
Internova Travel Group Case Study
Discover how Avertium helps unburden Internova Travel Group's security team to have the space to start focusing on more strategic cybersecurity priorities.
Context over chaos. Disconnected technologies, siloed data, and reactive processes can only get you so far. Protecting businesses in today’s threat landscape demands more than a set of security tools – it requires context.
That's where Avertium comes in
Security. It’s in our DNA. It’s elemental, foundational. Something that an always-on, everything’s-IoT-connected world depends on.
Helping mid-to-enterprise organizations protect assets and manage risk is our only business. Our mission is to make our customers’ world a safer place so that they may thrive in an always-on, connected world.
Best-in-class technology from our partners... backed by service excellence from Avertium.
Interested in becoming a partner?
With Avertium's deal registration, partners can efficiently and confidently connect with Avertium on opportunities to protect your deals.
Microsoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
Dive into our resource hub and explore top
cybersecurity topics along with what we do
and what we can do for you.
Originally focused on healthcare security, HITRUST's reputation for being the most comprehensive security framework has resulted in cross-industry popularity. This spike in popularity has caused many organizational decision-makers to ask the question, “What is HITRUST?" and evaluate if their company should earn HITRUST certification.
This article provides a HITRUST overview and answers your HITRUST security framework questions.
HITRUST originally stood for the Health Information Trust Alliance, but the organization rebranded to simply become HITRUST Alliance. This is a privately held company founded in 2007.
Created in collaboration with healthcare, technology, and information security organizations, the company established a cybersecurity framework to help organizations from all sectors — but especially healthcare — effectively manage data, information risk, and compliance.
Today, the organization offers an industry-agnostic HITRUST Approach:
"A comprehensive information risk management and compliance program to provide an integrated approach that ensures all programs are aligned, maintained and comprehensive to support an organization’s information risk management and compliance objectives."
The HITRUST Common Security Framework (CSF), or HITRUST Risk-Based Two Year (r2), is a set of security controls that incorporates the HITRUST Approach. HITRUST r2 helps organizations that work with sensitive data to become more secure.
It is designed to provide a flexible and configurable standard that organizations can use to develop cybersecurity strategies compliant with the HIPAA, ISO, NIST, SOC 2, CMMC, PCI-DSS, and many other data protection regulations.
Related Resource:
The HITRUST Alliance recently announced two new assessments designed to provide the same level of management and compliance recognition, but with greater ease and faster results. The design of HITRUST Implemented One-Year (i1) and HITRUST Basic Current State (bC) is similar to that of the original HITRUST CSF assessment, now known as HITRUST r2. Like HITRUST CSF, these newly added assessments will help organizations understand their cybersecurity's control effectiveness, preparedness, and resilience.
It's about diving into the best practices for your organization. HITRUST i1 Validated Assessment is an abbreviated version of HITRUST r2, cutting down on the levels of time, cost, and effort spent. While this may seem like a shortcut, it's quite the opposite, as it still provides the same transparency and integrity as the r2 assessment, but on a scale that fits mid-size and larger organizations.
To understand what this certification hones in on, let's first take a look at what the five key areas a typical r2 assessment focuses on:
In comparison to the list above, HITRUST i1 concentrates solely on the "implemented" section, which is why the i1 assessment takes less time and effort to perform. It is important to note as well that a major difference between i1 and r2 is that the i1 certification only lasts one year, while the r2 lasts two years. The implemented i1 validated assessment is recommended for circumstances that present moderate risk or where a baseline risk assessment is needed. And make no mistake — though it's a leaner version of r2, the evaluation process of i1 is still incredibly rigorous and provides the same credibility associated with the original HITRUST assessment.
i1 assessments can also be used as either a readiness assessment (identification and remediation report) or a validated assessment (requirements check and official certification). It's recommended that every organization start with a readiness assessment to get a detailed report on what your organization's cybersecurity looks like and where the areas for improvement are before performing a validated assessment. This is important in finding vulnerabilities within your organization as it allows you to complete any recommended remediations before a HITRUST QA team conducts the validated assessment.
It's about checking on your organization's cybersecurity hygiene. HITRUST bC is even faster than i1, however, it does not provide a certification. The purpose of HITRUST bC is to act as a self-assessment (similar to that of the standing HITRUST self-assessment) which can later be utilized when a company is working towards its i1 or r2 certification.
By working with the HITRUST Assurance Intelligence Engine™ (AI Engine), the bC assessment evaluates and curates a report calling attention to any disturbances or errors within your company's IT environment. This assessment is not only beneficial for self-correction, but if you are required or plan to ever achieve a HITRUST certification, the bC assessment provides you with a substantial baseline analysis of the controls involved.
To have a firmer grasp on whether or not your organization needs to perform a HITRUST bC assessment, you can look to an external accessor partner for direction.
