- WHY AVERTIUM?
-
-
Why Avertium?
Context over chaos. Disconnected technologies, siloed data, and reactive processes can only get you so far. Protecting businesses in today’s threat landscape demands more than a set of security tools – it requires context.
That's where Avertium comes in
-
Considering Microsoft?
Avertium Named Microsoft Security Solutions PartnerAvertium’s managed services for Microsoft Security Solutions is delivered through the company’s premium service: Fusion MXDR. Fusion MXDR includes 24x7 monitoring and management of Defender for Endpoint and Sentinel, threat intelligence, attack surface
monitoring, and vulnerability management for Microsoft Security customers. -
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- SOLUTIONS
-
-
Governance, Risk, + Compliance
GRC with context – not complexity. -
Attack Surface Management
No more blind spots, weak links, or fire drills. -
Threat Detection + Response
Detect, adapt, and attack with context. -
Microsoft Security Solutions
End-to-end support from strategy to daily operations to maximize your Microsoft Security.
-
-
- COMPANY
-
-
About Us
Security. It’s in our DNA. It’s elemental, foundational. Something that an always-on, everything’s-IoT-connected world depends on.
Helping mid-to-enterprise organizations protect assets and manage risk is our only business. Our mission is to make our customers’ world a safer place so that they may thrive in an always-on, connected world.
-
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- PARTNERS
-
-
Our Partners
Best-in-class technology from our partners... backed by service excellence from Avertium.
-
Partner Opportunity Registration
Interested in becoming a partner?
With Avertium's deal registration, partners can efficiently and confidently connect with Avertium on opportunities to protect your deals.
-
Latest Avertium Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- NEWS & RESOURCES
-
-
News & Resources
Dive into our resource hub and explore top
cybersecurity topics along with what we do
and what we can do for you. -
Latest Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- CONTACT
A Closer Look at QakBot
qakbot Executive Summary
Last week, Avertium's Cyber Threat Intelligence team published a Flash Notice regarding QakBot and its distribution of malware through OneNote files. The malware campaigns, named QakNote, are currently affecting various organizations and we have witnessed numerous cases of this malware. It appears to be a rapidly spreading, extensive campaign.
QakBot has a lengthy history, dating back to 2007 when it began as a banking trojan. Since then, it has developed into one of the most intricate trojans available, regularly featuring in malware top 10 lists. QakBot has also been among the most adaptable malware strains, modifying its infection methods, targeting new data sources, and dropping different tools as computer usage and defensive systems have evolved.
In recent weeks, several spam campaigns have been identified that deliver malicious OneNote attachments embedded with an HTML application. Both campaigns employ a classic QakBot technique of injecting malicious emails into an existing thread, deceiving users into believing that the spam is part of an ongoing conversation. The malicious emails contain OneNote notebook attachments or http links to download OneNote notebooks. Once opened, the malware executes, downloads various payloads, installs multiple persistence mechanisms, extracts emails, and spreads to other users by responding to existing messages.

the origins of qakbot
2007
QakBot (also known as QBot) has been active since 2007, and initially started as a banking Trojan that utilized command and control (C2) servers for payload delivery. Previously, the threat actors who delivered QakBot also sold access to affected devices to other threat actors, who then used this access for a range of activities, from deploying other trojans to ransomware. With modularity being a crucial component, QakBot’s primary objective was to steal financial data and login credentials from victims. It was also capable of spying on financial operations and redirecting users to fake banking sites.
The modularity and flexibility of QakBot has always posed a challenge for security analysts and defenders because parallel QakBot campaigns look significantly different on each affected device, which significantly impacts how defenders respond to attacks. Consequently, a comprehensive understanding of QakBot was crucial in building a comprehensive defense strategy against it.
