- WHY AVERTIUM?
-
-
Why Avertium?
Context over chaos. Disconnected technologies, siloed data, and reactive processes can only get you so far. Protecting businesses in today’s threat landscape demands more than a set of security tools – it requires context.
That's where Avertium comes in
-
Considering Microsoft?
Avertium Named Microsoft Security Solutions PartnerAvertium’s managed services for Microsoft Security Solutions is delivered through the company’s premium service: Fusion MXDR. Fusion MXDR includes 24x7 monitoring and management of Defender for Endpoint and Sentinel, threat intelligence, attack surface
monitoring, and vulnerability management for Microsoft Security customers. -
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- SOLUTIONS
-
-
Governance, Risk, + Compliance
GRC with context – not complexity. -
Attack Surface Management
No more blind spots, weak links, or fire drills. -
Threat Detection + Response
Detect, adapt, and attack with context. -
Microsoft Security Solutions
End-to-end support from strategy to daily operations to maximize your Microsoft Security.
-
-
- COMPANY
-
-
About Us
Security. It’s in our DNA. It’s elemental, foundational. Something that an always-on, everything’s-IoT-connected world depends on.
Helping mid-to-enterprise organizations protect assets and manage risk is our only business. Our mission is to make our customers’ world a safer place so that they may thrive in an always-on, connected world.
-
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- PARTNERS
-
-
Our Partners
Best-in-class technology from our partners... backed by service excellence from Avertium.
-
Partner Opportunity Registration
Interested in becoming a partner?
With Avertium's deal registration, partners can efficiently and confidently connect with Avertium on opportunities to protect your deals.
-
Latest Avertium Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- NEWS & RESOURCES
-
-
News & Resources
Dive into our resource hub and explore top
cybersecurity topics along with what we do
and what we can do for you. -
Latest Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- CONTACT
A Look into NoEscape Ransomware
executive summary
NoEscape ransomware, a fairly new threat actor, appeared in May 2023 and is suspected to be a rebrand of the now-defunct Avaddon ransomware group, which ceased operations in 2021. The developers claim to have created the malware entirely from scratch, distinguishing it from other ransomware groups.
In less than a year, NoEscape has become a remarkable Ransomware-as-a-Service (RaaS) group, using unique features and aggressive multi-extortion tactics. This report will dive into the group’s tactics and techniques, explore potential ties to Avaddon, and provide recommendations on how organizations can remain safe from this type of threat actor.
tir snapshot
- NoEscape is a sophisticated RaaS group, and their targets vary depending on the affiliate or the buyer.
- They have been seen targeting the manufacturing, professional services, information, and healthcare industries. However, they don't target Commonwealth of Independent States (CIS) or ex-Soviet Union republics.
- The group uses multi-extortion tactics, especially triple extortion - increasing the impact of a successful attack.
- NoEscape encrypts data on both Windows and Linux machines, including VMware ESXi.
- NoEscape employs various MITRE ATT&CK techniques, including initial access through external remote services, execution via user execution and scheduled task/job.
- The ransom notes generated by NoEscape are titled "HOW_TO_RECOVER_FILES.TXT" and are placed in every folder housing encrypted files.
- Ransom payments, demanded in cryptocurrency, vary based on the severity of the attack and the specific ransomware variant.
- The RaaS group follows a profit-sharing model, where affiliates and operators split the ransom collected. When the ransom exceeds $3 million USD, there's a 90/10 split in favor of the affiliates.
- The cybersecurity community believes that some core members of the Avaddon operation might be part of the NoEscape group due to similarities.
- In December 2023, it was reported that the LockBit ransomware operation is actively recruiting affiliates and developers from the BlackCat/ALPHV and NoEscape groups.
- Detecting NoEscape without advanced solutions will require a multi-layered approach. However, there are some best practices organizations can implement.
noescape
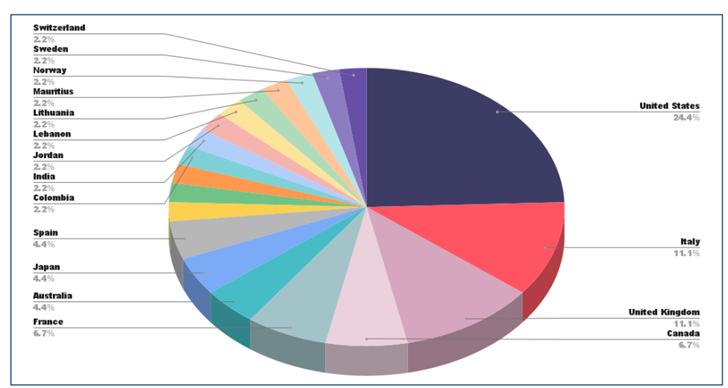
NoEscape is a sophisticated RaaS group, and their targets vary depending on the affiliate or the buyer. So far, they have been seen targeting the manufacturing, professional services, information, and healthcare industries. Interestingly, they don’t target Commonwealth of Independent States (CIS) or ex-Soviet Union republics. However, the group has been seen targeting the U.S. and several European countries at an alarming rate. The group uses multi-extortion tactics, especially triple extortion – increasing the impact of a successful attack.
