- WHY AVERTIUM?
-
-
Why Avertium?
Context over chaos. Disconnected technologies, siloed data, and reactive processes can only get you so far. Protecting businesses in today’s threat landscape demands more than a set of security tools – it requires context.
That's where Avertium comes in
-
Considering Microsoft?
Avertium Named Microsoft Security Solutions PartnerAvertium’s managed services for Microsoft Security Solutions is delivered through the company’s premium service: Fusion MXDR. Fusion MXDR includes 24x7 monitoring and management of Defender for Endpoint and Sentinel, threat intelligence, attack surface
monitoring, and vulnerability management for Microsoft Security customers. -
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- SOLUTIONS
-
-
Governance, Risk, + Compliance
GRC with context – not complexity. -
Attack Surface Management
No more blind spots, weak links, or fire drills. -
Threat Detection + Response
Detect, adapt, and attack with context. -
Microsoft Security Solutions
End-to-end support from strategy to daily operations to maximize your Microsoft Security.
-
-
- COMPANY
-
-
About Us
Security. It’s in our DNA. It’s elemental, foundational. Something that an always-on, everything’s-IoT-connected world depends on.
Helping mid-to-enterprise organizations protect assets and manage risk is our only business. Our mission is to make our customers’ world a safer place so that they may thrive in an always-on, connected world.
-
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- PARTNERS
-
-
Our Partners
Best-in-class technology from our partners... backed by service excellence from Avertium.
-
Partner Opportunity Registration
Interested in becoming a partner?
With Avertium's deal registration, partners can efficiently and confidently connect with Avertium on opportunities to protect your deals.
-
Latest Avertium Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- NEWS & RESOURCES
-
-
News & Resources
Dive into our resource hub and explore top
cybersecurity topics along with what we do
and what we can do for you. -
Latest Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- CONTACT
An In-Depth Look at Chinese APT, Aoqin Dragon
Executive Summary
Active since 2013, the APT Aoqin Dragon flew under the radar for ten years before researchers at Sentinel Labs identified their activity. Aoqin Dragon’s primary focus is cyberespionage against targets in Vietnam, Cambodia, Hong Kong, Australia, and Singapore. Although the Chinese speaking threat actor is a small group, they are powerful and launched attacks against education, government, and telecommunications organizations while remaining invisible. Let’s take a look at Aoqin Dragon’s techniques, tactics, and how the group was able to go unnoticed for a decade.

aoqin dragon
Aoqin Dragon is a Chinese speaking threat actor who has been operating since 2013. The group is known for using explicit themes to infect users, as well as using USB shortcut techniques to spread their malware and infect other targets. Aoqin Dragon’s infection chain can be divided into three parts. They include:
- The use of documents to exploit and trick victims into opening a malicious Word document to install a backdoor.
- Luring victims into clicking on fake anti-virus icons or links to deploy malware in the victim’s device.
- Forging a fake removable device to trick victims into opening a malicious folder and installing malware on their system.
According to our technology partner, SentinelOne's research team, Sentinel Labs, Aoqin Dragon’s baited documents (or lure documents) are geared towards targets interested in APAC political affairs. The documents also are not specific to one country but the entirety of Southeast Asia. Sentinel Labs also stated that because the group stayed in systems and networks long-term and were consistent with their attacks, they can assess that Aoqin Dragon’s motives are purely cyber espionage with their activities aligning with Chinese government political interests.
tactics and techniques
From 2012 to 2015, Aoqin Dragon took advantage of two vulnerabilities (CVE-2012-0158 and CVE-2010-3333) to compromise their targets. CVE-2012-0158 is a vulnerability in Windows Common Controls that allows for remote code execution. CVE-2010-3333 is a stack-based buffer overflow vulnerability in Microsoft Office that could allow attackers to execute arbitrary code via crafted RTF data.
Fake file icons and executable files have been used by varying threat actors over the years and is an effective tool for APTs like Aoqin Dragon. When combined with intriguing email content and a catchy file name, Aoqin Dragon can socially engineer their attacks and entice victims to click on a malicious file.
