- WHY AVERTIUM?
-
-
Why Avertium?
Context over chaos. Disconnected technologies, siloed data, and reactive processes can only get you so far. Protecting businesses in today’s threat landscape demands more than a set of security tools – it requires context.
That's where Avertium comes in
-
Considering Microsoft?
Avertium Named Microsoft Security Solutions PartnerAvertium’s managed services for Microsoft Security Solutions is delivered through the company’s premium service: Fusion MXDR. Fusion MXDR includes 24x7 monitoring and management of Defender for Endpoint and Sentinel, threat intelligence, attack surface
monitoring, and vulnerability management for Microsoft Security customers. -
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- SOLUTIONS
-
-
Governance, Risk, + Compliance
GRC with context – not complexity. -
Attack Surface Management
No more blind spots, weak links, or fire drills. -
Threat Detection + Response
Detect, adapt, and attack with context. -
Microsoft Security Solutions
End-to-end support from strategy to daily operations to maximize your Microsoft Security.
-
-
- COMPANY
-
-
About Us
Security. It’s in our DNA. It’s elemental, foundational. Something that an always-on, everything’s-IoT-connected world depends on.
Helping mid-to-enterprise organizations protect assets and manage risk is our only business. Our mission is to make our customers’ world a safer place so that they may thrive in an always-on, connected world.
-
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- PARTNERS
-
-
Our Partners
Best-in-class technology from our partners... backed by service excellence from Avertium.
-
Partner Opportunity Registration
Interested in becoming a partner?
With Avertium's deal registration, partners can efficiently and confidently connect with Avertium on opportunities to protect your deals.
-
Latest Avertium Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- NEWS & RESOURCES
-
-
News & Resources
Dive into our resource hub and explore top
cybersecurity topics along with what we do
and what we can do for you. -
Latest Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- CONTACT
MassLogger Malware
MassLogger Malware Overview
This threat report provides an overview of the MassLogger malware, the tactics, techniques, and procedures used, and what you can do to protect your organization.
MassLogger is recognized as spyware with keylogging and credential-stealing capabilities and contains actionable intelligence to protect against this risk.
The malware was first sighted in April 2020 and began to gain exposure from researchers in June. The threat actor NYANxCAT is widely recognized as the author and seller of the malware and has in the past written other malware such as AsyncRAT and LimeRAT. Due to its profitability, regular feature updates to the malware are expected by the author.
MassLogger Spyware Tactics, Techniques, and Procedures
MassLogger is a fully-featured malware written in .NET, with a variety of modules. It is designed for easy use by less technical malicious actors. Some of its functions include FTP, email, keylogging, and a variety of evasion techniques to avoid analysis from sandboxes and honeypots. Another unique capability of the malware is USB spreading, similar to LimeUSB, which was also written by NYANxCAT. Code for this and other malware from the author is available in a public GitHub repository: https://github.com/NYAN-x-CAT
The goal of MassLogger malware is to gather and exfiltrate sensitive data from infected hosts. It will check the host for installations of specific software and attempt to find stored passwords. MassLogger gathers data about the host into a log file, much like its name implies, and then sends it to the malicious actor’s server.
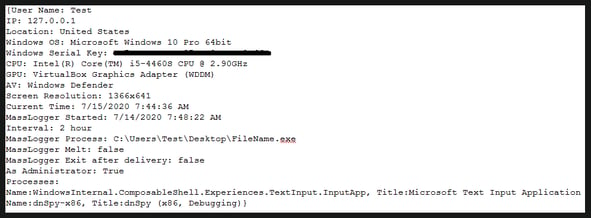
Initial access is normally gained by the malware through phishing techniques. A malicious attachment is used to deliver the payload to the victim. If the attachment itself does not directly contain the malware, it is often a Microsoft Office document with a malicious VBA macro used to download it. Seqrite notes that the below file attachment types have all been seen in MassLogger phishing attempts:
- zip
- rar
- gz
- 7z
- img
- iso
- doc
- arj
- xz
- ace
- docm
- z
- xlsm
- cab
What MassLogger Malware Means to You and What You Can Do
Possible MassLogger effects:
- May result in sensitive file exfiltration and data leakage.
- May result in compromised user credentials.
What you can do to protect your organization:
- Because MassLogger has only been observed infecting through phishing attempts, we recommend providing your users with training on best practices to avoid phishing, as well as awareness of recent trends in phishing campaigns.
- As a general rule, it is best practice to disable all Office macros by default and only have them enabled when it is necessary for a user’s daily job responsibilities. This will provide a measure of defense against files downloaded that contain malicious macros.
Indicators of Compromise
IOCs are provided in each of the linked sources, and in the AlienVault OTX pulses below:
- https://otx.alienvault.com/pulse/5f2d74a1f65c88c700583df6
- https://otx.alienvault.com/pulse/5f2cd6e13147684efc2106cc
Sources and Other Helpful Resources
Sources
- https://www.seqrite.com/blog/masslogger-an-emerging-spyware-and-keylogger/
- https://exchange.xforce.ibmcloud.com/collection/2642603865cd855f1199a3f8920cd83b/reports
- https://www.gdatasoftware.com/blog/2020/06/36129-harmful-logging-diving-into-masslogger
- https://cert-agid.gov.it/wp-content/uploads/2020/06/CERT-AGID_MassLogger-20200609.pdf
MITRE Mapping(s)
- Initial Access: https://attack.mitre.org/tactics/TA0001/
- Defense Evasion: https://attack.mitre.org/tactics/TA0005/
- Deobfuscate/Decode Files or information: https://attack.mitre.org/techniques/T1140/
- Virtualization/Sandbox Evasion: https://attack.mitre.org/techniques/T1497/
- Discovery: https://attack.mitre.org/tactics/TA0007/
- System Information Discovery: https://attack.mitre.org/techniques/T1082/
- Software Discovery: https://attack.mitre.org/techniques/T1518/
- Collection: https://attack.mitre.org/tactics/TA0009/
- Clipboard Data: https://attack.mitre.org/techniques/T1115/
- Input Capture: https://attack.mitre.org/techniques/T1056/
Supporting Links
- https://cofense.com/new-mass-logger-malware-massive/
- https://www.fireeye.com/blog/threat-research/2020/08/bypassing-masslogger-anti-analysis-man-in-the-middle-approach.html
Contact us for more information about Avertium’s managed security service capabilities.

8 Steps to Take if You've Been Breached
With the prevalence, severity, and sophistication of cybersecurity attacks growing by the day, businesses of all types and sizes are scrambling to protect themselves. This best practices guide takes you through the 8 essential steps to managing a data breach. Download now.
Note: The Avertium Threat Report analyzes one current threat that has been shared by threat intelligence networks across the globe. Used internally by the Avertium CyberOps Team, this report will outline a “top-of-mind” threat and how it ought to be addressed accordingly.
This informed analysis is based on the latest data available.