- WHY AVERTIUM?
-
-
Why Avertium?
Context over chaos. Disconnected technologies, siloed data, and reactive processes can only get you so far. Protecting businesses in today’s threat landscape demands more than a set of security tools – it requires context.
That's where Avertium comes in
-
Considering Microsoft?
Avertium Named Microsoft Security Solutions PartnerAvertium’s managed services for Microsoft Security Solutions is delivered through the company’s premium service: Fusion MXDR. Fusion MXDR includes 24x7 monitoring and management of Defender for Endpoint and Sentinel, threat intelligence, attack surface
monitoring, and vulnerability management for Microsoft Security customers. -
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- SOLUTIONS
-
-
Governance, Risk, + Compliance
GRC with context – not complexity. -
Attack Surface Management
No more blind spots, weak links, or fire drills. -
Threat Detection + Response
Detect, adapt, and attack with context. -
Microsoft Security Solutions
End-to-end support from strategy to daily operations to maximize your Microsoft Security.
-
-
- COMPANY
-
-
About Us
Security. It’s in our DNA. It’s elemental, foundational. Something that an always-on, everything’s-IoT-connected world depends on.
Helping mid-to-enterprise organizations protect assets and manage risk is our only business. Our mission is to make our customers’ world a safer place so that they may thrive in an always-on, connected world.
-
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- PARTNERS
-
-
Our Partners
Best-in-class technology from our partners... backed by service excellence from Avertium.
-
Partner Opportunity Registration
Interested in becoming a partner?
With Avertium's deal registration, partners can efficiently and confidently connect with Avertium on opportunities to protect your deals.
-
Latest Avertium Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- NEWS & RESOURCES
-
-
News & Resources
Dive into our resource hub and explore top
cybersecurity topics along with what we do
and what we can do for you. -
Latest Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- CONTACT
Everything You Need to Know About the Data Extortion Group RansomHouse
RANSOMHOUSE Executive Summary
RansomHouse is a fairly new operation that focuses on breaching networks via vulnerabilities to steal their targets’ data. Although new threat actors emerge daily, there is something about RansomHouse that is different from what threat researchers are used to seeing. Despite their name, RansomHouse is not a ransomware operation but a data-extortion cybercrime operation.
Instead of encrypting systems and deploying ransomware, RansomHouse eliminates the encryption phase and simply requests payment for the data they steal. What’s more interesting is that the threat actors don’t take responsibility for their attacks, they instead point the finger at organizations (their victims) not having good security posture. Let’s take a look at RansomHouse attacks, their tactics and techniques, and how organizations can protect themselves from this kind of threat actor.
ransomhouse attacks
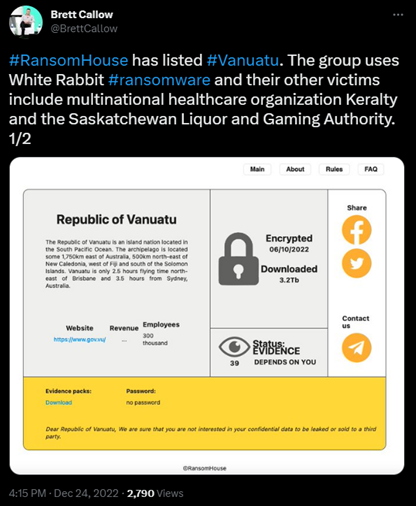
RansomHouse is thought to have debuted in December 2021, with their first victim allegedly being the Saskatchewan Liquor and Gaming Authority. The origins of RansomHouse are murky but Brett Callow of Emsisoft spoke with a representative of RansomHouse who spoke English with an Eastern European accent.
Image 1: White Rabbit
Source: Twitter
After the attack on the Saskatchewan Liquor and Gaming Authority, the group listed the organization on their extortion site, along with three other victims, including the Swedish rail company Dellner Couplers, the German airline support service provider AHS group, and Jefferson Credit Union.