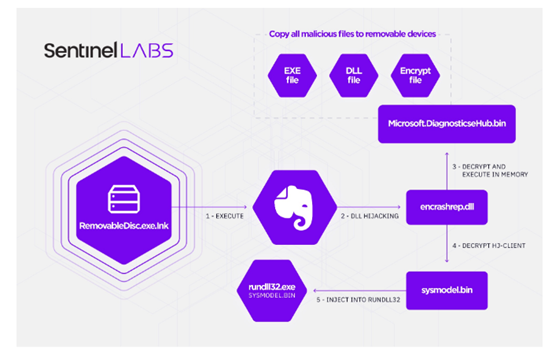
Since 2018, Aoqin Dagon has used fake removable USB device shortcuts as their initial point of infection. Victims who click on the shortcut icon will install a malicious loader, which contains two payloads. The first payload downloads the malicious files to removable devices for spreading and the second is an encrypted backdoor that creates a remote shell and uploads files to the victim’s machine. The second payload also downloads the files to Aoqin Dragon’s command and control servers. The encrypted backdoor also embedded three C2 servers for communication. Here is the attack chain of one of their most recent campaigns:
- To initiate malware, a removable Disk shortcut is made that contains a specific path
- After the victim clicks on the fake device, “Evernote Tray Application” is executed. This is followed by the use of DLL hijacking to load the malicious encashrep.dll loader as explore.exe.
- Once the loader is executed, it checks if it is in any attached removable devices.
- If the loader isn’t in the removable disk, it copies all modules under “%USERPROFILE%\AppData\Roaming\EverNoteService\”. This includes the backdoor loader, normal files, and the encrypted backdoor payload.
- The value “EverNoteTrayUService” is used by the malware to set the auto start function. One the victim restarts their computer, “Evernote Tray Application” is executed, and DLL hijacking is used to load the malicious loader.
- The loader checks the file path and then decrypts the payloads. As we mentioned previously, two payloads are used in the attack chain – 1. The spreader (copies malicious files to removable devices) and 2. The encrypted backdoor (injects itself into rundll32’s memory).
Aoqin Dragon also uses a custom backdoor that is more powerful than the previous one. The backdoor is a version of the Heyoka open-source project which uses spoofed DNS requests – creating bidirectional tunnel. Sentinel Labs stated that both backdoors have shell ability, but Heyoka is closer to a complete backdoor product.
Sentinel Labs stated that the main target type document formats Aoqin Dragon tries to find are Microsoft Word documents. Also, a script containing a “rar” command is embedded in the executable dropper with different fake security product icons. The dropper then employs a worm infection strategy using a removable device to infect malware into their victim’s device and breach their network.
Image 1: Infection Chain Flow
As you can see the DLL hijacking technique is used heavily by Aoqin Dragon to compromise targets and run their malware – including their newest malware loader, Mongall backdoor, and the modified version of Heyoka backdoor. According to Sentinel Labs, the Mongall backdoor is a small backdoor that goes back to 2013 when it was discovered by ESET. At that time, the threat actor using Mongall was targeting the Telecommunications Department and the Vietnamese government. Since then, Aoqin Dragon has been seen targeting Southeast Asia with an upgraded Mongall encryption protocol and Themida packer. Mongall isn’t rich in features but it’s still quite effective due to its ability to create a remote shell and upload files to a victim’s machine.
The modified Heyoka backdoor is a different from Mongall and is based on the Heyoka open-source project. The backdoor was modified to be a custom backdoor using the DLL injection to deploy in the victim’s environment. The debug log for Heyoka contains simplified Chinese characters, which indicates that the APT is Chinese speaking.
10 years the radar
Sentinel Labs has observed that Aoqin Dragon’s TTPs have evolved several times, which is how they were able to fly under the radar for a decade. The means they once used to infect their targeted devices has changed. During their first few years of operation, the threat actor relied on the previously mentioned CVE’s (CVE-2012-0158 and CVE-2010-3333). They were able to exploit these vulnerabilities due to their target’s negligence with patching.
In 2018, Aoqin Dragon changed the way they targeted devices by utilizing fake removable devices as their infection vector. They’ve also used other techniques to stay incognito, such as DNS tunneling. This technique involves the manipulation of an internet domain name system to bypass firewalls. Sentinel Labs reported that over time, Aoqin Dragon slowly executed their fake removable disc technique, which was done to keep their malware from being detected and removed by security products.
Researchers expect Aoqin Dragon to continue to conduct cyber espionage operations. They also expect the threat group to continue to advance their tradecraft and their methods for evading detection.
financially motivated threat groups vs. cyber espionage threat groups
Cyber Espionage Threat Groups
Unlike ransomware groups, cyberespionage threat actors are not typically seeking financial gain. Their purpose is to glean sensitive and classified data, trade secrets, and other forms of intellectual property that can be used politically. The attacks can be motivated by money, but this is not the case for cyber espionage groups most of the time.