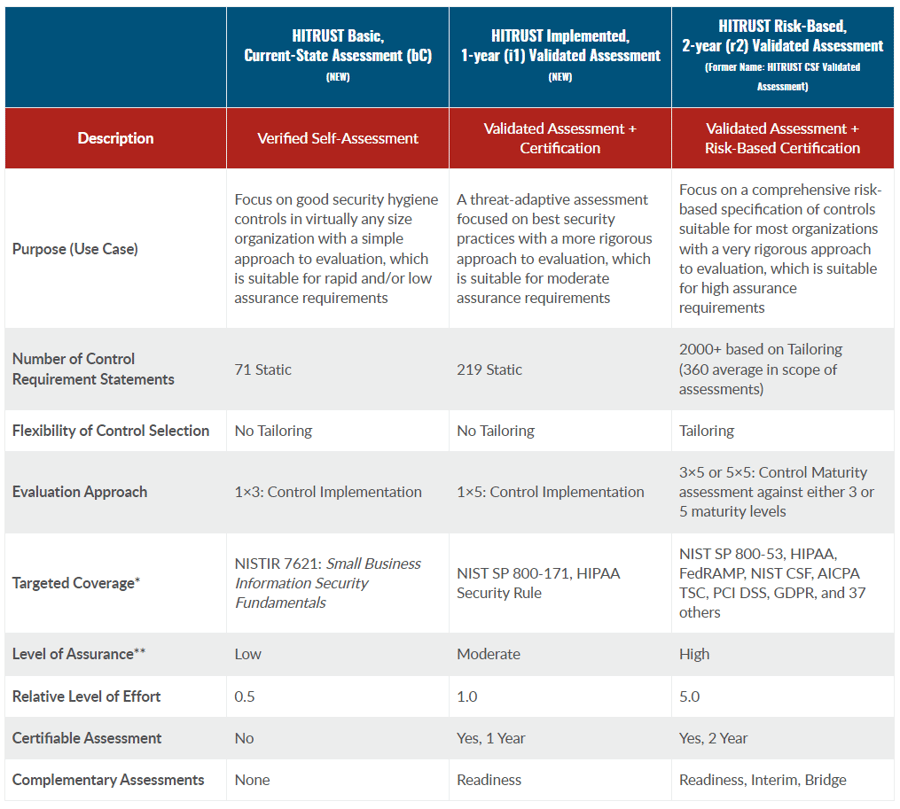
Source: HITRUST Alliance
HITRUST certification demonstrates that an organization complies with the HITRUST CSF. Achieving compliance with HITRUST is not mandatory under any regulation; however, the HITRUST CSF and certification have multiple benefits for an organization:
Some privacy and data protection regulations require the data to be protected “appropriately” and according to “best practice” without specifying what this means. This leaves the burden on the organization seeking compliance to determine what controls should be implemented and then to execute them.
Organizations can, therefore, be unintentionally non-compliant due to:
The HITRUST security framework is designed to give organizations concrete guidance on controls to put into practice and how to modify requirements to fit the business's needs based on size, function, and organization layout.
Certifying against a framework helps to ease the burden on organizations and ensures that steps are taken help to meaningfully increase organizational cyber resilience.
Related Reading: Achieve Secure Cloud Adoption Using HITRUST
Organizations are often liable for compliance with multiple regulations and/or security frameworks. For example, if a healthcare provider accepts credit or debit cards as payment for services, they are required to protect this information under the PCI-DSS.
Related Reading: Do I Have to Be PCI Compliant?
Trying to meet requirements for multiple regulations and standards can cause confusion and the potential for non-compliance if regulatory requirements are implemented, tested, and updated individually rather than as part of a comprehensive program.
Seeking HITRUST security framework certification can help an organization design its security strategy to minimize the probability of oversights or errors and ensure compliance with multiple regulations. The HITRUST CSF is designed to be configurable and allow organizations to demonstrate compliance with HIPAA, ISO, PCI-DSS, NIST, and many other state, private sector, and even international standards such as GDPR.
The HIPAA regulations advise that organizations must do what is “reasonable and appropriate” to protect sensitive healthcare data. This leaves the organization guessing how to implement a “compliant” system with no governing body that certifies compliance. As a result, vendors have developed their own testing methods and certifications that organizations can seek.
Without clearly defined requirements, it is difficult for organizations to prove that they are truly compliant under HIPAA regulations. An advantage of the HITRUST certification is that it provides organizations a way to prove compliance with a reputable certification framework that can cover a variety of regulations and can be tailored to meet the needs of the organization.
Download! The Essential Guide to HIPAA Compliance
A large number of data breaches across all industries underscores the importance of properly protecting sensitive data – personal information, business proprietary data, legal and contractual information, payroll, and human resources data all must be protected at the appropriate level. Achieving a third-party certification and attestation of an organization’s cybersecurity can be beneficial both internally and externally.
By achieving a third-party attestation of regulatory compliance, an organization can demonstrate appropriate due diligence for a legal investigation caused by a breach or official complaint.
Organizations can also proactively take advantage of HITRUST certification by advertising the fact that they are compliant in order to attract customers who are concerned about the appropriate protection of their sensitive data.
Free Download: Get the 9 Steps to Manage Third-Party Information Security Risk
HITRUST certification requires that your organization’s security controls be assessed by a HITRUST CSF assessor firm that provides HITRUST Certified CSF Practitioners (CCSFP). A good HITRUST assessor firm should do the following for you:
Find out which HITRUST Assessment is best for your organization and how you can start preparing for it now!