
Case Study:
INTERNOVA TRAVEL GROUP
Discover how Avertium helps unburden Internova Travel Group's security team to have the space to start focusing on more strategic cybersecurity priorities.
Threat actors continually innovate and adapt their tactics to deliver malware through phishing campaigns, often leveraging widely used software. Media coverage has highlighted the increased use of OneNote files as a first stage dropper to infect victim endpoints. Several threat families including IcedID, QakBot, AsyncRat, AgentTesla, have been observed abusing OneNote documents.
To address this emerging infection vector, Avertium’s threat hunters have been studying these files to improve detection methods and hunt for those that have evaded existing detections. Our research focuses on the exploitation of embedded files within OneNote, a prominent technique in recent adversary campaigns. By gaining a deeper understanding of this technique, we aim to proactively counteract the evolving strategies employed by threat actors and safeguard against potential vulnerabilities. Let’s dive into the analysis of embedded files in malicious OneNote Documents.
We downloaded five different malicious OneNote files to develop a sample of common activity among these files. The samples were associated with threat families like Emotet, Snake Keylogger, Qakbot, and Gozi. Initially, we ran the command “file” against the OneNote files, but it only categorized the files as “data”.
Image 1: Command on How to Identify OneNote Files 1
Thankfully, “trid” was able to identify them as Microsoft OneNote files.
Image 2: Command on How to Identify OneNote Files 2
As an alternative, we also executed XXD (HEX dump command) against the OneNote sample files to review the first few bytes, which were found to be identical. This approach could be valuable for creating a Yara rule that specifically looks for OneNote files. The below condition uses big endian to check the first four bytes of the file.
Image 3: Command on How to Identify OneNote Files 3
An example condition for a Yara rule based on this could be what we see below.
Unit32be(0x0) == 0xE4525C7B
According to Didier Stevens blog post on One Note files, the beginning of an embedded file section in OneNote is indicated by the following HEX string:
“E7 16 E3 BD 65 26 11 45 A4 C4 8D 4D 0B 7A 9E AC”
The HEX string corresponds to the GUID {BDE316E7-2665-4511-A4C4-8D4D0B7A9EAC}. This particular GUID is linked to the FileDataStoreObject structure, which defines the data for a file data object, as specified by Microsoft.
Following this, OneNote reserves twenty bytes, wherein the initial eight bytes indicate the file length, the subsequent four bytes are unused and set to zero, and the final eight bytes are reserved and also set to zero. As a result, the resulting HEX string looks like the following:
“E7 16 E3 BD 65 26 11 45 A4 C4 8D 4D 0B 7A 9E AC ?? ?? ?? ?? ?? ?? ?? ?? 00 00 00 00 00 00 00 00 00 00 00 00".
Following the above HEX string, the embedded file data is stored. Fortunately, OneNote does not attempt to encrypt any of the contents, rendering the contents of the file readable in a HEX editor. An example screenshot of this is shown in image 4. Notice the content is represented in plaintext.
Image 4: Content Represented in Plain Text
Based on our findings, we can include this string in a Yara rule that searches for the FileDataStoreObject GUID in HEX format. This will allow us to identify all OneNote files that contain an embedded file.
$FileDataStoreObject = { E7 16 E3 BD 65 26 11 45 A4 C4 8D 4D 0B 7A 9E AC }
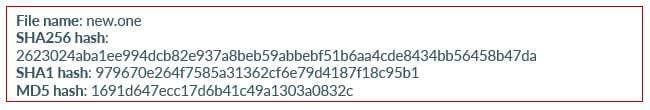
Now that we have gained a clear understanding of the contents of a malicious OneNote file, we can conduct further analysis on a single OneNote file. This will allow us to better understand the specimen, as well as how these files commonly work. Below is high-level information on the Specimen we will be analyzing.
What is commonly seen in these malicious OneNote files is an embedded file with a picture placed over it, with phrases to convince the user to click in the area the file is placed in. Below is an example of what this commonly looks like.
Image 5: Example of Malicious OneNote File
Source: Sophos
When the user clicks the “Open” image in the above screenshot, it opens the file hidden behind it. Didier Stevens developed a Python script to assist with analyzing OneNote files named onedump.py. After running it against the malicious OneNote file, the embedded objects appear to be in a similar format of what is commonly seen, with the .PNG images covering the “Set” object.
Image 6: Running onedump.py
After extracting the “Set” object, it provides the following PowerShell script, which creates a C2 connection via ‘Invoke-WebRequest’. This connection is used to download another PowerShell script called “boy1start.ps1”.
Image 7: PowerShell Script Inside OneNote File
From the above script, we have some useful indicators to assist with identifying this malicious OneNote file:

After accessing the website, it downloads a PowerShell script that contains a Base64 encoded executable, we provided sample snippets of the code below.
Image 8: Sample Snippets of Code 1
End of the script:
In the image below, it is worth noting that towards the end of the script, the Base64 encoding is decoded, and the resulting file, named 'boy1.pif,' is added to the 'C:\Users\Public' directory and subsequently executed.