Cyber Espionage groups generally target large corporations, government agencies, academic institution, and other organizations that have valuable intellectual property and technical data that can be used by another organization or government. Here is a list of assets cyber espionage threat actors attempt to access:
- Military intelligence
- Salaries (bonus structures and other information related to finances)
- Academic research
- Intellectual property (blueprints or formulas)
- Research and Development data and activity
- Political strategies, affiliations, and communications
- Client or customer lists and payment structures
- Business goals and strategic plans
By obtaining access to the aforementioned list, threat actors can target organizations and wage a war between individuals, such as political leaders and government officials, as well as business executives. Most cyber espionage activity is placed under the advanced persistent threat (APT) umbrella. APTs are sophisticated and they generally establish an undetected presence on networks and systems so they can gather the information they need. Like Aoqin Dragon, cyber espionage APTs use social engineering to gather information from their target. Social engineering exploits human emotions (curiosity, fear, empathy, etc.) to trick victims into clicking on links or downloading malware.
Financially Motivated Threat Groups
Ransomware gangs and data extortion groups fall under the category for financially motivated attacks. They are motivated solely by money and their operations move much quicker than cyber espionage. These individuals operate like a business, going after a variety of industries such as healthcare, agriculture, government, education, and engineering. These threat groups usually do one of two things during their attacks: encrypt data and hold it ransom in exchange for a decryption key or exfiltrate data and threaten to leak it if a ransom is not paid.
Ransomware gangs like Conti and Hive are known for deploying ransomware into their victim’s networks and systems. While they may go undetected at first, they don’t stay that way for long and will expose themselves once they have encrypted their victims’ data or gathered the information they need. Once the ransom is paid, they will provide their victims with the decryption key or will keep their sensitive information from being exposed – although they don’t always keep their word.
How Avertium is Protecting Our CUSTOMERS
Threat actors like Aoqin Dragon can gain unlimited access to networks and systems by remaining incognito for years, furthering reconnaissance. Avertium is here to keep your organization safe and to mitigate any attacks caused by APTs like Aoqin Dragon:
- To identify the source of your breach and the scope that it reached; you’ll want to include Avertium’s DFIR (Digital Forensics and Incident Response) services in your protection plan. We offer DFIR to mitigate damage from a successful breach. This service is provided as an on-demand crisis response service, as well as a retainer-based program.
- Implement XDR as a prevention method. Our XDR is a combination of monitoring software like LogRhythm, Microsoft Azure Sentinel, or AlienVault, combined with endpoint protection such as SentinelOne. XDR platforms enable cybersecurity through a technology focus by collecting, correlating, and analyzing event data from any source on the network. This includes endpoints, applications, network devices, and user interactions.
- MDR provides an in-depth investigation into potential threats to an organization’s network. Avertium’s risk-based approach to managed security delivers the right combination of technology, field-validated threat intelligence, and resource empowerment to reduce complexity, streamline operations, and enhance cybersecurity resilience. If you need a more advanced security solution, MDR is the next step. MDR is an outsourced security control solution that includes the elements of EDR, enhanced with a range of fundamental security processes.
- Avertium offers VMaaS to provide a deeper understanding and control over organizational information security risks. If your enterprise is facing challenges with the scope, resources, or skills required to implement a vulnerability management program with your team, outsourced solutions can help you bridge the gap.
- Avertium offers user awareness training through KnowBe4. The service also Incident Response Table-Top exercises (IR TTX) and Core Security Document development, as well as a comprehensive new-school approach that integrates baseline testing using mock attacks.
Avertium’s Recommendations
- Cybersecurity Education: Educate your employees on cyber security preparedness and the dangers of opening potentially malicious documents. Annual or quarterly training modules can help prevent threat actors from tricking employees into opening malicious email attachments.
- Risk Analysis: Prevent an attack by ensuring your organization has a detailed defense strategy based on a risk analysis approach.
- Tabletop Exercises: Have a good cyber incident response plan in place that has been tested with tabletop exercises.
- Security Review: Be sure to review your cyber incident response plan and improve it every time it’s tested on real cyber threats.
