- WHY AVERTIUM?
-
-
Why Avertium?
Context over chaos. Disconnected technologies, siloed data, and reactive processes can only get you so far. Protecting businesses in today’s threat landscape demands more than a set of security tools – it requires context.
That's where Avertium comes in
-
Considering Microsoft?
Avertium Named Microsoft Security Solutions PartnerAvertium’s managed services for Microsoft Security Solutions is delivered through the company’s premium service: Fusion MXDR. Fusion MXDR includes 24x7 monitoring and management of Defender for Endpoint and Sentinel, threat intelligence, attack surface
monitoring, and vulnerability management for Microsoft Security customers. -
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- SOLUTIONS
-
-
Governance, Risk, + Compliance
GRC with context – not complexity. -
Attack Surface Management
No more blind spots, weak links, or fire drills. -
Threat Detection + Response
Detect, adapt, and attack with context. -
Microsoft Security Solutions
End-to-end support from strategy to daily operations to maximize your Microsoft Security.
-
-
- COMPANY
-
-
About Us
Security. It’s in our DNA. It’s elemental, foundational. Something that an always-on, everything’s-IoT-connected world depends on.
Helping mid-to-enterprise organizations protect assets and manage risk is our only business. Our mission is to make our customers’ world a safer place so that they may thrive in an always-on, connected world.
-
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- PARTNERS
-
-
Our Partners
Best-in-class technology from our partners... backed by service excellence from Avertium.
-
Partner Opportunity Registration
Interested in becoming a partner?
With Avertium's deal registration, partners can efficiently and confidently connect with Avertium on opportunities to protect your deals.
-
Latest Avertium Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- NEWS & RESOURCES
-
-
News & Resources
Dive into our resource hub and explore top
cybersecurity topics along with what we do
and what we can do for you. -
Latest Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- CONTACT
PyXie distributing ransomware tools targeting Healthcare, Education, Government and Technology companies
PyXie Overview
This report is about PyXie Group's advanced ransomware campaign. The bad actor has developed three different notable tools each providing a means to an end by the financially-motivated group. The focus of the PyXie group is distributing ransomware across various sectors including healthcare, education, government, and technology.
Tactics, Techniques, and Procedures
PyXie's ransomware tools start by gaining a foothold in the affected organization’s network by using either commodity malware or by using their custom loader called Vatet. Vatet once installed on victim’s system, executes XOR encoded shellcode from the local disk or using a network share. The loader portion is often a well-known application such Notepad, Notepad++, or a Tetris game. The payload injections typically result in Cobalt Strike which is used to setup beaconing and/or staging. The most up-to-date versions of the Vatet loader will inject a payload of the PyXie RAT (Remote Access Trojan). Vatet’s latest iteration will load the payloads from the local disk and will delete malicious payloads once they have been loaded into memory for execution.
The execution flowchart can be seen below for more information:
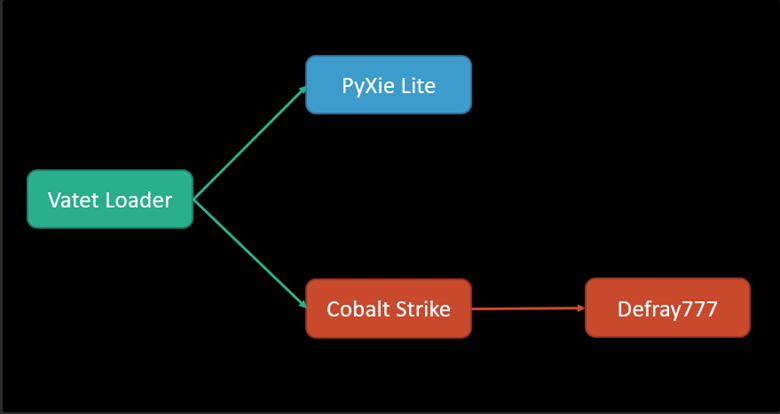
The RAT trojan primarily loaded by the Vatet malware is often referred to as PyXie Lite and contains a smaller codebase than the original. The lite version is designed to pull data from the infected host such as Cookie data, Citrix data, KeePass safes, password collection, and PowerShell history. The RAT can scan the network for other possible lateral movement avenues.
Additionally, there is a built-in version of Mimikatz should the need arise for credential harvesting which may be useful for deploying the Defray777 ransomware. The malware has hardcoded keywords that it uses on systems related to national defense, financial data, and cryptocurrency. Once all the data has been enumerated and gathered, the malware compresses it in a zip archive and encrypts using AES in CBC mode. The data is then sent to the command & control server over a specified network port.
The Defray777 ransomware family has a few unique features that should be covered in detail. The ransomware has separate standalone binaries for both the Linux and Windows operating systems. When the ransomware is installed, it avoids certain critical elements of the operating system to keep the affected device bootable and somewhat intact. The ransomware also queries that system for information that indicates the computational complexity of the device such as SSE2 support.
Business Unit Impact of PyXie Ransomware Tools
- May lead to the exfiltration of sensitive data such as financial data or national defense secrets
- Could result in the loss of mission-critical data from a ransomware attack
- Could lead to the propagation of malware within the environment
Recommendations
Security and IT professionals are highly encouraged to:
- Implement the blocklist linked below as a preemptive measure
- Consider maintaining regular backups of mission-critical assets on a regular schedule and test those backups to ensure that restoration of those systems is possible
Sources
• https://otx.alienvault.com/pulse/5fa9eae63b953f47ae203707
Supporting Documentation:
Blocklist:
- https://unit42.paloaltonetworks.com/vatet-pyxie-defray777/5/
- https://unit42.paloaltonetworks.com/vatet-pyxie-defray777/
- https://unit42.paloaltonetworks.com/vatet-pyxie-defray777/2/
- https://unit42.paloaltonetworks.com/vatet-pyxie-defray777/3/
MITRE Mapping(s)
- https://attack.mitre.org/techniques/T1027/
- https://attack.mitre.org/techniques/T1497/001/
- https://attack.mitre.org/techniques/T1083/
- https://attack.mitre.org/techniques/T1057/
- https://attack.mitre.org/techniques/T1012/
- https://attack.mitre.org/techniques/T1082/
- https://attack.mitre.org/techniques/T1033/
- https://attack.mitre.org/techniques/T1129/
- https://attack.mitre.org/techniques/T1543/003/
- https://attack.mitre.org/techniques/T1115/
- https://attack.mitre.org/techniques/T1056/001/
- https://attack.mitre.org/techniques/T1005/
- https://attack.mitre.org/techniques/T1055/
- https://attack.mitre.org/techniques/T1497/002/
- https://attack.mitre.org/techniques/T1010/
- https://attack.mitre.org/techniques/T1547/
- https://attack.mitre.org/techniques/T1486/
- https://attack.mitre.org/software/S0154/
- https://attack.mitre.org/software/S0002/
Incident Response Planning Webcast
Want a prima on creating an incident response plan for your company? Watch this webcast by Paul Caiazzo, senior vice president of security and compliance, as he steps through the five essentials steps to an incident response plan.
Note: The Avertium Threat Report analyzes one current threat that has been shared by threat intelligence networks across the globe. Used internally by the Avertium CyberOps Team, this report will outline a “top-of-mind” threat and how it ought to be addressed accordingly.
This informed analysis is based on the latest data available.
