- WHY AVERTIUM?
-
-
Why Avertium?
Context over chaos. Disconnected technologies, siloed data, and reactive processes can only get you so far. Protecting businesses in today’s threat landscape demands more than a set of security tools – it requires context.
That's where Avertium comes in
-
Considering Microsoft?
Avertium Named Microsoft Security Solutions PartnerAvertium’s managed services for Microsoft Security Solutions is delivered through the company’s premium service: Fusion MXDR. Fusion MXDR includes 24x7 monitoring and management of Defender for Endpoint and Sentinel, threat intelligence, attack surface
monitoring, and vulnerability management for Microsoft Security customers. -
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- SOLUTIONS
-
-
Governance, Risk, + Compliance
GRC with context – not complexity. -
Attack Surface Management
No more blind spots, weak links, or fire drills. -
Threat Detection + Response
Detect, adapt, and attack with context. -
Microsoft Security Solutions
End-to-end support from strategy to daily operations to maximize your Microsoft Security.
-
-
- COMPANY
-
-
About Us
Security. It’s in our DNA. It’s elemental, foundational. Something that an always-on, everything’s-IoT-connected world depends on.
Helping mid-to-enterprise organizations protect assets and manage risk is our only business. Our mission is to make our customers’ world a safer place so that they may thrive in an always-on, connected world.
-
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- PARTNERS
-
-
Our Partners
Best-in-class technology from our partners... backed by service excellence from Avertium.
-
Partner Opportunity Registration
Interested in becoming a partner?
With Avertium's deal registration, partners can efficiently and confidently connect with Avertium on opportunities to protect your deals.
-
Latest Avertium Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- NEWS & RESOURCES
-
-
News & Resources
Dive into our resource hub and explore top
cybersecurity topics along with what we do
and what we can do for you. -
Latest Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- CONTACT
Ryuk Ransomware's Increased Activity Targets Large Organizations Using Windows OS
This report is an overview of the Ryuk ransomware and contains actionable intelligence for understanding and protecting against the malware threat.
Overview of Ryuk Ransomware
Discovered in 2018, this ransomware continues to attract publicity because of its impact on large organizations. Malware researchers have noted increased activity by the ransomware in recent months. Most recently, Ryuk successfully attacked Universal Health Services, one of the largest healthcare providers in the nation.
Ryuk has been attributed to a few threat actors with its origins traced to North Korea or Russia. The Russia-based threat actor, Wizard Spider, appears to be behind the ransomware attacks and is also credited with activity by the TrickBot malware.
Ryuk Ransomware Tactics, Techniques, and Procedures
Malware researchers believe Ryuk is a derivative of the older Hermes ransomware, as much of the same code is used by Ryuk. However, Ryuk has continued to develop beyond Hermes since its discovery. At this time only Windows OS devices appear to be targeted.
Similar to other malware, an infection by Ryuk often begins with a phishing campaign. The campaign may then be used to directly infect victims with the ransomware or may initially infect with Emotet or TrickBot.
The threat actor may later decide to push out the Ryuk ransomware executable payload to encrypt the system. PowerShell scripts are commonly used for the download, leveraging tools like PowerShell Empire and PsExec. Avertium partner Sophos offers this graphic to depict an example chain of infection.
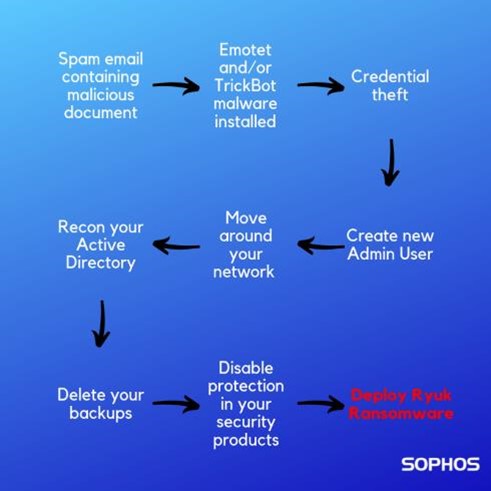
Ryuk is distributed with a dropper for the actual executable payload. The dropper is not often seen, as it is deleted from the system once the payload runs. The dropper randomly generates the payload file name upon installation.
Before encryption, the malware checks the system to determine whether VirtualBox is being used or whether the language is Russian, Ukrainian, or Belarusian, and will not execute on these systems. Ryuk enumerates the network and all drives on the host to encrypt all mounted drives on the system and any hosts it can reach remotely. Ryuk uses RSA-2048 and AES-256 to encrypt the files. Once encrypted, a ransom note is placed on the system requesting Bitcoin payment for the decryption of files.
