- WHY AVERTIUM?
-
-
Why Avertium?
Context over chaos. Disconnected technologies, siloed data, and reactive processes can only get you so far. Protecting businesses in today’s threat landscape demands more than a set of security tools – it requires context.
That's where Avertium comes in
-
Considering Microsoft?
Avertium Named Microsoft Security Solutions PartnerAvertium’s managed services for Microsoft Security Solutions is delivered through the company’s premium service: Fusion MXDR. Fusion MXDR includes 24x7 monitoring and management of Defender for Endpoint and Sentinel, threat intelligence, attack surface
monitoring, and vulnerability management for Microsoft Security customers. -
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- SOLUTIONS
-
-
Governance, Risk, + Compliance
GRC with context – not complexity. -
Attack Surface Management
No more blind spots, weak links, or fire drills. -
Threat Detection + Response
Detect, adapt, and attack with context. -
Microsoft Security Solutions
End-to-end support from strategy to daily operations to maximize your Microsoft Security.
-
-
- COMPANY
-
-
About Us
Security. It’s in our DNA. It’s elemental, foundational. Something that an always-on, everything’s-IoT-connected world depends on.
Helping mid-to-enterprise organizations protect assets and manage risk is our only business. Our mission is to make our customers’ world a safer place so that they may thrive in an always-on, connected world.
-
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- PARTNERS
-
-
Our Partners
Best-in-class technology from our partners... backed by service excellence from Avertium.
-
Partner Opportunity Registration
Interested in becoming a partner?
With Avertium's deal registration, partners can efficiently and confidently connect with Avertium on opportunities to protect your deals.
-
Latest Avertium Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- NEWS & RESOURCES
-
-
News & Resources
Dive into our resource hub and explore top
cybersecurity topics along with what we do
and what we can do for you. -
Latest Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- CONTACT
An In-Depth Look at Vice Society Ransomware
Executive Summary
At the beginning of September 2022, the Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) warned that a ransomware gang named Vice Society was targeting the education sector. The advisory stated that they expected an increase in attacks after the start of the 2022/2023 school year due to cyber criminal groups seeing opportunity.
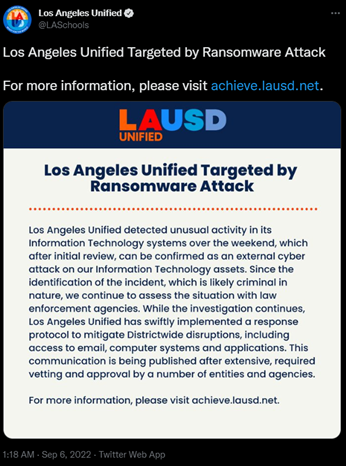
When the FBI and CISA issued the advisory on September 6, 2022, the Los Angeles Unified (LAUSD) school district announced that they were victims of a ransomware attack that took down some of their Information Technology systems. The district is the second largest school district in the U.S. and enrolls more than 640,000 students. At the time, a threat actor couldn’t be attributed to the attack, but later we would discover that the attack was the work of Vice Society.
In June 2022, Avertium published a Threat Intelligence Report regarding the top five cyber threats in education. In that report, ransomware was named as the number one threat and attack vector. Although the report was geared toward colleges and universities, the same holds true for K-12 education. In July 2022, Sophos conducted research and issued a whitepaper on the State of Ransomware in Education for 2022. The report included 320 respondents from lower education. Sophos discovered that 56% of the lower education organizations and 64% of the higher education organizations surveyed were hit by ransomware the previous year.
Also, lower education saw an increase in the volume of cyber attacks, as well as an increase in the complexity of cyber attacks. The report further stated that education has a low rate of cyber insurance coverage for ransomware. Threat actors like Vice Society know that the sector struggles in this area and it is likely a driving force behind their attacks on schools. Let’s take a look at Vice Society, their tactics and techniques, and how lower education school districts can better protect their cyber environments.
vice society
As previously stated, at the beginning of the 2022/2023 academic year, Vice Society launched a ransomware attack against the second largest school district in the U.S. – LAUSD. The attack took place over Labor Day weekend and disrupted LAUSD systems, including email servers. After the breach, LAUSD contacted officials including the White House, the Department of Education, the FBI, CISA, and the Department of Homeland Security.
