- WHY AVERTIUM?
-
-
Why Avertium?
Context over chaos. Disconnected technologies, siloed data, and reactive processes can only get you so far. Protecting businesses in today’s threat landscape demands more than a set of security tools – it requires context.
That's where Avertium comes in
-
Considering Microsoft?
Avertium Named Microsoft Security Solutions PartnerAvertium’s managed services for Microsoft Security Solutions is delivered through the company’s premium service: Fusion MXDR. Fusion MXDR includes 24x7 monitoring and management of Defender for Endpoint and Sentinel, threat intelligence, attack surface
monitoring, and vulnerability management for Microsoft Security customers. -
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- SOLUTIONS
-
-
Governance, Risk, + Compliance
GRC with context – not complexity. -
Attack Surface Management
No more blind spots, weak links, or fire drills. -
Threat Detection + Response
Detect, adapt, and attack with context. -
Microsoft Security Solutions
End-to-end support from strategy to daily operations to maximize your Microsoft Security.
-
-
- COMPANY
-
-
About Us
Security. It’s in our DNA. It’s elemental, foundational. Something that an always-on, everything’s-IoT-connected world depends on.
Helping mid-to-enterprise organizations protect assets and manage risk is our only business. Our mission is to make our customers’ world a safer place so that they may thrive in an always-on, connected world.
-
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- PARTNERS
-
-
Our Partners
Best-in-class technology from our partners... backed by service excellence from Avertium.
-
Partner Opportunity Registration
Interested in becoming a partner?
With Avertium's deal registration, partners can efficiently and confidently connect with Avertium on opportunities to protect your deals.
-
Latest Avertium Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- NEWS & RESOURCES
-
-
News & Resources
Dive into our resource hub and explore top
cybersecurity topics along with what we do
and what we can do for you. -
Latest Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- CONTACT
Netwalker Ransomware offered as Ransomware-as-a-Service creating increased prevalence
NetWalker (fka Mailto) Overview
This threat report is about the NetWalker ransomware previously known as Mailto. Since it was first detected in August 2019, NetWalker has quickly evolved and is now considered highly dangerous due to its implementation of advanced anti-detection and persistence techniques.
This report gives a technical analysis of its recently-observed behavior, as well as preventative measures that can be implemented to protect against NetWalker’s highly effective extortion efforts.
Related Reading: Ragnar Locker Ransomware New Invasion Technique
Netwalker Ransomware Tactics, Techniques, and Procedures
Although variants of NetWalker have been observed since August 2019, there has been a significant increase in prevalence since March 2020.
As the threat has evolved over the past few months, its establishment as a robust ransomware-as-a-service (RaaS) model has been evident. This enables even novice cybercriminals to launch a successful ransomware attack against targets.
NetWalker has been observed primarily infiltrating large-scale corporate networks. Researchers have linked large sums of bitcoin to ransomware, indicating its extortion efforts have likely been effective.
The following shows the global prevalence of these attacks:
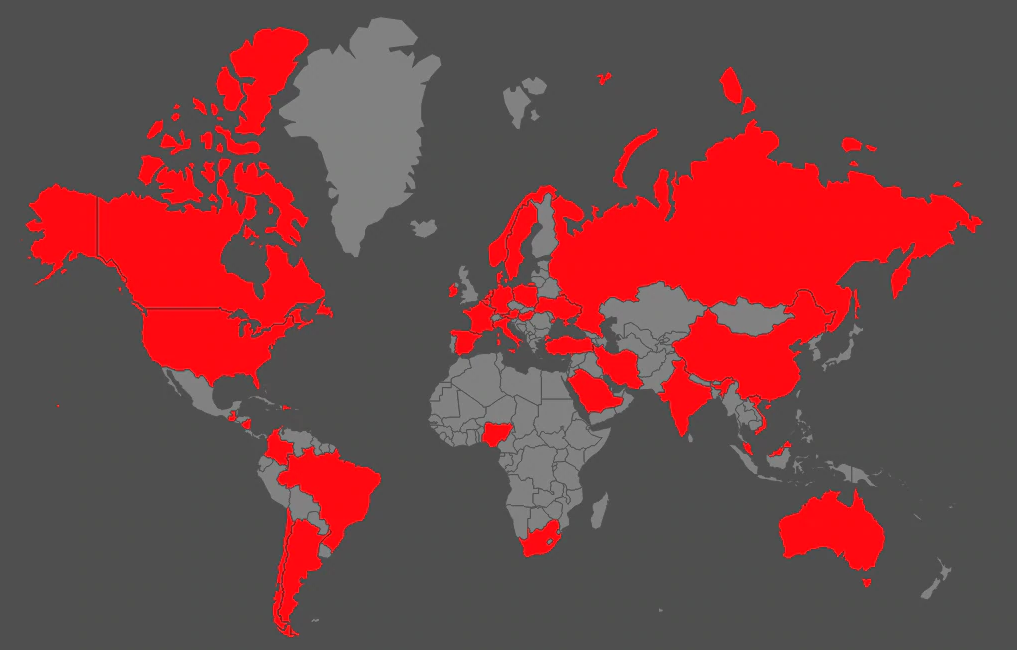
As the evolution of this malware has progressed, researchers have observed the implementation of more sophisticated defense evasion techniques along with other advanced features making these attacks more difficult to investigate by security analysts.
