- WHY AVERTIUM?
-
-
Why Avertium?
Context over chaos. Disconnected technologies, siloed data, and reactive processes can only get you so far. Protecting businesses in today’s threat landscape demands more than a set of security tools – it requires context.
That's where Avertium comes in
-
Considering Microsoft?
Avertium Named Microsoft Security Solutions PartnerAvertium’s managed services for Microsoft Security Solutions is delivered through the company’s premium service: Fusion MXDR. Fusion MXDR includes 24x7 monitoring and management of Defender for Endpoint and Sentinel, threat intelligence, attack surface
monitoring, and vulnerability management for Microsoft Security customers. -
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- SOLUTIONS
-
-
Governance, Risk, + Compliance
GRC with context – not complexity. -
Attack Surface Management
No more blind spots, weak links, or fire drills. -
Threat Detection + Response
Detect, adapt, and attack with context. -
Microsoft Security Solutions
End-to-end support from strategy to daily operations to maximize your Microsoft Security.
-
-
- COMPANY
-
-
About Us
Security. It’s in our DNA. It’s elemental, foundational. Something that an always-on, everything’s-IoT-connected world depends on.
Helping mid-to-enterprise organizations protect assets and manage risk is our only business. Our mission is to make our customers’ world a safer place so that they may thrive in an always-on, connected world.
-
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- PARTNERS
-
-
Our Partners
Best-in-class technology from our partners... backed by service excellence from Avertium.
-
Partner Opportunity Registration
Interested in becoming a partner?
With Avertium's deal registration, partners can efficiently and confidently connect with Avertium on opportunities to protect your deals.
-
Latest Avertium Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- NEWS & RESOURCES
-
-
News & Resources
Dive into our resource hub and explore top
cybersecurity topics along with what we do
and what we can do for you. -
Latest Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- CONTACT
TIR-20210913 TEAMTNT – “CHIMAERA” CRYPTOMINING MALWARE CAMPAIGN TARGETS SERVERS
Cryptomining - how raas gangs are installing malware to cryptojack
If you’re unfamiliar with cryptocurrency mining, then now may be the time to become educated. The cybercriminal world is constantly changing, and cybercriminal gangs are starting to make the shift from RaaS to cryptocurrency mining, with TeamTNT being the latest threat actor.
Cryptocurrency mining is just like mining for gold, diamonds, or other valuable materials. Instead of buying cryptocurrency (Bitcoin, Monero, Bytecoin, etc.), people can set up their computers at home to mine crypto tokens without having any capital. The act of cryptocurrency mining itself isn’t a crime. In fact, there are thousands of people who make a decent living from mining for cryptocurrency, including this 14- and 9-year-old from Dallas, Texas, who earn over $30,000 a month.
When does cryptocurrency mining become a cybercrime? When cyber threat actors like TeamTNT attack vulnerable operating systems and applications by installing cryptocurrency mining malware to cryptojack. The malware is installed so attackers can siphon the currency they stole via cryptojacking and put it into their own digital wallets. They do this by abusing machines that belong to large enterprises.
Not only does TeamTNT infiltrate systems that they don’t have the authority to be in, but they also steal resources. Cryptomining involves pushing a device to its limit and can cause serious damage. The malware that’s installed uses a great amount of power and leaves computers running slow (or not running at all) and electricity bills soaring.
TeamTNT
On September 8, 2021, our partner AT&T Alien Labs announced that the malware campaign, Chimaera, by TeamTNT, was actively targeting several operating systems and applications. The programs and applications currently under attack are Microsoft Windows, some Linux Installations (including Alpine), Docker, AWS, and Kubernetes.
While TeamTNT was first publicly acknowledged in May 2020 by Trend Micro, the Chimaera campaign didn’t make an appearance until July 2021. The new malware campaign is responsible for infecting thousands of systems globally by using new open-source tools to mine cryptocurrency. Last year, TeamTNT was responsible for installing cryptocurrency malware on vulnerable Docker containers.
In October 2020, we reported that TeamTNT was using the monitoring tool, Weave Scope, to gain administrative access to cloud environments. They attacked Docker, Kubernetes, Distributed Operation System (DC/OS), and AWS Elastic Compute Cloud instances. In January 2021, we followed up with another report detailing the additions to TeamTNT’s malware campaign. During that time the gang was still using malware to infect and spread through cloud environments, but they started using AWS IAM (Identity and Access Management) to capture credentials more effectively. This is their pattern – using tool kits to compromise cloud environments. While TeamTNT’s goal has not changed, their tools certainly have evolved.
