- WHY AVERTIUM?
-
-
Why Avertium?
Context over chaos. Disconnected technologies, siloed data, and reactive processes can only get you so far. Protecting businesses in today’s threat landscape demands more than a set of security tools – it requires context.
That's where Avertium comes in
-
Considering Microsoft?
Avertium Named Microsoft Security Solutions PartnerAvertium’s managed services for Microsoft Security Solutions is delivered through the company’s premium service: Fusion MXDR. Fusion MXDR includes 24x7 monitoring and management of Defender for Endpoint and Sentinel, threat intelligence, attack surface
monitoring, and vulnerability management for Microsoft Security customers. -
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- SOLUTIONS
-
-
Governance, Risk, + Compliance
GRC with context – not complexity. -
Attack Surface Management
No more blind spots, weak links, or fire drills. -
Threat Detection + Response
Detect, adapt, and attack with context. -
Microsoft Security Solutions
End-to-end support from strategy to daily operations to maximize your Microsoft Security.
-
-
- COMPANY
-
-
About Us
Security. It’s in our DNA. It’s elemental, foundational. Something that an always-on, everything’s-IoT-connected world depends on.
Helping mid-to-enterprise organizations protect assets and manage risk is our only business. Our mission is to make our customers’ world a safer place so that they may thrive in an always-on, connected world.
-
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- PARTNERS
-
-
Our Partners
Best-in-class technology from our partners... backed by service excellence from Avertium.
-
Partner Opportunity Registration
Interested in becoming a partner?
With Avertium's deal registration, partners can efficiently and confidently connect with Avertium on opportunities to protect your deals.
-
Latest Avertium Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- NEWS & RESOURCES
-
-
News & Resources
Dive into our resource hub and explore top
cybersecurity topics along with what we do
and what we can do for you. -
Latest Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- CONTACT
You are the Weakest Link: Assessing Vulnerabilities and Solutions for Cybersecurity in Agriculture
executive summary
In February 2023, Dole Food Co., a major produce company, temporarily closed its North American production plants and halted food shipments to grocery stores due to a ransomware attack. This attack affected roughly 50% of Dole's legacy company servers and 25% of its end user computers, leading to a shortage of popular items like Dole's salad kits.
A month later, it was revealed through a Securities and Exchange Commission (SEC) filing that the ransomware attack also disrupted their Chilean and fresh vegetables business, resulting in approximately $5.7 million in related costs. While all affected servers and computers were eventually restored, the attack led to unauthorized access to employee information. By May 2023, Dole had incurred $10.5 million in direct costs from the attack, with no expectation of recovering those expenses.
The Dole attack highlights how threat actors are increasingly targeting agricultural-based organizations that depend on farmers for food production. As technology plays a larger role in this sector, it's time to recognize its significance and the potential threats the sector faces. Let's examine vulnerabilities in agriculture (focusing on farming and food supply-chain) and discuss solutions for a sector that is unaccustomed to tech-related concerns.
tir snapshot
- In 2021, JBS, a U.S. food processing company, suffered a cyber-attack just before Memorial Day. The attack affected JBS's IT systems in North American and Australia, demanding an $11 million bitcoin ransom for decryption.
- In 2021, BlackMatter responsible for attacks on two agricultural companies, New Cooperative and Crystal Valley. New Cooperative, an Iowa-based farm service provider, fell victim to a ransomware attack on September 20, 2021 with BlackMatter demanding a $5.9 million ransom.
- Schreiber Foods also experienced a similar incident in 2021 when their systems were compromised by a ransomware attack. The ransomware gang demanded $2.5 million in ransom from the company.
- In 2020, Taylor Farms, which had an estimated annual revenue of $611.13 million USD in 2018, became a target of the infamous REvil ransomware group. REvil threatened to release stolen data unless Taylor Farms complied with their ransom demands.
- Ransomware attacks on agriculture-based businesses result in substantial financial losses due to ransom payments, decreased productivity, and remediation expenses.
- In an exclusive interview with Avertium, Dr. George Grispos highlighted that the significance of cybersecurity in agriculture only became apparent after 2010, coinciding with the emergence of cloud computing, which heightened awareness of critical infrastructure cybersecurity.
- Grispos suggests that the shift from labor-intensive, manual processes to technology-driven solutions might have skipped a crucial step in education.
