
Case Study:
INTERNOVA TRAVEL GROUP
Discover how Avertium helps unburden Internova Travel Group's security team to have the space to start focusing on more strategic cybersecurity priorities.
Context over chaos. Disconnected technologies, siloed data, and reactive processes can only get you so far. Protecting businesses in today’s threat landscape demands more than a set of security tools – it requires context.
That's where Avertium comes in
Security. It’s in our DNA. It’s elemental, foundational. Something that an always-on, everything’s-IoT-connected world depends on.
Helping mid-to-enterprise organizations protect assets and manage risk is our only business. Our mission is to make our customers’ world a safer place so that they may thrive in an always-on, connected world.
Best-in-class technology from our partners... backed by service excellence from Avertium.
Interested in becoming a partner?
With Avertium's deal registration, partners can efficiently and confidently connect with Avertium on opportunities to protect your deals.
Microsoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
Dive into our resource hub and explore top
cybersecurity topics along with what we do
and what we can do for you.
A new ransomware group, known as Money Message, has been observed encrypting network shares and targeting both Windows and Linux operating systems. Money Message targets victims globally, demanding million-dollar ransoms in exchange for the decryption key and to prevent the leakage of stolen data. So far, the group has successfully breached an Asian airline with an annual revenue of $1 billion, the Taiwanese hardware manufacturer Micro-Star International (MSI), and the large pharmacy provider PharMerica.
Although Money Message is a fairly new group, they have made quite a name for themselves within the past two months. Utilizing double extortion techniques, Money Message has one goal in mind – financial gain. Let’s examine Money Message’s tactics and techniques and how organizations can protect themselves from this kind of threat actor.
In April 2023, it was reported that a new threat actor breached the Taiwanese hardware maker Micro-Star International (MSI). The company was added to the Money Message Tor site where the group claimed to have stolen firmware, source code, and frameworks. Although MSI didn’t go into the details of how they were breached, the company reported the security incident to law enforcement and urged users to obtain firmware/BIOS updates from the official MSI website only. They also discouraged the use of files from sources other than the official website.
Based in New Taipei City, MSI generated over $6.6 billion in revenue during 2021 by designing and developing computer hardware, including laptops, desktops, motherboards, and graphics cards. Money Message claimed to have stolen 1.5 TB of data and demanded a ransom of $4 million from MSI.
Image 1: Notice to MSI
Also in April 2023, Money Message breached the systems of the national pharmacy network, PharMerica, and its parent company, BrightSpring Health Services. The pharmacy network serves long-term care, senior living, and behavioral health organizations. As one of the leading pharmacy service providers in the United States, PharMerica operates a vast network of more than 2,500 facilities and over 3,100 pharmacy and healthcare programs.
Following an investigation, PharMerica and BrightSpring, confirmed unauthorized access to sensitive patient information. The data breach was reported to the Maine Attorney General, affecting a total of 5,815,591 individuals. The breach is the largest healthcare data breach reported by a single HIPAA-covered organization in 2023.
PharMerica's notification letters stated that suspicious activity was detected on its computer networks on March 14, 2023. As a result, the company took swift action to isolate the network and initiate an investigation. After collaborating with cybersecurity experts, they determined that an unidentified third party had accessed the computer systems between March 12 and March 13, 2023. On March 21, 2023, PharMerica confirmed that personal information, including birth dates, Social Security numbers, medication information, and addresses, had been compromised. Despite the threat actors having access to this sensitive data, PharMerica reassured that there was no reason to believe that anyone's information had been misused for fraudulent purposes or identity theft.
According to an update from Databreaches.net, Money Message claims to possess 2 million records from PharMerica and BrightSpring Health, including Social Security numbers sourced from 400 databases. The group also stated its intention to publish the information every 48 hours, a claim that Databreaches.net confirms.
Despite Money Message's claims of significantly disrupting PharMerica's operations, the company has not indicated any operational disruptions in its data breach notification letter submitted to Maine or on its official website.
Initially appearing in March 2023, Money Message immediately started attacking companies on a global scale, demanding millions of dollars in ransom. ThreatLabz was the first to ring the alarm about Money Message when they reported their double extortion techniques on Twitter.
At the time, the group had just two victims listed on their data leak site, including an Asian airline with an annual revue of $1 billion. Money Message claimed that they exfiltrated data from the airline and posted a screenshot of the files as confirmation. Now, the group has impacted more than five publicly disclosed victims, most within the United States. The victims belong to several industries, including Transportation and Logistics, Professional Services, and BFSI.
Image 2: Tweet from ThreatLabz
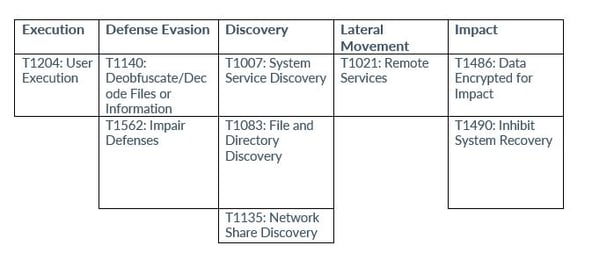
Money Message uses the C++ programming language for their encryptor, incorporating an embedded JSON file that decides the encryption process for a particular device. Within the JSON file, various parameters are set, such as the directories that should be excluded from encryption, the additional file extensions to target, the services and processes to be terminated, logging preferences, as well as the domain login credentials to be employed.
