An In-Depth Look at the APT, Evilnum
Executive Summary
Active since 2018, the APT TA4563 (also known as Evilnum) is a group that has launched several low volume but targeted attack campaigns against victims in the UK and Europe. The group initially only targeted the financial sector but has now switched gears and is targeting immigration organizations.
Evilnum was also observed targeting organizations related to cryptocurrency and DeFi, placing backdoors in their systems which allow the threat actors to steal valuable information or wait for opportunities to compromise financial platforms. We’ll discuss Evilnum’s evolution, their tactics and techniques, and why it’s important to pay attention to lesser-known threat actors.
evilnum 2018 - 2021
As previously stated, Evilnum is an APT that’s been active since 2018 and was named as such due to their flagship malware also being named Evilnum. Despite being active since 2018, little was known about the group until ESET analyzed their malware in 2020. They were previously seen attacking financial technology companies (fintech companies), using a toolset that consisted of custom, homemade malware combined with tools purchased from Golden Chickens and an MaaS provider.
ESET’s research revealed that Evilnum’s targets were financial companies that offered platforms and tools for online trading. Most of the targets were in Europe and the UK but attacks were also observed in Australia and Canada. Researchers believed that the geographical diversity of Evilnum’s attacks was due to the targeted companies having offices in several locations.
During this time, Evilnum’s primary goal was to spy on organizations and glean financial information from both the organization and their customers. Examples of the information the threat actor has been able to obtain includes:
- Internal presentations
- Spreadsheets that include lists, trading operations, and investments
- Software licenses
- Credentials for trading software
- Email credentials
- Addresses, credit card information, and identity documents for customers
- VPN configurations and other IT related information
.
tactics & techniques 2018 - 2021
During 2020, Evilnum’s tactics included spearphishing emails containing a link to a ZIP file hosted by Google Drive. The file contained shortcut files which extracted and executed a malicious JavaScript component all while displaying a decoy document. To trick victims into opening files, the shortcut files contained “double extensions” which victims thought were benign documents or pictures.
After the victim opened the shortcut file, the malware looked in the contents of its own file for lines with a particular marker and wrote them to a .js file. Next, the malicious JavaScript file executes, writes, and opens a decoy file that has the same name as the shortcut, but with the correct extension. The shortcut is then deleted.
The decoy documents included bills with proof of address and photos of credit cards or identity documents. The decoy documents resembled the same documents that financial institutions require from their customers when they join. Because the documents appeared to seem legitimate, researchers believed Evilnum collected the documents during years of operation.
The first stage of Evilnum’s attack was the JavaScript component, which deployed other malware such as a C# spy component and Golden Chickens components. Each component operated on its own and had their own C&C server. The servers used by Evilnum were referenced by IP addresses, except for the C&C servers used by the Golden Chicken components.
At this time, Evilnum’s malware came bundled in a MSI file (Windows Installer) and ran independently of the JS component. According to ESET, after the JavaScript malware gained initial access, the C# component was downloaded and executed. Once the MSI file was executed, there were three malicious components that were written to disk in %LOCALAPPDATA%\Microsoft\Mediia.
First, the file copier was executed so that it moved files to another location in %LOCALAPPDATA%. Next, the loader was executed and decrypted the contents of the file System.Memmory.dll (the malicious payload for the C# component). This version of Evilnum’s malware was capable of taking screenshots if the mouse was moved and was able to send them to the C&C - running commands, running other binaries via cmd.exe, and persisting in a compromised system via creating registry keys.
Evilnum primarily used publicly available tools (and still does), but also developed custom scripts. They kept their tools in password-protected archives but decompressed them on a victim’s PC as needed. The group also used LaZagne to retrieve stored passwords and IronPython to take screenshots and record DirectSound audio.
tactics & techniques 2022
As of 2022, Evilnum’s tactics and techniques have evolved. The group is now using MS Office Word documents, leveraging document template injection – delivering malicious payloads to their target’s machines. Surprisingly, Evilnum is not exploiting Follina (CVE-2022- 30190) – a June 2022 Windows/Office zero-day vulnerability which allows attackers to run malicious code on targeted systems. This might be because Follina is so well documented and publicized. The vulnerability also now has a patch, as well as workarounds.
While still targeting financial companies dealing with cryptocurrency and other currency, ThreatLabz observed the group changing their target from strictly financial organizations to intergovernmental organizations (IGO) in March 2022. One of the targeted organizations deals with international migration services. Evilnum boldly attacked an IGO, an entity that involves two or more nations to work on common interest issues.
Researchers stated that the recent targets were more than likely chosen by the threat actor to coincide with the Russia-Ukraine war. Their attacks have been low volume but targeted, with their deployed malware being used for reconnaissance and data theft (not specific to cryptocurrency theft).
ThreatLabz also observed several domains associated with Evilnum that weren’t detected by other security vendors – making Evilnum an APT that has successfully been flying under the radar for years. The malware also includes components to evade detection and modify infection paths.
