- WHY AVERTIUM?
-
-
Why Avertium?
Context over chaos. Disconnected technologies, siloed data, and reactive processes can only get you so far. Protecting businesses in today’s threat landscape demands more than a set of security tools – it requires context.
That's where Avertium comes in
-
Considering Microsoft?
Avertium Named Microsoft Security Solutions PartnerAvertium’s managed services for Microsoft Security Solutions is delivered through the company’s premium service: Fusion MXDR. Fusion MXDR includes 24x7 monitoring and management of Defender for Endpoint and Sentinel, threat intelligence, attack surface
monitoring, and vulnerability management for Microsoft Security customers. -
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- SOLUTIONS
-
-
Governance, Risk, + Compliance
GRC with context – not complexity. -
Attack Surface Management
No more blind spots, weak links, or fire drills. -
Threat Detection + Response
Detect, adapt, and attack with context. -
Microsoft Security Solutions
End-to-end support from strategy to daily operations to maximize your Microsoft Security.
-
-
- COMPANY
-
-
About Us
Security. It’s in our DNA. It’s elemental, foundational. Something that an always-on, everything’s-IoT-connected world depends on.
Helping mid-to-enterprise organizations protect assets and manage risk is our only business. Our mission is to make our customers’ world a safer place so that they may thrive in an always-on, connected world.
-
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- PARTNERS
-
-
Our Partners
Best-in-class technology from our partners... backed by service excellence from Avertium.
-
Partner Opportunity Registration
Interested in becoming a partner?
With Avertium's deal registration, partners can efficiently and confidently connect with Avertium on opportunities to protect your deals.
-
Latest Avertium Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- NEWS & RESOURCES
-
-
News & Resources
Dive into our resource hub and explore top
cybersecurity topics along with what we do
and what we can do for you. -
Latest Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- CONTACT
From Endpoints to Identity: Microsoft’s Approach to Holistic Cybersecurity
Protecting your business isn’t just about securing devices or locking down networks. The real challenge? Protecting your most vulnerable attack vector: people. As workforces become more distributed and cybersecurity grows more complex, identity protection often gets overlooked, but it remains a critical security priority.
And then there’s also the cloud. With so much of your data and operations moving to the cloud, having robust protection across cloud apps and services is critical. The challenge for many organizations is ensuring that these disparate pieces all work together effectively.
Over 90% of organizations experienced at least one identity-related incident in the past year. Hackers are getting smarter, finding new ways to steal credentials, infiltrate accounts, and wreak havoc.
So, what does that mean for your business? It means you need to think beyond traditional security and focus on protecting the people behind the screens. Even with all the new cybersecurity tools and proactive measures, remember that securing your people should always come first.
Related Resource: The Move from Reactive GRC to Proactive GRCaaS
Out-of-Band vs. In-Band Defense: Balancing Security and Operational Risk
In cybersecurity, it’s always a balancing act: you have to secure the business without getting in the way of day-to-day operations. There are two ways to think about the security measures taken to preserve this delicate balance: out-of-band and in-band defense.
-
Out-of-band defense refers to security measures that operate independently of the primary network traffic. They don’t interfere with day-to-day operations but provide additional layers of security that can be activated when needed.
-
In-band defense, on the other hand, is integrated directly into the network and system operations. While this approach can offer real-time protection and immediate response to threats, it also introduces potential operational risks. A well-known example of this risk is the recent CrowdStrike outage.
In July 2024, a flawed update from CrowdStrike caused a massive IT outage, affecting millions of Windows systems worldwide. The update introduced a logic error in their Falcon platform, which is an in-band security solution tightly integrated into the Windows kernel. The result was widespread system crashes and disruptions to critical services. This incident highlighted a risk of in-band defense: while it provides robust real-time protection, it can also lead to substantial operational disruptions if something goes wrong.
Microsoft and CrowdStrike’s swift response was a reminder that even the best cybersecurity systems can have vulnerabilities. However, Microsoft’s approach aims to strike a balance. By integrating security tools into their unified Managed Extended Detection and Response (MXDR) solution, they provide comprehensive protection while minimizing the risks associated with in-band defenses. This allows businesses to benefit from real-time security without the heightened risk of major disruptions, maintaining a balance between security and operational stability.
Why Identity is Your New Perimeter and Endpoint Protection
Remember when security was all about building a fortress around your data? Back then, protecting an organization’s perimeter and endpoints made sense. But today, your employees are working from everywhere – coffee shops, home offices, client sites. The perimeter isn’t just your office walls anymore; it’s wherever your people are.