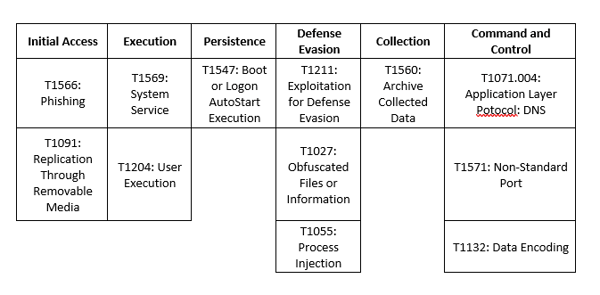
MITRE Map
Indicators of Compromise (IoCs)
Mongall Domains
- back[.]satunusa[.]org
- baomoi[.]vnptnet[.]info
- bbw[.]fushing[.]org
- bca[.]zdungk[.]com
- bkav[.]manlish[.]net
- bkav[.]welikejack[.]com
- bkavonline[.]vnptnet[.]info
- bush2015[.]net
- cl[.]weststations[.]com
- cloundvietnam[.]com
- cpt[.]vnptnet[.]inf
- dns[.]lioncity[.]top
- dns[.]satunusa[.]org
- dns[.]zdungk[.]com
- ds[.]vdcvn[.]com
- ds[.]xrayccc[.]top
- facebookmap[.]top
- fbcl2[.]adsoft[.]name
- fbcl2[.]softad[.]net
- flower2[.]yyppmm[.]com
- game[.]vietnamflash[.]com
- hello[.]bluesky1234[.]com
- ipad[.]vnptnet[.]info
- ks[.]manlish[.]net
- lepad[.]fushing[.]org
- lllyyy[.]adsoft[.]name
- lucky[.]manlish[.]net
- ma550[.]adsoft[.]name
- ma550[.]softad[.]net
- mail[.]comnnet[.]net
- mail[.]tiger1234[.]com
- mail[.]vdcvn[.]com
- mass[.]longvn[.]net
- mcafee[.]bluesky1234[.]com
- media[.]vietnamflash[.]com
- mil[.]dungk[.]com
- mil[.]zdungk[.]com
- mmchj2[.]telorg[.]net
- mmslsh[.]tiger1234[.]com
- mobile[.]vdcvn[.]com
- moit[.]longvn[.]net
- movie[.]vdcvn[.]com
- news[.]philstar2[.]com
- news[.]welikejack[.]com
- npt[.]vnptnet[.]info
- ns[.]fushing[.]org
- nycl[.]neverdropd[.]com
- phcl[.]followag[.]org
- phcl[.]neverdropd[.]com
- pna[.]adsoft[.]name
- pnavy3[.]neverdropd[.]com
- sky[.]bush2015[.]net
- sky[.]vietnamflash[.]com
- tcv[.]tiger1234[.]com
- telecom[.]longvn[.]net
- telecom[.]manlish[.]net
- th-y3[.]adsoft[.]name
- th550[.]adsoft[.]name
- th550[.]softad[.]net
- three[.]welikejack[.]com
- thy3[.]softad[.]net
- vdcvn[.]com
- video[.]philstar2[.]com
- viet[.]vnptnet[.]info
- viet[.]zdungk[.]com
- vietnam[.]vnptnet[.]info
- vietnamflash[.]com
- vnet[.]fushing[.]org
- vnn[.]bush2015[.]net
- vnn[.]phung123[.]com
- webmail[.]philstar2[.]com
- www[.]bush2015[.]net
- yok[.]fushing[.]org
- yote[.]dellyou[.]com
- zing[.]vietnamflash[.]com
- zingme[.]dungk[.]com
- zingme[.]longvn[.]net
- zw[.]dinhk[.]net
- zw[.]phung123[.]com
Mongall C2 Servers: IP Addresses
- 10[.]100[.]0[.]34 (Internal IPs)
- 10[.]100[.]27[.]4 (Internal IPs)
- 172[.]111[.]192[.]233
- 59[.]188[.]234[.]233
- 64[.]27[.]4[.]157
- 64[.]27[.]4[.]19
- 67[.]210[.]114[.]99
Mongall Hashes
- a96caf60c50e7c589fefc62d89c27e6ac60cdf2c
- ccccf5e131abe74066b75e8a49c82373414f5d95
- 5408f6281aa32c02e17003e0118de82dfa82081e
- a37bb5caa546bc4d58e264fe55e9e9155f36d9d8
- 779fa3ebfa1af49419be4ae80b54096b5abedbf9
- 2748cbafc7f3c9a3752dc1446ee838c5c5506b23
- eaf9fbddf357bdcf9a5c7f4ad2b9e5f81f96b6a1
- 6380b7cf83722044558512202634c2ef4bc5e786
- 31cddf48ee612d1d5ba2a7929750dee0408b19c7