As one of the most active cybercriminal groups since mid-2020, TeamTNT has developed a sneaky tool kit for malicious activity. The tool kit includes Masscan and port scanner, librocesshider, 7z (decompresses files), b374k shell (controls infected systems), and Lazagne. This tool kit allows TeamTNT to go undetected even with the use of anti-virus and malware detection tools – making it difficult for cyber intelligence engineers and analysts to keep up with their activity.
“As of the publishing of this report, many of the samples analyzed by Alien Labs have zero or low detection on VirusTotal.”
Image 1: TeamTNT’s Infection Statistics
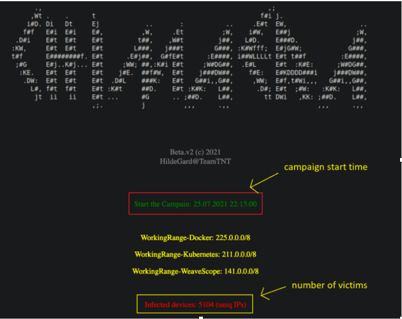
From TeamTNT website, infection statistics – AT&T Alien Labs
In conjunction with this new tool kit, TeamTNT is using Peirates, which is a cloud penetration testing toolset that can target cloud-based apps. TeamTNT’s focus appears to be compromising Kubernetes clusters – an open-source software used for deploying and managing containers at scale. The group’s attacks on Kubernetes include using a root payload component. When TeamTNT attacked Windows systems, they use the Xmrig miner, create a service, and add a batch file to the startup folder to maintain persistence.
By using open-source tools, TeamTNT can gather information in AWS and Google Cloud environments to execute post-exploitation operations. This means that the threat actor can laterally move within a system and perform privilege-escalation attacks that could allow them to obtain administrative access to an organization’s entire cloud environment.
While TeamTNT employs some of the same tactics as similar groups, TeamTNT stands out with its social media presence and the tendency for self-promotion. Most threat actors try to stay hidden, but TeamTNT has a public Twitter account and even interacts with researchers – almost as if they are bragging. Tweets from the account are in both English and German although it is unknown if they are located in Germany.
Image 2: TeamTNT’s Interaction with Researchers on Twitter
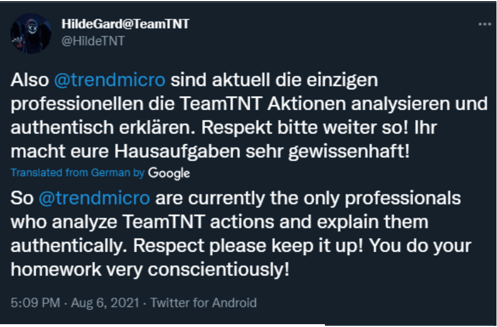
TeamTNT’s recent interaction with Trend Micro on Twitter.
Image 3: TeamTNT’s Statement Regarding Chimaera
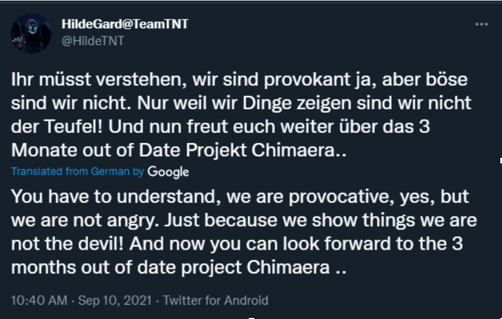
TeamTNT’s public Twitter account
How Cryptomining Malware Can Affect Your Business
Cryptomining malware can disrupt your entire business operation and create a long-lasting impact. Affecting more than 55% of businesses worldwide, cryptomining malware is the No. 2 threat to consumers and businesses, with no signs of slowing down. Servers are the most popular targets for cybercriminals to infect with the malware. TeamTNT also downloads software that continues to run in the background, draining the life of your computer long after attackers have wiped their presence from your system. Here are some of the impacts a cryptomining malware attack could have on your business:- May result in the loss of control over critical cloud assets.