In one recently analyzed case, the payload began with a PowerShell script that was executed directly in memory. No ransomware binary was stored on the disk, this enabled the malware to maintain persistence and evade detection by performing the attack through tools that were already present in the system.
One of the techniques leveraged with this process is referred to as "reflective DLL injection". This allows a DLL injection from memory rather than from a disk. This method does not require an actual DLL file on a disk or a Windows loader for injection, allowing evasion from DLL load monitoring tools.
In this case, the ransomware DLL was injected into the memory of the legitimate process explorer.exe. The diagram below shows a graphical representation of the PowerShell script observed in this variant of NetWalker:
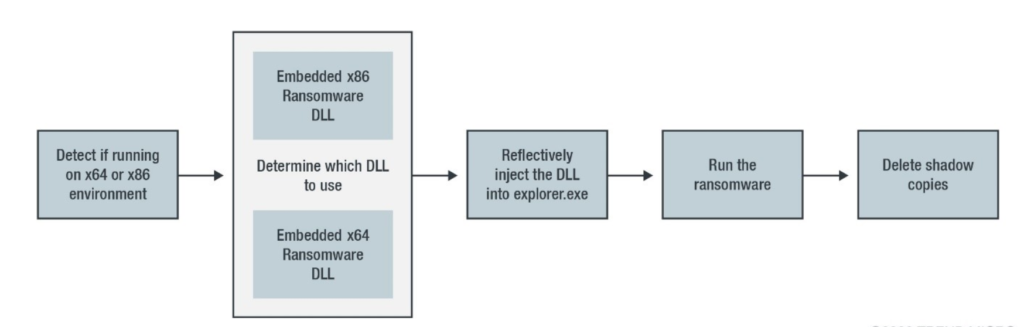
The malware’s first action in the executable process is to combine all required functions into one, combining the Windows modules with additional DLLs.
The malware also uses Process Environment Block (PEB) to inhibit analysis. If the malware fails to obtain its configuration file, it will terminate itself.
After successful completion of all encryption actions, the malware shows a ransom note, displayed in Notepad, informing the user of what has happened and threatening permanent data loss if the ransom is not paid. After all ransom actions have been completed, the malware attempts to remove itself to avoid being detected or analyzed.
Further technical information can be found linked in the Sources section below.
Related Reading: Ransomware Prevention to Incident Response
What Netwalker Vulnerability Means to You
- The infection will lead to encryption or loss of data.
- Critical company data could be leaked to the public.
- Could result in major production downtime costs.
What You Can Do About Netwalker Ransomware
Employing adequate preventative measures greatly minimizes the risk of being infected. One of the most effective methods is having good security policies and practices in place before an incident occurs:
- We highly recommend you block or set up detection for the existing IoCs associated with NetWalker linked in the Sources section below.
- Implement regular vulnerability scanning to identify and address security weaknesses in your environment.
- Consider implementing a security awareness training program for your organization to encourage best security practices when handling email content.
- Make sure you are using the latest version of the OS your systems are running. Each OS is coded for the best security practices of the time. Because these threats are constantly evolving it is important to implement these upgrades as they become available to you.
- Make sure all software on your devices is fully updated. Malicious actors and programs can utilize little-known vulnerabilities in outdated software to gain initial access. Perform regular software audits to identify unused applications and uninstall them as these could also present a risk.
- Recognize the risk with USB drives. If a USB drive has been infected or loaded with malware, it can automatically execute the malicious software on a device by simply being plugged in. Cloud storage services offer many conveniences in relation to file sharing and may be an option if your company would like to limit the use of USB drives.
- Utilize user security permissions on devices appropriately as an additional layer of protection in the case that a host is infected. Security permissions can limit an executable’s privileges when running at a locked-down user level. Accounts with administrative access should only be used when privileged access is necessary. This method of locking down security on individual devices can help quarantine infections from spreading rampantly through a network.