- However, there are some clear and practical recommendations for addressing cyber risks in agriculture as it pertains to farming and food-supply.
attacks on agricultural-based businesses
JBS
In 2021, the US-based food processing company, JBS, fell victim to a cyber attack just before Memorial Day weekend. The attack, orchestrated by the REvil ransomware group, impacted JBS's North American and Australian IT systems, infecting them with malware and demanding an $11 million bitcoin ransom for decryption.
Additionally, the U.S. subsidiary of Brazilian company JBS SA suspended cattle slaughtering in all of its U.S. plants for a day in reaction to the cyber attack. This move aimed to prevent potential disruptions in food supply chains and additional inflation of already soaring food prices.
In response, JBS had to temporarily take parts of their systems offline and paid the ransom to avoid further disruptions. They were able to maintain operations using backups but incurred an $11 million cost due to the ransom payment. While this prevented the malware from spreading, there was no assurance that REvil would not target them again.
JBS's American division and Pilgrims Pride Corp. (PPC.O), a U.S. chicken company largely owned by JBS, experienced a disruption equivalent to less than a day's worth of food production. JBS meat plants are responsible for nearly a quarter of the beef production in the U.S.
NEW COOPERATIVE AND CRYSTAL VALLEY
In 2021, the Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau of Investigation (FBI), and the National Security Agency (NSA) identified the ransomware threat actor BlackMatter as responsible for attacks on two agricultural companies, New Cooperative and Crystal Valley. New Cooperative, an Iowa-based farm service provider, fell victim to a ransomware attack on September 20, 2021 with BlackMatter demanding a $5.9 million ransom.
Crystal Valley, located in Minnesota, was targeted two days later. These attacks occurred at a critical time when farmers were gearing up for their harvests. Threat actors might view cooperatives as attractive targets, given their critical, time-sensitive role in agricultural production and their willingness to pay ransoms.
SCHREIBER FOODS
Aside from the cooperatives falling victim to ransomware attacks, Schreiber Foods also experienced a similar incident in 2021 when their systems were compromised by a ransomware attack. This affected all of their facilities, including plants and distribution centers. Schreiber Foods primarily specializes in yogurt, processed and natural cheese, and cream cheese production. The ransomware gang demanded $2.5 million in ransom from the company.
Schreiber had to inform milk transporters about computer system problems, which resulted in the transporters diverting the milk elsewhere. The disruption affected the entire milk supply chain since Schreiber relies on various digital systems and computers to oversee milk processing.
An attack disrupting operations in a protein or dairy facility can quickly result in product spoilage, setting off a chain reaction that impacts farms by preventing the processing of animals. Fortunately, Schreiber Foods had backups and an incident response team that immediately sprang into action. The company is one of the largest milk processors in the state of Wisconsin.
U.S. FARM - TAYLOR FARMS
As per Yelisey Bohuslavskiy, the Chief Research Officer of Avertium's intelligence partner, RedSense, Taylor Farms became a target of the infamous REvil in 2020. This company had an estimated annual revenue of $611.13 million USD in 2018. The threat actors posted certain company files on their data leak site, alleging that they had acquired samples of customer and employee data.
Image 1: Sample of Data Posted by REvil
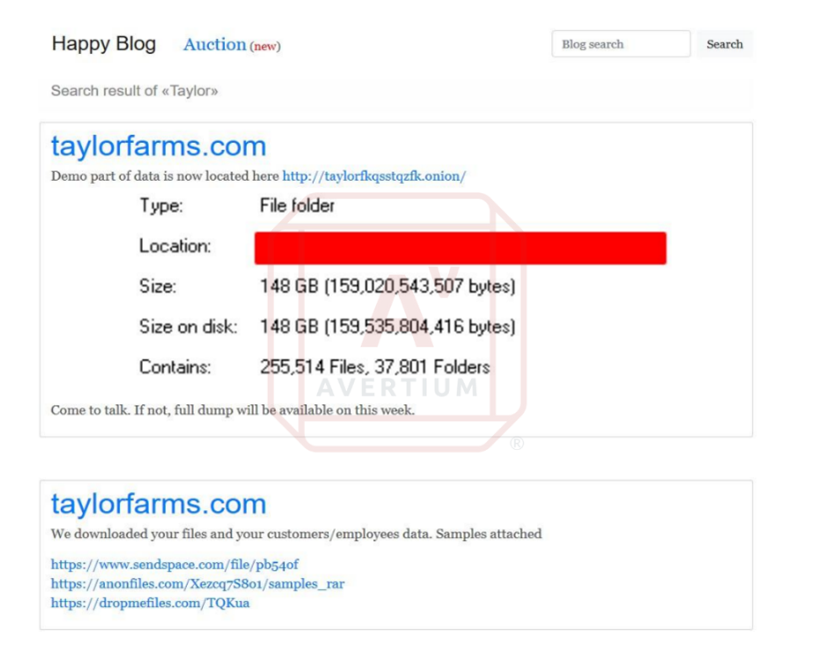
REvil threatened to release all the data unless Taylor Farms complied with their ransom demands. The company is globally renowned as the largest processor of fresh-cut vegetables and salads. Taylor Farms distributes its products through intermediaries like Golden State Foods to numerous California school districts and popular chain restaurants, including McDonald's and Chipotle Mexican Grill.