This method refers to a three-pronged approach where data exfiltration and encryption is coupled with distributed denial-of-service (DDoS) attacks against the targets in an attempt to disrupt their business and force them into paying a ransom. The DDoS service is available for an added $500,000 fee, with the operators imposing conditions that forbid affiliates from hitting entities located in CIS countries. Additional mechanisms are in place to reduce the chances of this malware running on hosts which are detected to be in CIS countries.
Image 1: Target Industries
Source: HHS.gov
NoEscape encrypts data on both Windows and Linux machines, including VMware ESXi. Unlike other RaaS groups, NoEscape claims to be developed from scratch in C++. It offers affiliates customization options through an interface, allowing optimization for speed or thoroughness of encryption, prioritizing file paths, and selecting services to terminate before initiating encryption.
The ransomware employs RSA and ChaCha20 encryption algorithms, supports asynchronous LAN scanning, and demonstrates the capability to encrypt network file shares and local drives. An interesting feature is shared encryption, which allows for the use of a single encryption key across all infected files in a network, streamlining both the encryption and decryption processes.
The ransomware is compatible with Windows safe mode, offering a series of scripts for rebooting a victim's host in safe mode, where endpoint detection and response (EDR) products can be more easily disabled before initiating encryption.
MITRE ATT&CK
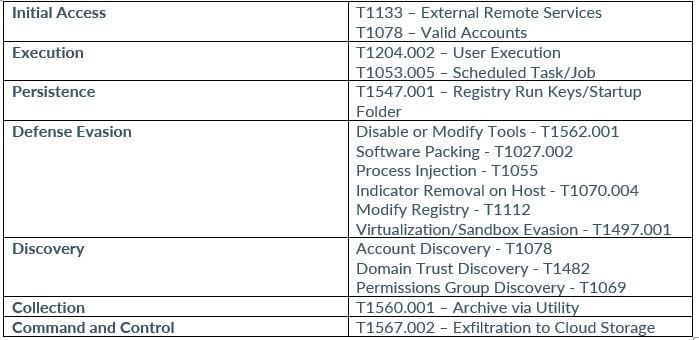
NoEscape employs various MITRE ATT&CK techniques, including initial access through external remote services, execution via user execution and scheduled task/job, persistence through registry run keys/startup folder, privilege escalation, defense evasion, credential access, discovery, lateral movement, collection, and command and control.
RANSOM
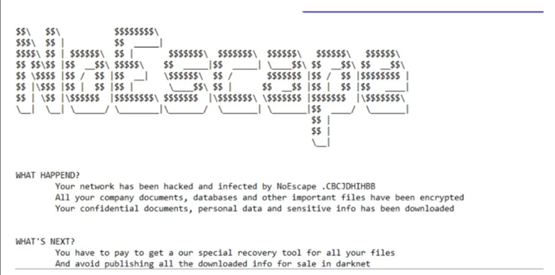
The ransom notes generated by NoEscape are titled "HOW_TO_RECOVER_FILES.TXT" and are placed in every folder housing encrypted files. Each encrypted file is marked with a distinct ten-character identifier as an extension. Noteworthy examples of observed extensions involve ".CCBDFHCHFD" and ".CBCJDHIHBB."
Image 2: Ransom Note
Source: SentinelOne
Ransom payments, demanded in cryptocurrency, vary based on the severity of the attack and the specific ransomware variant. Historical data shows that NoEscape ransom demands range from hundreds of thousands to over $10 million.
AFFILIATES
The RaaS group follows a profit-sharing model, where affiliates and operators split the ransom collected. When the ransom exceeds $3 million USD, there's a 90/10 split in favor of the affiliates. The split ratio changes for lower ransom amounts; for instance, a one-million-dollar payout results in an 80/20 split for the operator and affiliate, respectively.
