- ABOUT
-
-
About Us
Security. It’s in our DNA. It’s elemental, foundational. Something that an always-on, everything’s-IoT-connected world depends on.
Helping mid-to-enterprise organizations protect assets and manage risk is our only business. Our mission is to make our customers’ world a safer place so that they may thrive in an always-on, connected world.
-
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- SOLUTIONS
-
-
Governance, Risk & Compliance
GRC with context – not complexity. -
Attack Surface Management
No more blind spots, weak links, or fire drills. -
Managed XDR & SecOps
Detect, adapt, and attack with context. -
Microsoft Security Solutions
End-to-end support from strategy to daily operations to maximize your Microsoft Security.
-
-
- PARTNERS
-
-
Our Partners
Best-in-class technology from our partners... backed by service excellence from Avertium.
-
Partner Opportunity Registration
Interested in becoming a partner?
With Avertium's deal registration, partners can efficiently and confidently connect with Avertium on opportunities to protect your deals.
-
Latest Avertium Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- NEWS & RESOURCES
-
-
News & Resources
Dive into our resource hub and explore top
cybersecurity topics along with what we do
and what we can do for you. -
Latest Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- CONTACT
MFA Breaches & MFA Fatigue
Executive Summary
In October 2022, Uber suffered a security breach, and an attacker was able to access Uber’s user data that was stored on a third-party server. After gaining access to Uber’s internal network and Slack server, the attacker harassed employees while bragging about Uber’s systems being hacked. Prior to the attack, the same attacker used Slack to send messages regarding higher wages for Uber drivers. Because the incident couldn’t be mitigated by IT workers, it made it next to impossible for Uber drivers to fulfill their jobs.
After the security breach, Uber released statements saying that all of their services were fully functional, and that customer data was not compromised. While this was a relief to customers and stakeholders, there was still confusion regarding how the breach happened in the first place. The answer includes social engineering, Multi-Factor Authentication (MFA) fatigue, and breached credentials.
Despite Uber being at the forefront of the MFA attack, they would not be the only large company to suffer from a cyber attack in this manner. Let’s take a look at MFA attacks and what organizations can do to move toward better protection.

what is mfa?
Before we dig into MFA attacks, let’s talk about MFA in general. In the past, most people logged into banking accounts, school accounts, mobile phone provider accounts, and other confidential service accounts by entering a simple username and password. For a while that method worked until attackers started to guess passwords (likely re-used by the user on several sites) and brute force their way into accounts.
Now, we use something called Multi-factor Authentication or MFA. MFA is a security enhancement that allows an individual to provide two pieces of evidence (credentials) when logging into an account. Credentials can be any of the following: something you have (a credit card), something you know (a PIN number), somewhere you are (a location) or something you are (face ID).
To enhance security, the credentials must come from two separate categories – like typing your username and password on one screen, then using an authenticator app on your mobile device as a second factor to generate a one-time code that you enter on a different screen before being officially logged in. In some cases, if you come back to a site and use the same device, it will be remembered as the second factor.
MFA provides an extra layer of security and keeps your information that much more safe as a thief would need to steal both your password and your phone. This would make it extremely difficult for a cyber criminal since you would notice if your phone went missing and likely report it before anyone could log into an account with MFA enabled. Because cybercriminals use malware, phishing attacks, and brute-force to steal user information, every extra layer of security can help keep them from breaching individuals and organizations.
mfa breaches
Uber
In September 2022, Uber was allegedly breached by an 18-year-old hacker who goes by the name “Tea Pot”. The hacker tricked an Uber employee (social engineering) into giving him account access and accepting an MFA prompt, allowing the hacker to register their own device. After gaining a foothold, the attacker found Uber’s internal network share which contained PowerShell scripts with privileged admin credentials. The credentials granted access to other systems including OneLogin, SentinelOne’s incident response portal, AWS, Slack, and Google Cloud Platform.
Following the breach, the Singapore based cyber security firm Group-IB, confirmed that on September 16, 2022, vx-underground posted screenshots with access to Uber’s internal systems. The screen shots were posted by a user named “teapots2022”. After analysis, the firm’s researchers found two files which were identified as logs from stealers sold on the dark web.
The logs were then put up for sale on September 12th and 14th, indicating that the data was fresh due to the attack that utilized them being revealed between September 15th and 16th. According to Group-IB, the logs contained authorization data for uber.onelogin.com, an identity and access management provider. Researchers also stated that due to the screen shots, the attacker could have purchased logs to enable them to sort through accounts and find accounts with privileged access to internal network resources.
Group-IB stated that the other logs contained access credentials to other resources, including Facebook, Slack, Google, and Instagram. The credentials could have been used by the threat actor to move through Uber’s network via social engineering. Uber’s breach was made successful via MFA fatigue.
