
Case Study:
INTERNOVA TRAVEL GROUP
Discover how Avertium helps unburden Internova Travel Group's security team to have the space to start focusing on more strategic cybersecurity priorities.
Context over chaos. Disconnected technologies, siloed data, and reactive processes can only get you so far. Protecting businesses in today’s threat landscape demands more than a set of security tools – it requires context.
That's where Avertium comes in
Security. It’s in our DNA. It’s elemental, foundational. Something that an always-on, everything’s-IoT-connected world depends on.
Helping mid-to-enterprise organizations protect assets and manage risk is our only business. Our mission is to make our customers’ world a safer place so that they may thrive in an always-on, connected world.
Best-in-class technology from our partners... backed by service excellence from Avertium.
Interested in becoming a partner?
With Avertium's deal registration, partners can efficiently and confidently connect with Avertium on opportunities to protect your deals.
Microsoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
Dive into our resource hub and explore top
cybersecurity topics along with what we do
and what we can do for you.
Towards the end of May 2023, cybersecurity authorities in the U.S. and internationally raised concerns about a recently identified cluster of activity associated with a state-sponsored threat actor known as Volt Typhoon, originating from the People's Republic of China (PRC). This activity has impacted critical infrastructure networks across the U.S.
Volt Typhoon uses compromised small office and home (SOHO) devices and living off the land techniques, ensuring their activity goes unnoticed. By manually interacting with compromised devices and leveraging built-in network administration tools, the group successfully disguises their activities as normal Windows system and network operations, evading detection. The primary motive behind Volt Typhoon's actions is espionage, making it crucial for organizations to remain vigilant given the current geopolitical climate.
Let's examine the tactics and techniques employed by Volt Typhoon, as well as explore measures organizations can take to protect themselves against this specific threat actor.
As previously stated, towards the end of May 2023, a joint cybersecurity advisory was published by the U.S. Cybersecurity and Infrastructure Security Agency (CISA) and other international cybersecurity authorities regarding a cluster of activity associated with the PRC. The activity was attributed to the state-sponsored threat actor Volt Typhoon, who has been active since mid-2021.
Microsoft was one of the first to report on the threat actor, who observed their targeting of critical infrastructure organizations throughout the United States, including Guam - an island that hosts several military bases. The threat actor's targets and compromised entities encompass various critical sectors, such as government, maritime, communications, manufacturing, information technology, utilities, transportation, construction, and education.
According to Microsoft, based on observed behavior, it appears that the Volt Typhoon’s intention is to conduct espionage and maintain undetected access for as long as possible. The threat actor also prioritizes stealth, relying heavily on living-off-the-land techniques and hands-on-keyboard activity. Commands are issued via command line to:
Volt Typhoon also hides their activities by routing traffic through compromised small office and home office (SOHO) network equipment like routers, firewalls, and VPN hardware. They have also been observed utilizing customized versions of open-source tools to establish a command and control (C2) communication channel via proxy, further enhancing their ability to evade endpoint detection and response products that would usually alert detection engineers. The threat actor leverages various built-in tools such as wmic, ntdsutil, netsh, and PowerShell, as well as open-source tools such as Fast Reverse Proxy, the Mimikatz credential0stealing tool, and the Impacket networking framework.
Microsoft’s initial report stated that Volt Typhoon gains initial access into targeted organizations by exploiting internet-facing Fortinet FortiGuard devices. The threat actor’s goal is to utilize any privileges available through the compromised Fortinet device. They extract credentials associated with an Active Directory account used by the device before attempting to authenticate themselves on other network devices using those obtained credentials.
Utilizing the acquired privileged access from compromising the Fortinet devices, the state-sponsored threat actors can extract credentials through the Local Security Authority Subsystem Service (LSASS). With the stolen credentials, they deploy Awen-based web shells to facilitate data exfiltration and maintain persistence on the compromised systems. Initial access is also achieved by exploiting public-facing applications such as Earthworm and PortProxy.
To gather information about local drives, Volt Typhoon uses the following command:
cmd.exe /C "wmic path win32_logicaldisk get
caption,filesystem,freespace,size,volumename"
The command can return results without administrative credentials. It utilizes a command prompt to execute a Windows Management Instrumentation Command Line (WMIC) query, gathering details about the storage devices on the local host. This includes information such as drive letter, file system (e.g., NTFS), free space, drive size in bytes, and an optional volume name.
CISA’s advisory stated that Volt Typhoon may attempt to exfiltrate the ntds.dit file and the SYSTEM registry hive from Windows domain controllers (DCs) within the network for the purpose of password cracking. The ntds.dit file, located by default at %SystemRoot%\NTDS\ntds.dit, serves as the primary Active Directory (AD) database file. It holds crucial data such as user information, group details, group memberships, and password hashes for all domain users.
If Volt Typhoon manages to exfiltrate the ntds.dit and SYSTEM registry hive, an organization should consider the entire domain compromised. This is because the threat actor will likely be able to crack the password hashes for domain user accounts, create unauthorized accounts, and potentially connect unauthorized systems to the domain.
