- WHY AVERTIUM?
-
-
Why Avertium?
Context over chaos. Disconnected technologies, siloed data, and reactive processes can only get you so far. Protecting businesses in today’s threat landscape demands more than a set of security tools – it requires context.
That's where Avertium comes in
-
Considering Microsoft?
Avertium Named Microsoft Security Solutions PartnerAvertium’s managed services for Microsoft Security Solutions is delivered through the company’s premium service: Fusion MXDR. Fusion MXDR includes 24x7 monitoring and management of Defender for Endpoint and Sentinel, threat intelligence, attack surface
monitoring, and vulnerability management for Microsoft Security customers. -
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- SOLUTIONS
-
-
Governance, Risk, + Compliance
GRC with context – not complexity. -
Attack Surface Management
No more blind spots, weak links, or fire drills. -
Threat Detection + Response
Detect, adapt, and attack with context. -
Microsoft Security Solutions
End-to-end support from strategy to daily operations to maximize your Microsoft Security.
-
-
- COMPANY
-
-
About Us
Security. It’s in our DNA. It’s elemental, foundational. Something that an always-on, everything’s-IoT-connected world depends on.
Helping mid-to-enterprise organizations protect assets and manage risk is our only business. Our mission is to make our customers’ world a safer place so that they may thrive in an always-on, connected world.
-
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- PARTNERS
-
-
Our Partners
Best-in-class technology from our partners... backed by service excellence from Avertium.
-
Partner Opportunity Registration
Interested in becoming a partner?
With Avertium's deal registration, partners can efficiently and confidently connect with Avertium on opportunities to protect your deals.
-
Latest Avertium Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- NEWS & RESOURCES
-
-
News & Resources
Dive into our resource hub and explore top
cybersecurity topics along with what we do
and what we can do for you. -
Latest Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- CONTACT
An In-Depth Look at Russian Threat Actor, Killnet
Executive Summary
Since January 2022, the Russia and Ukraine war has been at the forefront of cyber space. From malware wipers to DDoS attacks, Russia and Ukraine have gone back and forth with retaliatory cyber attacks. Threat actors have declared their allegiance to either Russia or Ukraine and continue to make threats as the cyber war continues.
When it seemed like Russia had the upper hand after deploying malware-like worms such as HermeticWiper and WhisperGate, Ukraine turned the tables and began attacking Russia mercilessly. After the back and forth with deploying wipers, pro-Ukraine hacktivists started to take matters into their own hands – including Anonymous. Anonymous, NB65, DoomSec, AgainstTheWest, and other hacktivist groups bombarded Russia with cyber attacks, releasing the sensitive data of Russian soldiers and even hacking into Russia’s state-run television channels.
However, the tides have once again turned and Russian hacktivists like Killnet are making threats against and attacking not only Ukraine, but the U.S. as well. Alas, this is not Killnet’s first run at threatening and attacking countries who support Ukraine. In June 2022, Killnet claimed responsibility for a DDoS attack on the European country, Lithuania. The attack was in response to the country’s decision to block transit goods sanctioned by the European Union to the Russian exclave of Kaliningrad. As a result, Killnet disrupted 1652 of Lithuania’s web resources. Let’s take a look at Killnet, their tactics and techniques, and why organizations with weak cybersecurity posture may fall victim to a threat group like Killnet.

killnet
Killnet is a pro-Kremlin hacker group known for targeting European governments and infrastructure via disinformation campaigns. When the Russia and Ukraine war began, the group immediately took a stance and sided with Russia. Although there have been more than 100 groups that have deployed cyberattacks against the two countries, Killnet has been one of the most vocal and active among the groups.
Unlike other highly-skilled Russian threat groups (Sandworm and FancyBear), Killnet is not sophisticated and is not a well-organized threat group. The group is semi-structured, comprised of smaller lesser-known groups who are also sympathetic towards Russia. Killnet is known for spreading propaganda and disinformation. Pro-Russia groups associated with Killnet include Legion and Xaknet.
Often communicating via Telegram, Killnet uses the social platform to make announcements regarding their future attacks, as well as successful attacks. The conversations in the chat are often riddled with Russian propaganda and unfavorable opinions towards countries that are not in support of Russia. The channel also contains information regarding attacks against Anonymous – a pro-Ukraine hacktivist group. When Killnet launched their attack on Lithuania, Anonymous responded and launched a campaign to take down Killnet.