According to Uber, the attacker likely purchased the Uber contractor’s corporate password on the dark web, after the contractor’s mobile phone was infected with malware. The attacker then disguised himself as Uber’s IT and contacted the contractor on WhatsApp. The attacker told the contractor that the only way to get rid of the MFA notifications was to accept one.
Lapsus$ has also been successful with attacking large organizations via MFA fatigue. At the end of March 2022, Lapsus$ breached the software services firm, Globant, and dumped a 73GB archive of stolen data. Globant provides software services for brands such as Google, Disney, and Electronic Arts. The group also was responsible for breaching T-Mobile in April 2022 and stealing their source code. Kevin Beaumont observed the threat actors posting the below messages in their Telegram channel.
Image 1: Lapsus$ Telegram Channel Messages
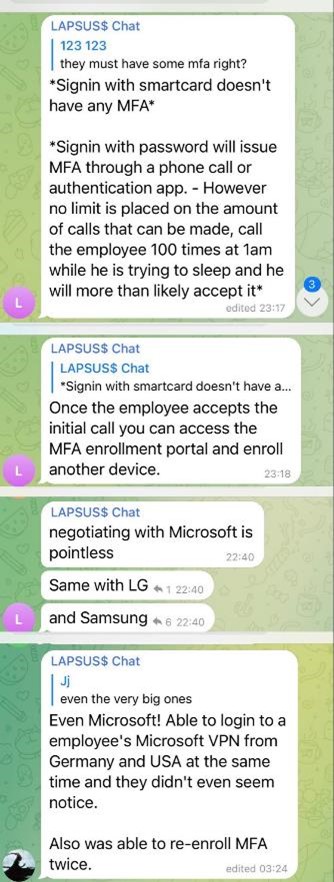
Source: Kevin Beaumont
Rockstar Games
Following the Uber breach, the American video game publisher Rockstar Games confirmed they were also victims of a cyber attack. The attack involved an unauthorized user illegally downloading non-released footage of Grand Theft Auto VI. The breach didn’t disrupt the company’s live game services and didn’t have an impact on the development of ongoing projects, but the attacker accessed confidential information.
The data accessed contained almost 90 videos of clips from the game and was leaked over the weekend by a familiar source with the following username – “teapotuberhacker”. In a forum message, the attacker said that the videos were downloaded from Slack. This confession indicates that the threat actor used the same MFA bombing he used in the Uber breach, to get past extra account security layers. In another message in the forum, the attacker stated that he would leak more if Rockstar didn’t pay him – his ultimate goal being financial gain.
Dropbox & GitHub
By November 1, 2022, Dropbox informed the public that the company suffered from a data breach and threat actors gained access to some source code and sensitive information belonging to customers and employees. The company actually learned about the breach in October 2022 after being informed by GitHub.
Not long after alerting Dropbox of their breach, GitHub learned that they too were the victims of a cyber attack. Some of GitHub’s users were targeted in a phishing campaign that impersonated the integration and delivery platform, CircleCI. Their goal was to obtain credentials and two-factor authentication codes. Similarly, the threat actors behind Dropbox’s breach sent phishing emails to several employees. The emails directed them to bogus CircleCI websites intended to glean credentials and passwords for MFA.
The threat actors were able to successfully access one of Dropbox’s GitHub organizations and copied 130 code repositories. Dropbox explained that the repositories included copies of third-party libraries slightly modified for use by Dropbox, as well as internal prototypes. Also, user payment information, passwords, and developer credentials were exposed.
How did the threat actors manage to breach the organizations? According to Security Week, the attackers phished for one-time passwords generated by employee hardware authentication keys. Although hardware authentication keys are considered more secure, Dropbox stated that the ones they used were not the best and they needed to develop a more phishing resistant MFA – something that combines WebAuthn with hardware tokens or biometric factors.
mfa fatigue
As MFA attacks become more popular with threat actors, it’s important to talk about the rise of MFA fatigue. One of the most common ways threat actors breach corporate networks is via stolen employee login credentials. It doesn’t take much for threat actors to obtain these credentials – dark web forums, malware, and phishing attacks are just a few of the ways malicious actors get what they want.
Most large corporations know that threat actors are looking for any way possible to breach their networks, and most make sure that their networks and systems are safe by enforcing MFA amongst staff and third-party vendors. As we stated previously, MFA is an extra layer of security that prevents users from logging into a network without entering an additional form of verification.
Yes, there are ways threat actors bypass MFA, but most methods include man-in-the-middle phishing attack frameworks or stealing cookies through malware. Lately, threat actors have adopted a new way of bypassing roadblocks and that is through MFA fatigue or MFA push spam. This technique doesn’t require malware or even phishing infrastructure but has been quite successful for various threat actors.
