- WHY AVERTIUM?
-
-
Why Avertium?
Context over chaos. Disconnected technologies, siloed data, and reactive processes can only get you so far. Protecting businesses in today’s threat landscape demands more than a set of security tools – it requires context.
That's where Avertium comes in
-
Considering Microsoft?
Avertium Named Microsoft Security Solutions PartnerAvertium’s managed services for Microsoft Security Solutions is delivered through the company’s premium service: Fusion MXDR. Fusion MXDR includes 24x7 monitoring and management of Defender for Endpoint and Sentinel, threat intelligence, attack surface
monitoring, and vulnerability management for Microsoft Security customers. -
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- SOLUTIONS
-
-
Governance, Risk, + Compliance
GRC with context – not complexity. -
Attack Surface Management
No more blind spots, weak links, or fire drills. -
Threat Detection + Response
Detect, adapt, and attack with context. -
Microsoft Security Solutions
End-to-end support from strategy to daily operations to maximize your Microsoft Security.
-
-
- COMPANY
-
-
About Us
Security. It’s in our DNA. It’s elemental, foundational. Something that an always-on, everything’s-IoT-connected world depends on.
Helping mid-to-enterprise organizations protect assets and manage risk is our only business. Our mission is to make our customers’ world a safer place so that they may thrive in an always-on, connected world.
-
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- PARTNERS
-
-
Our Partners
Best-in-class technology from our partners... backed by service excellence from Avertium.
-
Partner Opportunity Registration
Interested in becoming a partner?
With Avertium's deal registration, partners can efficiently and confidently connect with Avertium on opportunities to protect your deals.
-
Latest Avertium Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- NEWS & RESOURCES
-
-
News & Resources
Dive into our resource hub and explore top
cybersecurity topics along with what we do
and what we can do for you. -
Latest Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- CONTACT
Lockbit 2.0 Ransomware: An In-Depth Look At Lockfile & LockBit
Overview of ransomware gangs: lockfile and lockbit 2.o
Ransomware gang attacks have been the talk of the year with the most recent attacks being from LockFile and LockBit 2.0. In April 2021, LockFile discovered a Microsoft Exchange Server vulnerability and took advantage of that discovery by successfully compromising hundreds of Exchange servers across the U.S and Asia.
In 2020, the Australian Cyber Security Center (ACSC) became aware of several incidents involving LockBit 2.0, with attacks being reported by enterprises in July 2021. The organization previously tried to warn of these attacks and mentioned that there was a considerable increase in domestic victims compared to other tracked ransomware variants.
Since being discovered, the gangs have trended across social media platforms due to their underhanded tactics – sending cyber intelligence analysts and engineers to scramble to try to figure how the gangs are able to operate so covertly and so efficiently. Let’s take a look at who these gangs are and why stopping them could be a challenge for cyber security professionals everywhere.
LockFile
Emerging in July 2021, LockFile is responsible for exploiting ProxyShell vulnerabilities found in unpatched Microsoft Exchange servers. They then followed up their ProxyShell attack with a PetitPotam NTLM relay attack to take control of the domain. They executed a PowerShell Command to download a malicious file.
As of September 2021, the Exchange servers are still being exploited by attackers despite the vulnerabilities being months old. The new series of attacks (ProxyShell) are said to be worse than the original attacks. According to Huntress.com, attackers are storing web shells in unusual locations (lateral movement), making it difficult to recover files should they be compromised. The researchers from our partner, Sophos, also have seen LockFile utilize “intermittent encryption” – a technique that involves encrypting every 16 bytes of a file. This is the first time the cybersecurity firm has seen this approach used.
“Intermittent encryption helps the ransomware to evade detection by some ransomware protection solutions because an encrypted document looks statistically very similar to the unencrypted original.” – News.Sophos.com
- ProxyShell – initial access vector
- PetitPotam – privilege, escalation, and lateral movement
To date, LockFile has compromised over 300 servers in an ongoing ransomware campaign.
