
Case Study:
INTERNOVA TRAVEL GROUP
Discover how Avertium helps unburden Internova Travel Group's security team to have the space to start focusing on more strategic cybersecurity priorities.
Context over chaos. Disconnected technologies, siloed data, and reactive processes can only get you so far. Protecting businesses in today’s threat landscape demands more than a set of security tools – it requires context.
That's where Avertium comes in
Security. It’s in our DNA. It’s elemental, foundational. Something that an always-on, everything’s-IoT-connected world depends on.
Helping mid-to-enterprise organizations protect assets and manage risk is our only business. Our mission is to make our customers’ world a safer place so that they may thrive in an always-on, connected world.
Best-in-class technology from our partners... backed by service excellence from Avertium.
Interested in becoming a partner?
With Avertium's deal registration, partners can efficiently and confidently connect with Avertium on opportunities to protect your deals.
Microsoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
Dive into our resource hub and explore top
cybersecurity topics along with what we do
and what we can do for you.
Cuba ransomware first appeared in 2019 but remained relatively unnoticed until November 2021, when they reportedly targeted a minimum of 49 organizations across various sectors. The sectors included government, healthcare, information technology, manufacturing, and finance. During this time, Cuba ransomware operators were infiltrating networks by encrypting files using the “.cuba” extension. Over the years, the ransom demands from Cuba totals at least $145 million, and the group has successfully collected at least $60 million in ransom payments.
By 2022, the threat actors had expanded their tactics, techniques, and procedures (TTPs), leading security researchers to suggest a potential connection between Cuba ransomware actors, RomCom Remote Access Trojan (RAT) actors, and Industrial Spy ransomware actors. This month, Cuba garnered attention when they took responsibility for a cyberattack on The Philadelphia Inquirer. The purported attack resulted in temporary disruptions to the newspaper's distribution and certain business operations. As we delve into Cuba's latest attacks, tactics, and techniques, it is important to assess how ransomware can disrupt business operations.
In December 2021, the Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency issued a joint advisory regarding Cuba ransomware. According to the advisory, the group successfully targeted a minimum of 49 entities across critical infrastructure sectors, including finance, government, healthcare, manufacturing, and information technology.
Cuba ransomware was being distributed through Hancitor malware, a loader known for deploying stealers like Remote Access Trojans (RATs) and various types of ransomware onto victims' networks. The actors behind Hancitor used phishing emails, exploit Microsoft Exchange vulnerabilities, compromised credentials, or used legitimate Remote Desktop Protocol (RDP) tools to gain initial access to the victim's network.
Once inside, the ransomware actors utilized legitimate Windows services, including PowerShell, PsExec, and other unspecified services, along with Windows Admin privileges, to execute their ransomware and other processes remotely. The compromise of a victim network was achieved through the encryption of targeted files, with the ".cuba" extension.
In October 2022, the Ukrainian authorities warned about a new ransomware group that was targeting organizations in the country. The unknown group was actually Cuba, and they were sending members of the Ukrainian government spoofed phishing emails that appeared to be sent from the “Press Service of the General Staff of the Armed Forces of Ukraine”. When recipients fell for the scam and clicked on the link provided in the email, they were directed to a webpage where they were encouraged to download a new version of PDF Reader. Unfortunately, this action triggered the execution of a malicious executable.
Running the mentioned file decoded and executed the 'rmtpak.dll' file, which was identified as RomCom malware. Palo Alto Networks originally discovered RomCom in August 2022. Their research connected this remote access Trojan (RAT) to a newly associated Cuba ransomware affiliate called "Tropical Scorpius”, confirming that Cuba allows threat actors to carry out various post-intrusion activities, including data exfiltration. Tropical Scorpius played a significant role in Cuba ransomware infections, accounting for almost half of the victims listed on the group's leak site from 2019 to the summer of 2022.
Palo Alto reported that Cuba ransomware successfully targeted 27 more organizations, including sectors like state and local government, transportation and logistics, utilities and energy, education, healthcare, and others. This information suggests that Cuba's operations in Ukraine were mainly driven by financial motives, rather than being coordinated with the objectives of the Russian state.
The Chilean government also became a victim of Cuba ransomware in 2022. The government’s Microsoft and VMware ESXi servers were targeted by the group. After encrypting the servers and renaming all files with “.crypt”, the group took complete control of the victim’s system and left a ransom note behind with a way to contact them.
