-cap
As we previously mentioned, we learned there was a critical zero-day vulnerability named Log4Shell in the Apache Log4j2 Java-based logging library. The vulnerability is an unauthenticated remote code execution (RCE) vulnerability that allows for complete system takeover on systems with Log4j 2.0-beta9 up to 2.16.1. Log4Shell could allow attackers to install crypto miners, as well as steal data and credentials.
Initially seen on sites hosting Minecraft servers, attackers discovered the vulnerability could be triggered by hosting chat messages. The first attacks were observed two weeks before they were publicly disclosed, and mass exploitation began a day after the vulnerability was made public. Those exploits originated from professional cryptomining and DDoS botnets, like Muhstik and Mirai. Additionally, Microsoft observed Log4Shell being used to deploy webshells with Cobalt Strike beacons, which are backdoors.
Because almost every network security system runs on some kind of logging process (with Log4j2 being the most popular logging library), Log4Shell was and still is a serious concern for organizations using the software. Millions of applications use Log4j2 and if an attacker had the Log4j2 app, they would be able to compromise it by logging a special string of characters. There ended up being three vulnerabilities associated with Log4Shell (CVE-221-44228, CVE-2021-4104, and CVE-2021-45046) and cyber security analysts knew it was only a matter of time before threat actors found a way to exploit every
single one.
WHAT IS NIGHT SKY RANSOMWARE?
Night Sky Ransomware
By January 2022, threat actors began to take advantage of the vulnerabilities in Log4j2. The vulnerabilities are:
- CVE-221-44228 – JNDI flaw in Log4j2.x.
- CVE-2021-4104 – addresses when an attacker has write-access to the Log4j configuration, causing JMSAppender to perform JNDI requests that result in remote code execution
- CVE-2021-45046 - allows the attacker to craft malicious input data using a JNDI Lookup pattern resulting in a denial of service (DOS) attack
Although patches are available, many systems remain unpatched, and Night Sky has been exploiting unpatched versions of VMware Horizon. The exploits follow VMware’s security alert warning that CVE-2021-44228 and CVE-2021-45046 were found in VMware Horizon and VMware Horizon Agent that runs on-premises.
Initially discovered by the security research group, MalwareHunterTeam, Night Sky is a new ransomware that is targeting corporate networks. The threat actors behind it are practicing double extortion – demanding payment for a decryptor, as well as for the non-release of stolen data.
The Night Sky operation started on December 27, 2021, and has already published the data of two victims on their Tor data leak site. According to MalwareHunterTeam, the victims are in Bangladesh and Japan. Night Sky demanded $800,000 from one of the victims in exchange for a decryptor and the non-release of all of their stolen data.
Cyber intelligence researchers at Microsoft believe that the threat actors behind Night Sky (tracked as DEV-0401) are based in China. Night Sky previously deployed several ransomware families (LockFile, AtomSilo, and Rook) and exploited other internet-facing systems running Confluence (CVE-2021-26084) and on-premises Exchange servers (CVE-2021-34473).
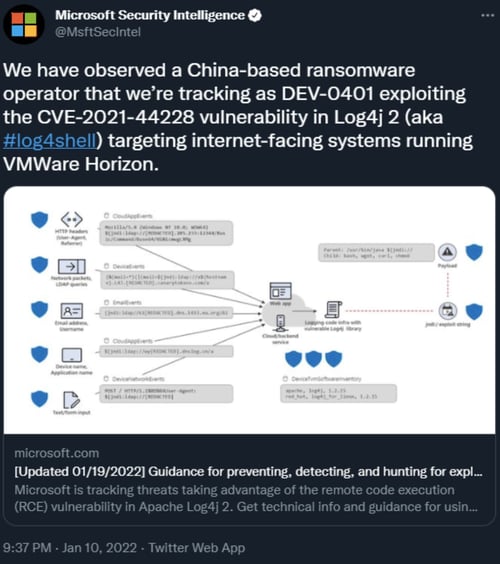
Image 1: Tweet from Microsoft
The United Kingdom’s National Health Service issued an alert warning that attackers compromised VMware Horizon to gain persistence on the National Health Service’s system. Although these attacks were attributed to a specific group, the Log4j flaw was used.
