- WHY AVERTIUM?
-
-
Why Avertium?
Context over chaos. Disconnected technologies, siloed data, and reactive processes can only get you so far. Protecting businesses in today’s threat landscape demands more than a set of security tools – it requires context.
That's where Avertium comes in
-
Considering Microsoft?
Avertium Named Microsoft Security Solutions PartnerAvertium’s managed services for Microsoft Security Solutions is delivered through the company’s premium service: Fusion MXDR. Fusion MXDR includes 24x7 monitoring and management of Defender for Endpoint and Sentinel, threat intelligence, attack surface
monitoring, and vulnerability management for Microsoft Security customers. -
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- SOLUTIONS
-
-
Governance, Risk, + Compliance
GRC with context – not complexity. -
Attack Surface Management
No more blind spots, weak links, or fire drills. -
Threat Detection + Response
Detect, adapt, and attack with context. -
Microsoft Security Solutions
End-to-end support from strategy to daily operations to maximize your Microsoft Security.
-
-
- COMPANY
-
-
About Us
Security. It’s in our DNA. It’s elemental, foundational. Something that an always-on, everything’s-IoT-connected world depends on.
Helping mid-to-enterprise organizations protect assets and manage risk is our only business. Our mission is to make our customers’ world a safer place so that they may thrive in an always-on, connected world.
-
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- PARTNERS
-
-
Our Partners
Best-in-class technology from our partners... backed by service excellence from Avertium.
-
Partner Opportunity Registration
Interested in becoming a partner?
With Avertium's deal registration, partners can efficiently and confidently connect with Avertium on opportunities to protect your deals.
-
Latest Avertium Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- NEWS & RESOURCES
-
-
News & Resources
Dive into our resource hub and explore top
cybersecurity topics along with what we do
and what we can do for you. -
Latest Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- CONTACT
To CMMC & Beyond: What You can do Today to Prepare for CMMC Tomorrow
The Cybersecurity Maturity Model Certification (CMMC) is coming - whether you’re ready or not. Today, it’s primarily meant for the Department of Defense (DoD) and its subcontractors, but this comprehensive framework could be coming to an enterprise like yours in the future.
CMMC is a holistic look at cybersecurity. With cybercrime becoming ever more sophisticated, there’s a real need for a change in the way we assess our current state of cybersecurity readiness.
Reasons for the creation and enforcement of CMMC:
-
To secure unclassified networks - The CMMC was created as a means to ensure that the Defense Industrial Base (DIB) Community is utilizing proper cybersecurity practices in protecting Federal Contract Information (FCI) and Controlled Unclassified Information (CUI) contained in their unclassified networks. It was created in Jan 2020 with the goal of improving the security of CUI and FCI that may be in possession of their federal contractor network.
-
To offer levels of compliance that make sense for the level of involvement for each business - DoD contractors have been required to comply with NIST SP 800-171 – a comparable security framework - since January 1, 2018 (currently in Rev 2, 1/21). The majority of NIST SP 800-171 can be found within CMMC, but unlike the entirety which can be difficult to manage for some businesses, CMMC takes a different approach stepping through five levels as mentioned.
-
It’s intended to reduce third-party risk - In short, the DoD realized that while their own systems were secure, they could not ensure the security of the various third parties connecting to their networks, providing personnel, or executing government service contracts. CMMC was designed to mitigate that risk by ensuring that primary and subcontractors are tightening their controls with Controlled Unclassified Information (CUI), as well as thoughtful measures around where it’s stored, transmitted, or processed.
The New CMMC 2.0 Model
With the implementation of the CMMC 2.0 progression model, the DoD introduces the following changes to the CMMC Model relative to CMMC 1.0:- Removing two progressive levels (levels 2 and 4)
- Eliminating the maturity processes and CMMC 1.0 level unique practices
What is the goal of CMMC 2.0?
- Simplify the process of becoming CMMC certified/compliant to enhance clarity on cybersecurity regulations, policies, and contract requirements
- Narrow the focus on third-party audit mandates and the most advanced cybersecurity measures of organizations
- Increase DoD oversight of professional and ethical criteria regarding third-party assessments to better safeguard sensitive federal information
CMMC 2.0 release date is March 2023 and contracts go into effect in July 2023.
Related Reading: Does CMMC Immunize You to Ransomware?