That’s why identity is now the frontline of defense. Cybercriminals are targeting usernames and passwords, sending out sophisticated phishing attacks, and lurking in the shadows, waiting for the perfect moment to strike. And once they have someone’s credentials, it’s game over. That’s why protecting identity is so important – and why Microsoft has made it a vital part of their security strategy.
The Shift to an Asset-Based Model and a Holistic View
Risk management can be approached in two ways: asset-based or service-based. While the service-based approach is familiar to many, focusing on the asset-based model provides a more comprehensive perspective. In this model, users themselves are considered the primary assets, necessitating a holistic approach to security. This means expanding beyond merely securing devices or endpoints to encompass a full 360-degree view that includes identities, devices, and cloud environments.
Microsoft’s Identity-Centric Approach
This is where Microsoft Defender for Identity comes into play. Defender for Identity isn’t just about detecting bad software or blocking malicious links. It’s about understanding behavior – like when someone tries to log in at 3 a.m. from a country they’ve never been to. By focusing on identity, Microsoft helps you spot suspicious activity before it turns into a full-blown crisis.
And it doesn’t stop there. Identity is a fabric that is woven in all MS solutions. Whether it by Dynamics365 for ERP, to Viva Learning, Identities are a current that flows throughout Microsoft. Out of all of the 4 DefenderXDR components, Identity is the most important, and the first pillar any Microsoft solution, platform, or product is built on. Microsoft Defender for Identity integrates seamlessly with Entra ID (formerly Azure AD), tying into a larger, unified security ecosystem. This integration ensures that your identity protection is not just a patchwork of tools but a well-coordinated strategy designed to keep your people – and your business – safe.
Fitting Identity and Endpoint into the Bigger Picture: Microsoft DEFENDER XDR
Microsoft’s identity tools, like Defender for Identity and Microsoft Defender for Endpoint (MDE), aren’t just standalone solutions – they’re key pieces of Microsoft’s Defender Extended Detection and Response strategy. Defender XDR goes beyond traditional security by delivering a 360-degree view of your environment, combining identity, endpoint, cloud, and email protection into one powerful solution.
When you look at Microsoft’s full Defender suite, it includes more than just endpoint protection:
- Defender for Identity safeguards your workforce by analyzing user behaviors and flagging anomalies.
- Defender for Endpoint (MDE) detects and responds to threats on devices.
- Defender for Office 365 monitors and protects email, attachments, and links.
- Defender for Cloud Apps secures the cloud environment by detecting risky behaviors.
These tools integrate seamlessly into the MXDR framework, providing real-time insights, automated responses, and proactive defense across your entire digital ecosystem. Defender XDR can also connect with Copilot for Security, which enhances visibility and response capabilities by feeding off all the XDR components. This integration, alongside Sentinel SIEM and tighter integration with Entra ID, prepares you for the shift toward identity-based cybersecurity, offering comprehensive protection and a unified view of your security landscape.
Related Resource: Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseSimplifying Security for Mid-Market Companies with Microsoft Defender XDR
Let’s be real – security can be complicated. For mid-sized businesses, juggling multiple vendors, tools, and contracts can feel like trying to solve a never-ending puzzle. The beauty of Microsoft’s approach is that it brings everything under one roof.
Defender XDR correlates signals from endpoints, identities, cloud apps, and emails. For example, if there’s an identity breach flagged by Defender for Identity, that information is cross-referenced with data from Defender for Cloud Apps and Defender for 365 to see if there’s unusual activity in your cloud services or email. This correlation of data across multiple layers of your environment is what sets Defender XDR apart from traditional EDR solutions.
By combining different sources of threat intelligence and behavioral analysis, Defender XDR provides deeper context and visibility that allows you to detect and respond to threats faster and more accurately. Instead of treating incidents as isolated events, you see the whole story – and that makes all the difference when it comes to stopping attacks in their tracks.
Instead of managing separate solutions for identity, endpoint, and cloud security, Microsoft offers a unified platform that works seamlessly. This not only simplifies your security but also cuts down on costs. You get 80-90% of the functionality of other expensive tools, without the headaches of managing a bunch of separate systems. More security, less hassle.