Volt Typhoon also uses the following tools to obtain information:
To enable port forwarding, Volt Typhoon uses the following commands:
"cmd.exe /c "netsh interface portproxy add v4tov4
listenaddress=0.0.0.0 listenport=9999
connectaddress=<rfc1918 internal ip address>
connectport=8443 protocol=tcp""
-----------------------------------------------------------------------
"cmd.exe /c netsh interface portproxy add v4tov4
listenport=50100 listenaddress=0.0.0.0 connectport=1433
connectaddress=<rfc1918 internal ip address>"
To identify successful logons to the host, Volt Typhoon uses the following PowerShell command:
Get-EventLog security -instanceid 4624
The command helps determine the user account currently being used to gain access to the network, identify other logged-on users on the host, or identify how their activities are being logged. Unfortunately, Volt Typhoon has other commands to identify additional opportunities for obtaining credentials in an environment. See the following commands below:
dir C:\Users\{REDACTED}\.ssh\known_hosts
dir
C:\users\{REDACTED}\appdata\roaming\Mozilla\firefox\profile
s
mimikatz.exe
reg query hklm\software\OpenSSH
reg query hklm\software\OpenSSH\Agent
reg query hklm\software\realvnc
reg query hklm\software\realvnc\vncserver
reg query hklm\software\realvnc\Allusers
reg query hklm\software\realvnc\Allusers\vncserver
reg query hkcu\software\{REDACTED}\putty\session
reg save hklm\sam ss.dat
reg save hklm\system sy.dat
Along with operating system and domain credentials, Volt Typhoon extracts information from local web browser applications. Microsoft detected the threat actors staging the collected data in password-protected archives.
As Volt Typhoon continues their attacks, news is slowly surfacing of exactly which U.S. critical infrastructure entities were breached. One of those entities is the U.S. Navy. The U.S Navy Secretary Carlos Del Toro stated that the recent cyber attacks from Volt Typhoon have in fact impacted the U.S. Navy. While Del Toro did not provide further detail, he did state that he was not surprised that China was “behaving in this manner, not just for the last couple of years, but for decades.”
The recent breach of U.S. critical infrastructure is believed to be a strategic move aimed at granting China access in case of a future conflict with the U.S. While threat actors target critical infrastructure for various reasons, their consistent focus suggests preparations for a potential cyber attack.
Detecting and mitigating an attack from the Volt Typhoon can pose challenges due to its reliance on legitimate accounts and the use of living-off-the-land binaries (LOLBins). It is crucial to address the issue by either closing or changing compromised accounts.
To prevent the misuse of SOHO devices, it is important for owners to ensure that network management interfaces are not accessible from the Internet. In cases where such exposure is necessary, device owners and operators should adhere to zero trust principles and implement robust authentication and access controls to maintain a high level of security. Also, because Volt Typhoon exploits ntds.dit, it’s important to implement best practices such as strengthening the security of Domain Controllers and regularly monitoring event logs for activities involving ntdsutil.exe and similar processes.
Furthermore, it is important to carefully audit and verify any usage of administrator privileges to ensure the authenticity and legitimacy of executed commands. By following these practices, organizations can bolster the protection of ntds.dit and mitigate potential risks and unauthorized access. Please see Avertium’s Recommendations section for mitigation and logging recommendations.
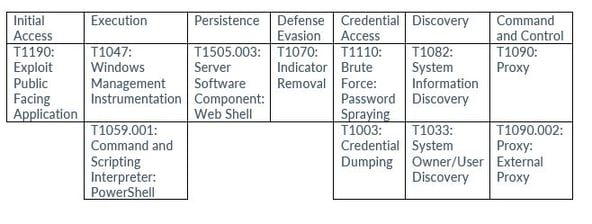
Avertium’s Capability Management Team has found several detections for activity related to Volt Typhoon:
Please Note: These detections could have a high volume of false positives and are not a replacement for a proper security policy. Unused but enabled services like WMIC can increase risk.
|
New Port Forwarding Rule Added Via Netsh.EXX |
Detects the execution of netsh commands that configure a new port forwarding rule |
|
Shadow Copies Creation Using Operating Systems Utilities |
Detects Shadow Copies creation using operating systems utilities. |
|
PortProxy Registry Key |
Detects the modification of PortProxy registry key which is used for port forwarding. |
|
Process Memory Dump Via Comsvcs.DLL |
Detects a process memory dump via "comsvcs.dll" using rundll32. |
|
Activity Related to NTDS.dit Domain Hash Retrieval |
Detects suspicious commands that uses NTDS.dit file remotely |
|
Suspicious Process Patterns NTDS.DIT Exfil |
Detects suspicious process patterns used in NTDS.DIT exfiltration. |
|
Invocation of Active Directory Diagnostic Tool (ntdsutil.exe) |
Detects execution of ntdsutil.exe. |
|
Ntdsutil obtaining SeBackupPrivilege |
Matches on the ntdsutil.exe system utility obtaining SeBackupPrivilege privileges, bypassing ACL. |
|
Explorer mounting a ntdsutil snapshot |
Detects possible attempt to dump AD credentials from the NTDS database. |
|
Vssadmin utility used to create snapshot (Sysmon) |
Detects execution of the snapshot creation command. |
|
Vssadmin utility used to create snapshot (Windows auditing) |
Detects execution of the snapshot creation command. |
|
Suspicious Usage of Ntdsutil |
Detects use of Ntdsutil.exe. |
Avertium also has the following services to help your organization remain safe:
CISA and the FBI have found the following IoCs for Volt Typhoon:
Related Resource:
CSA_Living_off_the_Land.PDF (defense.gov)
Joint_CSA_Top_CVEs_Exploited_by_PRC_cyber_actors.PDF (defense.gov)
Chinese hackers breach US critical infrastructure in stealthy attacks (bleepingcomputer.com)
Threat Brief: Attacks on Critical Infrastructure Attributed to Volt Typhoon (paloaltonetworks.com)
Microsoft warns of Volt Typhoon, latest salvo in global cyberwar (techrepublic.com)
Volt Typhoon: The Chinese APT Group Abuse LOLBins for Cyber Espionage (picussecurity.com)
Five Eyes nations warn of attacks by Volt Typhoon Chinese hackers (techmonitor.ai)
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.