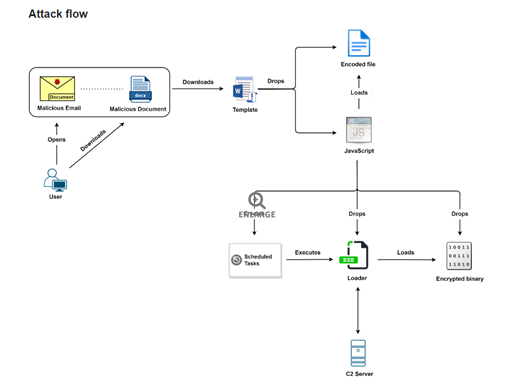
Image 1: Current Attack Flow
Source: Threatlabz
Evilnum starts their attacks by sending a malicious Word document to their victim via spear phishing emails with rogue attachments. Once the victim opens the Word document, a message is displayed claiming that the document was created in a later version of Microsoft Word. This message explains how to enable editing in order to view the content.
After the victim enables editing, an obfuscated JavaScript decrypts and deposits an encrypted binary and a malware loader before creating a scheduled task. To assist in avoiding detection, file system artefacts are created during execution, which are designed to imitate real Windows binary names.
Image 2: An Executable Attributed to Evilnum
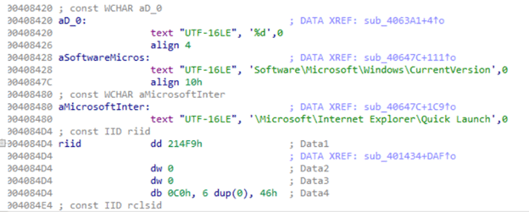
Source: Avertium's Cyber Threat Intelligence Team
In the screen shot above, you can see the strings that the program references to get environmental data from a compromised host. Evilnum’s goal is to create a backdoor on infected systems, while machine screen grabs are taken and sent back to the threat actors via POST requests with the exfiltrated data now being in encrypted form.
Selecting one of the C2 domains, the backdoor also selects a path string from the configuration and sends the beacon network request. The backdoor will then query the server for available content and downloaded it if the beacon is successful.
Immigration
You may be wondering why Evilnum would pivot to immigration. Multiple organizations that were set up after Russian troops invaded Ukraine, are assisting Ukrainian refugees. The lawyers that help to run the groups, don’t know much about cyber security but are still following strict regulations regarding client data by default. However, even though they’re performing security-centric tasks to keep data secure, they may not notice the crossover.
For instance, most interactions between lawyers and clients in the UK are done remotely. The reason for remote communication is primarily due to COVID-19 and because the UK’s visa system is online. Therefore, everything involving sensitive data starts in the form of an email. It sounds non-secure when you initially hear it, however lawyers and clients don’t email important documents in plain text. They use encrypted documents, secure file uploads, and delete data when required.
There are several things immigration organizations can do to keep sensitive information secure and safe from APTs like Evilnum:
- Your website should use HTTP over TLS, or HTTP over SSL (HTTPS) so that sensitive information isn’t intercepted because your website is insecure.
- Use an alias for public facing email addresses and lock down email addresses with MFA.
- Choose hardware-based security keys for 2FA (SMS won’t work without signal reception and attackers will divert your SMA codes).
- Use a password manager for organization passwords. If an organization must share passwords, use a management tool to share logins without revealing the password itself.
According to Malwarebytes Labs, there aren’t any UK based immigration organizations (including those focused on helping Ukrainians) who have been targeted by attacks similar to what we previously mentioned. However, those kinds of organizations are certainly targets for a threat actor looking to cause serious damage.
pay attention to lesser-known groups
Sometimes the cyber security community can spend too much time focused on threat actors who are making headlining news. While it’s important to keep up with what’s current, it’s equally important to pay attention to the threat groups who aren’t making a big splash with the media.
Evilnum is a threat actor that has flown under the radar since 2018 but has made a big impact regarding their attacks. Their attacks are very targeted but are not numerous. They also use legitimate tools in their attack chain. Those two incredibly calculated tactics are why Evilnum has been able to go undetected for so long.
When lesser-known threat groups and APTs like Evilnum pivot and evolve, it’s important to take note. This generally means that the group has a deeper plan and it’s only a matter of time before they make a major move and cause irreversible destruction. It's imperative that cyber security researchers be proactive and stay ahead by keeping a close watch on threat actors who lay low but are persistent and consistently active.
How Avertium is Protecting Our CUSTOMERS
APTs like Evilnum can fly under the radar and go undetected for years before causing destruction to an organization’s network or system. Avertium is here to keep your organization safe and to mitigate any attacks caused by APTs like Evilnum:
- To identify the source of your breach and the scope that it reached; you’ll want to include Avertium’s DFIR (Digital Forensics and Incident Response) services in your protection plan. We offer DFIR to mitigate damage from a successful breach. This service is provided as an on-demand crisis response service, as well as a retainer-based program.
- Implement XDR as a prevention method. Our XDR is a combination of monitoring software like LogRhythm, Microsoft Azure Sentinel, or AlienVault, combined with endpoint protection such as SentinelOne. XDR platforms enable cybersecurity through a technology focus by collecting, correlating, and analyzing event data from any source on the network. This includes endpoints, applications, network devices, and user interactions.