- 677cdfd2d686f7148a49897b9f6c377c7d26c5e0
- 911e4e76f3e56c9eccf57e2da7350ce18b488a7f
- c6b061b0a4d725357d5753c48dda8f272c0cf2ae
- dc7436e9bc83deea01e44db3d5dac0eec566b28c
- 94b486d650f5ca1761ee79cdff36544c0cc07fe9
- 1bef29f2ab38f0219b1dceb5d37b9bda0e9288f5
- 01fb97fbb0b864c62d3a59a10e785592bb26c716
- 03a5bee9e9686c18a4f673aadd1e279f53e1c68f
- 1270af048aadcc7a9fc0fd4a82b9864ace0b6fb6
- e2e7b7ba7cbd96c9eec1bcb16639dec87d06b8dd
- ed441509380e72961b263d07409ee5987820d7ae
- 45d156d2b696338bf557a509eaaca9d4bc34ba4a
- bac8248bb6f4a303d5c4e4ce0cd410dc447951ea
- 15350967659da8a57e4d8e19368d785776268a0e
- 008dd0c161a0d4042bdeb1f1bd62039a9224b7f0
- db4b1507f8902c95d10b1ed601b56e03499718c
- f5cc1819c4792df19f8154c88ff466b725a695f6
- 86e04e6a149fd818869721df9712789d04c84182
- a64fbd2e5e47fea174dd739053eec021e13667f8
- d36c3d857d23c89bbdfefd6c395516a68ffa6b82
- d15947ba6d65a22dcf8eff917678e2b386c5f662
- 5fa90cb49d0829410505b78d4037461b67935371
- 9a9aff027ad62323bdcca34f898dbcefe4df629b
- 9cd48fddd536f2c2e28f622170e2527a9ca84ee0
- 19bd1573564fe2c73e08dce4c4ad08b2161e0556
- a1d0c96db49f1eef7fd71cbed13f2fb6d521ab6a
- 936748b63b1c9775cef17c8cdbba9f45ceba3389
- 46d54a3de7e139b191b999118972ea394c48a97f
- 4786066b29066986b35db0bfce1f58ec8051ba6b
- b1d84d33d37526c042f5d241b94f8b77e1aa8b98
- 7bb500f0c17014dd0d5e7179c52134b849982465
- d1d3219006fdfd4654c52e84051fb2551de2373a
- 0ffa5e49f17bc722c37a08041e6d80ee073d0d8f
- dceecf543f15344b875418ad086d9706bfef1447
- fa177d9bd5334d8e4d981a5a9ab09b41141e9dcc
- 07aab5761d56159622970a0213038a62d53743c2
- d83dde58a510bdd3243038b1f1873e7da3114bcf
- a0da713ee28a17371691aaa901149745f965eb90
- c5b644a33fb027900111d5d4912e28b7dcce88ff
- db5437fec902cc1bcbad4bef4d055651e9926a89
- ff42d2819c1a73e0032df6c430f0c67582adba74
- 3b2d858c682342127769202a806e8ab7f1e43173
- c08bf3ae164e8e9d1d9f51dffcbe7039dce4c643
- f41d1966285667e74a419e404f43c7693f3b0383
- 3ccb546f12d9ed6ad7736c581e7a00c86592e5dd
- 904556fed1aa00250eee1a69d68f78c4ce66a8dc
- bd9dec094c349a5b7d9690ab1e58877a9f001acf
- 87e6ab15f16b1ed3db9cc63d738bf9d0b739a220
- f8fc307f7d53b2991dea3805f1eebf3417a7082b
- ece4c9fc15acd96909deab3ff207359037012fd5
- 7fdfec70c8daae07a29a2c9077062e6636029806
- 17d548b2dca6625271649dc93293fdf998813b21
- 6a7ac7ebab65c7d8394d187aafb5d8b3f7994d21
- fee78ccadb727797ddf51d76ff43bf459bfa8e89
- 4bf58addcd01ab6eebca355a5dda819d78631b44
- fd9f0e40bf4f7f975385f58d120d07cdd91df330
- a76c21af39b0cc3f7557de645e4aaeccaf244c1e
- 7ff9511ebe6f95fc73bc0fa94458f18ee0fb395d
- 97c5003e5eacbc8f5258b88493f148f148305df5
- f92edf91407ab2c22f2246a028e81cf1c99ce89e