Bohuslavskiy mentioned that the agricultural industry has been slower than other sectors in adopting cybersecurity measures to defend against cyber threats. He and other researchers were very confident that REvil would increasingly focus on the agriculture sector to make money and steal valuable data since this sector is likely to pay a ransom to restore its systems.
security weakness in agriculture
Ransomware attacks on agriculture businesses result in substantial financial losses due to ransom payments, decreased productivity, and remediation expenses. Additionally, these businesses impacted may lose proprietary and personal data, potentially causing reputational harm.
When it comes to the farming aspect of agriculture, growers may assume that their labor-intensive operations can rely on conventional pen-and-paper methods if securing technology becomes too cumbersome or if they are attacked by cybercriminals. While this may be partially true, vital functions like labeling, shipping, and quality assurance hinge on data, which means that vital operations will be vulnerable to cyber threats. The era of farming as a manual, sun-soaked industry with individuals in overalls hand-planting seeds is a thing of the past.
Farming today is far more digital and machinery-dependent than many people realize. Contemporary farmers rely on a range of technologies, including GPS-guided tractors, crop monitoring sensors, drones, weather stations, automated irrigation systems, and even livestock tracking devices. John Deere is among the manufacturers that supply this kind of equipment to farmers.
JOHN DEERE
While the appearance of John Deere's tractors may not have undergone significant changes over the past four decades, a substantial transformation lies beneath the surface: the complete computerization of these machines.
In 2021, an Australian researcher known as "Sick Codes" from Sakura Samurai revealed significant vulnerabilities in the systems of the Moline, Illinois-based company during a Def Con conference in Las Vegas. These findings were of grave concern, as they uncovered a combination of issues that provided root access to John Deere's Operations Center, a comprehensive platform for monitoring and managing farm equipment.
The root access was made possible by two problems. Firstly, Sakura Samurai's John Jackson and another researcher, Robert Willis, identified a vulnerability within a business process management tool named Pega, commonly used by businesses. This vulnerability was attributed to unchanged default admin credentials, granting remote access to Pega's Chat Access Group Portal. This flaw opened doors to numerous other resources, including Pega's security audit log and even an Okta signing certificate. Furthermore, the researchers managed to export the private key for John Deere's single sign-on SAML server.
The severity of these combined issues led Sick Codes and his team to halt further exploration of Deere's systems. This vulnerability could essentially enabled an attacker to upload files to any user, impersonate any user, gain unauthorized access to various accounts, and manipulate, retrieve, or delete data as they please.
John Deere's machinery continuously sends data to the cloud, including details like when a farmer is in the cab, soil moisture levels, and the size of the harvest. Data has always played a vital role in farming, but today, it's collected on an unprecedented scale for smart farming or precision agriculture. This allows farmers to cut expenses, like using fewer pesticides, and boost crop yields.
While these advancements are remarkable and essential for efficiency, agriculture and farming often overlook the hidden dangers associated with their advanced technology. Dr. George Grispos, Ph.D., an assistant professor of cybersecurity at the University of Nebraska Omaha (UNO), is a leading figure in the field of cybersecurity, working diligently to raise awareness among farmers about the significance of safeguarding their machinery. These machines essentially serve as IoT devices with vulnerabilities that threat actors will try to exploit.