Image 1: Tweet from Los Angeles Unified
Despite the disrupted LAUSD infrastructure, the district opened as usual while it worked to restore their servers. At this point, LAUSD was not sure of what kind of data was stolen, or if data was stolen at all. However, it didn’t take long for Vice Society to claim responsibility for the attack. A Vice Society representative told Bleeping Computer that they stole 500GB of data from LAUSD’s systems before encrypting them with ransomware, but they didn’t want to provide proof until they published an entry on their data leak site.
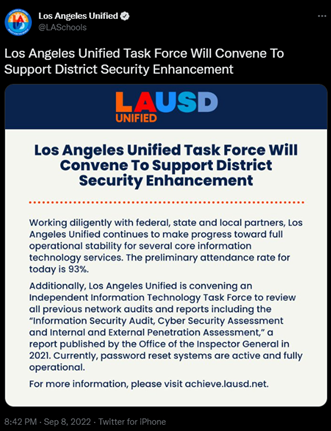
During that time, LAUSD made statements saying that their task force was making progress towards stabilizing their core information technology services. They also asked all district employees and students to reset their @LAUSD.net account credentials in person at a school site. The district also began a rollout of their multi-factor authentication process. The school district stated that it planned to establish an independent task force to review their system audits to determine how they were breached in the first place.
Image 2: Tweet from LAUSD
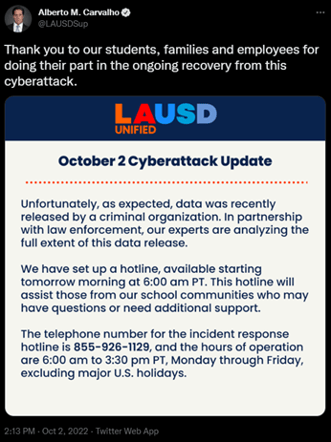
By October 2022, Vice Society published around 500GB of stolen data about students and employees of LAUSD. This was done in response to the school district’s superintendent stating that they would not be paying the demanded ransom (ransom amount is still unknown).
Image 3: Tweet from LAUSD Superintendent
Alberto Carvalho told the Los Angeles Times that the district was not going to pay the ransom to prevent data from being leaked because it was not a guarantee that the hackers wouldn’t end up leaking the data anyway. The district believed that the money could be put to better use such as funding different needs for students and their education.
Carvalho confirmed that the data was leaked and encouraged parents and student to ask questions about the leak through a new hotline. Vice Society has attacked at least eight other U.S. school districts and higher education institutions in 2022.
tactics & techniques
According to CISA, Vice Society is an intrusion, exfiltration, and extortion ransomware gang that initially appeared in the summer of 2021. Despite it being a new ransomware group, the gang is not using a new ransomware variant of unique origin. Vice Society is known for deploying versions of Hello Kitty, Five Hands, and Zeppelin ransomware. However, this does not mean that they will not deploy other ransomware variants in the future.
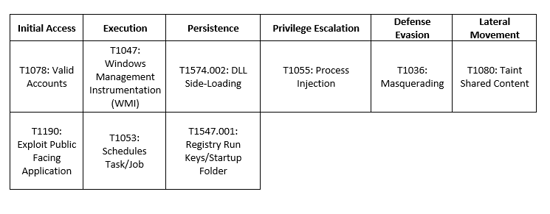
Vice Society obtains initial network access through compromised credentials by exploiting internet facing applications. Before deploying their ransomware, Vice Society explores their victim’s network to identify opportunities to increase accesses and to exfiltrate data for double extortion. The group has also been seen using several tools, including PowerShell Empire, SytemBC, and Cobalt Strike for lateral movement.