- Could lead to heavy resource usage as various miners execute in the environment
- Could provide privileged access to sensitive data on potentially multiple containers.
- May allow for the compromise of mission-critical cloud assets hosting sensitive data.
How Do I Know If I’m Being Cryptojacked?
If your system is being cryptojacked, there are several indicators. The main indicator will be your computer itself, but there are other indicators that will tip you off:- Reduced performance on your device – your systems seem to be running extremely slow.
- There is a spike in our CPU usage - this could mean that cryptomining scripts are executing.
- Battery draining – your battery life drains quickly.
- An extremely loud fan – if the fan on your computer seems to be in overdrive and is extremely loud, this is a sign that you have extra activity on your device and your computer is running its fan longer than necessary to try and cool down the system.
Don’t underestimate the harmful and negative effects of cryptomining malware. Being proactive against these attacks means that your business environment will remain safe and will not be exploited by cybercriminals looking to make money on your dime.
Indicators of Compromise (IoCs):
- 8373c0e8abdd962f46d3808fb10589e4961e38cd96d68a4464d1811788a4f2b7
- 73a4e43a50c533dffdce6575a630be808780d1b408a6dda335106de0c48926ac
- 24c75a2f86d3c0f13f77b453d476787607a87c1033dca501351846524a4e8ff6
- e842c810b6ecb9c7634f1cfbf81b6245094528ac5584179eb8e6932eaa34f421
- 1e565e0672c4cd60b7db32c0ecc1abace6dfd8b6c2e0623c949d31536940fd62
- 12466d33f1d0e9114b4c20e14d51ca3e7e374b866c57adb6ba5dfef3ee34ee5b
- The.borg[.]wtf(45.9.150.36)
- Teamtnt[.]red(45.9.148.108)
- Irc.borg[.]wtf(123.245.9[.]147)
- Sampwn.anondns[.]net (13.245.9[.]147)
- 45.9.148[.]35/chimaera/bin/
- 45.9.148[.]35/chimaera/data/
- 45.9.148[.]35/chimaera/init/
- 45.9.148[.]35/chimaera/pl/
- 45.9.148[.]35/chimaera/py/
- 45.9.148[.]35/chimaera/sh/
- 45.9.148[.]35/chimaera/spread/
- 45.9.148[.]35/chimaera/up/
- pool.supportxmr[.]com
- Teamtnt[.]red
- Chimaera[.]cc
- 164.68.106.96
- 62.234.121.105
- 4.154.7.3
- 0.122.62.1
- 6.110.215.3
- 0.128.254.1
Avertium’s Recommendations
- Update your software with the latest security updates.
- Monitor traffic on your network. You should also monitor unreasonable bandwidth usage and outbound port scans.
- Minimize exposure to the Internet on your Linux servers and IoT devices.
- Use a well-configured firewall.
- You may want to limit the capabilities of specific IAM roles in the environment to reduce risk.
- Consider monitoring the environment for any odd outbound http requests containing sensitive AWS data.
- Consider monitoring the environment for any odd outbound http requests containing sensitive AWS data.
- Educate your cyber intelligence team and your employees on the dangers of cryptomining malware.
- Use ad-blocking extensions – this can prevent malicious cryptomining code.
- Disable JavaScript – when surfing the web, disabling JavaScript can keep cryptojacking malware from infecting your computer.
How to Prevent and Recover from a Cryptomining Malware Attack
- The best offense is defense. If you want to be proactive with protecting your business, you need to add the listed IoCs to SIEM platforms for detection.
- You also need to implement XDR as a prevention method. Our XDR is a combination of monitoring software like LogRhthm, Microsoft Azure Sentinel, or AlienVault, combined with endpoint protection such as SentinelOne. XDR platforms enable cybersecurity through a technology focus by collecting, correlating, and analyzing event data from any source on the network. This includes end-points, applications, network devices, and user interactions.
- XDR Reimagined - Avertium builds on this multi-dimensional model by combining deep knowledge of these capabilities in best-in-class technologies, our proprietary engagement methodology, our security maturity model, and extraordinary people with decades of certified expertise and broad experience in managed security and professional services.
- Rather than point solutions, Avertium is able to fully integrate SIEM, EDR, Vulnerability Management, Zero-Trust Networking and Architecture & Integration Services, all by our certified experts 24/7. Avertium builds on customer relationships by creating, in collaboration with the customer, a methodical and disciplined forward motion by which to improve an organization’s security posture.