By March 2022, Killnet launched DDoS attacks against a Ukrainian news service and the Ukrainian branch of Vodafone. They also attacked the Ministry of the Interior of Latvia. By the end of March 2022, they began attacking Poland, starting with the website of the Supreme Court in the Republic of Poland – following up with an attack on Narodwy Bank Polski (National Bank of Poland). Next, Killnet launched another DDoS attack against the Polish Investment and Trading Agency, which resulted in a 20GB data leak. The threat actor claimed that all of their attacks were in response to countries outwardly stating their non-support of Russia.
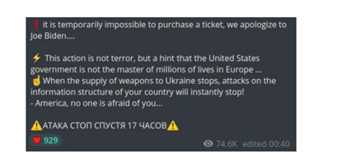
In April 2022, Killnet successfully attacked the United States by launching a DDoS attack on Bradley International Airport’s website. The incident was isolated to the airport’s website and did not impact airport operations. However, the objective for the attack was to prevent military aid to Ukraine.
Image 1: Telegram Message from Killnet
Source: Forescout
The previously mentioned attacks were followed up with an attack on CYBERPOL’s website and an attack against the Federal Ministry of Defence (intentional spelling) of Germany. Killnet also launched several attacks on German airports and financial organizations, as well as attacks on eight airports in Poland. Killnet even launched a “special attack” as homage to the threat actor REvil. The attack was against the U.S. energy entity Devon Energy Corporation. It was not clear if the attack was solely against the company’s website or if the company’s infrastructure was attacked as well.
The messages in Killnet’s Telegram channel are primarily centered around their disdain for countries that won’t stop supporting Ukraine. Some messages are aggressive and obscene, corresponding with Killnet’s attacks. Many of their announcements between April 19 and May 2022 contain reports related to successful attacks against Poland, Romania, Estonia, the UK, France, Lithuania, and the U.S. Interestingly, the messages within the channel are written in Russian, so despite the group’s constant hate speech, their ideals have not reached their intended audiences. The motivation behind Killnet’s attacks is purely political and has nothing to do with financial gain.
tactics & techniques
According to researchers from Forescout, Killnet’s attack vector of choice is Distributed Denial of Service (DDoS). They don’t use or develop custom tools and the tools that they do use are not very sophisticated. The group has a preference for brute-forcing credentials on TCP ports 21 (FTP), 80 (HTTP), 443 (HTTPS) and 22 (SSH).
Forescout set up honeypots and observed/analyzed Killnet’s attacks between April and May 2022. They observed 381 attacks coming from 58 unique IP addresses – 56 of which were dictionary attacks using well-known default credentials in hopes that their target wouldn’t change them. When utilizing brute-force, Forescout observed that Killnet’s attempts were exclusively against port 22, implying that the threat actor aims to have persistence/proxying capabilities. It also appeared that this action could be their way of conducting reconnaissance or credential harvesting for later use. Observed password attempts didn’t contain a specific pattern except for the passwords being weak.
The IP addresses that did not execute dictionary attacks, often repeated attacks over a course of three days. The IP addresses that did execute dictionary attacks, did not repeat the attack again. This implies different goals of attack scripts associated with each IP address. On the occasion that Killnet was tricked into an SSH session, they tried to use Forescout’s attacker engagement environment as a proxy toward google.com by attempting to create SSH tunnels.
After Killnet conducts a DDoS attack, they deface their target’s website and post pro-Russia messages. Killnet appears to work based off of emotion and revenge. If they believe that anyone has wronged Russia, they will retaliate by launching DDoS attacks against them. The group has often been described as a nuisance due to their lack of sophistication and their sometimes empty threats. They also only attack organizations via DDoS attacks, therefore their tactics and techniques are quite limited.
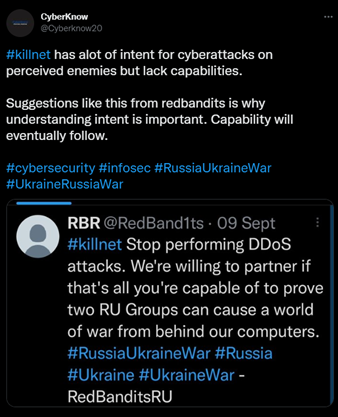
Image 2: Tweet from CyberKnow
Source: Twitter
Avertium’s technology partner, AdvIntel’s believes that the group is simply a DDoS group despite their constant threats. Killnet’s tactics are primitive and even though they are able to take a server down for a period of time, they seem to be more focused on publicity than anything else.