After the group achieves initial access, they use several techniques to conduct post-compromise discovery and reconnaissance within their target’s environment. While analyzing one of the group’s attacks, Cisco Talos observed Vice Society attempting to access the backup solution employed in their victim’s environment. The group likely performs this action to try and prevent their target from successfully recovering from an attack without paying the demanded ransom. According to Cisco Talos, the following “sudo” command was used to obtain credentials associated with a commercial backup solution to gain access to an organization’s backups.
sudo -s -k -p [Backup Prompt] whoami
Cisco Talos also observed the threat group using Impacket – a network protocol manipulation tool. The tool is used to enumerate the victim’s environment and obtain further information about the Active Directory configuration in place. Vice Society likely uses Impacket to identify high-value targets. The threat actors also use Impacket to execute Windows Management Instrumentation to achieve command execution on other systems present in the environment.
Additionally, Vice Society has been observed exploiting the PrintNightmare vulnerability. In August 2021, PrintNightmare (CVE-2021-34527) was a Microsoft vulnerability that affected the PrintSpooler service – a service that runs on every computer participating in the Print Services system for Windows-based print clients. PrintNightmare has been an issue for Windows users since 2021 and continues to be exploited by several threat actors.
In addition to exploiting PrintNightmare, Vice Society attempts to extract credentials from their victims in two ways:
- By accessing the Active Directory global catalog file dit and utilizing comsvcs.dll (comsvcs.dll is used to extract Local Security Authority Subsystem Service data).
- By invoking dll with rundll32.exe – a common living off the land binary tactic that avoids credential extraction tools which may alert defenders.
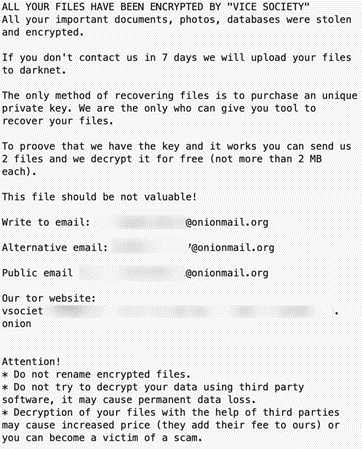
To evade detection, Vice Society attempts to clear security log contents on compromised systems. They will also try to remotely modify the Windows Registry on remote systems to disable remote administration restrictions. This action allows the threat actors to leverage “pass-the-hash” attacks and hinder RDP’s security systems. Vice Society has also attempted to use AMSI bypass to evade detection by endpoint security solutions.
Image 4: Vice Society Ransomware Note
Source: Tripwire
ransomware and education
Unfortunately, cyber attacks are common at the start of every school year. Threat actors have made it a habit to target schools during the first few weeks of classes because they know that teachers and administrators are overwhelmed with the hustle of a new year, emails, and other online tasks. However, there is a bigger picture here – LAUSD is not a small school district that lacks resources, yet they were still breached. The district has more than 600,000 students from more than 1,000 schools within the district.
Not every school district in America has the resources to defend themselves against a ransomware attack. In July 2022, Cedar Rapids Community School District in Iowa actually paid the demanded ransom to a threat actor so they could regain access to their systems. The school’s superintendent stated the following:
“As part of the process to resolve this matter, CRCSD made payment to a third-party entity to ensure critical information that may have been accessed was not released," Superintendent Noreen Bush wrote Friday in a letter to parents. "We made this decision after consulting closely with cybersecurity experts and legal counsel and determining it was in the best interest of our school community.” Superintendent Noreen Bush – Govtech.com
As a result of the attack, the district experienced disruption to their computer systems and had to shut down some of their operations for a few days just as the school year was starting on August 3, 2022. The district had to work with their internal IT staff, as well as third-party vendors to make sure something similar did not happen in the future. The ransom amount was not disclosed nor was the name of the ransomware gang, but the breach impacted over 750 students.
Personal information such as names, addresses, social security numbers, and driver’s license numbers were exposed from the breach. The district stated that they would offer a free year’s worth of credit monitoring services to help protect the impacted individuals. This is a good example of threat actors attacking districts at a time when they know they will be vulnerable. Attackers need this kind of personal data because they know how valuable it is if they attempt to sell it on the dark web. It is also valuable to the threat actors themselves.