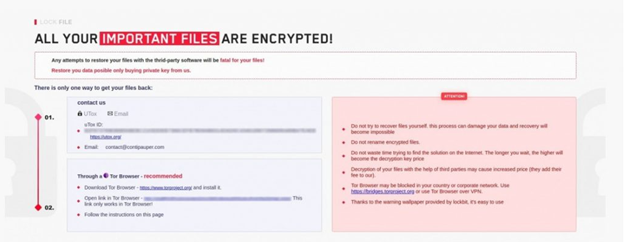
LockFile’s tactics include using three chained Exchange vulnerabilities: CVE-2021-34473 , CVE-2021-34523, and CVE-2021-31207 to gain remote access, infect systems with malware, and compromise confidential information for financial gain. After the attacker is successful with exploiting the ProxyShell vulnerability, they then use an obfuscated PowerShell command to download malicious files. One researcher found that this IP address [209.14.0[.]234] was used to host these malicious files.
LockFile’s ransomware can go undetected for an extended period because it doesn’t need to connect to a command-and-control center to communicate. One should also keep in mind that LockFile renames encrypted documents to lower case and adds a “.lockfile” file extension.
With most of LockFile’s victims in the U.S. and Asia, one undisclosed U.S. financial organization has already become a victim of LockFile’s ransomware. The ransomware gang has also targeted other industries like travel, engineering, manufacturing, legal, and business services.
LockBit 2.0
LockBit 2.0 is a ransomware variant of the original LockBit ransomware gang. The group uses ransomware-as-a-service (RaaS), with their most recent victim being Accenture. First appearing in Russian-language cybercrime forums in January 2021, LockBit 2.0 is thought to be related to the LockerGoga and the MegaCrotex malware families due to similarities in tactics, techniques, and procedures (TTPs). LockBit 2.0 relies on tools such as Windows PowerShell and Server Message Block (SMB) to attack organizations – scanning networks to infect compromised devices.
The ransomware gang primarily uses tools that are built-in to Windows systems (sometimes called Living off the Land Binaries, or LoLBins), which means it will be more difficult to detect malicious activity. LockBit 2.0 has successfully deployed ransomware within the following industries: manufacturing, retail and food, construction, and professional services, with most of the attempts being against Chile, Tawain, Italy, and the U.K.
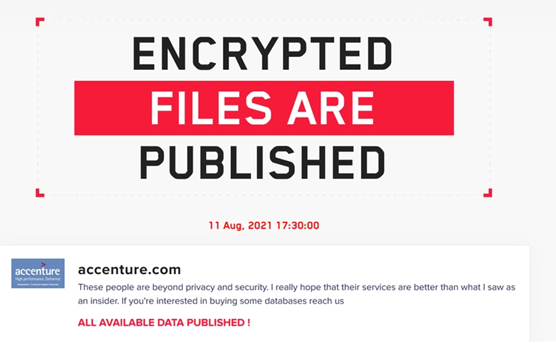
Recently, the gang has chosen to not only encrypt systems, but they have also adopted the double extortion model. This model involves locating and exfiltrating sensitive and confidential information before a system is encrypted – ensuring that the stolen data gives victims an incentive to pay the requested ransom. If the victims refuse to pay, then the information gets published publicly or sold. LockBit 2.0 has already threatened to sell or release information on their dark website “LockBit 2.0”, which is hosted on The Onion Router (Tor) network.
Additionally, the ransomware gang posted a recruitment flyer for insiders who work for enterprises they wish to target. The flyer promises the insiders that they will receive a percentage of the ransom if they give the gang access to systems.
After attacking Accenture, LockBit 2.0 was able to steal databases containing over 6 TB of data and demanded that the company pay a $50 million ransom. In Accenture’s case, researchers from Cyble believe an insider helped the ransomware gang gain access to the firm’s network. It was reported that companies with annual revenues between $1 billion and $9.9 billion account for 54% of all ransomware or extortion victims. Accenture’s revenue for 2020 was $44.33 billion.
LockBit 2.0’s ransom note appears to ask victims to contact this e-mail address: contact [@] contipauper.com. The email address appears to be derogatively referencing ransomware group, Conti, which is an active and competing ransomware group.
Lately, interviews have become free public relations for ransomware gangs. In August 2021, we mentioned in our Threat Actor Profile report that BlackMatter recently did an interview with The Record where they vaguely talked about their ransomware operation and their confidence in their longevity. The idea behind these interviews is to build public relations and recruit potential penetration testers for ransomware operations.