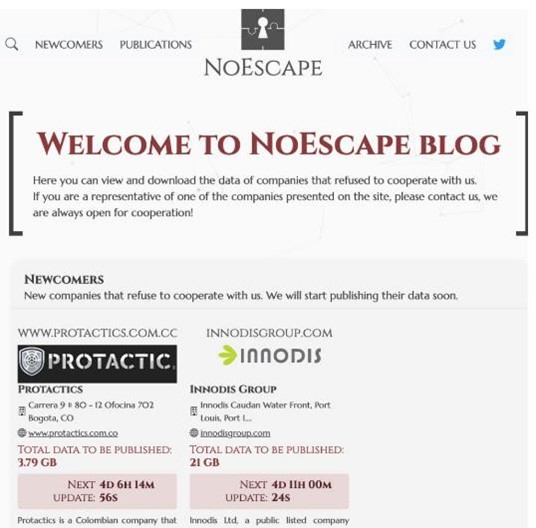
Potential NoEscape affiliates are provided with a comprehensive management panel for overseeing and controlling their ransomware campaigns. This panel includes features like 'full automation' within the TOR network, automatic updates to the TOR-based leak blog, a private victim chat, and various communication channels.
Image 3: NoEscape Blog
Source: SentinelOne
CONNECTIONS TO AVADDON
The emergence of NoEscape shortly after the ending of the Russian group, Avaddon in 2021, coupled with striking similarities in encryption logic and file formats, suggests a potential rebranding. While Avaddon used AES for file encryption, NoEscape shifted to the Salsa20 algorithm, with the overall encryptors being practically identical. The cybersecurity community believes that some core members of the Avaddon operation might be part of the NoEscape group.
RECENT ATTACKS AND SECURITY WARNINGS
NOESCAPE TARGETING MULKAY CARDIOLOGY CONSULTANTS IN NEW JERSEY
On September 2, 2023, the NoEscape ransomware group claimed to have successfully encrypted Mulkay Cardiology Consultants, a New Jersey-based medical practice. According to their leak site, the group stole 60GB of confidential patient data, including scans, doctor's conclusions, and other sensitive information.
DataBreaches attempted to verify the claim but found no issues with Mulkay's website. Interestingly, the listing on NoEscape's leak site for Mulkay later disappeared without explanation, raising questions about whether Mulkay paid the demanded ransom, negotiated, or faced other issues.
UNIVERSITY OF HAWAI'I RESOLVES NOESCAPE RANSOMWARE ATTACK WITH RANSOM PAYMENT
In June 2023, the University of Hawai'i suffered a ransomware attack on its Hawai'i Community College campus by NoEscape. Threatened with exposing 65GB of data, the university decided to pay the ransom to prevent data exposure. The payment was made to ensure the destruction of the illegally obtained information. The university collaborated with cybersecurity experts to address the situation with the goal of restoring its IT infrastructure. Following the payment of a ransom, the ransomware group removed the University of Hawai'i entry from their data leak site.
HEALTHCARE AND PUBLIC HEALTH SECTOR WARNED OF NOESCAPE
In October 2023, the U.S. Department of Health and Human Services’ Health Sector Cybersecurity Coordination Center (HC3) issued a warning about the NoEscape ransomware threat, particularly targeting the healthcare and public health (HPH) sector. H3 stated that the group refrains from allowing affiliates to attack entities in the former Soviet Union republics within the Commonwealth of Independent States (CIS). The government organization advised healthcare providers to implement standard protective measures against ransomware and leverage industry-specific resources to enhance their security practices.
TROUBLE?
In December 2023, it was reported that the LockBit ransomware operation is actively recruiting affiliates and developers from the BlackCat/ALPHV and NoEscape groups. According to insiders, both NoEscape and BlackCat/ALPHV ransomware operations’ Tor sites unexpectedly became inaccessible, with affiliates alleging an exit scam by NoEscape operators, involving the theft of significant ransom payments and the shutdown of key operation elements.
The BlackCat/ALPHV ransomware operation also faced a 5-day disruption, claiming hardware failure by the ALPHV admin, although sources suggest a potential law enforcement connection. In response to the chaos, “LockBitSupp”, the manager of the LockBit operation, is actively recruiting affiliates from the troubled BlackCat and NoEscape groups.
The LockBit group sees the outages in BlackCat/ALPHV as a favorable development, and while it remains uncertain if affiliates have migrated, one victim from BlackCat/ALPHV has already surfaced on LockBit's data leak site. Given the current landscape, it is unclear if trust issues will lead to a potential rebranding or shift of affiliates to other operations in the near future.
defense
Detecting NoEscape without advanced solutions will require a multi-layered approach. Take a look at some best practices organizations can implement:
- Consistently Back Up Your Data: It's crucial to regularly create backups of your vital data. Store these backups securely, preferably offline, to safeguard them from potential ransomware threats.
- Keep Software Updated: Ensure all your software, particularly your operating system and security solutions, are regularly updated. Routine updates frequently include fixes for known vulnerabilities that could be exploited by ransomware.