- Avertium recommends utilizing our service for DFIR (Digital Forensics and Incident Response) to help you rapidly assess, contain, eradicate, and recover from a security incident like a cryptomining malware attack. This service is provided as an on-demand crisis response service, as well as retainer-based program.
Don't stop at TeamTNT and their latest campaign. Learn more on Ransomware Trends in 2021 and how to protect your organization from becoming a RaaS gang's next victim.
MITRE TTPs
[T1595] Active Scanning- [T1589] Gather Victim Identity Information
- [T1609] Container Administration Command
- [T1610] Deploy Container
- [T1505] Server Software Component
- [T1555] Credentials from Password Stores
- [T1212] Exploitation for Credential Access
- [T1580] Cloud Infrastructure Discovery
- [T1071] Application Layer Protocol
- [T1496] Resource Hijacking
Terms
AWS (Amazon Web Services) – a cloud computing platform for amazon. The platform provides servers, storage, networking, remote computing, email, mobile development, and security. TeamTNT uses this to break into cloud instances to mine for Monero cryptocurrency.
AWS IAM (Identity and Access Management) – allows you to create and manage AWS users and group – using permissions to allow and deny access to AWS resources.
Cryptojacking – When an attacker maliciously hacks into a computer (mobile device or laptop) and installs malicious software. The software is used to steal cryptocurrency and a code runs in the background (even after attackers have left), hijacking their victims’ resources.
Cryptocurrency Mining – The act of using a machine, typically a computer, to mine for crypto tokens. Pushing the computer to its maximum capacity and that’s why it uses more electricity. It can be bad for computer equipment and damage it if it runs.
Masscan – searches for new candidates to infect.
Libprocesshider – a software that hides a process under Linux using the Id preloader. This helps execute the TeamTNT bot from memory.
Lazagne – an open-source tool for web operating systems (think Chrome, Wi-Fi, and Firefox), used to collect stored credentials (passwords, usernames, etc.) from applications.
Containers – containers are used to help build modern applications. Containers are microservices packed with their dependencies and configurations.
Related Threat Intelligence Report
- TeamTNT Attacks Cloud Environments
- Recent Additions to TeamTNT Malware Campaign on Cloud Environments (TIR-20210124)
Supporting Documentation
https://www.zdnet.com/article/operation-chimaera-teamtnt-hacking-group-strikes-thousands-of-victims-worldwide/
https://malpedia.caad.fkie.fraunhofer.de/actor/teamtnt
https://cybersecurity.att.com/blogs/labs-research/teamtnt-with-new-campaign-aka-chimaera
https://github.com/gianlucaborello/libprocesshider
https://unit42.paloaltonetworks.com/teamtnt-operations-cloud-environments/
https://threatpost.com/teamtnt-target-multiple-os/169279/
https://www.redpacketsecurity.com/thousands-of-organizations-targeted-via-operation-chimaera/
https://azure.microsoft.com/en-us/topic/what-is-kubernetes/?&ef_id=EAIaIQobChMI4K_r89_08gIVXmxvBB2N5AhlEAAYAiAAEgKL3_D_BwE:G:s&OCID=AID2201006_SEM_EAIaIQobChMI4K_r89_08gIVXmxvBB2N5AhlEAAYAiAAEgKL3_D_BwE:G:s&gclid=EAIaIQobChMI4K_r89_08gIVXmxvBB2N5AhlEAAYAiAAEgKL3_D_BwE
https://oal.law/a-guide-to-cryptojacking-detection-prevention-and-protection-against-cryptojacking-attacks/?utm_source=Mondaq&utm_medium=syndication&utm_campaign=LinkedIn-integration
https://www.investopedia.com/articles/investing/011316/what-amazon-web-services-and-why-it-so-successful.asp
https://www.cnbc.com/2021/08/31/kid-siblings-earn-thousands-per-month-mining-crypto-like-bitcoin-eth.html
https://www.intezer.com/resources/research-report/teamtnt-cryptomining/
https://www.eset.com/int/malicious-cryptominers/
https://aws.amazon.com/iam/
APPENDIX II: Disclaimer
This document and its contents do not constitute and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of the Client's compliance with any law, regulation or standard.