2022
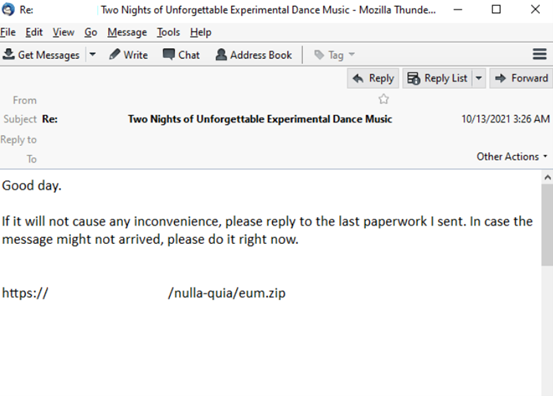
By March 2022, QakBot had evolved and spread through email thread hijacking. Researchers gave the name "TA577" to the threat actors behind QakBot. In one example, Sophos observed the Trojan inserting malicious replies into the middle of existing email conversations and compromising the accounts of other infection victims. The conversations included a brief sentence and a link to download a zip file. Inside the file was a malicious office document that deployed the malware.
Image 1: Malicious Email
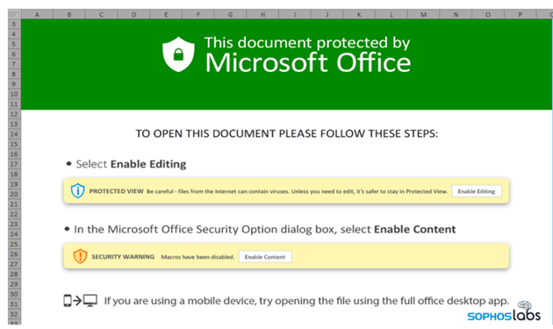
Image 2: Malicious Excel File
Source: Sophos
The phishing emails lured victims by using contextually aware themes and contained information such as work order, shipping, urgent requests, claims, and invoices. After establishing trust, the threat actors presented an official looking DocuSign graphic, guiding the victim through the process of enabling the Excel 4 Macros.
The QakBot Excel sheets included concealed spreadsheets, Excel 4.0 macros, and spreadsheet formulas. They also used BIFF records designed to deceive the user into thinking they were safe to open, and bypassed detection mechanisms that tried to parse various legacy formats found inside the spreadsheet.
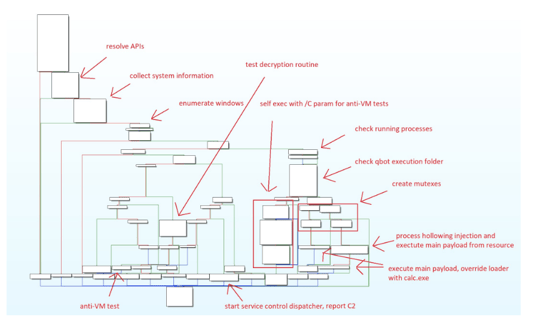
QakBot first tested the infected system to determine if it was suitable for infection. Next, the QakBot loader checked the environment by verifying if it was operating on a Virtual Machine, identifying any security, and monitoring tools or common security researcher tools.
According to Sophos, after successfully infiltrating the system, the bot injected itself into instances of Explorer.exe and Msedge.exe, before retrieving a range of harmful payloads which it injected into further instances of these two system programs. The primary malicious payload, which was injected into Explorer, regularly communicated with its C2 server every five minutes. It’s worth noting that this C2 address has been operational and accessible for a minimum of five months.
Interestingly, QakBot triggered one or more of its payload DLLs. One of the payloads acted as a web proxy, as the malware initiated a connection to the administrative interface of a website, employing pilfered login details, and subsequently uploaded various files to the site's hosting storage. Additionally, another payload resolved the locations of roughly twelve SMTP servers and attempted to establish a connection to each one and send spam.
Image 3: Previous QakBot Execution Flow
Source: AT&T Cybersecurity
QakBot made detection more difficult by encrypting strings and decrypting them at runtime before use. After the QakBot execution logic finished using a string, it immediately deleted the string from memory. After successfully infecting an environment, QakBot installed a backdoor that allowed threat actors to drop additional malware – including ransomware.
Anti-analysis and evasion methods throughout the infection chain made it extremely difficult for EDR and other security defenses to detect and prevent initial infection. This version of QakBot was used by ransomware gangs such as Black Basta. The gang used QakBot to create an initial point of entry and move laterally within an organization’s network.
