- WHY AVERTIUM?
-
-
Why Avertium?
Context over chaos. Disconnected technologies, siloed data, and reactive processes can only get you so far. Protecting businesses in today’s threat landscape demands more than a set of security tools – it requires context.
That's where Avertium comes in
-
Considering Microsoft?
Avertium Named Microsoft Security Solutions PartnerAvertium’s managed services for Microsoft Security Solutions is delivered through the company’s premium service: Fusion MXDR. Fusion MXDR includes 24x7 monitoring and management of Defender for Endpoint and Sentinel, threat intelligence, attack surface
monitoring, and vulnerability management for Microsoft Security customers. -
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- SOLUTIONS
-
-
Governance, Risk, + Compliance
GRC with context – not complexity. -
Attack Surface Management
No more blind spots, weak links, or fire drills. -
Threat Detection + Response
Detect, adapt, and attack with context. -
Microsoft Security Solutions
End-to-end support from strategy to daily operations to maximize your Microsoft Security.
-
-
- COMPANY
-
-
About Us
Security. It’s in our DNA. It’s elemental, foundational. Something that an always-on, everything’s-IoT-connected world depends on.
Helping mid-to-enterprise organizations protect assets and manage risk is our only business. Our mission is to make our customers’ world a safer place so that they may thrive in an always-on, connected world.
-
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- PARTNERS
-
-
Our Partners
Best-in-class technology from our partners... backed by service excellence from Avertium.
-
Partner Opportunity Registration
Interested in becoming a partner?
With Avertium's deal registration, partners can efficiently and confidently connect with Avertium on opportunities to protect your deals.
-
Latest Avertium Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- NEWS & RESOURCES
-
-
News & Resources
Dive into our resource hub and explore top
cybersecurity topics along with what we do
and what we can do for you. -
Latest Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- CONTACT
LockBit 4.0? - An Update on the LockBit Ransomware Group
executive summary
For years, Avertium has diligently monitored the malicious activities of LockBit as they targeted organizations across various countries, including the U.S., the UK, Germany, China, India, France, Ukraine, and Indonesia. Our most recent LockBit threat intelligence report dates back to 2022. Throughout this period, the threat actors exhibited high levels of activity, launching attacks across multiple sectors and global regions. Although their pace momentarily slowed for a few months, they resumed activity in the fall of 2022, notably making headlines for targeting organizations in the IT services and automotive industries.
The LockBit ransomware group, known as one of the most prolific in the world, victimized over 2,000 entities, accumulating ransom payments exceeding $120 million and issuing demands totaling hundreds of millions more.
While other threat actors faced the repercussions of law enforcement, LockBit persisted in its attacks into 2024—until recently. In February 2024, the UK National Crime Agency's Cyber Division, in collaboration with the Justice Department, FBI, and international partners, disrupted LockBit's operations. This intervention involved seizing numerous public-facing websites and control of servers used by LockBit administrators. As a result, LockBit's ability to attack, encrypt networks, and extort victims through data threats was severely impeded.
Despite this significant disruption, there are concerns that LockBit may have developed a new version of their file-encrypting malware just prior to the takedown. This raises the critical question: Has LockBit truly been eliminated, or should the cybersecurity community brace itself for LockBit 4.0?
tir snapshot
- LockBit is a ransomware-as-a-service (RaaS) operation that has been active since 2019. Historically, LockBit refrained from targeting systems within Russia or the Commonwealth of Independent States, likely as a precaution against law enforcement action.
- In January 2021, LockBit underwent its first rebranding, emerging as LockBit 2.0. This iteration relied on tools like Windows PowerShell and Server Message Block (SMB) to infiltrate organizations.
- In March 2022, LockBit underwent its second rebranding, known as LockBit 3.0. They persisted in targeting various sectors, with approximately one-third of their victims originating in the BFSI sector.
- Right before law enforcement dismantled LockBit's ransomware operation, the developers were on the verge of releasing a new version of their notorious malware, tentatively named LockBit-NG-Dev or LockBit 4.0.
- The new LockBit variant, currently in development, diverges from previous versions by being written in .NET and compiled with CoreRT, utilizing MPRESS for packing.
- This advanced encryptor supports three encryption modes - "fast," "intermittent," and "full" - utilizing AES+RSA encryption.
- While LockBit relied on talent hired externally, these individuals are likely to continue their activities, with LockBit potentially shifting operations to external collectives like Akira.
- Red Sense believes that the chances of rebuilding LockBit's infrastructure are slim due to the technical limitations of its leadership and the departure of key personnel responsible for its development.
lockbit
As previously stated, LockBit is a ransomware-as-a-service (RaaS) operation that has been active since 2019. Historically, LockBit refrained from targeting systems within Russia or the Commonwealth of Independent States, likely as a precaution against law enforcement action.