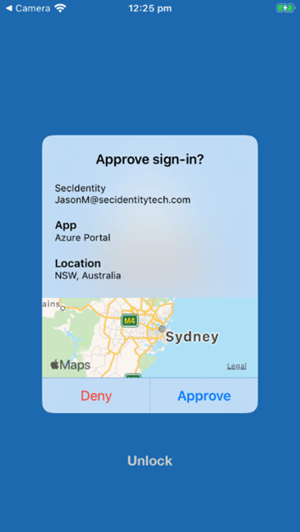
Image 2: MFA Prompt
Source: Microsoft
When organizations implement MFA and configure “push” notifications, the employees see a message on the mobile device asking them to confirm if it’s them who is trying to log in using their credentials. MFA fatigue happens when an attacker runs a script, attempting to log in with stolen credentials repeatedly – causing a nonstop stream of MFA push requests. The goal is to keep sending these push notifications day and night until the victim on the receiving end of the requests breaks down and accepts the request or accidentally hits the “approve” button.
In some cases, an attacker will send the requests, then follow up by contacting the victim through email or other messaging platforms pretending to be IT support. This is done to try and convince the victim to accept the MFA prompt (i.e., Uber’s contractor). This kind of social engineering has been successful with threat actors like Lapsus$ and Yanluowang. The threat actors have breached large organizations such as Cisco, Uber, and Microsoft.
What can Organizations do?
When MFA fatigue attacks happen, most people don’t realize they are the target of a cyber attack. Instead, they get confused and think that their device is glitching or that maybe they did try to sign in to one of their accounts but forgot. This kind of attack can be scary for organizations because most of the time it goes undetected until a breach takes place.
However, all hope is not lost. There are measures that organizations can take to prevent MFA fatigue attacks and MFA breaches. Cyber security professionals such as Kevin Beaumont state that there are other ways to authenticate users that are more effective, including but not limited to:
- Duo Verified Push – this verification method involves number matching. When a user wants to login to an account, a number will display on the web browser’s screen prompting the user to enter it into the MFA app. This number may also appear in the MFA app and prompt you to enter it on the browser screen. Only the user logging into the account will see the numbers and it should raise a red flag for the user if there are attempts to convince them to enter numbers into their MFA app.
- Specops Password Policy – this is a password policy enforcement tool that can help organizations automate the development of higher quality passwords, closing security gaps. This tool has built in defenses and could have been helpful for Uber and other organizations.
- Specops Secure Service Desk – this tool automates the verification of an end user before they are allowed to reset their password. Due to the tool’s zero-trust system, help desk employees don’t have to trust that the caller is who they say they are, the automation does that for them.
- Limit Authentication Requests – limiting the amount of MFA authentication requests per user and locking accounts or raising alerts when thresholds are exceeded could prevent an MFA fatigue attack.
- FIDO – Some security experts recommend that organizations move toward FIDO hardware security keys. This will help ensure secure logins. FIDO Authentication replaces password-only logins with security keys, facial recognition, fingerprints, and voice recognition. However, some security experts say that this kind of security may not be compatible with some online services.
Image 3: DUO Verified Push
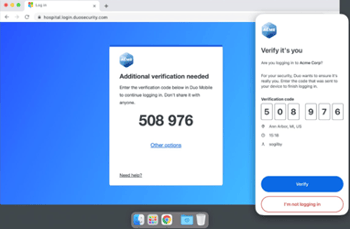
Source: Kevin Beaumont
If you want to continue to keep your organization safe, Avertium highly recommends that your organization consider implementing one of the above recommendations in addition to utilizing Avertium’s services. Avertium has the tools to assess your cyber environment and to provide a deeper understanding regarding why it’s important to maintain excellent cyber security posture.
How Avertium is Protecting Our CUSTOMERS
- Expanding endpoints, cloud computing environments, and accelerated digital transformation have decimated the perimeter in an ever-expanding attack surface. Avertium offers Attack Surface Management, so you’ll have no more blind spots, weak links, or fire drills.
- Avertium recommends utilizing our service for DFIR (Digital Forensics and Incident Response) to help you rapidly assess, contain, eradicate, and recover from a security incident like a malware attack.
- Fusion MXDR is the first MDR offering that fuses together all aspects of security operations into a living, breathing, threat-resistant XDR solution. By fusing insights from threat intelligence, security assessments, and vulnerability management into our MDR approach, Fusion MXDR offers a more informed, robust, and cost-effective approach to cybersecurity – one that is greater than the sum of its parts.'
- Avertium offers VMaaS to provide a deeper understanding and control over organizational information security risks. If your enterprise is facing challenges with the scope, resources, or skills required to implement a vulnerability management program with your team, outsourced solutions can help you bridge the gap.