- d932f7d11f8681a635e70849b9c8181406675930
- b0b13e9445b94ed2b69448044fbfd569589f8586
- b194b26de8c1f31b0c075ceb0ab1e80d9c110efc
- df26b43439c02b8cd4bff78b0ea01035df221f68
- 60bd17aa94531b89f80d7158458494b279be62b4
- 33abee43acfe25b295a4b2accfaf33e2aaf2b879
- c87a8492de90a415d1fbe32becbafef5d5d8eabb
- 68b731fcb6d1a88adf30af079bea8efdb0c2ee6e
- cf7c5d32d73fb90475e58597044e7f20f77728a
- 1ab85632e63a1e4944128619a9dafb6405558863
- 1f0d3c8e373c529a0c3e0172f5f0fb37e1cdd290
- f69050c8bdcbb1b5f16ca069e231b66d52c0a652
- 6ff079e886cbc6be0f745b044ee324120de3dab2
- 8c90aa0a521992d57035f00d3fbdfd0fa7067574
- 5e32a5a5ca270f69a3bf4e7dd3889b0d10d90ec2
- 0db3626a8800d421c8b16298916a7655a73460de
- 01751ea8ac4963e40c42acfa465936cbe3eed6c2
- 6b3032252b1f883cbe817fd846181f596260935b
- 741168d01e7ea8a2079ee108c32893da7662bb63
- b9cc2f913c4d2d9a602f2c05594af0148ab1fb03
- c7e6f7131eb71d2f0e7120b11abfaa3a50e2b19e
- ae0fdf2ab73e06c0cd04cf79b9c5a9283815bacb
- 67f2cd4f1a60e1b940494812cdf38cd7c0290050
- aca99cfd074ed79c13f6349bd016d5b65e73c324
- ba7142e016d0e5920249f2e6d0f92c4fadfc7244
- 98a907b18095672f92407d92bfd600d9a0037f93
- afaffef28d8b6983ada574a4319d16c688c2cb38
- 98e2afed718649a38d9daf10ac792415081191fe
- bc32e66a6346907f4417dc4a81d569368594f4ae
- 8d569ac92f1ca8437397765d351302c75c20525b
- 5c32a4e4c3d69a95e00a981a67f5ae36c7aae05e
- d807a2c01686132f5f1c359c30c9c5a7ab4d31c2
- 155db617c6cf661507c24df2d248645427de492c
- 7e6870a527ffb5235ee2b4235cd8e74eb0f69d0e
- 2f0ea0a0a2ffe204ec78a0bdf1f5dee372ec4d42
- 041d9b089a9c8408c99073c9953ab59bd3447878
- 1edada1bb87b35458d7e059b5ca78c70cd64fd3f
- 4033c313497c898001a9f06a35318bb8ed621dfb
- 683a3e0d464c7dcbe5f959f8fd82d738f4039b38
- 97d30b904e7b521a9b7a629fdd1e0ae8a5bf8238
- 53525da91e87326cea124955cbc075f8e8f3276b
- 73ac8512035536ffa2531ee9580ef21085511dc5
- 28b8843e3e2a385da312fd937752cd5b529f9483
- cd59c14d46daaf874dc720be140129d94ee68e39
SUPPORTING DOCUMENTATION
CVE - CVE-2010-3333 (mitre.org)
Aoqin Dragon APT targets entities in Southeast Asia and AustraliaSecurity Affairs
What is Cyber Espionage? – CrowdStrike
Chinese 'Aoqin Dragon' gang runs ten-year espionage spree • The Register
This hacking group quietly spied on their targets for 10 years | ZDNet
Chinese hacking group Aoqin Dragon quietly spied orgs for a decade (bleepingcomputer.com)
China-linked APT Flew Under Radar for Decade | Threatpost
Chinese-Linked APT Spying on Organizations for 10 Years (bankinfosecurity.com)
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.
Related Resource: An In-Depth Look at Iranian APT "MuddyWater"