Image 9: Sample Snippets of Code 2
After decoding the Base64, we were able to verify it as a Windows executable based on the Windows MZ signature at the beginning.
Image 10: Windows MZ Signature
After executing the dropped PowerShell script, it decoded the Base64 and dropped the file “boy1.pif” in the “C:\Users\Public” directory as expected. It’s worth mentioning that we removed the last line of the script (Start-Process -FilePath "C:\Users\Public\ boy1.pif"), which attempts to automatically execute the .pif file, allowing us to have better control of the file while analyzing it.
Image 11: Dropped PowerShell Script
After executing the dropped file “boy1.pif”, it was observed reaching out to IP address 37[.]139[.]128[.]83 which has a malicious reputation on multiple OSINT sites.
Image 12: Malicious File Reaching Out to IP Addressess
Our analysis of this particular file has reached its conclusion. It is strongly associated with Snake Keylogger, a malware known for exploiting Office and PDF documents to gather account credentials for use in account takeover. In addition, we observed various other malicious activities performed by the file. The activities include attempts to manipulate the task schedule using schtasks.exe and attempts to harvest and steal browser information (passwords, history, etc.).
Additionally, the file demonstrated the theft of FTP login credentials, emphasizing its scope of unauthorized access and potential for unauthorized file transfers. Finally, it actively attempted to identify the external IP address of the infected machine, potentially to establish remote control or facilitate communication with command-and-control servers.
Our analysis serves as a reminder of the ever-present threats lurking in cyberspace, with adversaries constantly honing their techniques and deploying increasingly sophisticated malware. Vigilance and robust security measures are essential in safeguarding against such threats. Stay informed, keep your defenses up-to-date, and remain proactive in protecting your digital assets from the evolving landscape of cybercrime.
Note: This blog entry was written by Senior Cybersecurity Analyst Alex Johnson, with editorial contributions by Portia Cole.
As an overview of this malicious OneNote files capabilities, below is a TTP breakdown based on MITRE ATT&CK.
|
Tactic_ID |
Tactic |
Technique_ID |
Technique |
Procedures |
|
Reconnaissance |
T1589.002 |
Gather Victim Identity Information: Email Addresses |
Adversaries may gather email addresses that can be used during targeting. Adversaries may easily gather email addresses, since they may be readily available and exposed via online or other accessible data sets. |
|
|
Initial Access |
Phishing |
Adversary will send a phishing email containing a “.One” attachment enticing the user to open the file and click the image that has a malicious attachment hidden behind it. |
||
|
Execution |
Command and Scripting Interpreter: PowerShell |
When the user clicks on the embedded file, it executes a malicious PowerShell script that is invoked by wscript. |
||
|
Defense Evasion |
Obfuscated Files or Information |
The downloaded PowerShell script has a “.pif” file encoded in Base64, which is decoded and dropped in the C:\Users\Public\ directory, then automatically executed. |
||
|
Collection |
Input Capture: Keylogging |
When executed, boy1.pif acts as a keylogger, attempting to harvest and steal browser information (passwords, history, etc), steal ftp login credentials, and attempts to identify the external address of the machine it infected. |
||
|
Command and Control |
Application Layer Protocol: Web Protocols |
The malicious PowerShell script invokes a web request to bitbucket[.]org to download a second PowerShell script. |
It’s important to get ahead of the curve by being proactive with protecting your organization, instead of waiting to put out a massive fire. Avertium can provide the following services to help keep your organization safe:
File Type: One Note
MD5 hash: 1691d647ecc17d6b41c49a1303a0832c
SHA1 hash: 979670e264f7585a31362cf6e79d4187f18c95b1
SHA-256 hash: 2623024aba1ee994dcb82e937a8beb59abbebf51b6aa4cde8434bb56458b47da
File Type: ASCII text, with very long lines (65536), with no line terminators
MD5: C0AA6A02799611928896463D8C6A324D
SHA1: 0FB21E6665E06E1C4014649872A1A0973195D11F
SHA-256: F9FD9B8F43086A5C5F8B638E12C83D6732B344D78F6A7071C18A9A2FC28915C2
File Type: PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows
MD5: 77472E194EB88BEFDA1974BFFB53240C
SHA1: B307F49590DDC1A1D4C432D315AD8C5DDEA05721
SHA256: 625C96F6FEDA28DAC1BF5CB32C9B83BCCEBE5B8D97155F431A0BADDC3D941A2D
hxxps[://]bitbucket[.]org/!api/2[.]0/snippets/mounmeinlylo/jqMGMx/27fc0a1358d8c2669262a0bed6bae8de365ff059/files/boy1start[.]ps1
37[.]139[.]128[.]83
-OutFile 'C:\Users\Public\boy1[.]ps1'
C:\Users\Public\boy1[.]pif
Related Resource:
Qakbot mechanizes distribution of malicious OneNote notebooks – Sophos News
Beta/onedump.py at master · DidierStevens/Beta · GitHub
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.