- WHY AVERTIUM?
-
-
Why Avertium?
Context over chaos. Disconnected technologies, siloed data, and reactive processes can only get you so far. Protecting businesses in today’s threat landscape demands more than a set of security tools – it requires context.
That's where Avertium comes in
-
Considering Microsoft?
Avertium Named Microsoft Security Solutions PartnerAvertium’s managed services for Microsoft Security Solutions is delivered through the company’s premium service: Fusion MXDR. Fusion MXDR includes 24x7 monitoring and management of Defender for Endpoint and Sentinel, threat intelligence, attack surface
monitoring, and vulnerability management for Microsoft Security customers. -
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- SOLUTIONS
-
-
Governance, Risk, + Compliance
GRC with context – not complexity. -
Attack Surface Management
No more blind spots, weak links, or fire drills. -
Threat Detection + Response
Detect, adapt, and attack with context. -
Microsoft Security Solutions
End-to-end support from strategy to daily operations to maximize your Microsoft Security.
-
-
- COMPANY
-
-
About Us
Security. It’s in our DNA. It’s elemental, foundational. Something that an always-on, everything’s-IoT-connected world depends on.
Helping mid-to-enterprise organizations protect assets and manage risk is our only business. Our mission is to make our customers’ world a safer place so that they may thrive in an always-on, connected world.
-
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- PARTNERS
-
-
Our Partners
Best-in-class technology from our partners... backed by service excellence from Avertium.
-
Partner Opportunity Registration
Interested in becoming a partner?
With Avertium's deal registration, partners can efficiently and confidently connect with Avertium on opportunities to protect your deals.
-
Latest Avertium Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- NEWS & RESOURCES
-
-
News & Resources
Dive into our resource hub and explore top
cybersecurity topics along with what we do
and what we can do for you. -
Latest Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- CONTACT
The Basics of Cybersecurity Maturity
Recently, Avertium released our 2023 Cybersecurity Landscape eBook, where we discuss threats that we see bubbling up this year. We also talk about how organizations can prepare based on your current levels of maturity within your security programs.
When we say ‘maturity’ what does that mean? How can you determine your level of cyber maturity and use that to help drive positive business impact? Let’s discuss that today and get you comfortable with the idea.
We are using ‘maturity’ in the context of cybersecurity and risk management only here. In simplest terms, you are going from doing nothing to doing nearly everything. Everything relevant to your security program at least. Understand that you can have all possible security controls in place and still not reach ‘top level maturity.’ Simply having the right technology in place is not enough. You must do all the right things to get the most from that tech with people, processes, documentation, and optimization. There are multiple frameworks that can be used to build maturity (such as NIST-CSF or ISO27001). For now, let’s focus on how to use maturity scoring to drive improved security.
Basic STEPS of Cybersecurity Maturity
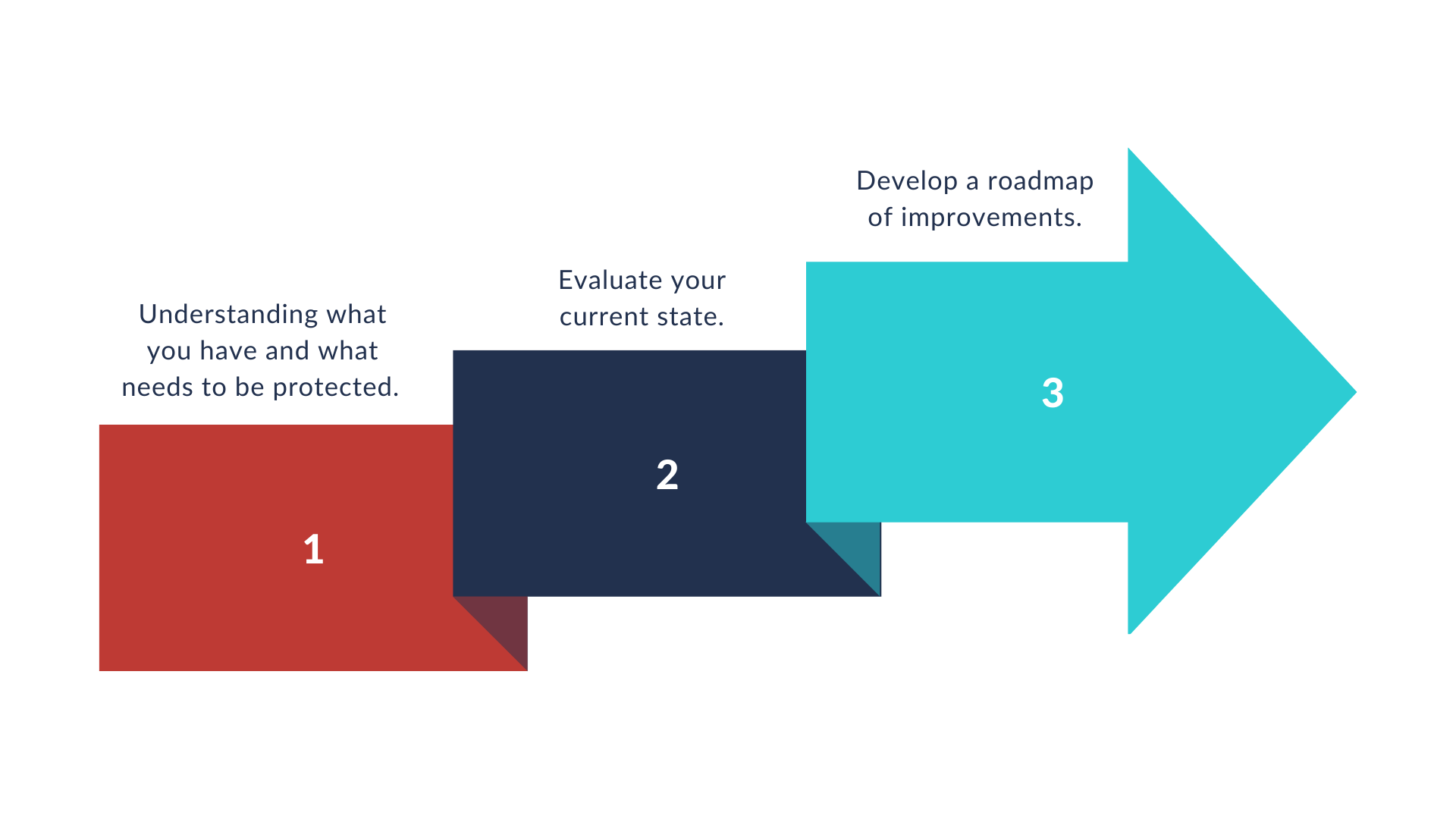 Step 1) Understanding what you have and what needs to be protected.