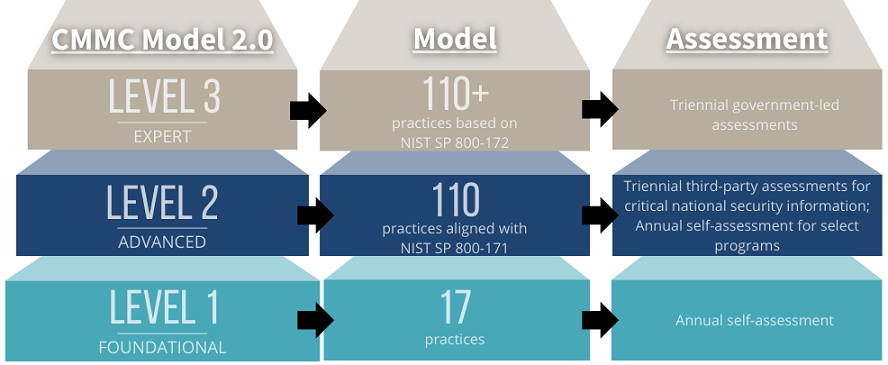
CMMC Model – Levels
Working towards certification, there are three CMMC Levels, and each is linked to a specific number of controls consisting of several assets: domains, capabilities (or a collection of practices), practices, and processes defined as maturity levels corresponding to the specific certification level. (see chart above for level specifications)
At first glance, this new set of requirements looks daunting. You should understand that they are a cumulative set of practices and processes across all 17 domains. To achieve a certain CMMC Level, you must have completed the preceding level. A participant must determine which level of certification applies best to their business requirements.
Let’s review and get a better understanding of the basic CMMC Levels:
CMMC Level 1 (Foundational)
Processes: Performed - Level 1 requires that an organization performs the specified practices. Because the organization may only be able to perform these practices in an ad-hoc manner and may or may not rely on documentation, process maturity is not assessed for Level 1.
Practices: Basic Cyber Hygiene - Level 1 focuses on the protection of FCI and consists only of practices that correspond to the basic safeguarding requirements specified in 48 CFR 52.204-21
Level one is comprised of 17 practices.
- An organization must demonstrate basic cyber hygiene practices, such as ensuring employees change passwords regularly to protect Federal Contract Information (FCI). FCI is "information, not intended for public release, that is provided by or generated for the Government under a contract to develop or deliver a product or service to the Government."
CMMC Level 2 (Advanced)
Processes: Managed - Level 2 requires that an organization establish, maintain, and resource a plan demonstrating the management of activities for practice implementation. The plan may include information on missions, goals, project plans, resourcing, required training, and involvement of relevant stakeholders.
Practices: Good Cyber Hygiene - Level 2 focuses on the protection of CUI and encompasses all of the security requirements specified in NIST SP 800-171 [4] as well as additional practices from other standards and references to mitigate threats.
Level two is comprised of 110 practices.
- An organization must have an institutionalized management plan to implement good cyber hygiene practices to safeguard CUI, including all the NIST 800-171 r2 security requirements and processes.
CMMC Level 3 (Expert)
Processes: Optimizing - Level 3 requires an organization to standardize and optimize process implementation across the organization.
Practices: Advanced/Proactive - Level 3 focuses on the protection of CUI from APTs. The additional practices increase the depth and sophistication of cybersecurity capabilities.
Level three is comprised of 110+ practices.
- An organization must have standardized and optimized processes in place and additional enhanced practices that detect and respond to changing tactics, techniques, and procedures (TTPs) of advanced persistent threats (APTs). An APT is an adversary that possesses sophisticated levels of cyber expertise, and significant resources to conduct attacks from multiple vectors. Capabilities include having resources to monitor, scan, and process data forensics.
Related Reading: Threat-Based Security at the Intersection of MITRE ATT&CK and NIST CSF (Whitepaper)
The “Known Unknowns”
-
The standard is evolving. There may be new controls over the next quarter.
-
The CMMC timeline is subject to change. Some CMMC specifications apply to only some contracts now and are expected to become part of DoD procurement in 2026.