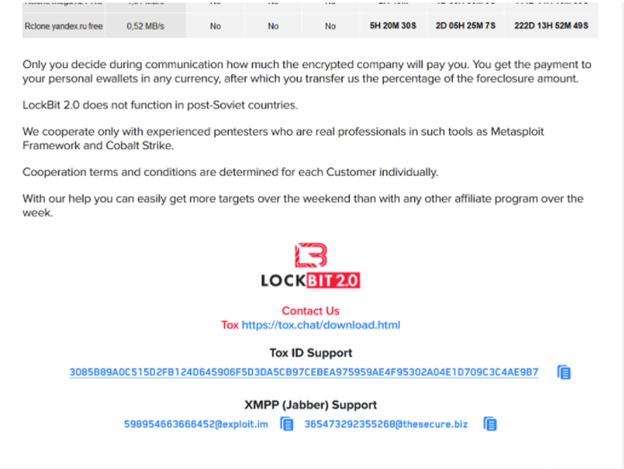
According to our partner, Advanced Intelligence, a LockBit 2.0 representative recently gave an interview (in Russian) where they allude to a relationship between ransomware operators and the Russian political system (although this cannot be confirmed). During the interview, the gang claimed to be unbeatable regarding encryption speed and data exfiltration. All it takes is for the attacker to take control of a domain controller to encrypt their victim’s network in the shortest amount of time – exactly how much time is unclear. All data harvested is stored on LockBit 2.0’s data leak site.
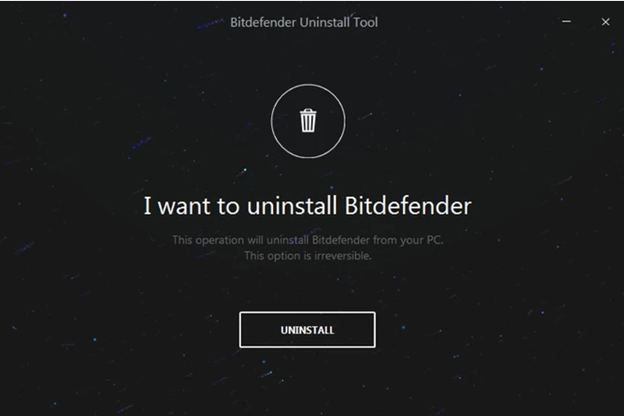
Ever cunning, the ransomware gang recommends that organizations use Bitdefender to defend against ransomware attacks, however; it is known that ransomware groups have figured out ways to bypass Bitdefender, including using the official Bitdefender Uninstall Tool to disable defenses.
How are LockFile and LockBit 2.0 Different?
Although LockBit 2.0 and LockFile both use partial encryption in their attacks, LockFile has a unique way they employ that encryption. If you recall earlier, we discussed how LockFile encrypts every 16 bytes of a file. To put it simply, this means that a text document encrypted by using this technique is still partially readable. The advantage that LockFile has over LockBit 2.0 is that its unique encryption technique confuses ransomware protection technologies. The gang can essentially encrypt a system and delete any evidence they were ever there with a PING command.
Another difference between the two gangs is that LockBit 2.0 is using RaaS and is actively recruiting people who work for large enterprises, while LockFile is not too concerned with recruiting and focuses heavily on harvesting sensitive data before anyone even notices their presence. Also, LockBit 2.0 locates sensitive information within a system before encrypting files for double extortion purposes, while LockFile appears to simply request a ransom in exchange for file decryption.
Both ransomware gangs stated that they aren’t attacking the healthcare and education industries, with LockBit 2.0 specifically stating, “We do not attack healthcare and educational institutions, as well as social services and charities. Anything that contributes to the development of human beings and their safety remains untouched.”
LockBit 2.0 further stated that they value their reputation and will destroy all data if the ransom is paid, guaranteeing full confidentiality.
As ransomware gangs continue to infiltrate the systems and networks of large enterprises, it’s important to be vigilant in protecting your enterprise against attacks. As seen with Accenture and other institutions within the U.S, LockFile and LockBit 2.0 are two cybercriminal gangs that are more than capable of stealing sensitive data and crippling an entire business. Attacks can happen to anyone – keeping up to date with the latest cyber intelligence news could help keep your organization from being the next victim.