Black Basta was also the first group to use QakBot to deliver the Brute Ratel C4 framework and leverage it to drop Cobalt Strike. Brute Ratel and Cobalt Strike are legitimate penetration testing tools that are used by penetration testers who seek to improve an organization’s ability to detect and respond to real cyberattacks. These frameworks are designed to simulate the tactics, techniques, and procedures (TTPs) utilized by attackers in network intrusions. Over the years, cyber criminals have been known to use these legitimate tools for illegal activity.
recent attacks
The most recent QakBot campaign started at the end of January 2023 using Microsoft OneNote files. This approach circumvents Microsoft’s blocking of office macros by default in 2022.
As previously stated, the first QakNote campaign involves attackers hijacking existing email threads and sending "reply-to-all messages" to participants with a malicious OneNote Notebook attachment. In the second campaign, attackers send malicious emails with a malicious .one file attachment.
The QakNote campaigns allow operators to embed most file types, such as VBS attachments and LNK files, in the malicious OneNote notebooks. If a victim double-clicks on an embedded attachment in a OneNote Notebook, the malicious payload is executed. A common social engineering technique of using a call to action is used to convince the target to open the payload. For example, by including a fake “Double Click to View File” button, which then runs the embedded file and retrieves the malware payload.
Proofpoint researchers have described the use of OneNote as an "unusual" method, and they believe that attackers are testing Microsoft's digital notebook as they explore different attachment types to bypass threat detection. Proofpoint also observed that "TA577's adoption of OneNote suggests that other threat actors will soon begin using this technique."
Between January 1 and 31, 2023, Proofpoint detected more than 50 campaigns that used OneNote attachments. Most of the campaigns that Proofpoint observed were related to shipping, invoices, taxes, and other generic business-related items. Researchers initially detected AsyncRAT payloads from December through early January. However, on January 9, 2023, they also identified QuasarRAT and XWorm malware campaigns in addition to AsyncRAT. Redline and AgentTesla were first spotted on January 11, 2023, followed by Netwire on January 12, 2023.
During their investigation, Proofpoint researchers found that several of the OneNote documents included a file history, suggesting that the same threat actor was reusing a file and modifying the payload URLs to create a new file.
Although most campaigns were found to be in English, Proofpoint discovered one campaign that used invoice themes to distribute XWorm and AsyncRAT and which included lures in both English and French languages.
The researchers at Logpoint selected a sample (MD5:17478bdc88d5d8101ff1058ab0a44116) and analyzed QakBot. Here are their findings regarding some of the bot’s core capabilities:
- Initial Access - Qakbot has recently employed malware spam campaigns with malicious attachments, hyperlinks, or embedded images to drop a second-stage payload. Lately, HTML attachments have been used to download a password-protected ZIP file containing an ISO file, a .LNK file, a Windows 7 version of calc.exe, and two DLLs. One of these DLLs is disguised as a support file for exe, named WindowsCodecs.dll.
- Execution - To execute the payload, the bot uses rundll32 or regsvr32 to execute or register/unregister DLLs.
- Privilege Escalation - Qakbot creates scheduled tasks to run payloads as the SYSTEM user.
- Persistence - to achieve persistence, the bot modifies registry Run keys.
- Defense Evasion - the malware modifies Defender registry keys and injects itself into processes such as exe, explorer.exe, msra.exe, mobsync.exe, and OneDriveSetup.exe.
- Discovery - QakBot performs discovery activities such as running whoami /all, ipconfig /all, and net view /all.
- Lateral Movement - The bot can move laterally by using WMI to create services on other endpoints within the breached network.
- Credential Harvesting - QakBot attempts to extract browser data from Internet Explorer and Microsoft Edge using esentutl.exe, a built-in Microsoft utility, for credential harvesting.
- Data Collection and Exfiltration - Qakbot creates a staging folder that collects emails dating back several years in attempts to perform email thread hijacking.