YOU ARE THE WEAKEST LINK
In an exclusive interview with Avertium, Grispos highlighted that the significance of cybersecurity in agriculture only became apparent after 2010, coinciding with the emergence of cloud computing, which heightened awareness of critical infrastructure cybersecurity. He also noted that the adoption of cybersecurity in the agricultural sector might lag, primarily because many farms are privately owned, lacking dedicated Chief Information Security Officers.
When asked how cyber attacks can trigger a chain reaction within agriculture as it pertains to food and farming, Grispos stated that the attack on JBS is a good example of how things can go awry very quickly.
“I think JBS is a good example of what could happen to a major supplier but also let's say something like a plant is attacked - it’s going to have a ripple effect on food production,” said Grispos. Co-op farmers wouldn’t be able to deposit grain either. They're going to have to figure out where else they're going to go and deposit their grain. Also, grains are going to start rotting if they've been sitting there for too long, and that's going to lead to a ripple effect. The grain wouldn’t be exported to other nations that genuinely need food.
So, similar to what we saw in the Russia-Ukraine conflict, where grain from Ukraine was impacting Africa – that was a physical conflict. But you can imagine a similar scenario if a state like Iowa or Nebraska, known for corn and beef exports worldwide, is hit by a major attack. This could have a devastating ripple effect on other countries around the world."
Regarding cyber criminals targeting planting and harvesting and the farmers' trust in their equipment's security, Grispos and his research team are currently investigating this topic. They are working to demonstrate the feasibility of cyberattacks during planting and cropping processes.
“You don't realize for several months that you were attacked. So, it's not like an attacker disables your servers and you can immediately notice the denial of service. If someone were to attack a piece of machinery, the farmer might continue working, trusting what the interface indicates. For instance, in an attack on a fertilizer machine, you wouldn’t detect that your fertilizer output has been compromised until harvest. Then, you notice your crops' irregular growth, with some receiving no fertilization, resulting in significant yield losses,” said Grispos.
Grispos and his research team conducted tests on 100-acre plots, demonstrating losses of tens of thousands of dollars resulting from compromising a single piece of machinery. The professor believes that introducing any form of technology to individuals unaccustomed to its use is not the best idea.
This is especially concerning because most farmers don’t even own their own equipment. One piece of farming equipment can cost up to $750k. The traditional farming model today involves leasing equipment from manufacturers, and users trust that the necessary updates and maintenance are taking place, although this is not to suggest that manufacturers are neglecting their responsibilities.
This scenario introduces the possibility of a third-party taking on the responsibility of ensuring equipment security. However, it raises important questions regarding accountability. Should the dealer, manufacturer, or the farmer be responsible for updates? In some cases, updates coincide with a busy season's end, leading farmers to prioritize other tasks over patching. The challenge lies in defining a reliable update and patching responsibility structure within an environment where technology is increasingly integrated into machinery. Most equipment will include technology, but it is important to determine how these updates will be managed, especially when some users may only use the machinery for its core function, such as harvesting.
Clearly, there is a different mindset at play here, potentially creating a vulnerability. Many individuals using this technology lack the proper education and training. Thus, the ultimate vulnerability is the human. It's comparable to giving a smartphone with pre-loaded credit card information to someone who may not be well-versed in its use, potentially falling victim to scams. The individuals in the agriculture and farming industry generally do not consider themselves potential targets for cyberattacks.
solution
Why isn't security a priority in agriculture and farming if a severe enough cyber attack can lead to the disruption of food-supply for the U.S. and other countries? One possible explanation is that the importance of security has only recently caught up with these industries.
While cloud technology standards have existed since 2006, transitioning this technology into agriculture didn't require reinventing the wheel. However, Grispos suggests that the shift from labor-intensive, manual processes to technology-driven solutions might have skipped a crucial step in education.
Unlike traditional sectors like technology or finance, where information security is a fundamental part of training, most in farming and food production have not had access to cybersecurity education. To address this gap, Grispos has received an NSF grant to design a cybersecurity course tailored to farmers and food producers, aiming to provide the education and training necessary for safeguarding their operations.
