
Case Study:
INTERNOVA TRAVEL GROUP
Discover how Avertium helps unburden Internova Travel Group's security team to have the space to start focusing on more strategic cybersecurity priorities.
Context over chaos. Disconnected technologies, siloed data, and reactive processes can only get you so far. Protecting businesses in today’s threat landscape demands more than a set of security tools – it requires context.
That's where Avertium comes in
Security. It’s in our DNA. It’s elemental, foundational. Something that an always-on, everything’s-IoT-connected world depends on.
Helping mid-to-enterprise organizations protect assets and manage risk is our only business. Our mission is to make our customers’ world a safer place so that they may thrive in an always-on, connected world.
Best-in-class technology from our partners... backed by service excellence from Avertium.
Interested in becoming a partner?
With Avertium's deal registration, partners can efficiently and confidently connect with Avertium on opportunities to protect your deals.
Microsoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
Dive into our resource hub and explore top
cybersecurity topics along with what we do
and what we can do for you.
June 2023 marked the beginning of Progress Software's MOVEit file transfer zero-days. The initial vulnerability, CVE-2023-34362, was identified as an SQL injection flaw that could lead to escalated privileges and unauthorized access to victims' environments.
Shortly after discovering this, Progress found additional critical SQL injection vulnerabilities that could allow attackers to steal data from customer databases. Exploitation of these vulnerabilities could allow attackers to compromise internet-exposed servers and manipulate or extract customer information without authentication. The flaws are now tracked as CVE-2023-35708 and CVE-2023-35036.
Although Progress promptly released patches, the Clop ransomware gang proved even quicker, leading to the compromise of several companies in the subsequent weeks. Let’s dive into the ongoing devastation caused by the MOVEit vulnerabilities and the threat actor targeting organizations.
In early June 2023, attackers leveraged Progress Software's managed file transfer solution, MOVEit Transfer, to pilfer corporate data. Although the SQL injection vulnerability lacked an assigned CVE number at the time, Progress issued a critical security advisory acknowledging its severity. The vulnerability was later tracked as CVE-2023-34362.
One week after the initial vulnerability, Progress announced another set of critical SQL vulnerabilities in MOVEit Transfer MFT that impacted all versions of MOVEit Transfer. The company stated that the vulnerabilities could allow attackers to compromise Internet-exposed servers and manipulate or extract customer information without authentication. They could submit a crafted payload to a MOVEit Transfer application endpoint which could result in modification and disclose of MOVEit database content.
The vulnerabilities were later tracked as CVE-2023-35708 and CVE-2023-35036. Progress provided patches and mitigations for the vulnerabilities, but not before threat actors exploited the flaws and stole significant data from various companies. The data theft took place within a few days.
By the second week of the MOVEit vulnerability discussions, reports surfaced that the Clop ransomware gang was responsible for the majority of breaches targeting organizations. On June 8, 2023, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) and Federal Bureau of Investigation (FBI) jointly issued an advisory, shedding light on the ongoing exploitation of the critical vulnerabilities in Progress Software's MOVEit Transfer application, as they were actively being abused as a method for ransomware distribution.
According to corporate investigation and risk consulting firm Kroll, evidence indicates that the cybercrime gang had been conducting experiments to exploit CVE-2023-34362 as early as July 2021. Additionally, they were devising techniques to steal data from compromised MOVEit servers since at least April 2022. In July 2021, a significant portion of their reconnaissance and testing activities were reportedly conducted manually. However, by April 2022, the gang had transitioned to an automated approach for investigating multiple organizations and gathering information.
The company stated that Clop had already developed the MOVEit Transfer exploit during the GoAnywhere event, but they deliberately chose to execute the attacks sequentially instead of simultaneously. This observation highlights the extensive planning and preparation that typically leads to large-scale exploitation incidents. The threat actors sent an extortion notice to targeted companies, demanding that they reach out to the group by June 14, 2023 or have their data published on the group’s data leak site.
In March 2023, Avertium's Capability Development team released a Threat Intelligence report that addressed the GoAnywhere vulnerability (CVE-2023-0669) exploited by Clop. Like MOVEit, GoAnywhere was utilized by the threat actors to exfiltrate data and extort organizations. GoAnywhere, similar to MOVEit, serves as a secure file transfer tool widely adopted by numerous organizations. By exploiting the vulnerabilities in GoAnywhere, Clop managed to breach more than 130 organizations.
By June 15, 2023, Clop started publishing a list of victims, which included various U.S. banks and universities, on their data leak site. Reports indicated that the Russian-linked ransomware group had been actively exploiting the vulnerability since May 2023.
The list of victims included U.S.-based financial institutions like First National Bankers Bank and 1st Source, along with Putnam Investments, a Boston-based investment management firm, Shell, the U.K.-based energy company, and Landal Greenparks, a Netherlands-based organization. Other victims listed:
Among the most alarming breaches are those impacting Schneider Electric, Siemens Energy, the University of California at Los Angeles (UCLA), Werum (a pharmaceutical technology provider), AbbVie (a biopharmaceutical company), and the New York City Department of Education (a school district).
UCLA utilizes MOVEit Transfer to facilitate file transfers within the campus and with external entities. The university stated that it discovered the breach on May 28, 2023, and immediately activated incident response procedures and applied the patch issued by Progress. The fallout from the attack on UCLA appears to be minimal but the New York City Department of Education was not as fortunate.
In late June 2023, it was verified that the New York City Department of Education fell victim to the MOVEit vulnerabilities, resulting in a breach. Exploiting this vulnerability, Clop obtained access to critical student and staff data, affecting approximately 45,000 students and a total of 19,000 documents.