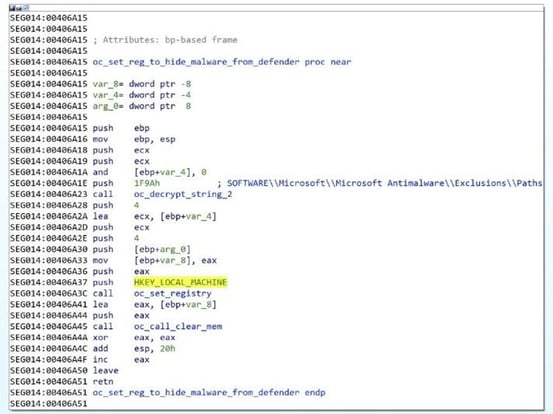
The behavior of Qakbot varies depending on the antivirus processes it detects. For instance, if it identifies Windows Defender, it will include its persistence folder in the Windows Defender exclusion path.
1 C:\Windows\system32\reg.exe, ADD, HKLM\SOFTWARE\Microsoft\Windows Defender\Exclusions\Paths, /f, /t, REG_DWORD, /V, C:\Users [REDACTED]\AppData\Roaming\Microsoft\Vybgeuye, /d, 0
- Microsoft Registry editor is in C:\Windows\system32\reg.exe.
- The folder location in the registry for Windows Defender exclusions is added using the command "ADD HKLM\SOFTWARE\Microsoft\Windows Defender\Exclusions\Paths".
- The command "/f" is used to add the registry entry without prompting for confirmation.
- The type for the registry entry is specified using the command "/t REG_DWORD".
- The name of the registry entry is specified using the command "/v C:\Users[REDACTED]\AppData\Roaming\Microsoft\Vybgeuye".
- The data for the new registry entry is specified using the command "/d 0".
Image 4: Registry Location
Source: AT&T Cybersecurity
avertium case study
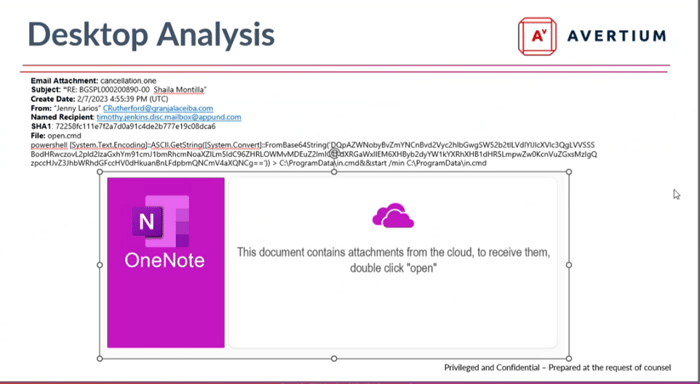
Avertium’s Cyber Response Unit (CRU) recently worked on a case where an organization was impacted by QakBot’s QakNote campaign. Like in other cases, Avertium’s case began when a malicious email with a OneNote attachment was sent to a client’s administrative assistant. Typically, the administrative assistant receives mail for six to eight executives, which is perfect from a threat actor’s perspective. Naturally, the assistant double-clicks on the OneNote attachment as instructed. The attachment looked like it contained information about a meeting cancellation.
Image 5: Email From Threat Actor
Once double clicked, a Base64 encoded PowerShell command downloads a malicious file named 01.GIF. The payload is then renamed Putty.jpg and upon execution establishes a connection to C2 servers.
Once active, QakBot attempts to enumerate the target's mailbox and retrieve as many email messages as possible. It then creates a file called collector_log.txt that logs the email retrieval process. The log includes a list of the mailboxes, subfolders, and all the emails that the bot is trying to copy. Next, a copy of the log is saved under a folder named EmailStorage_hostname-username-randomstring and is exfiltrated.
As with previous variants, Qakbot uses several techniques to avoid detection and analysis - including DLL side loading, anti-malware detection and evasion, and detection of sandbox analysis environments. After the initial detonation, the threat actors established C2 and extracted additional data. They used persistence mechanisms, such as adding the malicious executable to startup items on the computer, creating recurrent scheduled tasks, and the creation of malicious service entries.