Among LockBit's notable earlier exploits was the attack on Accenture, a leading global tech consultancy firm, in August 2021. During this incident, the group exfiltrated 6 TB of data and demanded a $50 million ransom. LockBit is known for thorough reconnaissance of its targets, evidenced by Accenture's substantial revenue of $44.33 billion in 2020.
In January 2021, LockBit underwent its first rebranding, emerging as LockBit 2.0. This iteration relied on tools like Windows PowerShell and Server Message Block (SMB) to infiltrate organizations. Additionally, the group became more public-facing, granting multiple interviews. They even advocated for the use of Bitdefender as a defense against ransomware attacks.
During this time, LockBit figured out how to bypass Bitdefender, such as utilizing the official Bitdefender Uninstall Tool to deactivate defenses.
SECOND REBRANDING
In March 2022, LockBit underwent its second rebranding, known as LockBit 3.0. They persisted in targeting various sectors, with approximately one-third of their victims originating from the BFSI sector. This rebranding introduced new tactics and techniques. The latest ransomware variant encrypted files on victims' machines and added the extension "HLjkNskOq" to encrypted files.
LockBit 3.0 used sophisticated tactics to encrypt files, including deleting select services and utilizing WMI queries to enumerate Volume Shadow copies before encryption, thus hindering restoration attempts. The ransomware also altered victims' wallpapers to indicate compromise and issued ransom notes instructing payment via Bitcoin, threatening data leaks if demands were not met.
In the new extortion model, LockBit 3.0 enabled the purchase of stolen data through its leak site, facilitating downloads via Torrent or direct links based on data size. Additionally, the group initiated a bug bounty program, redirecting victims to a Tor link in ransom notes to access the program, inviting security researchers and hackers to uncover flaws in LockBit's ransomware.
In September 2022, LockBit 3.0 adopted a unique advertising strategy by offering payment to individuals willing to tattoo the LockBit logo on their bodies, citing high demand for the promotion which was set to end by September 11, 2022. Participants were required to make the tattoo permanent and provide a photo of it alongside their bitcoin wallet, with LockBit ultimately compensating over 10 individuals with $1,000 each for their tattoos. Despite its unconventional nature, this approach to advertising was considered cost-effective by security experts.
ATTACKS
PAST
- Pendragon Attack (October 2022):
- LockBit 3.0 targeted Pendragon, a UK car dealership, claiming to have stolen over two million files and demanding a $60 million ransom.
- Pendragon refused to negotiate or pay the ransom, opting instead to conduct an investigation. LockBit stole only 5% of their database.
- Oomiya Attack (October 2022):
- A LockBit 3.0 affiliate attacked Japanese tech company Oomiya, threatening to leak stolen data if the ransom was not paid by October 20, 2022.
- Oomiya's role in the global supply chain across various industries could have significant repercussions for third-party organizations.
- Kingfisher Insurance Attack:
- LockBit 3.0 targeted Kingfisher Insurance, a UK insurance company, claiming to have stolen 1.4 TB of personal data and demanding an undisclosed ransom by November 28, 2022.
- Thales Attack (November 2022):
- LockBit 3.0 attacked Thales, a French defense and technology group, stealing their data and threatening to publish it on their data leak site by November 7, 2022.
- Thales initiated an internal investigation and informed the ANSSI national cyber security agency, with LockBit eventually publishing Thales' data on their site by November 10, 2022.
RECENT
Boeing (October 2023)
LockBit claimed responsibility for an attack against Boeing on October 27, 2023, listing the company on its data leak site and setting ransom deadlines of November 2 and 10. Following warnings, LockBit released approximately 4 GB of alleged Boeing data on its leak site, threatening further publication if the company did not cooperate and participate in ransom negotiations.
Later, the entire cache of alleged Boeing data, estimated at around 40 GB, was made public. While Boeing confirmed that they were aware of the incident and engaged in investigations, it assured that the event was no threat to aircraft or flight safety. LockBit was able to breach Boeing by exploited Citrix Bleed (CVE-20233-4966).
Industrial and Commercial Bank of China (November 2023)
China's Industrial and Commercial Bank of China (ICBC), the nation's largest lender, reportedly paid a ransom following a recent ransomware attack on its U.S. arm, according to a representative from the LockBit ransomware gang. The attack, which disrupted trades in the U.S. Treasury market on November 9, left ICBC's U.S. broker-dealer owing BNY Mellon $9 billion temporarily.
The attack resulted in extensive disruptions, including a corporate email blackout, and forced employees to switch to Google mail. While the market has mostly returned to normalcy, the incident highlighted concerns about the resilience of the Treasury market and the regulatory scrutiny it would face. LockBit, a prominent ransomware threat, has targeted numerous organizations globally, with some choosing to pay ransom to avoid reputational damage or restore systems without digital backups.