Analysts at Cyble Research and Intelligence Labs (CRIL) analyzed the group’s binaries and found admin credentials in the configuration. The credentials were then used to target network resources. Due to this, the researchers suspected that the threat actors behind the campaign were using stealer logs as part of their operation.
Image 3: Money Message Ransomware Binary
|
dc563953f845fb88c6375b3e9311ebed49ce4bcd613f7044989304c8de384dac) is a 32-bit executable compiled in c/c++ |
CRIL stated that during execution, the ransomware retrieves its configuration settings from the overlay of the ransomware binary. These configuration details are appended to the end of the file at the offset 0XBF000. The configuration includes various parameters, such as a ransom note encoded in Base64 format, along with other settings that dictate the behavior of the ransomware during its execution. The configuration includes the following parameters:
Following that, the ransomware uses the CreateMutexA() method to generate a mutex with the name "12345-12345-12235-12354", obtained from the configuration. Next, the ransomware proceeds to stop the services present in the configuration file. It begins by accessing the Service Control Manager (SCM) by calling the OpenSCManagerW() function.
It then calls the EnumServicesStatusExW() function to retrieve a list of all services and their statuses. If any of the services listed in the configuration file are found to be running, the ransomware uses the CloseServiceHandle() function to stop them.
Next, the ransomware obtains a list of active processes on the victim's machine using the CreateToolhelp32Snapshot() function and iterates through each process using Process32FirstW() and Process32NextW() functions. It compares each process name with the entries in its configuration file and terminates any matching processes using the TerminateProcess() function. The ransomware is specifically programmed to terminate the following processes:
|
sql.exe |
mydesktopservice.exe |
steam.exe |
thebat.exe |
|
oracle.exe |
ocautoupds.exe |
excel.exe |
sqbcoreservice.exe |
|
ocssd.exe |
infopath.exe |
encsvc.exe |
thunderbird.exe |
|
dbsnmp.exe |
msaccess.exe |
firefox.exe |
visio.exe |
|
synctime.exe |
mspub.exe |
tbirdconfig.exe |
winword.exe |
|
agntsvc.exe |
onenote.exe |
mdesktopqos.exe |
wordpad.exe |
|
isqlplussvc.exe |
outlook.exe |
ocomm.exe |
vmms.exe |
|
xfssvccon.exe |
powerpnt.exe |
dbeng50.exe |
vmwp.exe |
Next, the ransomware employs the ShellExecuteW() function to execute the command "vssadmin.exe delete shadows /all /quiet". This command deletes all Volume Shadow Copy Service (VSS) snapshots on the system without requiring confirmation. Following that, the ransomware scans all available drive letters on the system, beginning from A to Z, using the GetDriveTypeW() function to determine the type of drive associated with each letter, including fixed, removable, or network drives.
Finally, Money Message initiates encryption using the Elliptic Curve Diffie-Hellman key exchange and the ChaCha stream cipher algorithm to encrypt data on a victim’s system and demand a ransom. The file money_message.log is created to write the ransom note, which has instructions given by the threat actor.
Image 4: Money Message Ransom Note
Based on Money Message’s targeting, their ultimate goal is financial gain. Although the malware is not sophisticated, the group has attacked billion-dollar companies, demanding millions in ransom. Therefore, it is crucial for organizations to remain vigilant and implement the necessary precautions to avoid falling victim to the ransomware group’s attacks.
Here are some ransomware best practices Avertium recommends to keep your organization safe from threat actors like Money Message:
Remember, relying on outdated tools and point solutions will only compromise the security of your network or system. Organizations should prioritize adopting modern technology that is capable of detecting and defending against complex attacks.
MD5
SHA1
SHA256
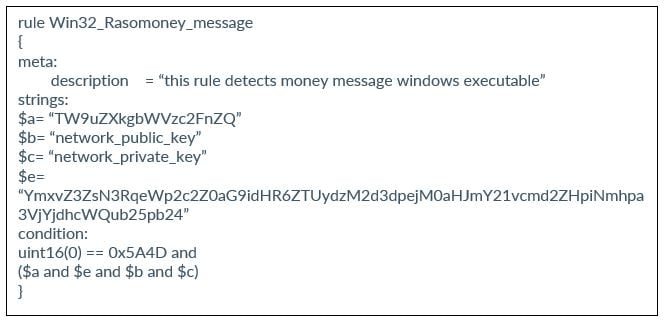
YARA Rule
It’s important to get ahead of the curve by being proactive with protecting your organization, instead of waiting to put out a massive fire. Avertium can provide the following services to help keep your organization safe from ransomware attacks:
Related Resource:
Hardware giant MSI confirms cyberattack after new ransomware group issues demand (therecord.media)
Millions of PharMerica customers hit in ransomware attack | TechRadar
Almost 6 Million Individuals Affected by PharMerica Data Breach (hipaajournal.com)
PharMerica announces health data breach, possibly largest of Q1 2023 | Healthcare IT News
PharMerica and BrightSpring Health Services hit by Money Message (update2) (databreaches.net)
Money Message: The Newest Ransomware Gang that Threatens Organizations (heimdalsecurity.com)
Cyble — Demystifying Money Message Ransomware
New Money Message ransomware demands million dollar ransoms (bleepingcomputer.com)
Money Message ransomware gang claims MSI breach, demands $4 million (bleepingcomputer.com)
Money Message Ransomware Attacks Windows & Linux Users (cybersecuritynews.com)
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.