In January 2023, in a private threat analytics report, Microsoft stated that Cuba ransomware operators were infiltrating unpatched Microsoft Exchange servers via a critical server-side request forgery (SSRF) vulnerability. The vulnerability was tracked as CVE-2022-41080 and was also used by Play ransomware.
Rackspace, a cloud computing provider, verified that Play ransomware successfully exploited CVE-2022-41080, compromising servers on Rackspace’s network by bypassing ProxyNotShell URL rewrite mitigations. The flaw was initially abused by the ransomware group in late November 2022. Although Microsoft released security updates on November 8, 2022, to resolve the SSRF Exchange vulnerability, and shared information with some customers regarding its exploitation by ransomware groups, the official advisory was not updated to clearly warn about active exploitation in the wild.
In May 2023, Cuba ransomware took credit for the recent cyber-attack on The Philadelphia Inquirer, causing a temporary disruption in the newspaper's distribution and impacting certain business activities. The breach was disclosed on May 14, 2023, and The Inquirer was forced to take its systems offline. The attack disrupted the distribution of The Inquirer's Sunday newspaper, making the disruption the most significant since the Blizzard of 1996.
Image 1: Cuba Publishes Stolen Files
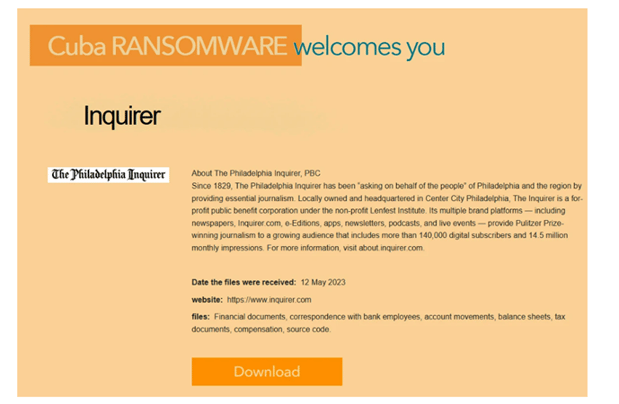 Source: Gridinsoft
Source: Gridinsoft
Although the Inquirer’s CEO, Lisa Hughes, stated that they have not seen evidence of The Inquirer’s data being shared online, Cuba claimed the cyber attack on their extortion site and the newspaper’s data was allegedly officially released by the gang. The data included source code, financial documents, account movements, tax documents, and more. However, the group has since removed the listed data, which could mean two things: they initiated negotiations and paid the ransom, or the leaked files didn’t belong to the victim. Brett Callow, a threat analyst at Emsisoft, stated that it’s too early to determine the exact reason why Cuba chose to remove the listing from the extortion site.
First observed in late 2019, Cuba ransomware is a file-encrypting ransomware that is typically distributed through Hancitor. It is notorious for adding the ".cuba" extension to the encrypted files. According to the FBI, since 2021, Cuba ransomware operators have demanded a minimum of $145 million in ransom payments and it is estimated that they may have already received over [1]$60 million from their victims. The gang has compromised 101 entities, 65 being within the United States and 36 outside the United States.
[1] aa22-335a-stopransomware-cuba-ransomware.pdf (cisa.gov)
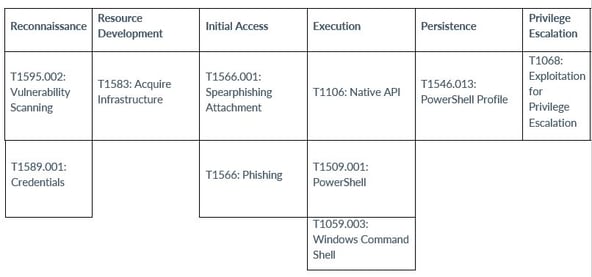
In December 2021, the FBI reported on Cuba’s tactics and techniques. To gain initial access to organizations in critical infrastructure sectors, Cuba leveraged the following techniques: legitimate remote desktop protocol (RDP) tools, compromised credentials, phishing campaigns, and exploiting known vulnerabilities in commercial software.
Upon compromise, Cuba installed and executed a Cobalt Strike beacon-as-a-service on the victim’s network via PowerShell. Once installed, the ransomware downloaded two executable files, which included “pones.exe” for password acquisition and “krots.exe,” also known as KPOT, enabling the Cuba ransomware actors to write to the compromised system’s temporary (TMP) file. Once the TMP file was uploaded, the “krots.exe” file was deleted and the TMP file was executed in the compromised network.