Step 1) Understanding what you have and what needs to be protected.
Start by defining critical systems and processes for your business. These can be the systems (and data) that run your business, use regulated data, or any number of areas requiring protection.
Once you know what needs to be protected and the value it holds, you can then start to define ‘how mature’ your protection needs to be around them.
Also, understand that maturity is not a blanket score. You are going to look at different aspects of your security program and invest in maturing the areas that make the most impact. Some areas of your business will have low risk and they may not need to be a ‘5’ (on a 1-5 scale). This is a critical aspect to ensure you get the most from your budget and focus on what matters. You need to take into consideration your company’s appetite for risk as well as actual threats facing organizations like yours.
Step 2) Evaluate your current state.
Assess the domains of your security program. In some areas, you may have a good process but no documentation. In other areas, you may have zero protection or have highly optimized processes, technology, and documentation.
There are multiple frameworks you can use as a guide, but all roads lead to your level of risk tolerance:
-
Rolling the dice with maximum exposure
-
Getting by with some level of security technology, but it is not well-optimized or managed
-
Sound tech investment, managed processes, documentation, and optimized domain
With that said, even organizations committed to cybersecurity maturity do not reach some ‘hacker-proof’ state (in the same way that being compliant with a regulation does not guarantee protection). This is about establishing an understanding of maturity scoring and how that can help you improve the right areas of your security based on your risk assessment.
Step 3) Develop a roadmap of improvements.
Based on an assessment of your current state, you can develop a roadmap of improvements. Start by asking yourself, “Where is the most risk? And where does the business benefit most from the investment?”
You want to optimize your cost-to-risk ratio as well as be sure you attack what is critically necessary. This comes from understanding what needs to be protected and to what degree. If your front door has no locks, you do not need to place laser beams in the air ducts (at least not yet). Now, one day you may need sharks with laser beams so you can now build a plan on how to get there.
Define what domains you want to push up, and what those ambitions look like. In some areas, a 2 or 3 may be ‘good’ for your business. Remember this is not about everything needing to be a ‘5.’ It is about maturing the right areas for your business. This maturity planning will aid in your budgeting and long-term planning.
Every division or team has projects they want to get done, but what pushes the needle in the right direction?
-
Your risk appetite and regulatory requirements will give you a clear picture of where to invest
-
Your security maturity planning will direct when and where projects need to be done
With this, you now can clearly communicate the needs to leadership on the budget, and know why and how it will impact the security of the business. This is more effective than saying, “We need this new tech because we do not like the old stuff…” Instead, you will be saying, “Our application security is severely lacking; we are at a 1 and we should be operating at a 4. By spending $X and implementing LMNOP we’ll be addressing the most critical areas of high risk where the business sees the most return.”
This is something companies of any size can do and get value from. There is not always a need to conduct a deep inspection of everything, though sometimes that can bring added value. Using maturity mapping with a good understanding of risk appetite and requirements can provide clear goals for your security organization. It also helps other areas of the business understand why something is needed. And at the end of the day, this helps communicate to the business how security improvements will help drive the company's mission.
|
|
INSIGHT BOX: About NIST Cybersecurity Framework (CSF) One of the most commonly used frameworks when evaluating security maturity is the NIST Cybersecurity Framework (CSF) and it can be very useful in guiding security assessments. This provides a common language and framework for identifying, managing, and communicating cybersecurity risks. By following the guidelines outlined in the NIST CSF, organizations can better understand their current maturity level, identify areas for improvement, and take steps to strengthen their overall cybersecurity posture. Leveraging a common framework with a cybersecurity maturity plan will also make it easier to govern your compliance around regulations such as: General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA). By creating a maturity plan based on a foundational framework such as NIST CSF, and incorporating your own standards and industry regulations, you will have an invaluable tool for organizations looking to improve their cyber maturity and protect against cyber threats.
|
|
Looking for your next read? Download our Internova Travel Group case study!
ABOUT AVERTIUM
Avertium is a cyber fusion company with a programmatic approach to measurable cyber maturity outcomes. Organizations turn to Avertium for end-to-end cybersecurity solutions that attack the chaos of the cybersecurity landscape with context. By fusing together human expertise and a business-first mindset with the right combination of technology and threat intelligence, Avertium delivers a more comprehensive approach to cybersecurity. That's why over 1,200 mid-market and enterprise-level organizations across 15 industries turn to Avertium when they want to be more efficient, more effective, and more resilient when waging today's cyber war.