QakBot is one of the more difficult malware strains for security experts to tackle. It is polymorphic, meaning that each bot interaction generates a distinct name and file hash, making it untraceable through a simple file name or hash value search, as each iteration of the bot is associated with a slightly different file.
The only hope detection engineers have at catching QakBot are behavioral indicators, such as creation of Putty.jpg, creation of collector_log, communication with known bad IP addresses or URLs, and injection into common windows executables – including msra.exe and wermgr.exe.
As a result, heuristic, behavioral detection, and access to known C2 servers are the best methods of detection.
DEFENSE
Qakbot is typically distributed through various phishing methods, such as malicious emails that originate from previously unseen email addresses or as replies to ongoing email conversations. The tactic of reusing existing email conversations has proven to be especially successful, since the emails look like they could be from a trusted source, often from someone the email recipient has recently corresponded with. This type of social engineering may lead the victim to open files and click on links that could launch the malware.
To protect your organization from QakBot, a bit of user awareness is necessary. Let’s look at a few tips that will help users determine if an email could be infected with QakBot:
- Users should exercise caution when receiving attachments that have specific instructions to open them.
- Be suspicious if you must navigate several folder layers or if there are unpackaging actions required to access a document.
- Verify by contacting the original sender by phone or by creating a new email conversation using the email address from another source (not as a reply).
- Usually, .one file extensions are not sent as attachments. If you receive a .one file attachment, be weary of clicking on it because it may be malicious.
As previously stated, .one file extensions are usually NOT sent as attachments; therefore, it is highly recommended that email administrators block all .one file extensions. For defense in depth, it's important to have endpoint protection installed, properly running, and appropriately configured on each device. If one EDR solution fails to detect a threat, it's good to have additional measures in place, such as a secure proxy. Your organization should also:
- Regularly apply system patches and keep antivirus software up to date.
- Follow the principle of least privilege for user accounts to limit the impact of malware in case of inadvertent execution.
- Disable macros by default for untrusted documents.
- Organizations should consider disabling the auto-mounting of disk image files, including ISO files, to prevent the use of detection bypass techniques. This can be done by modifying the Registry values.
- However, disabling this feature may cause issues with the standard operating procedure if disk image files are regularly used, so it should be carefully considered.
how avertium is protecting our customers
- Avertium offers user awareness training through KnowBe4. The service also includes Incident Response Table-Top exercises (IR TTX) and Core Security Document development, as well as a comprehensive new-school approach that integrates baseline testing using mock attacks.
- Minimizing the impact of a successful ransomware attack requires detecting it as early in the attack as possible. A Security Information and Event Management (SIEM) system can help an organization to accomplish this. Avertium offers a comprehensive SIEM-based approach that increases the potential for detecting a ransomware infection before it deploys. SIEM provides a holistic overview of a company’s IT environment from a single point of view in terms of its specific security events, empowering teams to detect and analyze unusual behavior.
- Managed Detection Response (MDR) provides an in-depth investigation into potential threats on an organization’s network. Avertium’s risk-based approach to managed security delivers the right combination of technology, field-validated threat intelligence, and resource empowerment to reduce complexity, streamline operations, and enhance cybersecurity resilience. If you need a more advanced security solution, MDR is the next step. MDR is an outsourced security control solution that includes the elements of EDR, enhanced with a range of fundamental security processes.
- Avertium offers Zero Trust Architecture, like AppGate, to contain lateral movement of malware.