The TMP file included Application Programming Interface (API) calls related to memory injection that, once executed, deleted itself from the system. Upon deletion of the TMP file, the compromised network communicated with a malware repository located at Montenegro-based Uniform Resource Locator (URL) teoresp[.]com.
Additionally, Cuba ransomware actors used MimiKatz malware to steal credentials, and then used RDP to log into the compromised network host with a specific user account. Once the RDP connection was complete, Cuba used the Cobalt Strike server to communicate with the compromised user account. One of the initial PowerShell script functions allocated memory space to run a base64-encoded payload.
Once this payload was loaded into memory, it was used to reach the remote command-and-control (C2) server and then deployed the next stage of files for the ransomware. The remote C2 server is located at the malicious URL kurvalarva[.]com.
However, since the spring of 2022, Cuba’s operators have modified their tactics and techniques, as well as their tools. According to Palo Alto Networks, Cuba has exploited known vulnerabilities and weaknesses, using various tools to escalate privileges on compromised systems:
Palo Alto Networks also stated that Cuba uses specific tools to evade detection as they move laterally through compromised environments before ultimately executing the ransomware. The threat actors utilize a dropper that generates a kernel driver named ApcHelper.sys, which is designed to target and terminate security products. Although the dropper itself is unsigned, the kernel driver is signed using the certificate obtained from the LAPSUS NVIDIA leak. Cuba also uses double extortion, demanding a ransom payment in exchange for data decryption. They also threaten to publicly disclose stolen data in the ransom is not paid.
A ransomware attack can cause significant harm to an organization or business. In addition to lost work time, a ransomware attack can cause an organization reputational damage, as well as legal and regulatory penalties for failing to protect data. What most organizations fail to realize is that by the time ransomware begins encrypting files, the damage has already been done.
Unless an organization can fully recover its files from backups, there will be some data loss, even if a ransom is paid. Additionally, modern ransomware often steals and sends out data before encrypting it, indicating that the company may have already experienced a data breach. The best way to get ahead of a ransomware attack is to be proactive, utilizing ransomware best practices to protect against the threat:
Avertium and the FBI recommend that network defenders apply the following mitigations to reduce the risk of compromise by Cuba ransomware:
IP Addresses
Bitcoin Wallets
Email Addresses
SHA256 - File Hashes
MD5 – Hashes
Related Resource:
Ukraine Warns of Cuba Ransomware Attacks - Infosecurity Magazine (infosecurity-magazine.com)
Microsoft Word - Cuba Ransomware FLASH NOV11292021(1) (ic3.gov)
FBI: Cuba ransomware raked in $60 million from over 100 victims (bleepingcomputer.com)
Novel News on Cuba Ransomware: Greetings From Tropical Scorpius (paloaltonetworks.com)
Unit 42 (paloaltonetworks.com)
Chile and Montenegro Floored by Ransomware - Infosecurity Magazine (infosecurity-magazine.com)
Microsoft: Cuba ransomware hacking Exchange servers via OWASSRF flaw (bleepingcomputer.com)
Philadelphia Inquirer is Struck by Cuba Ransomware – Blogs (gridinsoft.com)
Novel News on Cuba Ransomware: Greetings From Tropical Scorpius (paloaltonetworks.com)
Philly Inquirer disputes Cuba ransomware gang's leak claims • The Register
FBI Warns of Cuba Ransomware Attacks on Critical Infrastructure - SecurityWeek
Cuba Ransomware Group’s New Variant Found Using Optimized Infection Techniques (trendmicro.com)
Signed driver malware moves up the software trust chain – Sophos News
Healthcare Sector Warned About Cuba Ransomware Attacks (hipaajournal.com)
Cuba ransomware claims cyberattack on Philadelphia Inquirer (bleepingcomputer.com)
aa22-335a-stopransomware-cuba-ransomware.pdf (cisa.gov)
How Should Companies Handle Ransomware? - Check Point Software
Cuba Ransomware Group’s New Variant Found Using Optimized Infection Techniques (trendmicro.com)
CISA Alert AA22-335A: Cuba Ransomware Analysis, Simulation, TTPs & IOCs (picussecurity.com)
FBI: Cuba ransomware breached 49 US critical infrastructure orgs (bleepingcomputer.com)
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.