EquiLend Holdings (February 2024)
EquiLend Holdings, a New York-based securities lending platform, suffered from a ransomware attack in January, leading to the theft of employee data, as confirmed in breach notification letters sent to affected personnel. While the company initially remained discreet about the incident, LockBit claimed responsibility.
EquiLend later acknowledged the ransomware attack on February 2, reassuring that client transaction data remained untouched. However, employee personally identifiable information (PII) was compromised, including names, dates of birth, and Social Security numbers. EquiLend assured employees of proactive measures, offering two years of free identity theft protection services. Established in 2001 by major global banks and broker-dealers, EquiLend now serves over 190 firms worldwide, providing securities finance marketplace services and multi-asset trading platforms, with transactions exceeding $2.4 trillion monthly.
Bluffing – Fulton County Georgia (February 2024)
Fulton County, Georgia, faced a ransomware threat from LockBit, who threatened to release stolen internal documents unless a ransom was paid. However, county officials denied making any payment or engaging in negotiations, with security experts suggesting LockBit's claims were likely a bluff. Following U.S. and U.K. law enforcement seizing LockBit's servers, the group's credibility was questioned. Despite LockBit's claims that Fulton County had paid the ransom and their data had been deleted, county officials remained adamant about not paying, and no evidence of payment was provided. Security analysts speculate that LockBit's recent actions are attempts to maintain credibility within the cybercrime community, but doubt remains about the validity of their claims.
lockbit 4.0? - lockbit-ng-dev
Right before law enforcement dismantled LockBit’s ransomware operation. The developers were on the verge of releasing a new version of their notorious malware, tentatively named LockBit-NG-Dev or LockBit 4.0. Thanks to collaboration with the UK's National Crime Agency, cybersecurity experts from Trend Micro were able to analyze a sample of the latest LockBit development, revealing its capabilities across multiple operating systems.
The new LockBit variant, currently in development, diverges from previous versions by being written in .NET and compiled with CoreRT, utilizing MPRESS for packing. Trend Micro's analysis shows a JSON-format configuration file detailing various operational parameters, including execution settings, ransom note specifics, unique identifiers, and RSA public key details. While lacking some features found in earlier versions, such as network self-propagation and printing ransom notes on printers, this new encryptor seems to be nearing completion.
Image 1: Decrypted Configuration
Source: Trend Micro
This advanced encryptor supports three encryption modes - "fast," "intermittent," and "full" - utilizing AES+RSA encryption. It also offers custom file or directory exclusion and can obfuscate file names to hinder restoration attempts. Additionally, it includes a self-delete feature that replaces LockBit's file contents with null bytes.
Trend Micro's comprehensive analysis sheds light on the intricate workings of LockBit-NG-Dev, providing valuable insight into its configuration parameters and operational mechanisms. Despite this technical advancement, the recent law enforcement action, part of Operation Cronos, deals another significant blow to LockBit operators, making it challenging to revive their illegal business, especially with security researchers now aware of the encrypting malware's source code.
what happens next?
On February 19, 2024, an official law enforcement announcement replaced LockBit’s shame blog, signaling an end to the group's operations, according to Yelisey Bohuslavskiy and Marley Smith from Red Sense. While LockBit relied on talent hired externally, these individuals are likely to continue their activities, with LockBit potentially shifting operations to external collectives like Akira. For potential victims, particularly in the healthcare sector, this means that former LockBit members will use familiar tactics but now operating under Akira's name.
As LockBit’s ransomware ecosystem faces collapse, outsourcing operations to maintain the allure of the ransomware operation’s past glory has become common practice. LockBit's demise is further emphasized by the loss of their blog, which law enforcement has openly mocked, highlighting the group's public image as a factor in its downfall.
Red Sense believes that the chances of rebuilding LockBit's infrastructure are slim due to the technical limitations of its leadership and the departure of key personnel responsible for its development. Additionally, the inclusion of LockBit members on the OFAC list ensures that any attempt to rebrand or revive the group will fail, as seen with Conti and previous sanctions. Also, potential financial backers (IABs) are unlikely to trust their investments in a group post-takedown, as their primary goal is financial gain. While LockBit may resort to dumping old data, a common tactic post-takedown, it is unlikely to yield any substantial results beyond media speculation. What lies ahead for LockBit? Probably, nothing.
avertium's recommendations
Even though law enforcement disrupted LockBit's operations, organizations shouldn't relax their security measures. It is important to remain vigilant and look out for LockBit's tactics, techniques, and procedures (TTPs), as they might incorporate them into Akira's ransomware operations:
- Sandboxed Browsers: Think about integrating sandboxed browsers as a security measure to safeguard systems against malware that comes from web browsing. Sandboxed browsers create a barrier between the host machine and any potentially harmful code.