According to Comparitech, it is estimated that ransomware attacks cost K-12 schools and colleges $3.56 billion in 2021 in the U.S. Also, there are additional costs associated with recovering data and improving cyber security for the future. Sometimes, it can be nearly impossible to recover massive amounts of stolen data and a lot of schools can’t afford the extra expense. This is why it’s important for school districts to get ahead of the curve and protect themselves now before they have to try to recover from a devastating ransomware attack. Take a look at some of the things your district can do to help keep your cyber environment safe:
- MFA – Implementing MFA (multi-factor authentication) adds another layer to your security process. Most data breaches in the education sector happen as a result of unauthorized access to student data and school operations. This is generally caused by human error within the educational institution via staff or students. By implementing an MFA prompt, educational institutions can block automated attacks and mitigate the risk associated with static passwords.
- Backup Data – Backing up your school’s data may seem simple, but it is often a step that is overlooked. With ransomware attacks on the rise, educational institutions need to make sure that even if they are breached, they have the proper backups in place to replace any stolen data. Also, testing those backups regularly will keep the school aware of any issues that may arise with backup recovery.
- Educate Students and Employees – Educating students and employees on cyber security best practices is essential to keeping cyber environments safe. While online learning is a valuable way to teach, it has also come with an increase in cyber attacks. Teaching students about social engineering, data theft, mobile malware, and phishing attacks can help prevent them from becoming victims. Providing training for school staff on the above topics can also keep them from becoming victims and infecting a school’s network and systems with malware.
- Auditing/Inventory – Knowing how many devices you have connected to your network, who is using them, and when they stop using those devices is an important cyber security best practice. If you don’t know what you have, how can you protect it? Being able to track and audit student/staff devices (tablets, laptops, mobile phones, desktops, etc.) can help keep threat actors from using them as access points.
How Avertium is Protecting Our CUSTOMERS
Threat actors like Vice Society will not stop until they have achieved their financial goal. It is crucial for educational institutions to have tools in place to keep attackers out of the cyber environments and to help mitigate cyber attacks should they be breached. Avertium can help by providing the following services:
- Expanding endpoints, cloud computing environments, and accelerated digital transformation have decimated the perimeter in an ever-expanding attack surface. Avertium offers Attack Surface Management, so you’ll have no more blind spots, weak links, or fire drills.
- Avertium recommends utilizing our service for DFIR (Digital Forensics and Incident Response) to help you rapidly assess, contain, eradicate, and recover from a security incident like a malware attack.
- Fusion MXDR is the first MDR offering that fuses together all aspects of security operations into a living, breathing, threat-resistant XDR solution. By fusing insights from threat intelligence, security assessments, and vulnerability management into our MDR approach, Fusion MXDR offers a more informed, robust, and cost-effective approach to cybersecurity – one that is great than the sum of its parts.
- Avertium offers VMaaS to provide a deeper understanding and control over organizational information security risks. If your enterprise is facing challenges with the scope, resources, or skills required to implement a vulnerability management program with your team, outsourced solutions can help you bridge the gap.
- Avertium offers user awareness training through KnowBe4. The service also includes Incident Response Table-Top exercises (IR TTX) and Core Security Document development, as well as a comprehensive new-school approach that integrates baseline testing using mock attacks.
- Avertium offers Zero Trust Network as a Service (ZTNaaS) for any organization that wants to control their attack surface. The zero-trust security model delivers exactly what the name promises: it is an IT security concept that specifies no access is allowed until the successful completion of authentication and authorization processes.
Avertium’s Recommendations
Avertium, CISA, and the FBI recommend the following for protection against Vice Society:
- Preparing for Cyber Incidents
- Maintain offline backups of data, and regularly maintain backup and restoration. By instituting this practice, the organization ensures they will not be severely interrupted, and/or only have irretrievable data.
- Ensure all backup data is encrypted, immutable (i.e., cannot be altered or deleted), and covers the entire organization’s data infrastructure. Ensure your backup data is not already infected.