In fact, if a threat actor like Killnet is able to inflict damage on a target, it says more about the target’s cybersecurity posture than the threat group. Although Killnet’s bark is stronger than their bite, that does not mean that organizations should discount the group’s intent – which is disruption. Disruption is not something that critical infrastructure can afford.
organizations with weak cybersecurity posture
Cybersecurity is critical for all organizations, large and small. With new security risks emerging every day, it is important to put your organization in the best position when connected to the internet. Killnet may not be a highly sophisticated threat group, but their intent is still malicious. If your organization does not have excellent cyber security hygiene, that is a problem.
Cybersecurity simply means that your organization is actively working to protect data and keep it safe from internal and external adversaries. Additionally, establishing a cybersecurity governance and risk management program for your organization can help protect data and keep adversaries out of your systems and networks. If you aren’t sure where to start, the National Institute of Standards and Technology (NIST) has examples of framework profiles that organizations can use.
According to NIST, the Framework Profile is the alignment of the Functions, Categories, and Subcategories with the business requirements, risk tolerance, and resources of the organization. This Profile can help organizations develop a roadmap for reducing cybersecurity risk, while aligning with organizations and sector goals. All organizations are unique, therefore it is not unusual to have multiple Profiles to recognize different needs. Also, the NIST includes five concurrent and constant functions:
- Identify: Manage cybersecurity risk to assets, data, and people by developing an organizations’ understanding.
- Protect: Ensure the delivery of critical services by developing and implementing the appropriate safeguards.
- Detect: Organizations can identify security incidents if they develop and implement the appropriate activities.
- Respond: Organizations can take action against a detected threat if they develop and implement the appropriate activities.
- Recover: Maintain plans for resiliency and restoration of all services that were impaired due to a security incident by developing and implementing the appropriate activities.
How Avertium is Protecting Our CUSTOMERS
Avertium is here to keep your organization safe and to mitigate any attacks caused by threat actors like Killnet:
- To identify the source of your breach and the scope that it reached; you’ll want to include Avertium’s DFIR (Digital Forensics and Incident Response) services in your protection plan. We offer DFIR to mitigate damage from a successful breach. This service is provided as an on-demand crisis response service, as well as a retainer-based program.
- Implement XDR as a prevention method. Our XDR is a combination of monitoring software like LogRhythm, Microsoft Azure Sentinel, or AlienVault, combined with endpoint protection such as SentinelOne. XDR platforms enable cybersecurity through a technology focus by collecting, correlating, and analyzing event data from any source on the network. This includes endpoints, applications, network devices, and user interactions.
- Avertium offers Vulnerability Management to provide a deeper understanding and control over organizational information security risks. If your enterprise is facing challenges with the scope, resources, or skills required to implement a vulnerability management program with your team, outsourced solutions can help you bridge the gap.
- Fusion MXDR is the first MDR offering that fuses together all aspects of security operations into a living, breathing, threat-resistant XDR solution. By fusing insights from threat intelligence, security assessments, and vulnerability management into our MDR approach, Fusion MXDR offers a more informed, robust, and cost-effective approach to cybersecurity – one that is great than the sum of its parts.
- Minimizing the impact of a successful ransomware attack requires detecting it as early in the attack as possible. A Security Information and Event Management (SIEM) system can help an organization to accomplish this. Avertium offers a comprehensive SIEM-based approach that increases the potential for detecting a ransomware infection before it deploys. SIEM provides a holistic overview of a company’s IT environment from a single point of view in terms of its specific security events, empowering teams to detect and analyze unusual behavior.
avertium's recommendations
In addition to establishing a strong cybersecurity governance and risk management program, Avertium recommends that organizations do the following to help keep their websites and data safe from threat actors like Killnet:
Basic cybersecurity best practices:
- Employee Based Security - Train Employees to Develop Better Security Habits
- Create a strong password.
- Consider using a password manager.
- Use multi-factor authentication, if available.
- Use security questions properly.
- Create unique accounts for each user per device.
- Be suspicious of unexpected emails.
- Keep all of your personal electronic device software current.
- Network Based Security Practices
- Use and maintain anti-virus software and a firewall.
- Regularly scan for spyware.
- Keep software up to date.
- Evaluate your software settings.
- Avoid unused software programs.
- Establish guidelines for computer use.
- Encrypt sensitive files.
- Dispose of sensitive information properly.
- Physical Security Practices
- Password-protect all computers.
- Consider using physical locks on devices with sensitive information.
- Consider an alarm or lock.
- Back up your files.
- Implement physical access control plans.
- Conduct background checks as part of the hiring process when hiring someone who will have access to sensitive information.