Additionally, Dr. Grispos and other researchers at the University of Nebraska-Lincoln (UNL) have created the "Security Testbed for Agricultural Vehicles and Environments" (STAVE) in collaboration with UNL. STAVE helps address the growing cybersecurity concerns in agriculture. With more farming machinery being connected online for tasks like mapping and automated steering, it's become important to protect them from potential cyberattacks. STAVE is like a miniaturized model of agricultural systems, making it easier to study and enhance their cybersecurity. It's based on an autonomous agricultural robot called Flex-Ro, developed by the UNL team.
STAVE includes a mix of electronic components commonly found in farm machinery and consumer electronics like Raspberry Pi microcomputers. These components are put together on a board and connected to a laptop. This setup allows researchers to simulate larger farming equipment and systems, helping to identify and fix potential vulnerabilities, which ultimately secures the agricultural industry.
Additionally, here are some clear and practical recommendations for addressing cyber risks in agriculture as it pertains to farming and food-supply:
- Formal Education Programs: Establish formal education programs tailored to farmers and food producers, focusing on cybersecurity awareness, mitigation of risks, and best practices.
- Promote widespread education initiatives as the primary solution to address the cybersecurity vulnerabilities in the agriculture and farming sectors.
- Basic Cyber Hygiene: Educate individuals with a technology background about fundamental cybersecurity principles, including confidentiality, integrity, and availability, as well as basic cyber hygiene practices to safeguard their operations.
- Ransomware and Phishing Prevention: Provide guidance on how to avoid ransomware and phishing attacks, particularly via email, as these are common entry points for cyber threats.
- Wireless Security: Strengthen wireless network security to protect against unauthorized access and data breaches.
- System Updates: Emphasize the importance of regularly updating software and equipment to mitigate vulnerabilities.
- Procurement and End-of-Life Systems: Educate on secure procurement practices and the management of end-of-life cycle systems to prevent potential security gaps.
By implementing the above recommendations, the industry can significantly enhance its cybersecurity posture and protect against cyber threats.
conclusion
The distinctive nature of farming and food production lies in the prevalence of privately owned enterprises, often passed down through generations. These aren't corporate entities with structured training programs; it's more of an intergenerational transfer of knowledge. Many farmers follow in the footsteps of their forebears, inheriting methods and practices without the inclusion of cybersecurity in their education. The absence of cybersecurity training might be where the challenge begins, which may help us understand the industry's current vulnerability to cyber threats.
The FBI highlighted instances where attacks on the agricultural sector have disrupted processing, email systems, and website administration, raising concerns that span from potential supply chain disruptions to impacts on commodity trading and stock prices. The realization of the need to secure critical infrastructure in agriculture is dawning, and steps are being taken to improve cybersecurity. This issue is increasingly registering on the radar, especially in Nebraska, where efforts to enhance cybersecurity measures are underway. The goal is to be well-prepared before a significant cyber incident occurs.
The arrival of autonomous technology adds a new dimension to the landscape. Autonomous machinery, including tractors, is on the horizon, with John Deere already making significant progress in this field. The era of autonomous tractors is not a distant future; it's arriving soon, with mass production plans already in motion.
Many farmers share a similar perspective, believing that their introduction to technology was primarily to streamline and simplify their work, enhancing efficiency and productivity. It often began with a single piece of equipment that seemed like a game-changer, taking over time-consuming tasks. However, as Grispos aptly puts it, "You don't have to worry about the task, but you do have to worry about the machine that is doing the task for you."
How Avertium is Protecting Our Customers
The need for education in the agriculture and farming is important, and it's not the fault of those involved. While manufacturers play a role in enhancing security, individual practices are equally important. Even if you aim to secure your operations, using an open network can introduce vulnerabilities. It's fundamental to understand the potential risks and ensure that farmers and food producers receive the necessary education to protect against cybersecurity threats effectively.
Avertium has services that can keep your organization secure:
- Avertium offers Vulnerability Management (VM) to provide a deeper understanding and control over organizational information security risks. If your enterprise is facing challenges with the scope, resources, or skills required to implement a vulnerability management program with your team, outsourced solutions can help you bridge the gap.
- Avertium aligns your Cybersecurity Strategy with your business strategy, ensuring that your investment in security is also an investment in your business. Our Cybersecurity Strategy service includes:
- Strategic Security Assessments - Strengthening your security posture begins with knowing where your current program stands (NIST CSF, Security Architecture, Business Impact Analysis, Sensitive Data Inventory, Network Virtualization and Cloud Assessment).