Source: Twitter
Night Sky's Tactics & Techniques
According to Microsoft, the China-based threat actors are using command and control (CnC) servers that spoof legitimate domains. These domains include:
- service[.]trendmrcio[.]com
- api[.]rogerscorp[.]org
- api[.]sophosantivirus[.]ga
- apicon[.]nvidialab[.]us
- w2zmii7kjb81pfj0ped16kg8szyvmk.burpcollaborator[.]net
- 139[.]180[.]217[.]203.
Analysts suspect that the threat actors behind Night Sky infiltrate corporate networks by using tried-and-tested methods, like social engineering tactics or by using stolen credentials. It’s also suspected that before Night Sky is launched, a human operator is involved in the reconnaissance, access, and eventual extraction of files from all network endpoints.
After the ransomware is launched. It encrypts the majority of the files on the affected computers, skipping files with extensions .dll and .exe. Night Sky also skips files and folders contained within the following folders:
| $Recycle.Bin | bootmgr | Mozilla Firefox |
| All Users | bootmgr.efi | ntldr |
| AppData | bootsect.bak | ntuser.dat |
| autorun.inf | desktop.ini | ntuser.dat.log |
| Boot | ntuser.ini | |
| boot.ini | iconcache.db | Opera |
| bootfont.bin | Internet Explorer | Opera Software |
| bootmgfw.efi | Mozilla | Program Files |
| Program Files (x86) | ProgramData | thumbs.db |
| Tor Browser | Windows | Windows.old |
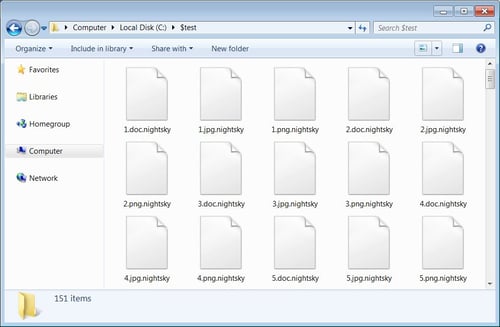
Image 2: Night Sky Extension
If your files have been encrypted by Night Sky, you’ll see the following .nightsky extension
Source: blog.malwarebytes.com
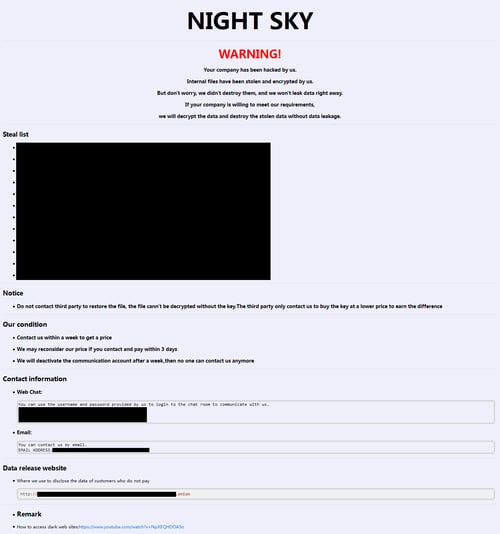
Image 3: Night Sky Ransom Note
Night Sky also drops a ransom note in every folder with encrypted files. The note’s file name is NightSkyReadMe.hta.
Source: blog.malwarebytes.com
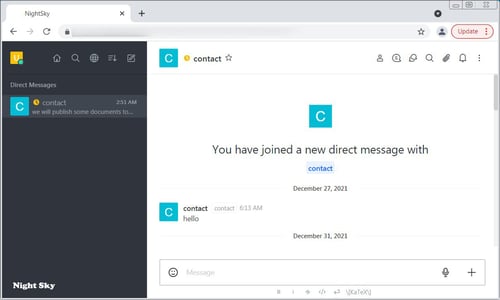
Image 4: Chat with Night Sky’s Threat Actors
The ransom note includes information about what Night Sky stole, email contacts, and “hardcoded credentials to the victim’s negotiation page”. The hardcoded credentials are then used by the victim to log into a chat (Rocket.Chat URL) so they can reach the threat actors directly.
Source: blog.malwarebytes.com
Log4j2 Patching Challenges
Because vendors are still in the process of identifying and patching vulnerable software and systems, Log4Shell remains an issue. It also doesn’t make things easier when the customers of those vendors have to test the updates and release them into their own environments. The open-source software vulnerabilities not only affect applications that use vulnerable libraries but any service that uses the applications. Customers may not immediately realize how widespread the issue is within their environment.