Image 2: RansomHouse Naming Victim on Extortion Site
Source: Bleeping Computer
Advanced Micro Devices (AMD)
In June 2022, RansomHouse compromised Advanced Micro Devices (AMD) – a multinational semiconductor manufacturer. The threat actors stole 450GB of financial data and research, including a CSV file containing a list of over 70k devices belonging to AMD’s internal network.
Initially, AMD claimed that RansomHouse stole their data on January 5, 2022. However, the threat actors denied the claims and stated that January 5, 2022, is when the threat actors lost access to AMD’s network. A spokesperson from RansomHouse stated that access was provided by a partner organization, implying that the group used an access broker or corporate insiders to gain access to AMD’s network.
During the same month, AMD was added to the RansomHouse extortion site, not because they didn’t pay a demanded ransom, but because RansomHouse finds ransom negotiations time consuming. It appears the threat actors believe selling data to other threat actors is more profitable than attempting to negotiate a ransom payment.
KERALTY
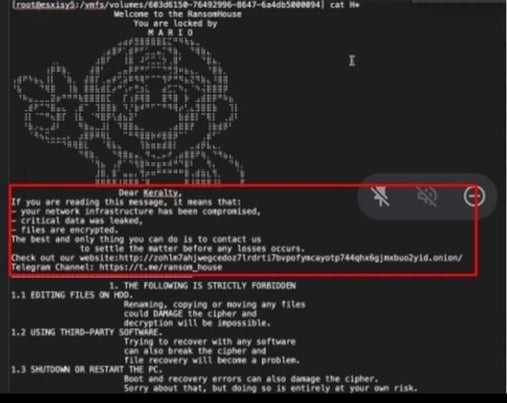
By November 2022, Keralty, a multinational healthcare organization, was breached by RansomHouse. The attack disrupted the organization’s website and operations, as well as the operations of its subsidiaries. The Columbian healthcare provider operates an international network of 12 hospitals and 371 medical centers in the U.S, Spain, Latin America, and Asia. The group provides healthcare for over 6 million patients.
The attack on Keralty impacted the organization’s IT operations, scheduling of medical appointments, and the functionality of various websites. Patients were seen waiting in line for over twelve hours to receive medical care, some even fainting due to lack of medical attention.
Image 3: RansomHouse Note for Keralty After Stealing Data
Source: Bleeping Computer
VANUATU
In December 2022, one day before Christmas, RansomHouse added the government of Vanuatu to their leak site. Vanuatu is a small archipelago of the South Pacific Ocean. As a result, the threat actors exfiltrated 3.2TB of data and crippled Vanuatu’s government. The attack also disabled websites of the island’s parliament, police, and prime minister’s office – taking down the database of hospitals and schools. The RansomHouse attack brought Vanuatu to a standstill and the island still has not fully recovered.
TACTICS & TECHNIQUES
Many of RansomHouse’s tactics are similar to the data extortion group, Lapsus$. Like Lapsus$, some have classified RansomHouse as a ransomware group. This is a mistake due to both groups not encrypting data on target networks. As previously stated, researchers have yet to confirm RansomHouse’s origins. White Rabbit’s (a ransomware strain with possible ties to the financial crime ring, FIN8) ransom notes were among the first to mention RansomHouse. However, RansomHouse insists that they only partnered with White Rabbit. However, Brett Callow suspects that RansomHouse is being operated by the same threat actors who operate White Rabbit.
As previously stated, RansomHouse campaigns focus on data exfiltration without encryption modules. Their goal is financial gain, and the threat actors operate manually, focusing on one victim at a time. RansomHouse keeps their actions simple and precise, investing resources in data exfiltration and vulnerability research. This model makes their attacks less complex than encrypting their victim’s assets.
If a victim refuses to pay the ransom, RansomHouse will shame them by publishing a portion of the victim’s data on their site. The public shaming casts a negative light on the breached organization with customers and shareholders watching. Within the site, RansomHouse lists URLs to media posts for victims who are actively being extorted. They do this to highlight the publicity of their attacks as a secondary extortion method. If victims still don’t pay the demanded ransom, their data is offered for sale on the dark web. If cyber criminals are not interested in buying the stolen data, then all the data is published on the RansomHouse Tor site.