- Threat Mapping – Leverage Avertium’s Cyber Threat Intelligence, getting a more informed view of your most likely attack scenarios (Threat Assessment and MITRE ATT&CK).
- Cyber Maturity Roadmap - Embrace a comprehensive, quantifiable, and well-organized approach to establishing and continuously enhancing your cybersecurity resilience (Policy + Procedure Development, Virtual CISO (VCISO), Training + Enablement, Tabletop Exercises, and Business Continuity + Disaster Recovery Plan).
- Minimizing the impact of a successful ransomware attack requires detecting it as early in the attack as possible. A Security Information and Event Management (SIEM) system can help an organization to accomplish this. Avertium offers a comprehensive SIEM-based approach that increases the potential for detecting a ransomware infection before it deploys. SIEM provides a holistic overview of a company’s IT environment from a single point of view in terms of its specific security events, empowering teams to detect and analyze unusual behavior.
INDICATORS OF COMPROMISE
REvil
Note: The Cylance Ransomware group is believed to be a potential rebranding of the REvil ransomware operation. However, there is no solid evidence confirming that Cylance is indeed REvil, except for Cylance's research efforts aimed at sharing and identifying REvil telemetry as part of their security operations. Below are some Indicators of Compromise (IoCs) associated with Cylance.
IPv4
- 139[.]99[.]233[.]175
Note: BlueCrab ransomware has also been linked to REvil. Here are some IoCs associated with the threat actor.
SHA256
- 0fa207940ea53e2b54a2b769d8ab033a6b2c5e08c78bf4d7dade79849960b54d
- 454f0fa5f12c1ca1d704efb6904562005fd291c056fe58511ff357b41f016dcf
- 66490c59cb9630b53fa3fa7125b5c9511afde38edab4459065938c1974229ca8
- 6727edbb5d6abee908851a8c5fd7b4aca6d664634fdcdfc15e04502b960abbc5
- 740ad8ea62f10de39e0b794cf6f579f25af1b8d79f859b48ecd41edc1f92cf13
- 78b592a2710d81fa91235b445f674ee804db39c8cc34f7e894b4e7b7f6eacaff
- 7bafd5de1b6724962ab920f71031978a101055f061ae3cc21db8bb9fa64c5829
- d5ce6f36a06b0dc8ce8e7e2c9a53e66094c2adfc93cfac61dd09efe9ac45a75f
SHA1
- 1399bf98a509adb07663476dee7f9fee571e09f3
- 20e3a0955baca4dc7f1f36d3b865e632474add77
- 527c1dc2a340dd48652aec14a6316c7af0ff74c0
- 778bef878540c39021b50942faaebf9b473d4918
- 7895e4d017c3ed5edb9bf92c156316b4990361eb
- f7b876edb8fc0c83fd8b665d3c5a1050d4396302
MD5
- 4a91cb0705539e1d09108c60f991ffcf
- 5a97a50e45e64db41049fd88a75f2dd2
- aaca0b25fa85ab4507d3861697824343
- fa8117afd2dbd20513522f2f8e991262
- fac2cf669daebaf56f2fd4b3e0da10c0
- fb68a02333431394a9a0cdbff3717b24
Supporting Documentation
Grispos, G., Ph.D. (2023, August 6,). Personal Interview
Meatpacker JBS says it paid equivalent of $11 mln in ransomware attack | Reuters
Stay Vigilant with Cybersecurity During the Holidays (avertium.com)
UNO cybersecurity group focused on protection of agriculture (ketv.com)
Dole incurs $10.5M in direct costs from February ransomware attack | Cybersecurity Dive
Dole Foods Cyber Attack Shows Importance of Cyber Resilience (govtech.com)
Food Producers Band Together in Face of Cyber Threats - WSJ
Dole Says Employee Information Compromised in Ransomware Attack - SecurityWeek
Cyber Threats Impacting the Food and Agriculture Sector | Food Safety (food-safety.com)
Schreiber Foods back to normal after ransomware attack shuts down milk plants | ZDNET
CISA says BlackMatter ransomware group behind recent attacks on agriculture companies | ZDNET
Autonomous tractors are coming to a farm field near you | KCUR - Kansas City news and NPR
New Cylance Ransomware strain emerges, experts speculate about its notorious members | ITPro
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.