- Review the security posture of third-party vendors and those interconnected with your organization. Ensure all connections between third-party vendors and outside software or hardware are monitored and reviewed for suspicious activity.
- Implement listing policies for applications and remote access that only allow systems to execute known and permitted programs under an established security policy.
- Document and monitor external remote connections. Organizations should document approved solutions for remote management and maintenance, and immediately investigate if an unapproved solution is installed on a workstation.
- Implement a recovery plan to maintain and retain multiple copies of sensitive or proprietary data and servers in a physically separate, segmented, and secure location (i.e., hard drive, storage device, the cloud).
- Maintain offline backups of data, and regularly maintain backup and restoration. By instituting this practice, the organization ensures they will not be severely interrupted, and/or only have irretrievable data.
- Identity and Access Management
- Require all accounts with password logins (e.g., service account, admin accounts, and domain admin accounts) to comply with National Institute of Standards and Technology (NIST) standards for developing and managing password policies.
- Use longer passwords consisting of at least 8 characters and no more than 64 characters in length;
- Store passwords in hashed format using industry-recognized password managers;
- Add password user “salts” to shared login credentials;
- Avoid reusing passwords;
- Implement multiple failed login attempt account lockouts;
- Disable password “hints”;
- Refrain from requiring password changes more frequently than once per year unless a password is known or suspected to be compromised.
Note: NIST guidance suggests favoring longer passwords instead of requiring regular and frequent password resets. Frequent password resets are more likely to result in users developing password “patterns” cyber criminals can easily decipher. - Require administrator credentials to install software.
- Require phishing-resistant multifactor authentication for all services to the extent possible, particularly for webmail, virtual private networks, and accounts that access critical systems.
- Review domain controllers, servers, workstations, and active directories for new and/or unrecognized accounts.
- Audit user accounts with administrative privileges and configure access controls according to the principle of least privilege.
- Implement time-based access for accounts set at the admin level and higher. For example, the Just-in-Time (JIT) access method provisions privileged access when needed and can support enforcement of the principle of least privilege (as well as the Zero Trust model). This is a process where a network-wide policy is set in place to automatically disable admin accounts at the Active Directory level when the account is not in direct need. Individual users may submit their requests through an automated process that grants them access to a specified system for a set timeframe when they need to support the completion of a certain task.
- Require all accounts with password logins (e.g., service account, admin accounts, and domain admin accounts) to comply with National Institute of Standards and Technology (NIST) standards for developing and managing password policies.
- Protective Controls and Architecture
- Segment networks to prevent the spread of ransomware. Network segmentation can help prevent the spread of ransomware by controlling traffic flows between—and access to—various subnetworks and by restricting adversary lateral movement.
- Identify, detect, and investigate abnormal activity and potential traversal of the indicated ransomware with a networking monitoring tool. To aid in detecting the ransomware, implement a tool that logs and reports all network traffic, including lateral movement activity on a network. Endpoint detection and response (EDR) tools are particularly useful for detecting lateral connections as they have insight into common and uncommon network connections for each host.
- Install, regularly update, and enable real time detection for antivirus software on all hosts.
- Secure and closely monitor remote desktop protocol (RDP) use.
- Limit access to resources over internal networks, especially by restricting RDP and using virtual desktop infrastructure. If RDP is deemed operationally necessary, restrict the originating sources and require MFA to mitigate credential theft and reuse. If RDP must be available externally, use a VPN, virtual desktop infrastructure, or other means to authenticate and secure the connection before allowing RDP to connect to internal devices. Monitor remote access/RDP logs, enforce account lockouts after a specified number of attempts to block brute force campaigns, log RDP login attempts, and disable unused remote access/RDP ports.
- Limit access to resources over internal networks, especially by restricting RDP and using virtual desktop infrastructure. If RDP is deemed operationally necessary, restrict the originating sources and require MFA to mitigate credential theft and reuse. If RDP must be available externally, use a VPN, virtual desktop infrastructure, or other means to authenticate and secure the connection before allowing RDP to connect to internal devices. Monitor remote access/RDP logs, enforce account lockouts after a specified number of attempts to block brute force campaigns, log RDP login attempts, and disable unused remote access/RDP ports.