RansomHouse also has a Telegram channel where they have been seen communicating with other threat actors on other channels. According to an analysis by Cyberint, the conversations are professional and “pro-freedom”. They also state in their channel that they don’t want to “mix business with politics or work with radical hacktivists/espionage groups.”
The threat actors also stated that many organizations refuse to invest the money required to secure their infrastructures and they don’t institute enough bug bounty plans. These statements led Cyberint to believe that RansomHouse is being run by disgruntled red-team pen-testers who are not happy with organizations’ low bounty payments and poor cyber security hygiene. Also, RansomHouse may have a connection to Lapsus$, as the group’s activities were seen advertised on the Lapsus$ Telegram channel.
While RansomHouse is clearly motivated by money, the group has also criticized AMD's poor security practices. After attacking AMD, the group stated that it was shameful that a high-profile technological entity like AMD allowed its employees to use weak credentials. This reinforces Cyberint’s belief that RansomHouse is a group of disgruntled white hat hackers looking to draw attention to its victims' lax security practices.
NEGOTIATIONS
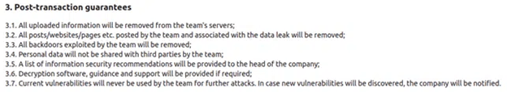
After an attack, RansomHouse conducts negotiations with their victims. They try to help the organization protect itself from future attacks by providing a full report on how they were breached and what vulnerabilities were exploited. Furthermore, they promise to delete stolen data, as well as evidence of the breached organization being on the group’s victims list. RansomHouse will also delete backdoors on the victim’s network.
Image 4: RansomHouse Commitment List
Source: Cyberint
defense
Until extortion attacks like data extortion become too difficult or extensive carry out, they won’t disappear from the cyber threat landscape. While it may be tempting to dismiss threat groups like RansomHouse due to their unsophisticated tactics, any disruption to an organization’s operations can have serious consequences.
When it comes to data extortion, backups are still important, but they won’t be enough to keep your organization from losing valuable data. Due to RansomHouse bypassing file encryption and focusing on data exfiltration, your security focus should be based on cyber security best practices and keeping threat actors out of your systems and networks.
Of course, backups are necessary and there will never be a time when they are not needed but focusing on keeping intruders out of your cyber environment in the first place will give you more leverage over data extortion groups. Implementing an intrusion prevention system (IPS) is a cyber security best practice that will help keep your organization safe.
WHAT IS AN IPS?
An IPS is an intrusion prevention system that offers protection for networks by detecting and preventing threats. The system constantly monitors the network for intrusion prevention mechanisms and also checks for potential malicious events. Once incidents are found, the IPS reports those incidents to system administrators and takes measures to prevent possible attacks.
How does an IPS prevent attacks from succeeding? The IPS prevents attacks by using different response strategies including altering the security environment, stopping an attack itself, or altering the content of an attack.
The IPS operates by scanning traffic on a network, avoiding different risks such as:
- Risk of viruses
- Risk of worms
- Risk of DDoS (Distributed Denial of Service) assault
- Risk of assault by DoS (Denial of Service)
- Risk of diverse types of vulnerabilities
Also, the IPS inspects any packet that passes through a network via real-time packet inspection. If a potential threat is observed, the IPS does one of the following:
- Reprograms or reconfigures the firewall to stop a similar attack from happening in the future.
- Deletes malicious content or replaces malicious content that persists on networks after an attack.
- Terminates abused TCP sessions and blocks the offending source IP address or user account from accessing other network properties or target hosts.
If your organization implements an IPS strategy, there will be several benefits, including:
- Your organization will reduce the risk of security incidents.
- An IPS provides complex security for threats.
- An IPS will notify system administrators immediately when suspicious behavior is observed.
- An IPS reduces network maintenance for IT personnel
- An IPS prevents threats, like DoS attacks, DDoS attacks, zero-day attacks, and brute-force attacks.
avertium's recommendations
- Implement MFA where possible to authenticate corporate accounts, with admin accounts being cross platformed and MFA enforced.
- Have a robust crisis management and incidence response plan in place.
- All internet-facing security and remote access appliances should be updated.