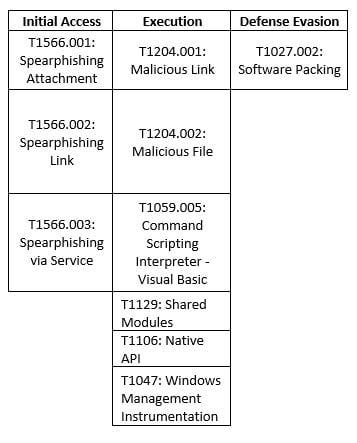
MITRE MAP
INDICATORS OF COMPROMISE (IOCs)
URLs
- hxxps://somosace[.]org/aswyw/01.gif
- hxxps://shifa365[.]com/hgxU5/01.gif
- hxxps://nerulgymkhana[.]com/CCoN/01.gif
- hxxps://starcomputadoras[.]com/lt2eLM6/01.gif
- hxxp://216.146.25[.]57/11747.dat
- hxxp://5.42.221[.]117/41067.dat
- hxxps://a1revenue.co[.]uk/SQ.php?TSI=5
- hxxps://gpshelpline[.]com/EAUD.php?NSII=10
- hxxps://limpiotucompu[.]com/OSIQ.php?ELIEAOSMT=1
- hxxps://smartvizx.com/UE.php?AISESCTISEBTUN=4
- hxxps://babarbrotherscargo[.]com/RO.php?NI=1
- hxxps://rjll.org.pk/TUEI[.]php?CUM=3
- hxxps://isoatte[.]com/LOTV.php?NTUEDRSE=8
- myvigyan[.]com/m1YPt/300123[.]gif
- 77[.]75[.2]30[.]128/47820[.]dat
- 86[.]194[.]156[.]14:2222
- 91[.]234[.]254[.]213/55788[.]dat
- hxxps:// jewishlabourbundarchive [.] net/ zdtK9c/01.gif
Hashes
- 4949b9d77f80cdb79f498b2def775dea9371dd08e2d66b4f513da35337af38c9
- 518518b0929911353cd7ab95d873e1fb290d8a494122cfb88e7f8bcf015576c8
- 5ade2a474118032ab353c7e835a0ca90669e690c997c8b374f94f408a9510b4e
- 7dd17b8cb0639732fe6929a5d7e1431fedae58acd401a7810afc0be8f9c42ad0
- 82ea16ea858ac6b9580f604695ebeaf1f004ae882a7d0e48688c28d466662f10
- 9981bf6ad64c2f48de970948b4dc6ca5e3e5f9ca8b86c2db921e032cd4a4c6cb
- b0339e18da6bfea0c60e388e631de79a83e2bc20880d6b9624d4784465a330b7
- b435653b9e1860cf38d78911eb7341c4b9c8e09af765b28a490ed269413eb2b1
- d13f70c241681df78ffa91ef105bfee069e78e7daa125cb7c47a50d34b234f12
- d80f18f5fc088c87905ee19c3f7b1dfd22920584913cc7b5925d64ad375e838f
- e0481af37fbb369ced2bff17468218b4676995b609fac1f96f604d93c55cfb5a
- eca50ee3c2ed694bf8b42a4e0eb14555c70c0d6186cc2dc863af8265c25ba4f1
Dropped Files
- cmd
- cmd
- jpg
Email Attachment Filename
- cancellation[.]one
SUPPORTING DOCUMENTATION
The rise of QakBot | AT&T Alien Labs (att.com)
Qakbot injects itself into the middle of your conversations – Sophos News
An In-depth Look at the Kraken Botnet (avertium.com)
Flash Notice: Beware - QakBot Group Infects Microsoft's OneNote with QakNote Malware (avertium.com)
Attackers increasingly use Microsoft’s OneNote to deliver QakBot malware | SC Media (scmagazine.com)
quakbot-emerging-threats-report.pdf (logpoint.com)
Ongoing reports of Qakbot malware incidents – Update 1 - Canadian Centre for Cyber Security
Nuspire Threat Analysis: Qakbot Spam Campaign Leveraging Microsoft OneNote - Security Boulevard
OneNote Documents Increasingly Used to Deliver Malware | Proofpoint US
QakNote Campaign Leverages OneNote to Infect Victims with QBot | Cyware Alerts - Hacker News
New QakNote attacks push QBot malware via Microsoft OneNote files (bleepingcomputer.com)
An In-Depth Look at Black Basta Ransomware (avertium.com)
Qakbot mechanizes distribution of malicious OneNote notebooks – Sophos News
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.