- Password Logins: Make it mandatory for all accounts using password logins (such as service accounts, admin accounts, and domain admin accounts) to adhere to NIST standards for crafting and overseeing password policies [CPG 2.L].
- Firewall: Deploy a web application firewall and set it up with suitable rules to protect enterprise assets.
- MFA: Implement phishing-resistant multifactor authentication (MFA) for all services wherever feasible, especially for webmail, virtual private networks, and privileged accounts with access to critical systems [CPG 2.H].
- Antivirus Software: Deploy, consistently update, and activate real-time detection for antivirus software across all devices.
- Limit Network Connections: Regulate and limit network connections as per a network flow matrix.
- Command Line: Turn off command-line and scripting activities and permissions.
- Privilege escalation and lateral movement often rely on software utilities executed from the command line. If threat actors cannot utilize these tools, their ability to escalate privileges and move laterally will be significantly hindered [CPG 2.N].
How Avertium is Protecting Our Customers
It’s important to get ahead of the curve by being proactive with protecting your organization, instead of waiting to put out a massive fire. Avertium can provide the following services to help keep your organization safe from Snatch Ransomware:
- Fusion MXDR is the first MDR offering that fuse together all aspects of security operations into a living, breathing, threat-resistant XDR solution. By fusing insights from threat intelligence, security assessments, and vulnerability management into our MDR approach, Fusion MXDR offers a more informed, robust, and cost-effective approach to cybersecurity – one that is greater than the sum of its parts.
- Avertium aligns your Cybersecurity Strategy with your business strategy, ensuring that your investment in security is also an investment in your business. Our Cybersecurity Strategy service includes:
- Strategic Security Assessments - Strengthening your security posture begins with knowing where your current program stands (NIST CSF, Security Architecture, Business Impact Analysis, Sensitive Data Inventory, Network Virtualization and Cloud Assessment).
- Threat Mapping – Leverage Avertium’s Cyber Threat Intelligence, getting a more informed view of your most likely attack scenarios (Threat Assessment and MITRE ATT&CK).
- Cyber Maturity Roadmap - Embrace a comprehensive, quantifiable, and well-organized approach to establishing and continuously enhancing your cybersecurity resilience (Policy + Procedure Development, Virtual CISO (VCISO), Training + Enablement, Tabletop Exercises, and Business Continuity + Disaster Recovery Plan).
- Expanding endpoints, cloud computing environments, and accelerated digital transformation have decimated the perimeter in an ever-expanding attack surface. Avertium offers Attack Surface Management, so you’ll have no more blind spots, weak links, or fire drills. See every threat in your attack surface, every device, every entry point, and every vulnerability. Our Attack Surface Management services include:
- Risk Assessments
- Pen Testing and Social Engineering
- Infrastructure Architecture and Integration
- Zero Trust Network Architecture
- Vulnerability Management
- Note: We highly value your feedback. Kindly spare a moment to complete our feedback form, allowing us to enhance our services for our valued customers.
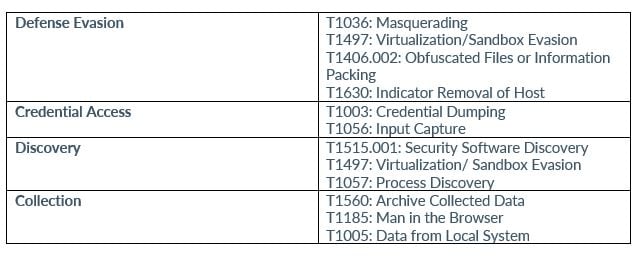
MITRE MAP
Supporting Documentation
Equilend warns employees their data was stolen by ransomware gang (bleepingcomputer.com)
LockBit ransomware gang claims it leaked stolen Boeing data | TechTarget
Gang says ICBC paid ransom over hack that disrupted US Treasury market | Reuters
LockBit Locked Down - Panda Security
Fulton County, Security Experts Call LockBit’s Bluff – Krebs on Security
An Update on LockBit 3.0 (avertium.com)
LockBit Malware Fix, Prevention & Patch | Trend Micro (US)
EquiLend data stolen in cyberattack, company confirms | TechRadar
LockBit's Leak Site Reemerges, a Week After 'Complete Compromise' (darkreading.com)
LockBit Story: A Three-Year Investigative Journey | RedSense Cyber Threat Intelligence
LockBit Attempts to Stay Afloat with a New Version | Trend Micro (US)
LockBit ransomware secretly building next-gen encryptor before takedown (bleepingcomputer.com)
Authorities disrupt LockBit ransomware, indict two RaaS affiliates (chainalysis.com)
LockBit claims ransomware attack on Fulton County, Georgia (bleepingcomputer.com)
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.