- Segment networks to prevent the spread of ransomware. Network segmentation can help prevent the spread of ransomware by controlling traffic flows between—and access to—various subnetworks and by restricting adversary lateral movement.
- Vulnerability and Configuration Management
- Keep all operating systems, software, and firmware up to date. Timely patching is one of the most efficient and cost-effective steps an organization can take to minimize its exposure to cybersecurity threats. Organizations should prioritize patching of vulnerabilities on CISA’s Known Exploited Vulnerabilities
- Disable unused ports.
- Consider adding an email banner to emails received from outside your organization.
- Disable hyperlinks in received emails.
- Disable command-line and scripting activities and permissions. Privilege escalation and lateral movement often depend on software utilities running from the command line. If threat actors are not able to run these tools, they will have difficulty escalating privileges and/or moving laterally.
- Ensure devices are properly configured and that security features are enabled.
- Disable ports and protocols that are not being used for a business purpose (e.g., RDP Transmission Control Protocol Port 3389).
- Restrict Server Message Block (SMB) Protocol within the network to only access servers that are necessary and remove or disable outdated versions of SMB (i.e., SMB version 1). Threat actors use SMB to propagate malware across organizations.
- Keep all operating systems, software, and firmware up to date. Timely patching is one of the most efficient and cost-effective steps an organization can take to minimize its exposure to cybersecurity threats. Organizations should prioritize patching of vulnerabilities on CISA’s Known Exploited Vulnerabilities
MITRE Map
Indicators of Compromise (IoCs)
- v-society[.]official@onionmail[.]org
- ViceSociety[@]onionmail[.]org
- OnionMail email accounts in the format of [First Name][Last Name]@onionmail[.]org
- hxxp://vsociethok6sbprvevl4dlwbqrzyhxcxaqpvcqt5belwvsuxaxsutyad[.]onion
- 5[.]255[.]99[.]59
- 5[.]161[.]136[.]176
- 198[.]252[.]98[.]184
- 194[.]34[.]246[.]90
- fb91e471cfa246beb9618e1689f1ae1d
- a0ee0761602470e24bcea5f403e8d1e8bfa29832
- 3122ea585623531df2e860e7d0df0f25cce39b21
- 41dc0ba220f30c70aea019de214eccd650bc6f37
- c9c2b6a5b930392b98f132f5395d54947391cb79
- 6f191f598589b7708b1890d56b374b45c6eb41610d34f976f0b4cfde8d5731af
Supporting Documentation
Cybersecurity in Education: What Teachers, Parents and Students Should Know | Berkeley Boot Camps
FBI warns of Vice Society ransomware attacks on school districts (bleepingcomputer.com)
sophos-state-of-ransomware-education-2022-wp.pdf (enterpriseav.com)
Second largest U.S. school district LAUSD hit by ransomware (bleepingcomputer.com)
Vice Society claims LAUSD ransomware attack, theft of 500GB of data (bleepingcomputer.com)
Ransomware attack leaves L.A. schools racing to recover (axios.com)
Flash Notice – The PrintNightmare Continues (avertium.com)
Cedar Rapids School District Pays Ransom for Cyber Attack (govtech.com)
Ransomware gang Vice Society leaks stolen L.A. students' data (axios.com)
Ransomware gang leaks data stolen from LAUSD school system (bleepingcomputer.com)
Huge Los Angeles Unified School district hit by cyberattack | AP News
#StopRansomware: Vice Society | CISA
Why is an Asset Inventory Important for Security? » Triaxiom Security
Multi-factor Authentication Deployment in Higher Education (bio-key.com)
Warning issued about Vice Society ransomware targeting the education sector (malwarebytes.com)
Warning issued about Vice Society ransomware gang (tripwire.com)
Vice Society Ransomware Actors Target PrintNightmare | Decipher (duo.com)
CISA, FBI Warn of Vice Society Ransomware Attacks on Schools | Decipher (duo.com)
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.