The below example is provided by CrowdStrike:
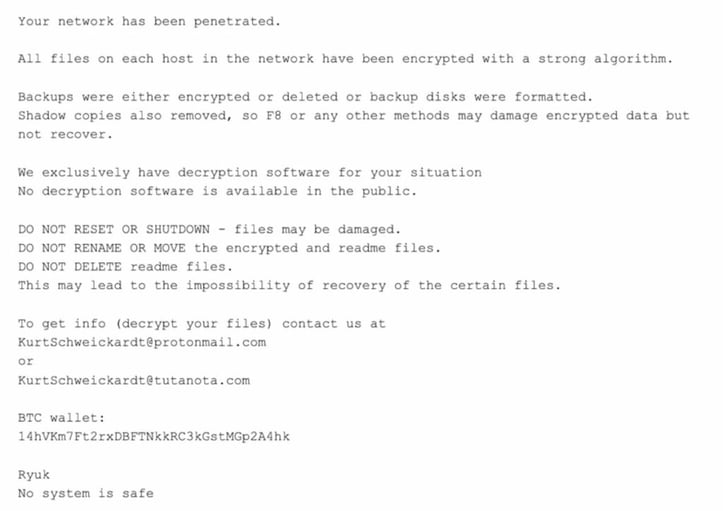
What Ryuk Infection Means to You
-
The infection leads to data encryption or loss.
-
Sensitive business data may be leaked to the public.
-
Payments have been requested by Wizard Spider of up to 99 BTC, approximately $1,047,429.
-
The true cost of ransomware infections can be in far excess of the demand due to a variety of factors like system downtime.
What You Can Do About Ryuk
-
Provide users with training on best practices to avoid phishing, as well as awareness of recent trends in phishing campaigns.
-
Regularly update Windows hosts with recently released patches.
-
Update older versions of Windows to Windows 10 for increased security features.
-
Implement a regular backup schedule for systems, especially those with critical data.
-
Use Endpoint Protection with anti-ransomware features such as Sophos Intercept X.
-
Implement best practices and security features for PowerShell on your network.
-
Run PowerShell 5.0 or greater on systems requiring PowerShell.
-
Implement the privilege of least principle, only allowing PowerShell, and related tools like PsExec, to be run by users and hosts requiring it.
-
Enable script block logging and transcription to better log PowerShell activity.
-

8 Steps to Take if You've Been Breached
With the prevalence, severity, and sophistication of cybersecurity attacks growing by the day, businesses of all types and sizes are scrambling to protect themselves. This best practices guide takes you through the 8 essential steps to managing a data breach. Download now.
Indicators of Compromise (IOCs)
-
The below commands/processes have been associated with Ryuk infections and may also be used by another ransomware.
-
"vssadmin.exe Delete Shadows /all /quiet"
-
"bcdedit /set {default} recoveryenabled No & bcdedit /set {default}"
-
"WMIC.exe shadowcopy delete"
-
-
File hashes:
-
-
cfe1678a7f2b949966d9a020faafb46662584f8a6ac4b72583a21fa858f2a2e8
-
e8a0e80dfc520bf7e76c33a90ed6d286e8729e9defe6bb7da2f38bc2db33f399
-
-
Source: https://www.crowdstrike.com/blog/big-game-hunting-with-ryuk-another-lucrative-targeted-ransomware/
-
795db7bdad1befdd3ad942be79715f6b0c5083d859901b81657b590c9628790f
-
501e925e5de6c824b5eeccb3ccc5111cf6e312258c0877634935df06b9d0f8b9
-
fe909d18cf0fde089594689f9a69fbc6d57b69291a09f3b9df1e9b1fb724222b
-
-
-
AlienVault OTX Pulses:
MITRE Mapping(s)
Sources and Other Helpful Information
-
https://www.crowdstrike.com/blog/big-game-hunting-with-ryuk-another-lucrative-targeted-ransomware/
-
https://research.checkpoint.com/2018/ryuk-ransomware-targeted-campaign-break/
-
https://news.sophos.com/en-us/2019/10/04/rolling-back-ryuk-ransomware/
Supporting Links:
Contact us for more information about Avertium’s managed security service capabilities.
Note: The Avertium Threat Report analyzes one current threat that has been shared by threat intelligence networks across the globe. Used internally by the Avertium CyberOps Team, this report will outline a “top-of-mind” threat and how it ought to be addressed accordingly.
This informed analysis is based on the latest data available.