- Exercise Caution with Emails: Be cautious when dealing with email attachments and links, especially those from unfamiliar senders. Phishing emails are a prevalent tactic employed by ransomware to infiltrate systems.
- Education and Training: Regularly educate and train your staff about the risks associated with ransomware and instruct them on how to identify potential threats.
- Establish an Effective Incident Response Plan: Develop a well-defined incident response plan. In the event of a ransomware attack, having clear and immediate steps to follow can significantly minimize potential damage.
- Exercise Caution with Downloads: Avoid downloading files or software from untrusted sources or websites to reduce the risk of exposure to ransomware.
How Avertium is Protecting Our Customers
- Fusion MXDR is the first MDR offering that fuses together all aspects of security operations into a living, breathing, threat-resistant XDR solution. By fusing insights from threat intelligence, security assessments, and vulnerability management into our MDR approach, Fusion MXDR offers a more informed, robust, and cost-effective approach to cybersecurity – one that is greater than the sum of its parts.
- Minimizing the impact of a successful ransomware attack requires detecting it as early in the attack as possible. A Security Information and Event Management (SIEM) system can help an organization to accomplish this. Avertium offers a comprehensive SIEM-based approach that increases the potential for detecting a ransomware infection before it deploys. SIEM provides a holistic overview of a company’s IT environment from a single point of view in terms of its specific security events, empowering teams to detect and analyze unusual behavior.
- Avertium uses KnowBe4 as a professional service for user awareness training. The service also includes Incident Response Table-Top exercises (IR TTX) and Core Security Document development, as well as a comprehensive new-school approach that integrates baseline testing using mock attacks.
- Note: We highly value your feedback. Kindly spare a moment to complete our feedback form, allowing us to enhance our services for our valued customers.
MITRE MAP
INDICATORS OF COMPROMISE (IOCS)
MD5
- 204f028c983f654be32b97e849edeaab
- 47ae17d89c2d9b6acdc7458f5df1c6f7
- 5779cec690b5bbc61687381ae8a8d518
- 58b4a4eed74fbfbf104d0ffd92207018
- a106c1236357c315722ddbd985c5613c
- c850f6816459e3364b2a54239642101b
SHA1
- 30c60f18279ed5fd36e3ac2d3ba5ddbdc5d1f624
- 8770132656d4f3d9b973848b89e96fc95d736179
- 994edc8d183a1a7243790539044d12b80b1d5d84
- aa8ebc0b00d116cfe46245e0bb4a0b5108aadc0f
- d38c613020cb4616783c8535380e28404f7eaebf
- e128b01745ae1cb0de41c1b1c2e7271a172cf696
SHA256
- 0073414c5a03b20f6f255f400291de67f2a7268c461f90ea6ff0355ca31af07a
- 2020cae5115b6980d6423d59492b99e6aaa945a2230b7379c2f8ae3f54e1efd5
- 21162bbd796ad2bf9954265276bfebea8741596e8fe9d86070245d9b5f9db6da
- 4d7da1654f9047b6c6a9d32564a66684407ed587cbaffa54ec1185fd73293d3e
- 53f5c2f70374696ff12adcaaf1bbbe0e5dd1b1995d98f2e876b0671888b43128
- 68bce3a400721d758560273ae024f61603b8a4986440a8ec9e28305d7e6d02b0
- 73c19eab8d2ae58db3968dd7de0e745db2d7709859305b113b748bb02494465e
- 8dd64ea7f226d3eb1e857b0086c0668542652cb37f8142dc000272dbd9569e31
- 9d346518330eeefbf288aeca7b2b6243bc158415c7fee3f2c19694f0e5f7d51c
- c34c5dd4a58048d7fd164e500c014d16befa956c0bce7cae559081d57f63a243
Supporting Documentation
202310121200_NoEscape Ransomware Analyst Note_TLPCLEAR (hhs.gov)
In-Depth Analysis of NoEscape Ransomware (hivepro.com)
One Source to Rule Them All: Chasing AVADDON Ransomware | Mandiant
LockBit ransomware now poaching BlackCat, NoEscape affiliates (bleepingcomputer.com)
Ransomware group claimed to have hit a New Jersey cardiology group. Did they? (databreaches.net)
Malware Analysis of NoEscape Ransomware | by Alameen Karim Merali | Medium
Dark Web Profile: NoEscape Ransomware (socradar.io)
Ransom paid for NoEscape attack on Hawai'i Community College | SC Media (scmagazine.com)
Hawai'i Community College pays ransomware gang to prevent data leak (bleepingcomputer.com)
Ransomware Roundup – NoEscape | FortiGuard Labs (fortinet.com)
Ransomware Roundup – NoEscape - AlienVault - Open Threat Exchange
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.