Indicators of Compromise (IoCs) for LockFile
- C:\inetpub\wwwroot\aspnet_client\HWTJQDMFVMPOON.aspx
- C:\inetpub\wwwroot\aspnet_client\VJRFWFCHRULT.aspx
- C:\inetpub\wwwroot\aspnet_client\error.aspx
- D:\Program Files\Microsoft\Exchange Server\V15\FrontEnd\HttpProxy\owa\auth\HWTJQDMFVMPOON.aspx
- C:\inetpub\wwwroot\aspnet_client\nhmxea.aspx.aspx
- C:\inetpub\wwwroot\aspnet_client\supp0rt.aspx
- C:\Program Files\Microsoft\Exchange Server\V15\FrontEnd\HttpProxy\owa\auth\d62ffcd688.aspx
- C:\Program Files\Microsoft\Exchange
- Server\V15\FrontEnd\HttpProxy\owa\auth\Current\themes\resources\zaivc.aspx
- C:\Program Files\Microsoft\Exchange Server\V15\FrontEnd\HttpProxy\owa\auth\415cc41ac1.aspx
- C:\inetpub\wwwroot\aspnet_client\253283293.aspx
- C:\inetpub\wwwroot\aspnet_client\ykmsr.aspx
- C:\Program Files\Microsoft\Exchange Server\V15\FrontEnd\HttpProxy\owa\auth\6514f55e1a.aspx
- C:\inetpub\wwwroot\aspnet_client\KDNLIE.aspx
- C:\inetpub\wwwroot\aspnet_client\VOLWMFQWPP.aspx
- C:\Program Files\Microsoft\Exchange Server\V15\FrontEnd\HttpProxy\owa\auth\VOLWMFQWPP.aspx
- C:\inetpub\wwwroot\aspnet_client\system_web\NUQvLIoq.aspx
- C:\inetpub\wwwroot\aspnet_client\shell.aspx
- C:\inetpub\wwwroot\aspnet_client\updateServer.aspx
- ed834722111782b2931e36cfa51b38852c813e3d7a4d16717f59c1d037b62291
- cafe54e85c539671c94abdeb4b8adbef3bde8655006003088760d04a86b5f915
- 36e8bb8719a619b78862907fd49445750371f40945fefd55a9862465dc2930f9
- 5a08ecb2fad5d5c701b4ec42bd0fab7b7b4616673b2d8fbd76557203c5340a0f
- 1091643890918175dc751538043ea0743618ec7a5a9801878554970036524b75
- 2a23fac4cfa697cc738d633ec00f3fbe93ba22d2498f14dea08983026fdf128a
- a926fe9fc32e645bdde9656470c7cd005b21590cda222f72daf854de9ffc4fe0
- 368756bbcaba9563e1eef2ed2ce59046fb8e69fb305d50a6232b62690d33f690
- d030d11482380ebf95aea030f308ac0e1cd091c673c7846c61c625bdf11e5c3a
- a0066b855dc93cf88f29158c9ffbbdca886a5d6642cbcb9e71e5c759ffe147f8
- 7bcb25854ea2e5f0b8cfca7066a13bc8af8e7bac6693dea1cdad5ef193b052fd
- c020d16902bd5405d57ee4973eb25797087086e4f8079fac0fd8420c716ad153
Indicators of Compromise (IoCs) for LockBit 2.0
- Sha256 -0545f842ca2eb77bcac0fd17d6d0a8c607d7dbc8669709f3096e5c1828e1c049
- hxxp://lockbitapt6vx57t3eeqjofwgcglmutr3a35nygvokja5uuccip4ykyd[.]onion
- hxxp://lockbitsap2oaqhcun3syvbqt6n5nzt7fqosc6jdlmsfleu3ka4k2did[.]onion
- hxxp://lockbitsup4yezcd5enk5unncx3zcy7kw6wllyqmiyhvanjj352jayid[.]onion
- hxxp://209.14.0[.]234:46613/VcEtrKighyIFS5foGNXH
Avertium’s Recommendations for LockFile Ransomware
- If you have on-premise Exchange servers that have not been patched to remediate the ProxyShell vulnerabilities, patch them immediately! The same patches that were deployed in the spring still work for the most recent attacks. Microsoft Exchange cumulative updates
- Consider disabling NTLM authentication on your domain controllers to prevent the PetitPotam domain takeover exploit.
- If disabling NTLM is not possible, use an unofficial 0patch to block NTLM relay attack vector or apply filters to block access to vulnerable functions.