-
CMMC is still being developed. In the National Defense Authorization Act that was just passed, you’ll find the following text: “1742. Department of Defense cyber hygiene and Cybersecurity Maturity Model Certification framework (a) Cybersecurity practices and capabilities in the Department of Defense (1) In general, not later than March 1, 2021, the Secretary of Defense, acting through the Chief Information Officer of the Department of Defense and the Commander, Joint Forces Headquarters-Department of Defense Information Network, shall assess each Department component against the Cybersecurity Maturity Model Certification (CMMC) framework and submit to the congressional defense committees a report that identifies each such component’s CMMC level and implementation of the cybersecurity practices and capabilities required in each of the levels of the CMMC framework.”
-
CMMC certification requirements will likely extend beyond the Department of Defense. Other branches of the government may and likely will choose to adopt CMMC.
What You Can do to Prepare for CMMC
STEP 1
Determine the maturity level that you want to be audited for compliance (CMMC Level 1-3).
Once you understand the CMMC requirements outlined above, you can determine the maturity level you need to reach. This begins with defining the CUI stored, processed, and transmitted within your environment.
STEP 2
Create room in the budget for CMMC certification.
While the DoD has expressed some degree of concern around the potential financial impact of reaching these CMMC requirements on small to medium-sized businesses, it has not outlined any provisions to assist these businesses with reaching the certification requirements. That’s why it’s important to outline a reasonable timeline and necessary resources (budget, personnel, etc.) around tasks like:
- Enhancing security requirements,
- Updating policies,
- SIEM technology, and
- Third-party assessor costs.
STEP 3
Take steps that can proactively address some of the issues impeding CMMC certification today.
Here is what we know regarding the rules for CMMC 2.0:
- Rules for CMMC 2.0 are expected to take around 9-24 months to be made
- CMMC 2.0 will not be required for government contractors until the rulemaking for title 32 CFR is done
While we don’t know all of the rules and stipulations around CMMC quite yet, we do have a general idea of which steps you can begin taking action on today:
- Align with NIST 800-171
- Develop and enforce policies and procedures that align with CMMC-related controls
- Establish The Scope of The CMMC Assessment Boundary.
- Create a Data Flow Diagram (DFD) that shows how CUI flows from the DoD all the way down to subcontractors;
- Create a detailed asset inventory for all systems, applications, and services for both in-scope and out-of-scope assets;
- Create a detailed network diagram that includes where CUI is stored, transmitted, and/or processed; and
- Inventory Third-Party Service Providers (TSP) to determine TSP access to CUI and/or in-scope systems, applications, and /or services.
- Have a system security plan (SSP, and a plan of action and Milestones in place (POA&M)
STEP 4
Have a third party conduct an assessment and gap analysis.
With CMMC, you cannot be self-certified. Therefore, enlisting the right partners- partners that have compliance expertise and are on the path to becoming a certified third-party assessment organization (C3PAO)- to conduct an assessment and gap analysis is recommended. You can ask your current cybersecurity provider if they’re a registered provider organization (RPO) for CMMC - this is often a good indicator of whether or not they’re on the path to becoming a C3PAO. Avertium is currently on under review to become a C3PAO.
Related Reading: The Cybersecurity Maturity Model Certification: Are You in Compliance?
How Avertium Can Help
Avertium, a CMMC registered provider organization (RPO), is an expert in CMMC Assessment, Readiness, and Program Creation. Avertium will get to know your organization, set a baseline maturity index, and work with you to tailor a path to compliance and security program improvement that fits the way you do business. Here’s what you can expect:
-
We’ll collaborate with your team, providing a Gap Analysis Report with a detailed matrix comparing baseline controls in place today with appropriate CMMC domain and control level requirements.
-
We’ll provide an Executive Summary Report to communicate findings and their implications to company decision-makers in support of your security efforts.
-
We’ll provide a detailed Remediation Roadmap based on the order of criticality to guide remediating deficiencies.
-
We’ll conduct Regular Touchpoint Meetings to review progress, and update your team on DoD guidance and CMMC changes, all while keeping you abreast of the latest technology trends and industry best practices.
-
Lastly, we can implement programs, technologies, and processes to help you become compliant and maintain your certification if you don’t have the resources or personnel to do so.
* Avertium is currently in the application process to become a CMMC Third Party Assessment Organization (C3PAO). A C3PAO is a certified CMMC assessor responsible for conducting CMMC assessments on behalf of the DoD. Once the assessment is completed, the C3PAO can appropriately issue CMMC certificates.*