- Consider using the internal software firewalls on systems to block the use of unnecessary ports. In most modern-day network topologies, it is not necessary for individual computers on a network to communicate directly. Enabling this will aid in preventing the spread of infection through discovered open ports.
- Turn off protocols that you do not need on individual PCs. The more information a bad actor or piece of software can obtain about a network, the more likely it is to be able to infect it. Turning off unnecessary sharing will also aid in shielding a PC from being attack by an infected device on that network.
Using Backups to Protect Against Breaches
Although the complications of a ransomware attack can be detrimental, it is only one of many ways critical data can be lost. Because of this, it is imperative that companies have a regular backup routine in place. Data backed up should also be moved to an isolated location off-site for protection in the case that ransomware or any other location-specific event were to occur.
Related Reading: 5 Ways to Prevent Ransomware
Risks of Paying the Ransom
In the unfortunate event that ransomware is active in your environment, keep in mind that paying the ransom does not guarantee you will receive the decryption key to get your data back.
It is also not guaranteed that you will not be infected again shortly after, since the vulnerabilities in your infrastructure that caused the infection, to begin with, are still exposed and susceptible to attack.
Finally, the more victims who pay the ransom, the more profitable it is for cybercriminals, so this response encourages the continuation of these attacks.
Sources and MITRE ATT&CK Techniques
IBM X-Force Exchange (IOC list):
McAfee:
Trend Micro:
MITRE ATT&CK Techniques:
- Exploit Public-Facing Application (T1190): https://attack.mitre.org/techniques/T1190/
- Spearphishing Attachment (T1566.001): https://attack.mitre.org/techniques/T1566/001/
- Valid Accounts (T1078): https://attack.mitre.org/techniques/T1078/
- Command and Scripting Interpreter (T1059): https://attack.mitre.org/techniques/T1059/
- Service Execution (T1569.002): https://attack.mitre.org/techniques/T1569/002/
- Native API (T1106): https://attack.mitre.org/techniques/T1106/
- Windows Management Instrumentation (T1047): https://attack.mitre.org/techniques/T1047/
- Registry Run Keys/Startup Folder (T1547.001): https://attack.mitre.org/techniques/T1547/001/
- Exploitation for Privilege Escalation (T1068): https://attack.mitre.org/techniques/T1068/
- Process Injection: Dynamic-link Library Injection (T1055.001): https://attack.mitre.org/techniques/T1055/001/
- Disable or Modify Tools (T1562.001): https://attack.mitre.org/techniques/T1562/001/
- Deobfuscate/Decode Files or Information (T1140): https://attack.mitre.org/techniques/T1140/
- Obfuscated Files or Information (T1027): https://attack.mitre.org/techniques/T1027/
- Credential Dumping (T1003): https://attack.mitre.org/techniques/T1003/
- Brute Force (T1110): https://attack.mitre.org/techniques/T1110/
- Network Service Scanning (T1046): https://attack.mitre.org/techniques/T1046/
- Software Discovery (T1518): https://attack.mitre.org/techniques/T1518/
- System Information Discovery (T1082): https://attack.mitre.org/techniques/T1082/
- Lateral Tool Transfer (T1570): https://attack.mitre.org/techniques/T1570/
- Software Deployment Tools (T1072): https://attack.mitre.org/techniques/T1072/
- Data from Information Repositories (T1213): https://attack.mitre.org/techniques/T1213/
- Data from Local System (T1005): https://attack.mitre.org/techniques/T1005/
- Data from Network Shared Drive (T1039): https://attack.mitre.org/techniques/T1039/
- Ingress Tool Transfer (T1105): https://attack.mitre.org/techniques/T1105/
- Data Encrypted for Impact (T1486): https://attack.mitre.org/techniques/T1486/
- Inhibit System Recovery (T1490): https://attack.mitre.org/techniques/T1490/
- Service Stop (T1489): https://attack.mitre.org/techniques/T1489/
Note: The Avertium Threat Report analyzes one current threat that has been shared by threat intelligence networks across the globe. Used internally by the Avertium CyberOps Team, this report will outline a “top-of-mind” threat and how it ought to be addressed accordingly.
This informed analysis is based on the latest data available.
Contact us for more information about Avertium’s managed security service capabilities.
Deciding between running an in-house SOC vs. using managed security services (MSS) to add more rigor, more relevance, and more responsiveness to your cybersecurity program? Compare the two options. Download the e-book!