- Reach out to your Service Delivery Manager or Account Executive if you need assistance applying any of the above recommendations
Avertium’s Recommendations for LockBit 2.0 Ransomware
- Reduce the target by including these technical practices: close vulnerabilities, augment security hygiene, create and enforce strong general policies, and sustain backup and recovery practices.
- Use anti-ransomware technology as a prevention method. Deploy prevention that works like next-generation antivirus and explicit anti-ransomware technology.
- Include an EDR, MDR or XDR strategy to stop ransomware before it spreads. You should also include a Zero Trust Architecture, like AppGate, to stop malware lateral movement.
- Relying on outdated tools and point solutions will compromise your network or system. Better technology exists to detect complex attacks like LockFile and LockBit ransomware.
- Be sure to test and re-test backups. Practice and use tools, people, and processes Test backups. Tabletop disasters. Practice and use your incident response muscle, tools, people, and processes.
- Monitor infrastructural endpoints for public-facing applications. LockBit 2.0 prefers Corporate VPN (particularly Citrix/FortiNET) LockBit 2.0 is known for actively exploiting public-facing applications.
- Externally exposed RDPs.
- It’s likely that LockBit 2.0 monitors the latest CVEs. Monitor exposed endpoints and application of CVE-addressing patches.
- Disrupt network movements/investigation by way of creating separated segments of network, clear access hierarchy, and additional security for active directory, domain admin, and local domains – thus complicating LockBit 2.0’s operations.
- Require multifactor authentication to protect employees’ accounts from being used by attackers to obtain account credentials and use them to escalate privileges and move laterally within the network.
- Perform daily backups and keep them offline to avoid losing data.
MITRE TTPs
[T1562.001] Impair defenses: Disable or Modify tools
[T1070.001] Indicator removal on Host: Clear Windows Event Logs
[T1041] Exfiltration Over C2 Channel
[T1486] Data encrypted for impact
[T1489] Service stop
[T1490] Inhibit System Recovery
How to Respond to a Ransomware Attack
- Contact Avertium for DFIR (Digital Forensics and Incident Response).
- Be prepared with a plan of communication for all of your third parties letting them know what has happened what they need to do.
- Move any untouched data to a safe location in which hackers are unable to reach it.
To learn more and gain a better understanding of what to do if your organization faces a ransomware attack, check out Avertium's 8 Steps to Take if You've Been Breached.
Terms
RaaS – A subscription-based model that enables affiliates to use already-developed ransomware tools to execute ransomware attacks. Affiliates earn a percentage of each successful ransom payment. Ransomware as a Service (RaaS) is an adoption of the Software as a Service (SaaS) business model.
PING Command – Verifies IP-level connectivity to another TCP/IP computer by sending Internet Control Message Protocol (ICMP) echo Request messages. The receipt of corresponding echo Reply messages are displayed, along with round-trip times. ping is the primary TCP/IP command used to troubleshoot connectivity, reachability, and name resolution. Used without parameters, this command displays Help content. You can also use this command to test both the computer name and the IP address of the computer.
Double Extortion – When ransomware gangs go beyond decryption in exchange for money, but also harvest sensitive information and threaten to publish it on a data leak site. They will also release stolen information via underground forums or blogs. The ransomware gang, Maze, was the first to be associated with double extortion.
LoLBins – Also known as Living off the land binaries, LoLBins are non-malicious and are local to the operating system and can be exploited by attackers, so their malicious activity goes unnoticed.
Supporting Documentation
https://www.cybereason.com/blog/rising-threat-from-lockbit-ransomware
https://www.cybereason.com/blog/accenture-responds-following-lockbit-ransomware-attack
https://blog.cyble.com/2021/08/25/lockfile-ransomware-using-proxyshell-attack-to-deploy-ransomware/
https://docs.microsoft.com/en-us/windows-server/administration/windows-commands/ping
https://www.advintel.io/post/from-russia-with-lockbit-ransomware-inside-look-preventive-solutions
https://www.avertium.com/blackmatter-threat-actor-profile/
Note: The Avertium Threat Report analyzes one current threat that has been shared by threat intelligence networks across the globe. Used internally by the Avertium CyberOps Team, this report will outline a “top-of-mind” threat and how it ought to be addressed accordingly.
This informed analysis is based on the latest data available.