"Customers should assume broad availability of exploit code and scanning capabilities to be a real and present danger to their environments. Due to the many software and services that are impacted and given the pace of updates, this is expected to have a long tail for remediation, requiring ongoing, sustainable vigilance." – Microsoft
Although Night Sky is still a relatively new ransomware, it’s a good example of how Log4Shell exploits continue to escalate. With there being so many moving parts, it’s important for everyone who is affected by Log4Shell to do their due diligence and patch their devices. If you leave your device unpatched, you run the risk of threat actors (like those behind Night Sky) breaking into systems, stealing passwords and logins, extracting data, and infecting networks with malicious software. Also, the last thing an organization needs is to be forced into paying a ransom for their own data.
According to CISA, there are largely low-level attacks targeting Log4j2. The attacks that have been observed are primarily aimed at building botnets or cryptomining. However, the Director of CISA, Jen Easterly, warned that advanced threat actors probably already exploited Log4Shell to gain persistence and to go unnoticed on systems until defenders are less alert.
Related Resource: A Comprehensive Guide to Ransomware
How Avertium is Protecting Our CUSTOMERS AGAINST LOG4j2 and night sky ransomware
When the news broke about Log4j2, Avertium began hunting for evidence of vulnerable or exploited Log4j2 instances in customer environments. Avertium continues to hunt for threats for both Log4j2 and Night Sky ransomware. Take a look at how we controlled our customer environments with Log4j2 and the services we continue to offer for vulnerabilities pertaining to the Log4Shell exploit:
- Threat Report on Log4Shell: Avertium has published detectors for synchronizing IoCs of malicious scanning activity associated with the Log4Shell vulnerability to all customer SIEMs. The detections that we published for CVE-2021-44228 are still effective.
- Endpoint Detection + Response: Avertium has conducted Endpoint research and reconnaissance for strings associated with this exploit and continues to do so. We offer EDR services to help prevent and detect threats.
- Strategic Security Assessments: Avertium development teams completed an inventory and assessment of all internally developed software that uses Java, to ensure the vulnerability didn’t exist or was mitigated. Avertium offers Strategic Security Assessments so your organization can get a comprehensive view of your risk surface.
- Technology Partners: Avertium reached out to our technology vendors to verify and mitigate any potential exposure to the vulnerability.
- Third-Party Risk Assessment: Avertium has third-party vendor risk assessment services that you can utilize to help protect you from this vulnerability. Please contact your Account Executive or Service Delivery Manager for further details.
Avertium’s Recommendations
All organizations should scan for vulnerable applications that use Log4j2 and update them to the latest versions.
- Please patch your devices as soon as possible with the latest version of Log4j. Apache has released version 2.17.1 here.
- Please follow the instructions above to mitigate CVE-2021-45046 .
- Apache Log4j recommends the following temporary mitigation if upgrading is not possible:
- In releases >=2.10, this behavior can be mitigated by setting either the system property log4j2.formatMsgNoLookups or the environment variable LOG4J_FORMAT_MSG_NO_LOOKUPS to true. With the release of CVE-2021-45046 this is no longer sufficient!
- For releases from 2.0-beta9 to 2.10.0, the mitigation is to remove the JndiLookup class from the classpath: zip -q -d log4j-core-*.jar org/apache/logging/log4j/core/lookup/JndiLookup.class.
- Avertium recommends that your organization complete inventory and assessment of internally developed code and external vendor tools.
- VMware’s recommendations for the Log4j vulnerabilities can be found here.