- Avertium offers user awareness training through KnowBe4. The service also includes Incident Response Table-Top exercises (IR TTX) and Core Security Document development, as well as a comprehensive new-school approach that integrates baseline testing using mock attacks.
avertium's recommendations
To mitigate MFA Fatigue attacks, Microsoft and Avertium recommend the following:
- Remove factors relying on simple approvals. Instead, approvals should require users have provable context on the login request. Example: instead of “press 3 to approve”, the user should have to round-trip information presented in the login request, such as entering a number they see on a screen.
- Having the user enter information provided in the authentication request means the requirements or requiring them to enter screen information on their authenticating device is a proven way to disrupt MFA fatigue attacks.
- Having the user enter information provided in the authentication request means the requirements or requiring them to enter screen information on their authenticating device is a proven way to disrupt MFA fatigue attacks.
- Avoid methods that allow simple approvals and are subject to MFA fatigue. Microsoft suppresses notifications originating with features unfamiliar to the “good” user, instead of asking the user to check the app. This prevents bad experiences triggered by the attacker by pushing unexpected notifications.
- Also, Azure AD provides risk levels on every login, as well as login attempts which show risk.
- Also, Azure AD provides risk levels on every login, as well as login attempts which show risk.
- Layered MFA adds a phone call or text message to password-based authentication. Layered MFA may deter attacks, but attacks can still use MFA fatigue to penetrate those defenses. Modern, passwordless authentication methods such as Windows Hello, FIDO, or Microsoft Authenticator will effectively defend against MFA fatigue and advanced adversary-in-the-middle attacks.
- The SOC can set anomaly-based triggers that will notify them if certain thresholds are exceeded or block user authentication from suspicious IP addresses.
- Look at hard indicators of compromise (IoCs). The attacker may have access to credentials and will need to solicit the user to approve MFA to gain access. Blocking MFA fatigue will force the attacker to choose a different attack path. The OTP configuration means the user is less susceptible to an MFA attack, thus reducing risk.
MITRE Map
Lapsus$
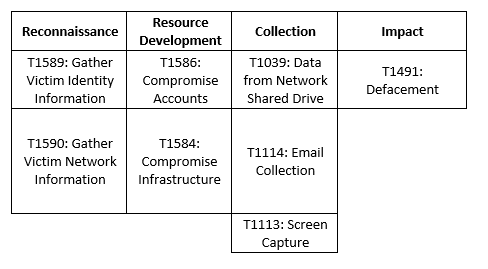
Indicators of Compromise (IoCs)
Lapsus$
|
07b7da86d2f548d18462f8d6d869052a |
|
14781bc862e8dc503a559346f5dcc518 |
|
43bb437d609866286dd839e1d00309f5 |
|
61089a51d3be666631053d516ad9b827 |
|
91b88d281ef983296157f8ebfc73958036148194 |
|
f9153289b209929130f897ee47710b4c94aa6453 |
|
065077fa74c211adf9563f00e57b5daf9594e72cea15b1c470d41b756c3b87e1 |
|
2f578cb0d97498b3482876c2f356035e3365e2c492e10513ff4e4159eebc44b8 |
|
http://8[.]3[.]1[.]0 |
Supporting Documentation
Back to Basics: What’s multi-factor authentication - and why should I care? | NIST
What is MFA (Multi-Factor Authentication)? Learn How it Works | UpGuard
https://twitter.com/GroupIB_GIB/status/1570821193510555649?s=20&t=5SUDu6dv6Bs_zBo3-3FJHg
https://twitter.com/GroupIB_GIB/status/1570821182026547201?s=20&t=5SUDu6dv6Bs_zBo3-3FJHg
Rockstar Games Confirms Hacker Stole Early Grand Theft Auto VI Footage (thehackernews.com)
https://twitter.com/GroupIB_GIB/status/1570821218428932096?s=20&t=5SUDu6dv6Bs_zBo3-3FJHg
Hackers Stole Source Code, Personal Data From Dropbox Following Phishing Attack | SecurityWeek.Com
Dropbox Hacked - IT Security Guru
What the Uber Hack can teach us about navigating IT Security (bleepingcomputer.com)
MFA Fatigue: Hackers’ new favorite tactic in high-profile breaches (bleepingcomputer.com)
https://twitter.com/GossiTheDog/status/1559933630608248837?s=20&t=po-wSQLDU7UT97mMkWF6lQ
MFA Fatigue: Hackers’ new favorite tactic in high-profile breaches (bleepingcomputer.com)
MFA Fatigue: Hackers’ new favorite tactic in high-profile breaches (bleepingcomputer.com)
Multi-Factor Authentication Fatigue Key Factor in Uber Breach (infoq.com)
LAPSUS$ Hacking Group - AlienVault - Open Threat Exchange
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.