- Don’t store unprotected credentials in files and scripts on shared locations.
- Admin accounts should only be used for administrative purposes and should never be connected to the network or to browse the internet.
- Implement cyber security best practices against malware, such as patching, updating anti-virus software, whitelisting where feasible, and maintaining strict network egress policies.
- Disable RDP on external-facing devices.
- Maintain a robust and routine user-awareness training regimen for users of all systems.
- Threat actors exploit older systems with existing vulnerabilities. Organizations should patch infrastructure to the highest available level.
- Having a strong corporate password policy (that includes industry standards for password length and complexity) will help keep your organization safe.
how avertium is protecting our customers
Avertium has advanced services that can help keep your organization safe:
- Avertium recommends utilizing our service for DFIR (Digital Forensics and Incident Response) to help you rapidly assess, contain, eradicate, and recover from a security incident like a malware attack.
- MDR provides an in-depth investigation into potential threats on an organization’s network. Avertium’s risk-based approach to managed security delivers the right combination of technology, field-validated threat intelligence, and resource empowerment to reduce complexity, streamline operations, and enhance cybersecurity resilience. If you need a more advanced security solution, MDR is the next step. MDR is an outsourced security control solution that includes the elements of EDR, enhanced with a range of fundamental security processes.
- Avertium offers security consulting services to develop robust internal security policies.
- Expanding endpoints, cloud computing environments, and accelerated digital transformation have decimated the perimeter in an ever-expanding attack surface. Avertium offers Attack Surface Management, so you’ll have no more blind spots, weak links, or fire drills.
- Fusion MXDR is the first MDR offering that fuses together all aspects of security operations into a living, breathing, threat-resistant XDR solution. By fusing insights from threat intelligence, security assessments, and vulnerability management into our MDR approach, Fusion MXDR offers a more informed, robust, and cost-effective approach to cybersecurity – one that is greater than the sum of its parts.
- Avertium offers user awareness training through KnowBe4. The service also includes Incident Response Table-Top exercises (IR TTX) and Core Security Document development, as well as a comprehensive new-school approach that integrates baseline testing using mock attacks.
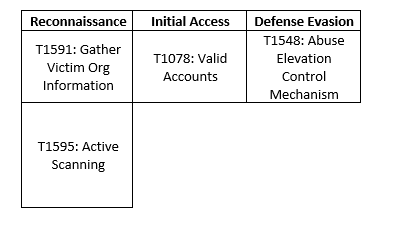
MITRE MAP
INDICATORS OF COMPROMISE (IoCs)
- hxxp://zohlm7ahjwegcedoz7lrdrti7bvpofymcayotp744qhx6gjmxbuo2yid[.]onion/
- zohlm7ahjwegcedoz7lrdrti7bvpofymcayotp744qhx6gjmxbuo2yid[.]onion
SUPPORTING DOCUMENTATION
The New RansomHouse on The Block (cyberint.com)
New RansomHouse group sets up extortion market, adds first victims (bleepingcomputer.com)
Intelligence-Report_28June_RansomHouse.pdf (secrutiny.com)
RansomHouse - AlienVault - Open Threat Exchange
Pacific island nation of Vanuatu has been knocked offline for more than a month : NPR
Vanuatu ransomware attack claimed by RansomHouse (databreaches.net)
Keralty ransomware attack impacts Colombia's health care system (bleepingcomputer.com)
Cyber Security Incident at SLGA | News and Media | Government of Saskatchewan
Vanuatu island hit by ransom attack, cripples government (databreaches.net)
Brazen, Unsophisticated and Illogical: Understanding the LAPSUS$ Extortion Group - Blog | Tenable®
Novel RansomHouse cybercrime operation detailed | SC Media (scmagazine.com)
Threat profile: RansomHouse makes extortion work without ransomware (malwarebytes.com)
An In-Depth Look at the Data Extortion Group, Karakurt (avertium.com)
RansomHouse attack disrupts multinational Colombian health provider | SC Media (scmagazine.com)
New Ransomware Group: RansomHouse - Is it Real or Fake? | Webz.io
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.