According to a letter sent to families, the Department of Education (DOE) utilized MOVEit to internally transfer documents and data, as well as to exchange information with vendors, which included third-party special education service providers. After being alerted about the vulnerability, the New York City DOE promptly addressed the issue by applying necessary patches, in collaboration with the NYC Cyber Command. However, an internal investigation conducted by the DOE unveiled that approximately 19,000 documents had already been illicitly accessed prior to patching.
Siemens Energy, a Munich-based energy technology company with a global reach, confirmed that their data was stolen in the recent data-theft attacks carried out by the Clop ransomware group, using the MOVEit zero-day. Siemens Energy, employing 91,000 individuals and generating an annual revenue of $35 billion, operates across various sectors of the energy industry.
Siemens Energy specializes in the design, development, and production of a diverse array of industrial products. These encompass industrial control systems (ICS), advanced power and heat generation units, renewable energy systems, energy delivery systems both on and off-site, as well as adaptable power transmission solutions.
Additionally, the company offers an extensive selection of cybersecurity consulting services tailored specifically for the oil and gas sector. These services encompass the development of incident response plans, conducting vulnerability assessments, and implementing effective patch management strategies.
Although the company confirmed the breach and data theft, they don’t have any evidence that critical data was stolen or that any data has been leaked.
Shortly after receiving the notification, it was reported that Clop targeted a minimum of three U.S. government agencies, leveraging the vulnerabilities in MOVEit file-transfer. In response, the State Department announced a reward of $10 million for any substantiated evidence linking Clop to a foreign government.
On June 20th, a class-action lawsuit was initiated in a Massachusetts district court by three individuals from Louisiana against Progress Software. The Bedford-based company is the manufacturer of MOVEit file Transfer and Cloud file transfer services, widely adopted by numerous organizations. The lawsuit, representing over 100 individuals, alleges that Progress Software's security practices were negligent, leading to the exposure and theft of personal data through the breach. The complaint highlights the significant value of this information to data thieves, describing it as a "gold mine." The plaintiffs are seeking damages exceeding $5 million.
Under its Ransomware Vulnerability Warning Pilot initiative, CISA has taken the step of notifying over 100 organizations that their internet-facing devices possess vulnerabilities frequently exploited by ransomware attackers. Among these alerts, 26 specifically pertain to the MOVEit Transfer vulnerability. This proactive effort aims to raise awareness and prompt remedial actions within the affected organizations to address the identified flaws and bolster their defenses against potential ransomware threats.
Through the implementation of the Ransomware Vulnerability Warning Pilot program, CISA aims to proactively assist critical infrastructure operators in preempting ransomware attacks. This involves conducting vulnerability scans on internet-exposed devices, targeting known vulnerabilities often exploited by ransomware groups.
Additionally, CISA utilizes its administrative subpoena authority to notify the owners of these devices about the flaws. The objective is to encourage these operators to take appropriate measures in addressing the vulnerabilities and strengthening their defenses against potential ransomware incidents.
“We’re also going to pivot fast when we need to. The MOVEit Transfer vulnerability cropped up a few weeks ago, and when we saw threat actors begin to exploit it, we put that into the program. And so far, there have been about 26 notifications of entities throughout the United States, and we’re making more as we speak… we have the ability to think strategically on how to use this, but also to pivot fast when we need to.” - CISA
The aftermath of Clop's MOVEit attacks continues to unfold, with ongoing disclosures of new victims on the gang's website and daily publication of compromised data. These attacks have had far-reaching consequences, affecting various companies, federal government agencies, and local state agencies. As a result, numerous data breaches have occurred, exposing the sensitive information of millions of individuals. However, there are ways organizations can take proactive steps to protect themselves from vulnerabilities such as MOVEit.
NOTE: For the latest mitigations and updates regarding the MOVEit vulnerabilities, please see Progress Software’s advisory.
It's important to note that these recommendations should be supplemented by ongoing monitoring of emerging threats, collaboration with cybersecurity experts, and adherence to industry best practices to strengthen an organization's overall security posture.
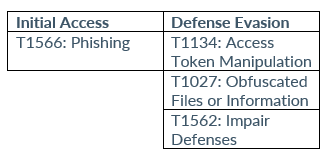
NOTE: For an extended list of Clop IoCs, please see the following link.
Related Resource:
Clop ransomware claims it breached 130 orgs using GoAnywhere zero-day (bleepingcomputer.com)
Government & Law Enforcement Crack Down On Cybercrime (avertium.com)
MOVEit Transfer and MOVEit Cloud Vulnerability (progress.com)
CISA Sounds Alarm on Critical Infrastructure Devices Vulnerable to Ransomware | Decipher (duo.com)
Latest MOVEit exploit hits thousands of NYC school students and staff | CSO Online
Progress Software hit with class action lawsuit over MOVEit hack | SC Media (scmagazine.com)
UCLA, Siemens Among Latest Victims of Relentless MOVEit Attacks (darkreading.com)
CISA Sounds Alarm on Critical Infrastructure Devices Vulnerable to Ransomware | Decipher (duo.com)
Clop Ransomware Gang Likely Aware of MOVEit Transfer Vulnerability Since 2021 (thehackernews.com)
CLOP Ransomware exploits MOVEit software | McAfee Blog
Siemens Energy confirms data breach after MOVEit data-theft attack (bleepingcomputer.com)
Clop Ransomware Gang Likely Aware of MOVEit Transfer Vulnerability Since 2021 (thehackernews.com)
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.