Mitigation
- Firewalls can protect your systems from a cyber a DDoS attack from threat actors accessing the organization’s systems via both internal and external communication links.
- To remediate a DDoS attack, use a static version of your website. This ensures you’ll have a place to send traffic if the website is down.
- Artificial Intelligence can analyze traffic and block access from unknown or suspicious locations. It can determine what is normal or abnormal for your organization’s website traffic.
- Having different networks and paths for data servers is the first step to designing a robust architecture.
- If your organization has a DDoS response plan, you’re in good shape. This will ensure that you will be able to promptly respond to attackers targeting your network.
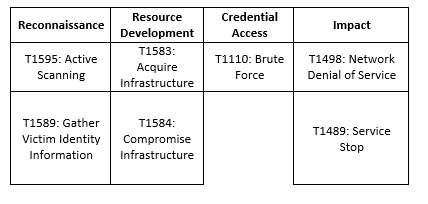
MITRE Map
Indicators of Compromise (IoCs)
IP Addresses
- 91[.]132[.]147[.]168
- 81[.]17[.]18[.]62
- 81[.]17[.]18[.]58
- 72[.]167[.]47[.]69
- 5[.]2[.]69[.]50
- 45[.]154[.]255[.]139
- 45[.]154[.]255[.]138
- 45[.]153[.]160[.]139
- 45[.]153[.]160[.]132
- 23[.]129[.]64[.]219
- 23[.]129[.]64[.]218
- 23[.]129[.]64[.]217
- 23[.]129[.]64[.]216
- 23[.]129[.]64[.]213
- 23[.]129[.]64[.]212
- 23[.]129[.]64[.]210
- 23[.]129[.]64[.]149
- 23[.]129[.]64[.]148
- 23[.]129[.]64[.]147
- 23[.]129[.]64[.]142
- 23[.]129[.]64[.]139
- 23[.]129[.]64[.]137
- 23[.]129[.]64[.]134
- 23[.]129[.]64[.]133
- 23[.]129[.]64[.]132
- 23[.]129[.]64[.]131
- 23[.]129[.]64[.]130
- 209[.]141[.]58[.]146
- 205[.]185[.]115[.]33
- 199[.]249[.]230[.]87
- 195[.]206[.]105[.]217
- 185[.]83[.]214[.]69
- 185[.]67[.]82[.]114
- 185[.]56[.]80[.]65
- 185[.]220[.]102[.]253
- 185[.]220[.]102[.]243
- 185[.]220[.]102[.]242
- 185[.]220[.]101[.]35
- 185[.]220[.]101[.]15
- 185[.]220[.]100[.]252
- 185[.]220[.]100[.]250
- 185[.]220[.]100[.]248
- 185[.]220[.]100[.]243
- 185[.]220[.]100[.]242
- 185[.]220[.]100[.]241
- 185[.]129[.]61[.]9
- 185[.]100[.]87[.]202
- 185[.]100[.]87[.]133
- 171[.]25[.]193[.]78
- 171[.]25[.]193[.]25
- 164[.]92[.]218[.]139
- 162[.]247[.]74[.]200
- 156[.]146[.]34[.]193
- 144[.]217[.]86[.]109
- 173[.]212[.]250[.]114
- 92[.]255[.]85[.]135
- 92[.]255[.]85[.]237
- 209[.]141[.]57[.]148
- 45[.]227[.]72[.]50
- 185[.]220[.]100[.]255
Supporting Documentation
How the Tables Have Turned - Russia vs. Ukraine Part Three (avertium.com)
https://www.forescout.com/resources/analysis-of-killnet-report/
Meet Killnet, Russia’s hacking patriots plaguing Europe – POLITICO
Retaliation by the Pro-Russian Group KillNet | Trustwave
5 Best Practices for Mitigating DDoS Attacks - Infosecurity Magazine (infosecurity-magazine.com)
Cybersecurity Is Critical for all Organizations – Large and Small | IFAC
Bradley Airport Website Suffers Cyber Attack – NBC Connecticut
Retaliation by the Pro-Russian Group KillNet | Trustwave
Cybersecurity Framework | NIST
Examples of Framework Profiles | NIST
Russian State-Sponsored and Criminal Cyber Threats to Critical Infrastructure | CISA
Killnet, pro-Russian hackers, knock some U.S. airport websites offline - The Washington Post
Meet Killnet, Russia’s hacking patriots plaguing Europe – POLITICO
US Airports in Cyberattack Crosshairs for Pro-Russian Group Killnet (darkreading.com)
Russia's Killnet hacker group says it attacked Lithuania | Reuters
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.