- Detection methodology:
- Monitor network traffic for communication with known IPs/domains exploiting this vulnerability (see IOCs section)
- Configure NIDS devices with known Log4shell snort/suricata rules
- Search Java application logs for the following regex string: \$\{jndi:(ldap[s]?|rmi|dns):/[^\n]+
MITRE TTPS
- [T1087] Account Discovery Mitigation
- [T1110] Brute Force Mitigation
- [T1003] Credential Dumping Mitigation
- [T1486] Data Encrypted for Impact
- [T1005] Data from Local System Mitigation
- [T1087] Account Discovery Mitigation
- [T1110] Brute Force Mitigation
- [T1003] Credential Dumping Mitigation
- [T1005] Data from Local System Mitigation
- [T1211] Exploitation for Defense Evasion Mitigation
- [T1068] Exploitation for Privilege Escalation Mitigation
- [T1210] Exploitation of Remote Services Mitigation
- [T1046] Network Service Scanning Mitigation
- [T1068] Exploitation for Privilege Escalation Mitigation
- [T1210] Exploitation of Remote Services Mitigation
- [T1046] Network Service Scanning Mitigation
Indicators of Compromise (IoCs)
- Night Sky
- 139.180.217.203
- 45.32.125.79
- 45.76.188.137
- 87.120.36.12
- 2594077763e054861c086f49b8b1e9cf
- 9608c8b6c8d80fdc67b99edd3c53d3d2
- f9481915373852640150ffe98e7218ab
- 37b11d3d7b7a1d18daafd6c63b33526860aaefe6
- 44a124b9e5894b69a1ef108d9afcdb64e3591162
- 682fa27b596bab8fc5b7f2a0c002447e6e2f1f6b
- 197d3c8a1ebf4650196e677f6b992fad1cb0f066c4d7dae32f35d24a76b1acaf
- 1fca1cd04992e0fcaa714d9dfa97323d81d7e3d43a024ec37d1c7a2767a17577
- 59c9e91ce745914985b3a0b77f6b09c9776d4746de52f02648108961063b2ddd
- 8c1a72991fb04dc3a8cf89605fb85150ef0e742472a0c58b8fa942a1f04877b0
- 93f840951fc457649fe595f8149a20be91ed742afaa90aa95759f0b29c5f5668
- a077a55608ced7cea2bd92e2ce7e43bf51076304990ec7bb40c2b384ce2e5283
- c30d6587fb149c117f8cebc54407abfdf2cefc6096d8a4fc9e5d2e5f890d9f64
- e7e7b19c255ea052bb3c59b5597cdc92e76abe4dab72dacb92b16b7029e0d72f
- 207.148.122.171
- http://139.180.217.203:443/LockDown[.dll]
- http://45.32.125.79:443/LockDown[.dll]
- nightsky[.cyou]
- api.rogerscorp[.org]
- api.sophosantivirus[.ga]
- apicon.nvidialab[.us]
- contact.nightsky[.cyou]
- mail.nightsky[.cyou]
- service.trendmrcio[.com]
- w2zmii7kjb81pfj0ped16kg8szyvmk.burpcollaborator[.net]
- 6d87be9212a1a0e92e58e1ed94c589f9
- 9608c8b6c8d80fdc67b99edd3c53d3d2
- 19ce538b2597da454abf835cff676c28b8eb66f7
- 37b11d3d7b7a1d18daafd6c63b33526860aaefe6
- 8c1a72991fb04dc3a8cf89605fb85150ef0e742472a0c58b8fa942a1f04877b0
- c2d46d256b8f9490c9599eea11ecef19fde7d4fdd2dea93604cee3cea8e172ac
- suit[.md]
- As this situation continues to develop, new IOCs will be added to the following links for the Log4Shell vulnerabilities:
- https://gist.github.com/gnremy/c546c7911d5f876f263309d7161a7217
- https://otx.alienvault.com/pulse/61b392cc57bf8855ae21bacf
- https://otx.alienvault.com/pulse/61b37c3acdabe5ac09c5b500
Supporting Documentation
- Log4j CVE-2021-44228 and CVE-2021-45046 in VMware Horizon and VMware Horizon Agent (on-premises) (87073)
- New Night Sky Ransomware Enters Corporate Ransom Attack Scene | Cyware Alerts - Hacker News
- Night Sky Ransomware Distributed via Log4j Exploits (bankinfosecurity.com)
- NIGHT SKY RANSOMWARE IOCs - AlienVault - Open Threat Exchange
- Log4Shell Post-Mortem and What We Learned About Open-Source Security (avertium.com)
- Night Sky is the latest ransomware targeting corporate networks (bleepingcomputer.com)
- Night Sky: the new corporate ransomware demanding a sky high ransom | Malwarebytes Labs
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.
 DOWNLOAD OUR LATEST EBOOK >>>
DOWNLOAD OUR LATEST EBOOK >>>
In this eBook, you will learn:
- The newest and growing trends in cybersecurity tools, processes,
and data storage. - Major cyber attacks that occurred in 2021, their impact, and what
we can learn. - Our expectations for what cybersecurity will look like in 2022,
based on the data collections and observations from Avertium
security experts, as well as commentary from Avertium's partners. - The tools and services your organization needs to show no
weakness in 2022.