- MDR provides an in-depth investigation into potential threats to an organization’s network. Avertium’s risk-based approach to managed security delivers the right combination of technology, field-validated threat intelligence, and resource empowerment to reduce complexity, streamline operations, and enhance cybersecurity resilience. If you need a more advanced security solution, MDR is the next step. MDR is an outsourced security control solution that includes the elements of EDR, enhanced with a range of fundamental security processes.
- Avertium offers VMaaS to provide a deeper understanding and control over organizational information security risks. If your enterprise is facing challenges with the scope, resources, or skills required to implement a vulnerability management program with your team, outsourced solutions can help you bridge the gap.
- Avertium offers user awareness training through KnowBe4. The service also Incident Response Table-Top exercises (IR TTX) and Core Security Document development, as well as a comprehensive new-school approach that integrates baseline testing using mock attacks.
Avertium’s Recommendations
- Tabletop Exercises: Have a good cyber incident response plan in place that has been tested with tabletop exercises.
- Security Review: Be sure to review the plan and improve it every time it’s tested on real cyber threats.
- Risk Analysis: Prevent an attack by ensuring your organization has a detailed defense strategy based on a risk analysis approach.
- Cybersecurity Education: Educate your employees on cyber security preparedness and the dangers of opening potentially malicious documents. Annual or quarterly training modules can help prevent threat actors from tricking employees into opening malicious email attachments.
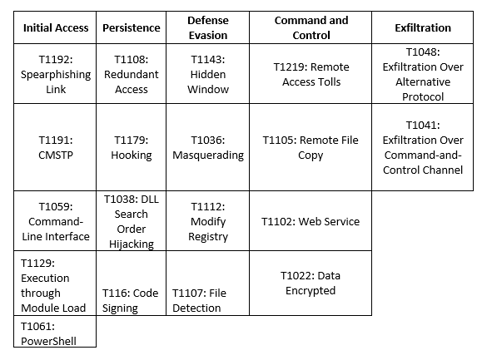
MITRE Map
Indicators of Compromise (IoCs)
C2 Domains
- travinfor[.]com
- webinfors[.]com
- khnga[.]com
- netwebsoc[.]com
- infcloudnet[.]com
- bgamifieder[.]com
- bunflun[.]com
- refinance-ltd[.]com
- book-advp[.]com
- mailservice-ns[.]com
- advertbart[.]com
- inetp-service[.]com
- yomangaw[.]com
- covdd[.]org
- visitaustriaislands[.]com
- traveladvnow[.]com
- tripadvit[.]com
- moreofestonia[.]com
- moretraveladv[.]com
- estoniaforall[.]com
- bookingitnow[.]org
- travelbooknow[.]org
- bookaustriavisit[.]com
- windnetap[.]com
- roblexmeet[.]com
- netrcmapi[.]com
- meetomoves[.]com
- bingapianalytics[.]com
- azuredcloud[.]com
- appdllsvc[.]com
- udporm[.]com
- pcamanalytics[.]com
- nortonalytics[.]com
- deltacldll[.]com
- mscloudin[.]com
- msdllopt[.]com
URL Paths
- /actions/async.php
- /admin/settings.php
- /admin/user/controller.php
- /admin/loginauth.php
- /administrator/index.php
- /cms/admin/login.php
- /backend/login/ajax_index.php
- /wp-admin/media-new.php
- /get.php
- /auth/login
Hashes
- 0b4f0ead0482582f7a98362dbf18c219
- 4406d7271b00328218723b0a89fb953b
- 61776b209b01d62565e148585fda1954
- 6d329140fb53a3078666e17c249ce112
- db0866289dfded1174941880af94296f
- f0d3cff26b419aff4acfede637f6d3a2
- 79157a3117b8d64571f60fe62c19bf17
- 63090a9d67ce9534126cfa70716d735f
- f5f9ba063e3fee25e0a298c0e108e2d4
- ea71fcc615025214b2893610cfab19e9
- 51425c9bbb9ff872db45b2c1c3ca0854
Supporting Documentation
More evil: A deep look at Evilnum and its toolset | WeLiveSecurity
Evilnum APT returns with updated TTPs and New Targets | Blog (zscaler.com)
How Evilnum Cyberattacks Target Microsoft Office Files - MSSP Alert
Immigration organisations targeted by APT group Evilnum | Malwarebytes Labs
Flash Notice: "Follina" a Microsoft Office Zero-Day RCE Vulnerability (avertium.com)
Buy, Sell, Steal, EvilNum Targets Cryptocurrency, Forex, Commodities | Proofpoint US
Hackers Use Evilnum Malware to Target Cryptocurrency and Commodities Platforms (thehackernews.com)
Cybercrime Group TA4563 Targets DeFi Market With Evolving Evilnum Backdoor (darkreading.com)
No Rest for the Wicked: Evilnum Unleashes PyVil RAT (cybereason.com)
EVILNUM Removal Report (enigmasoftware.com)
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.
Related Resource: Everything You Need to Know About the APT, Fancy Bear