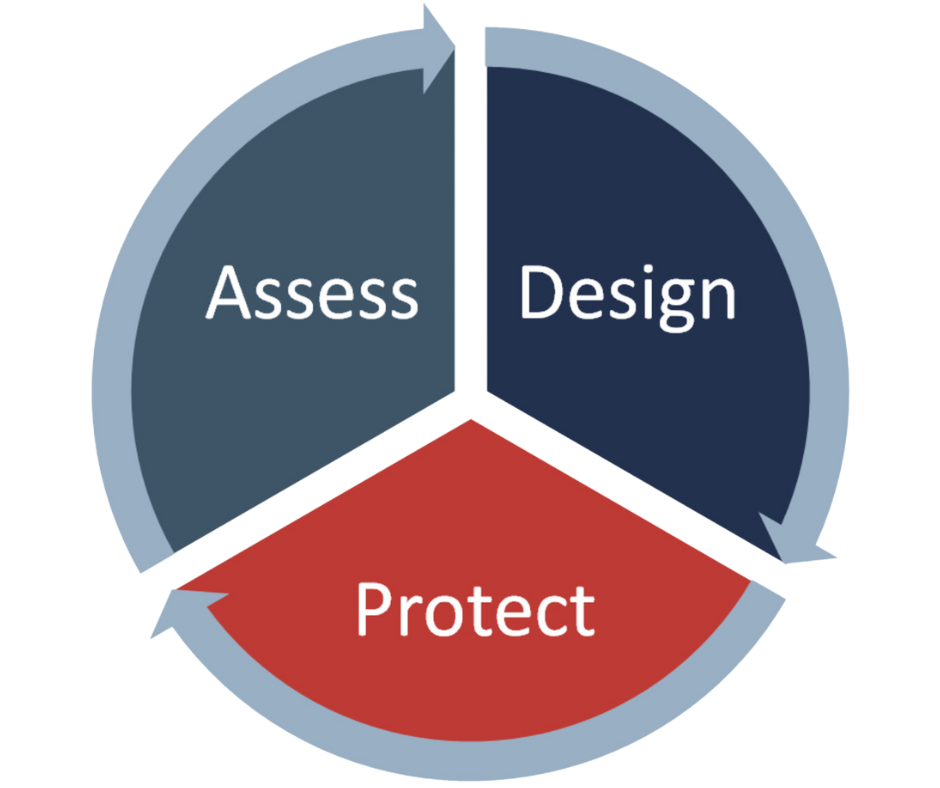
How MXDR Aligns with Avertium’s “Assess, Design, Protect” Approach
At Avertium, we believe security isn’t just a one-time project – it’s an ongoing process. That’s why our Assess, Design, Protect approach fits seamlessly with Microsoft’s Defender XDR solution. Here’s how:
-
Assess – Get a clear picture of your current state. We start by identifying your unique risks and vulnerabilities by assessing your overall security and compliance posture. With MXDR, this includes looking at your identity and endpoint security, cloud usage, and any gaps that might expose your business to threats.
-
Design – Prioritize and optimize your security architecture. Once we know where you stand, we help you design a security strategy that fits your needs. Microsoft’s integrated tools, from Defender for Identity to endpoint protection, give us the flexibility to build a solution that covers all your bases.
-
Protect – Fuse together your cybersecurity operations for continuous improvement and proactive protection. Finally, we implement and manage the solution, providing continuous protection through MXDR’s monitoring and response capabilities. This means you can focus on running your business while we keep an eye on the threats.
Together, Microsoft’s MXDR solution and Avertium’s expertise provide a comprehensive security approach that grows with your business and adapts to new challenges.
Real-World Impact: Why Focusing on Identity Matters in Healthcare
For healthcare organizations, the stakes are even higher. Protecting patient data isn’t just a priority – it’s a legal requirement. And with healthcare being a prime target for cyberattacks, securing identities is crucial. From patient records to medical devices, identity-based attacks can disrupt care and put lives at risk.
That’s where Microsoft’s identity solutions shine. By integrating identity protection with endpoint security, healthcare organizations can safeguard not only their employees but also their patients. And with MXDR, you get a proactive security approach that helps prevent breaches before they happen, ensuring that sensitive data stays protected.
Related Resource: Looking Ahead at the Cybersecurity Landscape for Healthcare in 2024
The Future of Cybersecurity Starts with Identity – Ready to Protect What Matters Most?
The reality is, cybersecurity is always changing. The old ways of protecting your business aren’t enough anymore. As AI and machine learning evolve, so do the threats – and the solutions. Microsoft is staying ahead of the curve with tools like Copilot for Security, which uses AI to help detect and stop identity threats before they cause damage.
Microsoft’s identity-centric security strategy is built to protect your business today and prepare it for the threats of tomorrow.
Your most vulnerable attack vector is your people, and protecting them starts with securing their identities. With Microsoft’s integrated approach to security, you can keep your business safe from the growing threat of identity-based attacks – without adding complexity to your day-to-day operations.
Let’s get started. Discover how Avertium can help your business stay one step ahead with identity management.
Check out our Blog on, "What Does the Microsoft e5 License Mean for Your Cybersecurity?"